About the ThreatQ Platform
ThreatQ is a cyber threat intelligence (CTI) platform designed to help organizations collect, prioritize, analyze, and operationalize threat intelligence at scale. It acts as a centralized intelligence hub that integrates data from multiple internal and external sources, enabling security teams to turn raw threat data into actionable insights.
At its core, ThreatQ ingests threat intelligence from commercial feeds, open-source intelligence, ISACs, partners, and internal tools such as SIEMs, EDRs, sandboxes, and ticketing systems. This data is normalized, correlated, and enriched to provide context around indicators, adversaries, campaigns, and incidents. Built-in scoring and prioritization mechanisms help analysts focus on the most relevant threats based on risk, confidence, and organizational relevance.
How the ThreatQ Platform Works
The ThreatQ platform is built to centralize, contextualize, and operationalize threat intelligence across the security ecosystem. By combining automated intelligence processing with analyst-driven workflows and an open integration framework, ThreatQ enables organizations to transform disparate threat data into actionable, prioritized intelligence.
Threat LibraryCentralized, Contextual Intelligence Management |
The Threat Library serves as the foundation of the ThreatQ platform, providing a centralized repository for threat intelligence from both internal and external sources. Intelligence is automatically normalized, enriched, scored, and prioritized based on customer-defined parameters and organizational context. By correlating data across multiple sources, ThreatQ delivers a single source of truth that reduces noise, minimizes false positives, and allows analysts to focus on the threats that pose the greatest risk.
Key Capabilities include:
- Automated, self-tuning scoring and prioritization
- Aggregated context from internal and external intelligence sources
- Support for structured and unstructured data ingestion
- Custom enrichment sources to extend existing security systems
 |
Adaptive WorkbenchAutomation Combined with Human Intelligence |
The Adaptive Workbench enables analysts to operationalize intelligence by combining automation with human expertise. Customer-defined configurations and integrations align ThreatQ with existing tools, processes, and workflows. Customizable enrichment, workflows, and prioritization logic streamline investigations, support continuous threat assessment, and automate key stages of the intelligence lifecycle—enabling faster, more informed detection and response.
Key Capabilities include:
- Consolidated, unified intelligence view across all sources
- Automated prioritization driven by aggregated context
- Continuous threat assessment and lifecycle management
- Push-button operations using existing tools and workflows
- User-specific watchlists for tailored intelligence monitoring
Open ExchangeOpen and Extensible Integration Ecosystem |
ThreatQ’s Open Exchange provides an open, extensible architecture that enables seamless integration across the security stack. Organizations can ingest intelligence from a wide range of internal and external sources, leverage existing enrichment and analysis tools, and distribute prioritized intelligence to downstream systems at the right time. Standard interfaces, APIs, and SDKs allow teams to customize integrations and maximize the value of existing security investments.
Key Capabilities include:
- Flexible ingestion and export of intelligence across tools
- Integration with enrichment, detection, and response platforms
- Standard APIs and SDKs for customization and extensibility
- Support for custom and customer-built connectors
Platform Modules
ThreatQ Modules extend the functionality of the core ThreatQ application. The current ThreatQ modules available are: ThreatQ Investigations, ThreatQ Data Exchange, and ThreatQ TDR Orchestrator.
These modules are not included in default ThreatQ deployment. Contact your Technical Account Manager to add one or more modules to your deployment.
ThreatQ Investigations
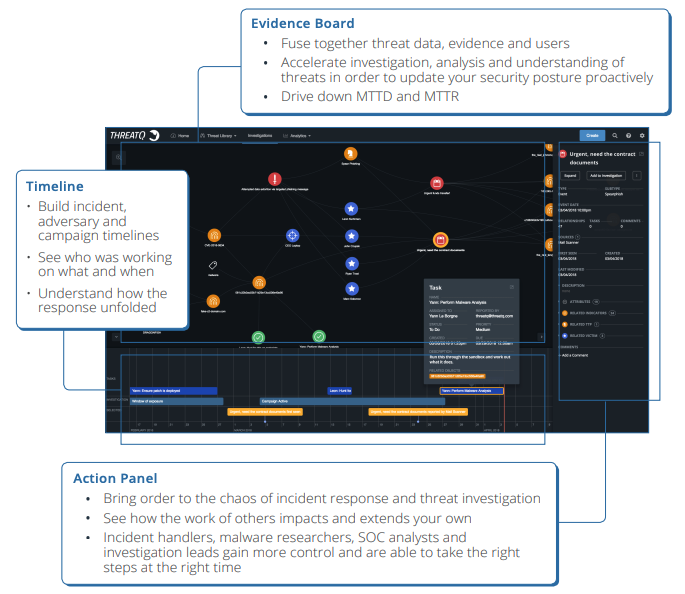
ThreatQ Investigations (TQI) is a collaborative investigation and analysis module built on the ThreatQ threat intelligence platform that provides a shared, centralized environment for managing complex security investigations. Designed as a cybersecurity “situation room,” it combines visualization, documentation, and intelligence context to deliver a unified view of threats, incidents, and response activities across teams.
The module enables security teams to capture, correlate, and share knowledge throughout the investigation lifecycle, creating a single, authoritative representation of each investigation—including associated threat data, evidence, user actions, and timelines. This shared understanding improves analytical focus, reduces investigative friction, and ensures transparency into who performed which actions and when.
ThreatQ Investigations enhances collaboration and coordination across distributed teams by streamlining communication, supporting parallel analysis, and enabling analysts to test hypotheses before sharing them more broadly. Team leads can assign tasks, guide investigative efforts, and monitor progress in near real time, helping organizations reduce mean time to detect (MTTD) and mean time to respond (MTTR) while bringing greater structure and efficiency to security operations.
ThreatQ TDR Orchestrator
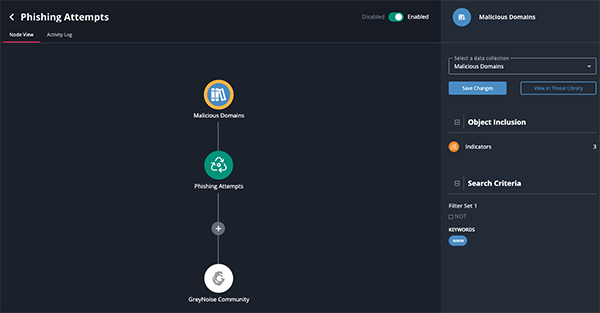
ThreatQ TDR Orchestrator (TQO) is an automation module designed to operationalize threat intelligence by enabling data-driven detection and response workflows across the security ecosystem. Built on ThreatQ data collections and ThreatQ Orchestration (TQO) actions, it simplifies configuration and ongoing maintenance while delivering more efficient, relevant, and scalable automation outcomes.
The module addresses the full automation lifecycle through a structured Initiate, Run, and Learn approach. During initiation, ThreatQ TDR Orchestrator uses curated intelligence and data-driven triggers to determine when automation should occur, ensuring actions are taken only when intelligence is relevant. In the execution phase, it orchestrates response actions using integrated third-party tools or native, data-driven playbooks defined within the ThreatQ platform. Finally, the learning phase captures resulting data and contextual outcomes to continuously refine analytics, improve triggering logic, and enhance future automation.
By prioritizing intelligence upfront and automating selectively, ThreatQ TDR Orchestrator reduces noise, streamlines response actions, and improves overall operational efficiency. It can function alongside other playbook and orchestration capabilities within the ThreatQuotient ecosystem, enabling organizations to build adaptive, intelligence-driven automation that continuously improves detection and response effectiveness over time.
ThreatQ Data Exchange
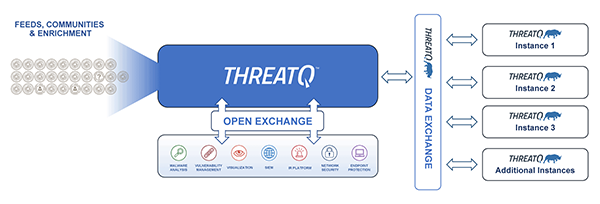
ThreatQ Data Exchange (TQX) is a secure intelligence-sharing module that enables organizations to distribute and consume threat intelligence using industry-standard transport mechanisms. It supports both bidirectional and unidirectional sharing models, allowing teams to collaborate effectively while maintaining control over how intelligence is shared and accessed.
TQX enables bidirectional intelligence sharing through an OpenDXL data transport, allowing multiple ThreatQ instances to exchange threat intelligence in near real time. Using this approach, publisher and subscriber instances share intelligence defined within Threat Library Data Collections, ensuring that only curated and relevant data is exchanged.
For unidirectional sharing, ThreatQ Data Exchange provides a TAXII server that formats intelligence from Threat Library Data Collections into STIX and makes it available to authorized external users and organizations. The module includes built-in credential generation and access management, enabling organizations to securely control who can access shared intelligence via TAXII.
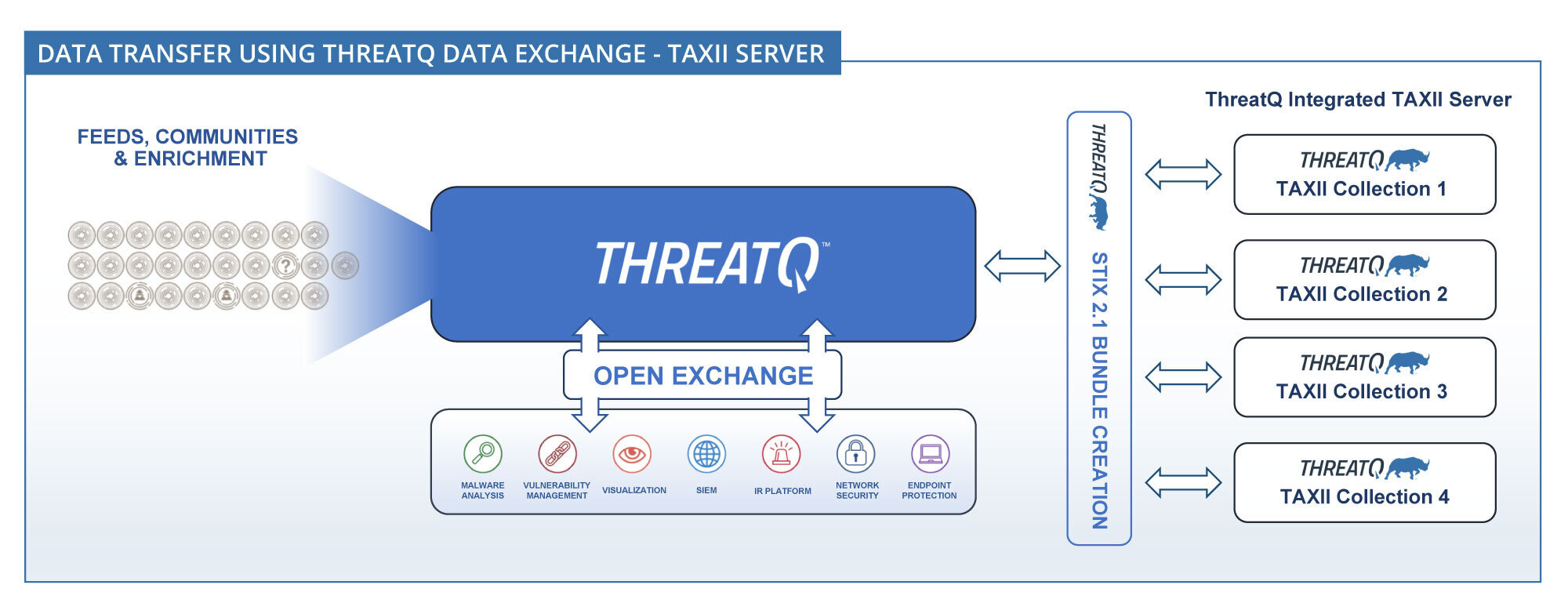
By supporting open standards and flexible sharing models, ThreatQ Data Exchange enables scalable, controlled collaboration across teams, partners, and communities, helping organizations operationalize shared threat intelligence more effectively.
PDF User Guides
Click on the version link below to open the PDF in your browser. You can also right-click the download link to save the file to your computer.
User Guides for prior releases are available in PDF only.
ThreatQ Version 6
| Document | Publish Date |
|---|---|
| ThreatQ v6.16.0 User Guide | 2026-02-24 |
| ThreatQ v6.15.0 User Guide | 2025-12-01 |
| ThreatQ v6.14.0 User Guide | 2025-11-10 |
| ThreatQ v6.12.0 User Guide | 2025-09-09 |
| ThreatQ v6.11.2 User Guide | 2025-08-08 |
| ThreatQ v6.10.0 User Guide | 2025-06-25 |
| ThreatQ v6.9.1 User Guide | 2025-06-05 |
| ThreatQ v6.9.0 User Guide | 2025-05-14 |
| ThreatQ v6.8.0 User Guide | 2025-04-30 |
| ThreatQ v6.7.4 User Guide | 2025-04-02 |
| ThreatQ v6.7.3 User Guide | 2025-03-11 |
| ThreatQ v6.7.2 User Guide | 2025-02-19 |
| ThreatQ v6.7.0 User Guide | 2025-01-28 |
| ThreatQ v6.6.0 User Guide | 2024-12-10 |
| ThreatQ v6.5.0 User Guide | 2024-10-29 |
| ThreatQ v6.4.0 User Guide | 2024-10-10 |
| ThreatQ v6.3.0 User Guide | 2024-09-17 |
ThreatQ Version 5
ThreatQ Version 4