ThreatQ Investigations
Default ThreatQ Role: Administrative, Maintenance, or Primary Contributor
Custom Role:
- Action Permissions: Objects & Context - Objects (all object types) OR Data Access Permissions: object types
- Action Permissions: Artifact Management - Investigations
Notes:
- Data Access Permissions also control your access to object types in TQI. For example:
- Evidence boards show only object types the user can access.
- Objects with No Access can be added to an investigation but cannot be committed or removed.
- Related objects appear only if the user has access to them.
ThreatQ Investigations is a cybersecurity situation room that enables collaborative threat analysis, investigation, and coordinated response. Investigations is built upon a collaborative investigation interface that aggregates all information on screen with a focus on the evidence board, which displays threat intelligence data as icons.
ThreatQ Investigations is built on top of the ThreatQ threat intelligence platform and allows for capturing, learning, and the sharing of knowledge. This results in a single visual representation of the complete investigation at hand, who did what and when, based on a shared understanding of all components of the investigation: threat data, evidence, and users.
The following describes the components of an investigation and how it can be used to drive an incident response.
Evidence Board
The evidence board provides a visual representation of the threat intelligence data you are currently investigating.
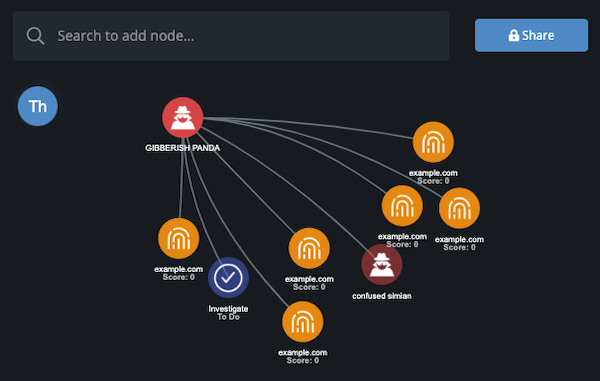
The evidence board allows you to:
- Fuse together threat data and user actions to more quickly determine the right actions to take.
- Accelerate investigation, analysis, and understanding of threats in order to update your defensive posture proactively.
- Drive down mean time to detect (MTTD) and mean time to respond (MTTR).
Action Panel
Using the action panel, incident handlers, malware researchers, SOC analysts, and investigation leads gain more control, and are able to take the right steps at the right time.
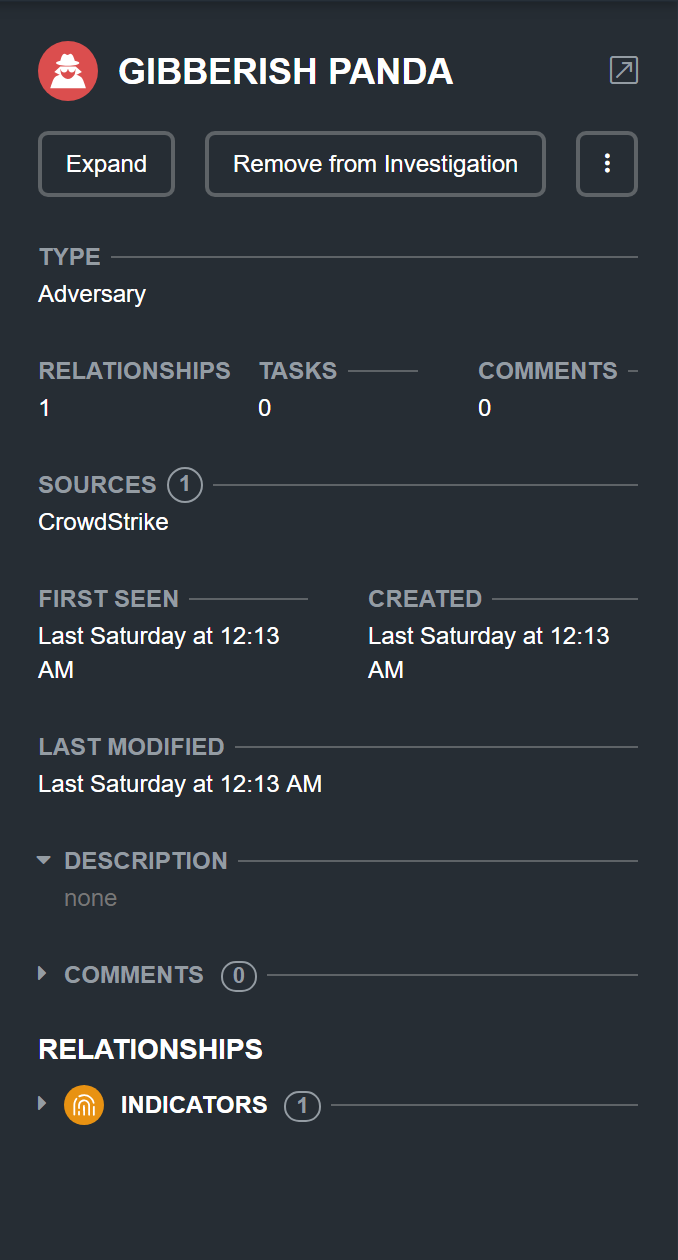
The action panel allows you to:
- See how the work of others impacts and extends your own.
- View a summary of any aspect of the evidence board that currently has mouse focus.
Timeline
You can build incident, adversary, and campaign timelines to accelerate understanding of threat intelligence data. The timeline portion of an investigation allows you to visualize how the investigation began and understand how the response unfolded.
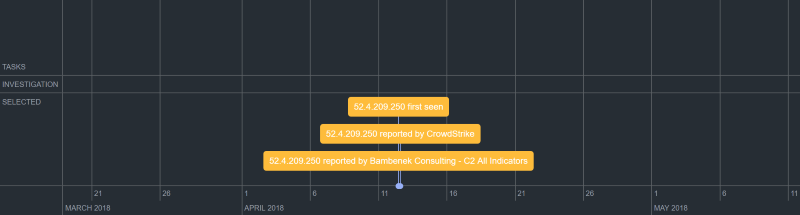
You can view:
- When indicators, events, adversaries, files, signatures, and so on were discovered and included in the Threat Library.
- Any assigned and closed tasks.
- Who was working on what aspect of the investigation and when.
PDF User Guides
ThreatQ Investigations is seeded as part of the ThreatQ platform. The document versioning assigned to the PDF guides below is for documentation-tracking purposes only and does not indicate a separate ThreatQ Investigations version.
| Guide | Min ThreatQ Version | Published Date |
|---|---|---|
| ThreatQ Investigations User Guide v4.4.2 | >= 6.16.0 | 2026-02-24 |
| ThreatQ Investigations User Guide v4.4.1 | 6.8.0 - 6.15.1 | 2025-04-30 |
| ThreatQ Investigations User Guide v4.4.0 | 6.7.0 - 6.7.4 | 2025-01-28 |
| ThreatQ Investigations User Guide v4.3.1 | 6.5.1 - 6.6.0 | 2024-11-19 |
| ThreatQ Investigations User Guide v4.3.0 | 5.28.0 - 6.5.0 | 2024-04-03 |
| ThreatQ Investigations User Guide v4.2.0 | 5.23.0 - 5.27.0 | 2023-11-30 |
| ThreatQ Investigations User Guide v4.1.0 | 5.21.0 - 5.22.0 | 2023-10-12 |
| ThreatQ Investigations User Guide v4.0.0 | 5.6.0 - 5.20.0 | 2023-06-21 |
| ThreatQ Investigations User Guide v3.0.0 | 5.6.0 | 2022-10-19 |
| ThreatQ Investigations User Guide v2.4.0 | 4.1.0 | 2021-09-01 |
| ThreatQ Investigations User Guide v2.3.0 | 4.1.0 | 2021-08-10 |
| ThreatQ Investigations User Guide v2.2.0 | 4.1.0 | 2021-07-07 |
| ThreatQ Investigations User Guide 2.1.0 | 4.1.0 | 2021-06-14 |
| ThreatQ Investigations User Guide v2.0.0 | 4.1.0 | 2020-11-23 |
| ThreatQ Investigations User Guide v1.0.0 | 4.1.0 | 2018-05-23 |