Current ThreatQ Version Filter
About LDAP Authentication
Default ThreatQ Role: Administrative or Maintenance
Custom Role - Action Permissions: Administrative Functions - Edit User Management
Lightweight Directory Access Protocol (LDAP) authentication verifies a user’s identity by validating credentials against a centralized directory service. ThreatQ supports the following LDAP connection options:
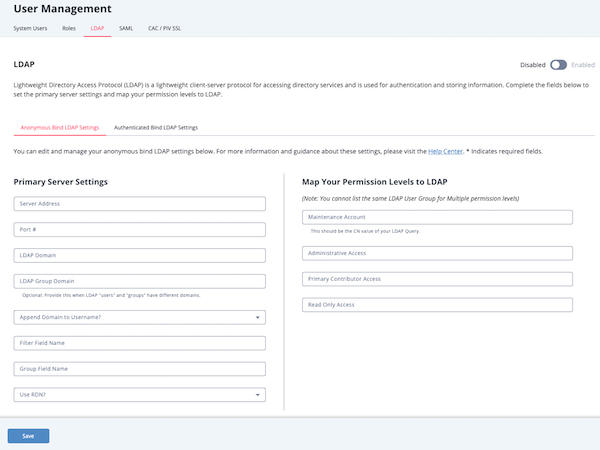
- Anonymous Bind – enables the application to connect to the LDAP directory without providing credentials. Access is restricted to directory information explicitly configured for anonymous use. See the Anonymous Bind topic for more details.
- Authenticated Bind – requires valid LDAP credentials to establish a connection, granting access based on the authenticated account’s permissions and group memberships. See the Authenticated Bind topic for more details.
Before configuring LDAP settings, review the following important considerations:
- LDAP Requirements - it is highly recommended that you review the LDAP Connection Requirements topic before configuring your LDAP settings.
- Switching from SSL Client Certificate to LDAP – if SSL Client Certificate Authentication is enabled, the LDAP configuration tab will display a warning indicating that SSL Client Certificate Authentication (CAC) must be disabled before LDAP can be enabled.
- Air Gapped Data Sync (AGDS) users – when LDAP or SAML authentication is enabled on a source ThreatQ instance and users are transferred via import, the same authentication method must be enabled on the target ThreatQ instance prior to the import to ensure continued authentication access for transferred users.
Accessing the LDAP tab:
- From the main menu, select the Settings
 icon > User Management.
icon > User Management. - Click the LDAP tab.
The LDAP tab opens with the Anonymous Bind LDAP Settings form loaded by default.