Authenticated Bind
Default ThreatQ Role: Administrative or Maintenance
Custom Role - Action Permissions: Administrative Functions - Edit User Management
An authenticated bind LDAP is an LDAP connection in which a client provides valid credentials, such as a username and password, to authenticate against an LDAP directory service. Follow the steps below to configure your ThreatQ instance for an authenticated bind LDAP connection.
It is recommended that you contact ThreatQ Support before configuring an authenticated bind connection.
- Navigate to Settings
 > User Management.
> User Management. - Click on the LDAP option and select the Authenticated Bind LDAP Settings tab.
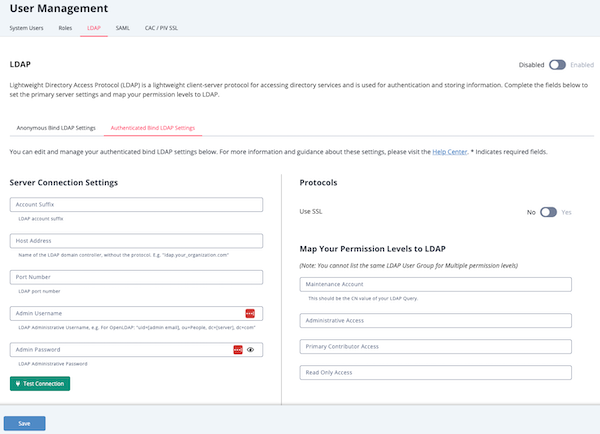
- Complete the Server Connections Settings section:
Field Description Account Suffix The LDAP account suffix. Host Address Name of the LDAP domain controller without the protocol.
Example: tqldap.threatq.comPort Number The LDAP port; either 636 or 389.
Only standard ports for secured and unsecured connections are supported. Use port 636 if using SSL to create a secured connection.Admin Username The LDAP administrative username. Admin Password The LDAP administrative password. - After you populate the Server Connections Settings fields, click the Test Connections button to verify the settings are correct.
- Complete the LDAP Schema section:
Field Description Base DN The Base DN of the LDAP server connection.
Example: DC=[server], DC="com"DN Field Name The field used to retrieve the DN or users and groups.
This field should be DN for both OpenLDAP and Active Directory.User Search Filter The field to search for users.
For OpenLDAP: objectClass=poslxAccount
For Active Directory: objectClass=userGroup Search Filter The field to search for grpups.
For OpenLDAP: objectClass=poslxGroup
For Active Directory: objectClass=groupPrimary Group Name The primary group name. Group Member Field Name This field is used to search for groups that a user belongs to.
For OpenLDAP: cn
For Active Directory: memberofUser ID Key Field Name Field used to search for users based on email.
For OpenLDAP: uid
For Active Directory: sAMAccountNameUser Group Member Key Field Name Field used to search for groups that user belongs to.
For OpenLDAP: memberUid
For Active Directory: uid - Under the Protocols section, use the Yes/No toggle switch to select whether the connection will use SSL.
If the connection will use SSL, confirm that the port number, set in step 3, is 636 to create a secured connection.
- Complete the MAP your Permission Levels to LDAP section:
To ensure successful authentication, each LDAP user should belong to only one (1) LDAP user group. If this is not feasible, new LDAP groups should be created with mutually exclusive user membership.
LDAP user groups require careful planning to avoid permission conflicts caused by overlapping group memberships. For example, when a user inherits read/write permissions from one group but is denied write access through another.
It is recommended to implement a clear hierarchy of group memberships for each security device instance, with an administrative group at the top and a standard user group at the bottom. Multi-group membership should be avoided in favor of a least-privilege approach, and group nesting should be kept as shallow as possible.
Permissions should be assigned through group membership rather than individual user roles to maintain consistency and simplify access management.
You cannot save the configuration without entering a value in each field. For roles not mapped, you should enter a hyphen:-.Field Description Maintenance Account The LDAP account the ThreatQ Maintenance group will map to for permissions.
Open LDAP Example: ldapSuper
Active Directory Example: CN=tq‑maintenance,CN=Builtin,DC=yourdomain,DC=comAdministrative Access The LDAP account the ThreatQ Administrative group will map to for permissions.
Open LDAP Example: administrator
Active Directory Example: CN=linux‑admins,CN=Builtin,DC=yourdomain,DC=comPrimary Contributor Access
The LDAP account the ThreatQ Primary Contributor group will map to for permissions.
Open LDAP Example: ldapAnalyst
Active Directory Example: CN=linux‑admins,CN=Builtin,DC=yourdomain,DC=comRead-Only Access The LDAP account the ThreatQ Read-Only group will map to for permissions.
Open LDAP Example: ldapObserver
Active Directory Example: CN=read‑onlyCN=Builtin,DC=yourdomain,DC=com - Use the Connect To Receive Data section connect to your LDAP using the settings on this page to pull group information and user lists
- Click Save.
- Click the Enable/Disable toggle switch to enable LDAP.
Green indicates the feature is active.