Anonymous Bind
Default ThreatQ Role: Administrative or Maintenance
Custom Role - Action Permissions: Administrative Functions - Edit User Management
Anonymous Bind LDAP refers to an LDAP connection in which a client accesses an LDAP directory without providing authentication credentials.
ThreatQuotient strongly recommends that you perform a full backup before changing your authentication method.
- Navigate to Settings
 > User Management.
> User Management. - Click on the LDAP option.
The Anonymous Bind LDAP Settings form will load by default.
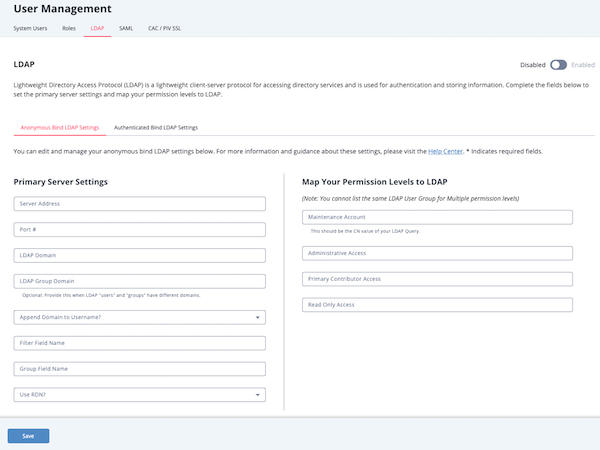
- Populate the fields in the Primary Server Settings section:
Field Description Server Address Enter the name of the server where LDAP is hosted.
Example: ldap://[servername]Port # 389 for LDAP
636 for LDAPS
If LDAPS is used, the Port # will default to 636.LDAP Domain Enter the domain for which LDAP is configured to authenticate.
Example: threatq.comLDAP Group Domain Optional - provide this when LDAP "users" and "groups" have different domains. Append Domain to Username? Choose from the following options: - Yes for most Active Directory servers
- No for most Open LDAP servers
Filter Field Name This field is specific to your LDAP directory configuration.
AD Example: memberuid
OpenLDAP Example: uid
Group Field Name This field is specific to your LDAP directory configuration.
AD Example: memberof
OpenLDAP Example: cnUse RDN? Choose from the following options: - Yes to use Relative Distinguished Names. When you select this option, the Organization Unit (OU) and User Lookup Name fields are displayed.
- No to use full Distinguished Names
Organizational Unit (OU) This field is specific to your LDAP directory configuration. Your LDAP administrator should provide the correct value for this field. User Lookup Name This field is specific to your LDAP directory configuration.
AD Example: memberUid
OpenLDAP Example: uid - Complete the MAP your Permission Levels to LDAP section.
To ensure successful authentication, each LDAP user should belong to only one (1) LDAP user group. If this is not feasible, new LDAP groups should be created with mutually exclusive user membership.
LDAP user groups require careful planning to avoid permission conflicts caused by overlapping group memberships. For example, when a user inherits read/write permissions from one group but is denied write access through another.
It is recommended to implement a clear hierarchy of group memberships for each security device instance, with an administrative group at the top and a standard user group at the bottom. Multi-group membership should be avoided in favor of a least-privilege approach, and group nesting should be kept as shallow as possible.
Permissions should be assigned through group membership rather than individual user roles to maintain consistency and simplify access management.
You cannot save the configuration without entering a value in each field. For roles not mapped, you should enter a hyphen:-.Field Example Maintenance Account OpenLDAP Example: ldapSuper
AD Example: CN=tq‑maintenance,CN=Builtin,DC=yourdomain,DC=comAdministrative Access OpenLDAP Example: administrator
AD Example: CN=linux‑admins,CN=Builtin,DC=yourdomain,DC=comPrimary Contributor Access OpenLDAP Example: ldapAnalyst
AD Example: CN=primary‑contributor,CN=Builtin,DC=yourdomain,DC=comRead Only Access OpenLDAP Example: ldapObserver
AD Example: CN=read‑onlyCN=Builtin,DC=yourdomain,DC=com - Click Save.
- Click on the Enable/Disable toggle switch to enable LDAP.
If your LDAP fails to enable or fails to function properly, validate your inputs. If the configuration continues to fail, please contact ThreatQ Support.
Configuring Secure LDAP
The following instructions are for Anonymous Bind LDAP connections only. The steps needed to create a secured connection authenticated bind are included in the Configuring Authenticated Bind LDAP Settings topic.
ThreatQuotient strongly recommends that you perform a full backup before changing your authentication method.
To configure secure LDAP, you must complete the following steps:
- Enter your LDAP settings in the ThreatQ user interface. See the Anonymous Bind steps above for more details.
- Access the ThreatQ appliance command line as root and edit and navigate to the following directory: /etc/openldap/.
- Use vi to edit ldap.conf and update/confirm that your settings are as follows:
# # LDAP Defaults # # See ldap.conf(5) for details # This file should be world readable but not world writable. BASE dc=[your domain],dc=com URI ldap://[your servername]:389 ldaps://[your servername]:636 #SIZELIMIT 12 #TIMELIMIT 15 #DEREF never TLS_CACERTDIR /etc/openldap/certs # Turning this off breaks GSSAPI used with krb5 when rdns = false SASL_NOCANON on TLS_REQCERT allowThreatQ recommends that you edit ldap.conf on the appliance, rather than editing off box and uploading it. If you do edit the file off box, ensure that you use a linux editor. Windows and Mac editors may corrupt the file.
If your LDAP fails to enable or fails to function properly, validate your inputs. If the configuration continues to fail, please contact ThreatQ Support.