Current ThreatQ Version Filter
Introduction
The ThreatQuotient App for Splunk provides users with the ability to pull ThreatQ indicators into their Splunk environment for evaluation. Once the indicators have been imported, they are added to a Splunk index or KVStore to provide further context on possible malicious activity that matches Splunk Events.
The app supports three Splunk Matching models for users to utilize:
- Enterprise Support Matching (ES)
- Common Information Matching (CIM)
- Raw Matching
See the Supported Matching Modes topic for more details on these matching models.
Users can then review and modify indicators using the Workflow Actions as well as send back the Splunk Sightings, in the form of events, to the ThreatQ platform.
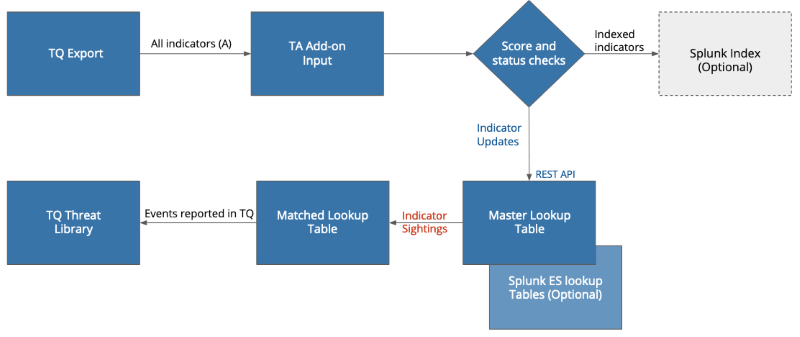
The app itself is composed of two main components:
- ThreatQuotient Add-On for Splunk - pulls indicator exports from the ThreatQ platform and submits the data to an index or the KVStore based on user configuration.
- ThreatQuotient App for Splunk - uses user-specified matching to identify sightings, updates indicators using app-provided workflow actions, and sends sightings back to the ThreatQ platform in the form of events.
Both of these components are required for the app to operate successfully.