Creating a New Input
Roles Required: Admin, Splunk_System_Role, ess_admin.
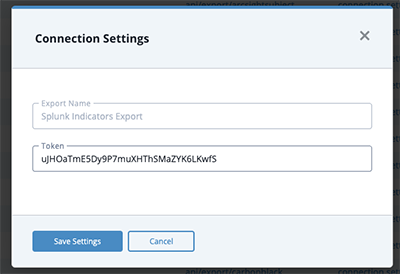
ThreatQ instances, starting with version 4.16.0, are shipped with a default export that this App uses: Splunk Indicators Export. You can find this export in ThreatQ by clicking on the Settings gear icon and selecting Exports.
The ThreatQuotient App for Splunk only supports one input.
First execution of this export results in the export of all indicators. Every subsequent run of this export will result in receiving new indicators as well as previously exported indicators that have since changed.
While in the ThreatQ Add-On for Splunk interface:
- Click on the Inputs menu heading.
- Click on Create New Input.
- Complete the following fields:
Parameter Description Interval The frequency of this job. This value can be reduced for faster detection and response. Minimum allowed is 60 seconds. Enable Index Enabling this option will result in data being saved to the designated index. Unchecking this option will result in data being saved directly to the KVStore. You must first complete the Splunk KVStore Rest configuration tab before disabling index storage. See the Configuring the KVStore section in the Installing the Add-On Component topic for more details. The Index parameter allows you to map the data extracted from a job in a predetermined Splunk index. You can create multiple jobs and map them to different Splunk indexes as needed.
Index Select from available indexes in the system. This is the Splunk index that you can optionally store data to. Export ID The Export ID is the final segment of the export's URL. The default ID in the Splunk Indicators Export seeded with the ThreatQ platform is splunk. As such, the default value in the Inputs form is splunk.

If you make a copy of the export, you must configure the ID of the export in this field as seen on the ThreatQ instance.

Export Token Enter the ThreatQ Splunk Indicator Export's Token in this field. The Export Token is located under the export's Connection Settings modal in ThreatQ.
Export Hash Defaults to 1. In the event you want to re-export all indicators from ThreatQ for any reason (such as installing a new Splunk instance), use this configuration. You can configure a different alphanumeric value of length up to 32 and cause exporting all indicators from ThreatQuotient again. If you need to re-pull all data after initial configuration, select the Pull All Indicators checkbox and then click Update.
Threshold Indicator Score Any indicator below this score is not indexed in Splunk. This threshold is very useful to reduce the data being indexed in the ThreatQuotient App. The default value is 8. Indicator Status Similar to the score threshold, any indicator not matching the status configured here is not indexed in Splunk. This technique is useful for reducing indexed data. The default values are Active. Pull All Indicators Enabling this checkbox will force pull all data on input edit. Initial import of ThreatQ data will now be performed using the pagination feature which imports a maximum of 10,000 records at once - see the Pagination Support topic for more details. The checkbox must be selected, upon input creation, before saving. This option should be utilized when changing the status or score of any input.
Response Page Size Define the number of indicators to retrieve per API request. The default value is 10000.Increasing this limit may cause memory exhaustion and result in the exports failing.
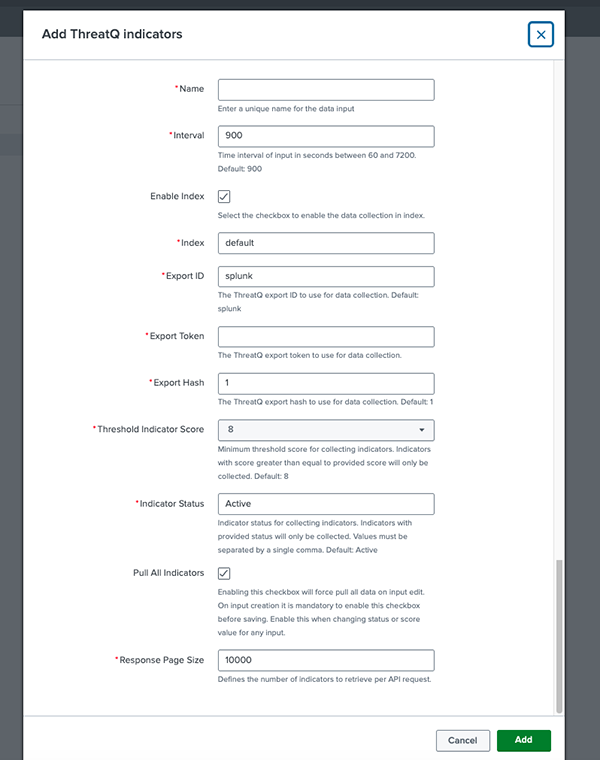
- Click on Add.