Current ThreatQ Version Filter
Supported Matching Modes
The ThreatQuotient App for Splunk can be used in one of three possible modes.
| Mode | Description | How Used |
|---|---|---|
| Enterprise Support (ES) | Splunk Enterprise Security is a specialized product offering from Splunk designed specifically for security operations and threat detection. It provides a comprehensive security information and event management (SIEM) solution that allows organizations to collect, analyze, and act upon security data from various sources in real-time. | Indicator data exported from ThreatQ is mapped to lookup tables native to Splunk ES. Threat Intelligence support for Enterprise Security is provided using its REST APIs. |
| Common Information Matching (CIM) | Splunk CIM (Common Information Model) is a standard for organizing and normalizing data in a consistent format to facilitate interoperability and integration between different security tools and technologies within an organization's security infrastructure. Splunk CIM Support refers to Splunk's built-in capabilities and tools for implementing and leveraging the CIM standard within the Splunk platform. | For users who map third party data (firewall events, logs for example) to Splunk's data models in CIM. The App provides optimized performance by leveraging those data models. |
| Raw Matching | Raw Matching Mode is applicable if you do not have Splunk Enterprise Security (ES) and do not map your traffic to Splunk's CIM. | In this mode, the App treats all events as raw binary data and looks for evidence of sightings inside said data using optimized regexes. See the tables in the Performance chapter for the expected performance data. |
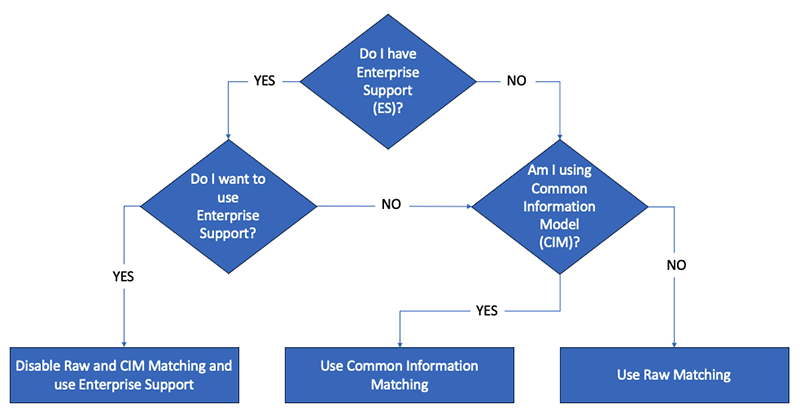
Determining Which Mode to Use
The workflow below can be used to determine which Splunk mode to utilize with the ThreatQ App and Add-On.