Platform Login
Log in steps vary based on the authentication methods enabled for your instance and/or user account.
| Authentication Method | Login Process |
|---|---|
| Local or LDAP | Local Log In |
| SAML | Single Sign-On (SSO) |
| SSL Client Certificate | SSL Client Certificate Authentication Log In |
Local Log In
The local login process applies to instances using local or LDAP authentication.
- Navigate to your ThreatQ instance -
https://your-ThreatQ-web-ip-address.

- Enter your username (email address) and password.
- If you have 2-step verification enabled, complete the following steps:
- Enter your verification code from Google Authenticator.
- Optionally, choose to Remember this computer for 30 days.
- Click Login or Submit.
Single Sign-On (SSO)
At this time, ThreatQ does not support IdP-initiated SSO, where a user can log in directly from an SSO provider's portal such as Okta's Portal. Users utilizing SSO must click the Log In Using SSO button on the ThreatQ landing page to authenticate with their IdP.
Users using SAML authentication use this log in method.
SAML users are required to add their email address to their user profiles in order to use the SSO. As part of the integration process, the ThreatQ platform expects that the user's email address has already been added to their IdP. See the Setting up LDAP Users/Groups for SAML topic for more details.
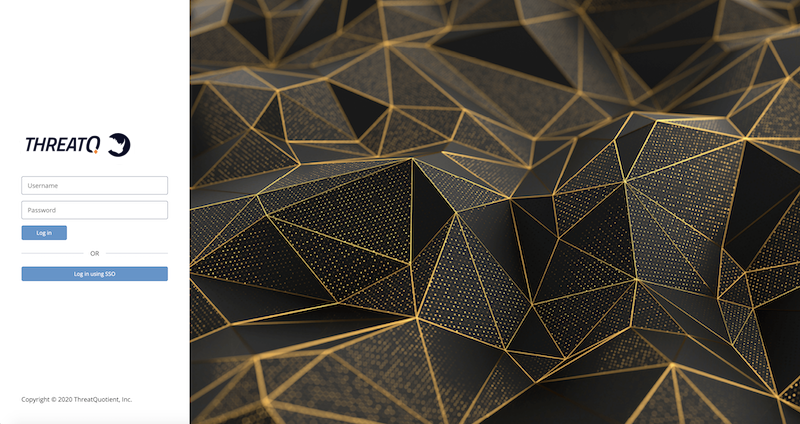
- Navigate to your ThreatQ instance -
https://your-ThreatQ-web-ip-address.If SAML is enabled, you will see a Single Sign-On option.
- Click the Log in Using SSO button.
Navigate to your third-party authenticated site to log in. Once that has been completed, you are automatically sent back to the ThreatQ instance.
SSL Client Certificate Authentication Log In
Maintenance users can log into ThreatQ using either username/password or certificate authentication. Administrative, Primary Contributor, and Read-Only users are required to use certificate authentication to log into ThreatQ if it is enabled.
After SSL Client Certificate Authentication is configured and you have added a certificate fingerprint to your user profile, you can use the following login method.
- Access your certificate, and enter your PIN. Your certificate must be active in the browser before you navigate to your ThreatQ instance.
- Navigate to your ThreatQ instance -
https://your-ThreatQ-web-ip-address.
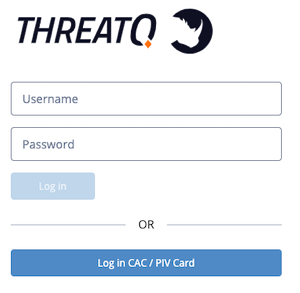
- Click the Log in CAC/PIV Card button.