Parsing for Events
Default ThreatQ Role: Administrative, Maintenance, or Primary Contributor
Custom Role - Action Permissions: Objects & Context - Perform Bulk Manual Import, Create, Edit, Delete Objects, Create, Edit, Delete Attributes, Create, Edit, Delete Relationships. See the Interdependent Permissions topic.
Notes:
- If a user's role has View Only permission for Sources, system object parsers default to the user’s login as the object source.
- If a user's role does not include permission to Edit or delete an object's Status, system object parsers apply the default status to seeded system objects and the first status option for custom objects.
Custom Role - Data Access Permissions: Events
Note:: If an import contains object types or context you lack Create/Edit/Delete permission for, the import fails.
ThreatQ gives you the option to import a file, parse it for events, and add those events to your Threat Library. During the import process you can assign a source, status, point of contact and a relationship to the imported events.
Importing Events with the Spearphish Parser
During the import process you can click the Abandon this Import button to stop the import process without adding any of the import file data.
- Go to Create > Spearphish Parser.
The Add Event window is displayed.
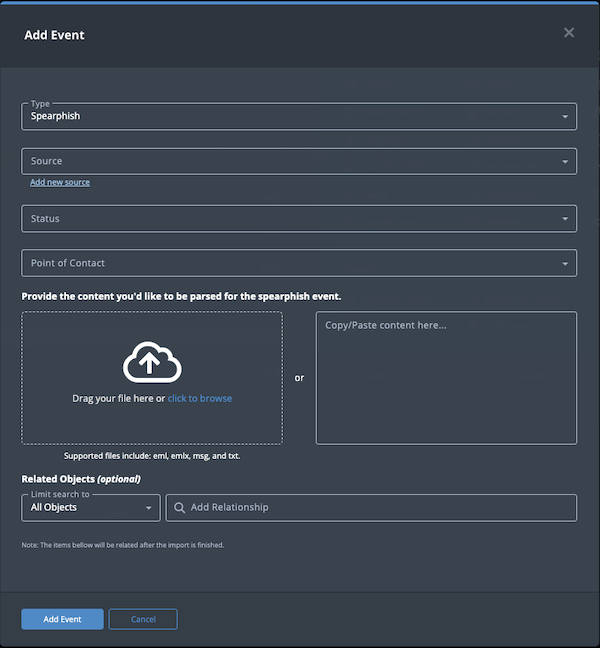
- Populate the following fields:
Field Description Type This field defaults to a value of Spearphish. Source Select a Source from the dropdown list provided. You can also click the Add a New Source option if the desired source is not listed in the drop-down list. If administrators have enabled TLP view settings, you can select a TLP label for the new source in the dropdown list provided. See the Traffic Light Protocol (TLP) topic for more information on TLP schema.Status Optional field. Click the Status field to assign a status to the event. Event statuses are configured in the Object Statuses tab in the Object Management page. If none are configured, this field is not displayed.
Point of Contact Optional field. Click the field to select the ThreatQ display name of the point of contact for the event. - Use one of the following methods to upload the file to be parsed:
- Drag the file to the window.
- Click the click to browse link to access your File Finder/File Explorer and select the file.
- Paste the email content into the text box on the right.
- Select any Related Objects you need to link to the event. This field is optional.
- Click Add Event.
The Spearphish Parser page is displayed.
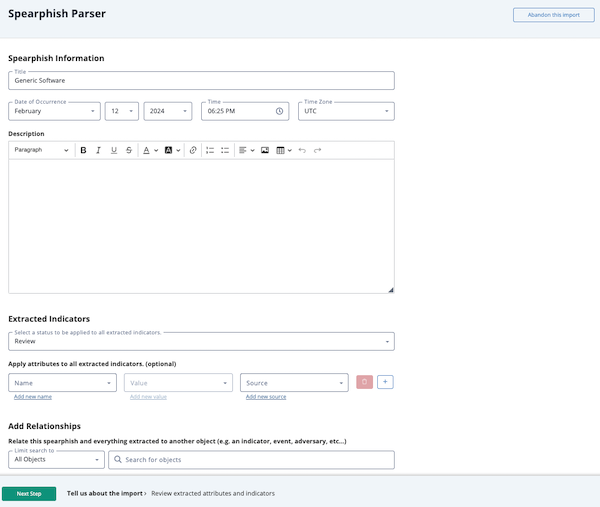
- The Spearphish Parser page consists of three sections that allow you to review and update the following information:
- Spearphish Information - Allows you to review and update the event information extracted from the file you uploaded.
- Extracted Indicators - Allows you to specify the status and attributes to be applied to all extracted indicators.
- Add Relationships - Allows you to add relationships to the spearphish event and any other extracted object.
- Click the Next Step button.
The second Spearphish Parser screen displays any attachments associated with the imported email. You can import these attachments or remove them from the import by checking the checkbox to the left of the attachment and clicking the Remove option.If the imported email did not include attachments, ThreatQ bypasses this screen and takes you directly to the third Spearphish Parser page.
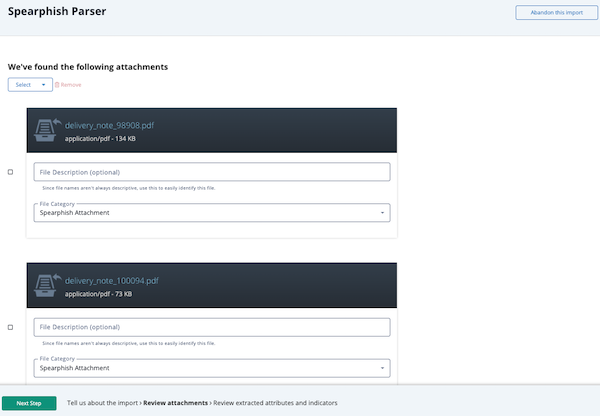
- Click the Next Step button.
The third Spearphish Parser page is displayed.
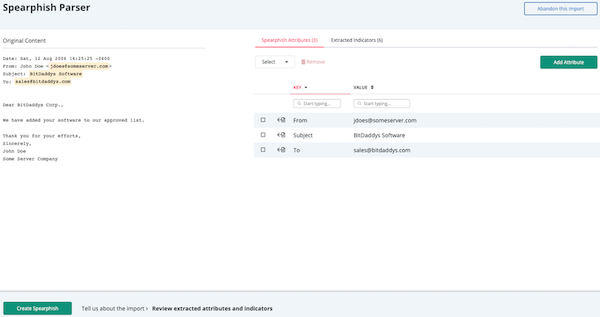
- The third Spearphish Parser page allows you to review the attributes and indicators to be imported. From this page, you can:
- Add/remove an attribute - From the Spearphish Attributes tab, click the Add Attribute button and enter the attribute details in the Add Attribute window. To remove an attribute, check the checkbox located to the left of the attribute key. Then, click the Remove option.
- Add/remove an indicator - From the Extracted Indicators tab, click the Add Indicator button and enter the indicator details in the Add Indicator window. To remove an indicator, check the checkbox located to the left of the indicator value. Then, click the Remove option.
- Add information to an indicator - Check the checkbox located to the left of the indicator you want to update. Then, click the Add Info option to access the Add Info window. Enter your changes in the Set Status or Add Comment tab and click the Add Attributes button.
- Click the Create Spearphish button.
The spearphish event is ingested into the Threat Library.