Attack Patterns
Default ThreatQ Role: Administrative, Maintenance, or Primary Contributor
Custom Role:
- Action Permissions: Objects & Context - Objects (all object types) OR Data Access Permissions: Attack Pattern
- Action Permissions: Individual Object Context & Actions
Note: If a user has View Only permission for Sources, system object creation modals default to the user’s login as the object source.
Attack Patterns are descriptions of methods used to exploit software.
Use the steps below to create, edit and delete an Attack Pattern.
Adding an Attack Patterns
- Go to Create > Attack Pattern.
The Add Attack Pattern window is displayed
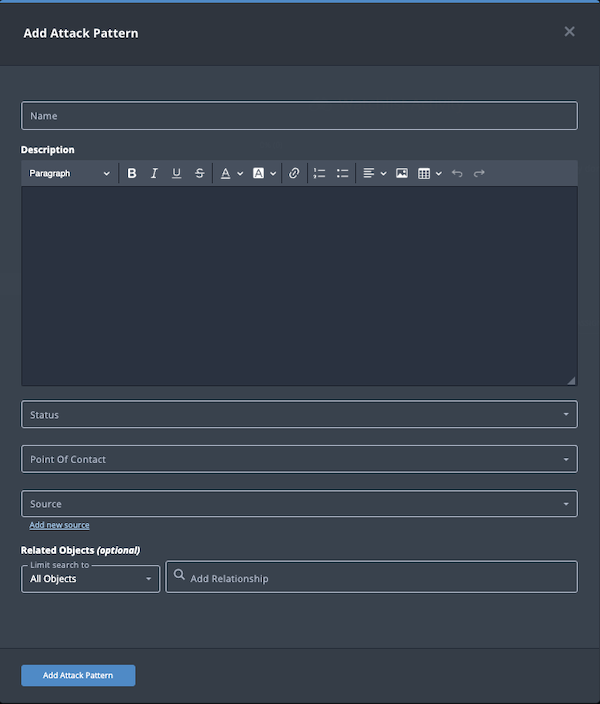
- Populate the following fields:
Field Description Name Add an attack pattern name. Description Enter a brief description of the attack pattern. Any description you add during object creation defaults to a Source value of ThreatQ System.
Status Optional field. Click the Status field to assign a status to the attack pattern object. Attack pattern statuses are configured in the Object Statuses tab in the Object Management page. If none are configured, this field is not displayed.
Point of Contact Optional field. Click the field to select the ThreatQ display name of the point of contact for the attack pattern. Source Select a Source from the dropdown list provided. You can also click the Add a New Source option if the desired source is not listed in the drop-down list. If administrators have enabled TLP view settings, you can select a TLP label for the new source in the dropdown list provided. See the Traffic Light Protocol (TLP) topic for more information on TLP schema. - Select any Related Objects you need to link to the attack pattern. This field is optional.
- Click Add Attack Pattern.
Adding Context
See the About Object Details section and its topics for details on adding context to an object such as adding sources, attributes, and related objects.
Editing an Attack Pattern
- Locate and click on the attack pattern.
The Attack Pattern's detail page opens.
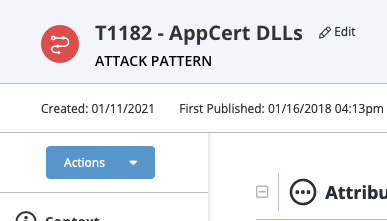
- Click on Edit next to the Attack Pattern's name.
The Edit Attack Pattern dialog box opens.
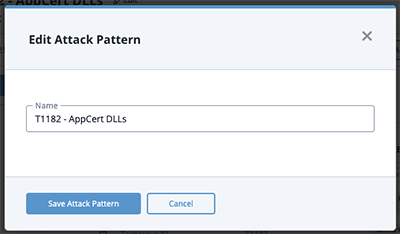
- Make the desired change to the Attack Pattern name and click Save Attack Pattern.
Changing the Point of Contact
Default ThreatQ Role: Administrative, Maintenance, or Primary Contributor
Custom Role - Action Permissions: Objects & Context - Objects, Individual Object Context & Actions - Point of Contact
- Locate and click the system object.
- From the object details page, click the Point of Contact field.
- Use the field's scroll or search option to locate and select a new user as the object's point of contact or to change the point of contact to Unassigned.
Deleting an Attack Pattern
- Locate and click on the Attack Pattern.
The Attack Pattern's details page opens.

- Click on the Actions menu and select Delete Attack Pattern.
A confirmation dialog box appears.
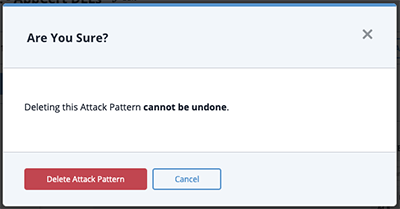
- Click on Delete Attack Pattern.