Getting Started With ThreatQ
As you begin to use any new application, it is always best to think about your goals and to begin your configuration and use with these goals in mind. This Getting Started guide is a compilation of recommendations for making the most of your new ThreatQ Platform installation and laying the foundations for effective threat intel management.
Documentation and Training Resources
ThreatQuotient provides training and documentation resources for all new and existing customers. These resources provide you with an overview of the product as a whole as well as focused content based on your role.
ThreatQ Documentation
The ThreatQ Help Center, accessible from the ThreatQ Help Menu, is your go-to resource for all product documentation, release notes, integration guides, and developer resources.
The topics available on this site reflect the most current version of ThreatQ. User Guides, in the form of PDFs, are available for all major ThreatQ versions on each topic. In addition, you can stay up-to-date on ThreatQ product changes by subscribing to Product Release and Integration Release emails.
ThreatQ Training
ThreatQ Academy consists of a dedicated team of experts and a portfolio of training resources that allow you to learn and explore ThreatQ via virtual instructor-led, onsite instructor-led, and online self-paced training.

These learning solutions cover a wide range of topics including:
- ThreatQ Security and Intelligence Operations
- ThreatQ Integrations Development Training (instructor-led only at this time)
- ThreatQ Platform Administration
- ThreatQ Certified Partner Training
- Cyber Threat Intelligence Foundations
In addition to standard, foundational courses, the Training team can provide custom-tailored learning solutions to meet virtually any operational need.
To gain the full benefit of your training, we recommend you:
- Review the ThreatQ Academy catalog.
- Determine which classes are appropriate for each employee’s role.
- Plan for new employee training and ongoing training needs.
Reach out to ThreatQuotient Sales or Customer Success to schedule training for your employees.
Support Resources
ThreatQuotient’s dedicated Customer Support team provides the assistance you need via the communication method you prefer such as:
Our primary support hours are 12:00AM to 5:00 PM ET Monday through Friday except for holidays. And the Rhino Support AI is available to assist with product questions 24/7.
To expedite your Support interactions, please provide the following information, if available:
- Issue Description - Include information on actual behavior and expected behavior as well as your current application and integration versions if relevant. To focus troubleshooting, it’s also helpful to report one issue per ticket.
- Recent Changes - Describe any recent internal/external changes to your environment such as network changes or upgrades.
- Documentation - Provide error logs and screenshots
- Urgency - Specify issue urgency and describe how it impacts your business operations including examples.
- Point of Contact - Identify a primary and secondary point of contact for the issue and list any communication limits (i.e. not available for calls after 6 PM).
You can also send your new feature requests to ThreatQuotient Support. For these requests, you will want to describe the business need and a use case.
Environment Specifications
One of the keys to success with any threat intelligence platform is understanding and managing your data storage needs. As such, we strongly recommend you verify that your environment meets ThreatQ’s system requirements ThreatQ's system requirements before you enter production and periodically reassess to ensure your environment keeps pace with your data needs.
ThreatQ Backups
Before you begin using ThreatQ in production, make a plan for how you will protect your data with data backups:
- Frequency - At a minimum, you will want to perform nightly backups as well as a backup before each upgrade.
- Time - You can run these backups during a scheduled maintenance window or you can run an online backup that allows your users to work in ThreatQ during the backup.
Online backups cover your database but do not include a Solr backup.
- Storage - We recommend storing backups on a mounted drive or file location rather than the local file system.
In addition to planning for routine data protection, you should also document a disaster recovery plan to prepare for contingencies.
User Access
Before you add user accounts to ThreatQ, we recommend you determine, identify, and implement your desired authentication method(s):
- Local authentication
- 2-step verification
- LDAP authentication
- SAML authentication
- SSL client certificate authentication
If you plan to use local authentication with or without 2-step verification, you can proceed to create user accounts immediately. If you plan to use any of the other authentication methods listed above, we recommend you implement the authentication method and enable it in ThreatQ before creating local user accounts.
User Permissions
In keeping with the principle of least privilege (PoLP), we recommend that you set up users with the minimum access privileges required to perform their job functions. ThreatQ supports the following access levels:
- Administrator - Configure at least one local login with administrator privileges. And, set up an Admin or Maintenance user account to access the ThreatQ Monitoring Platform.
- Maintenance
- Contributor
- Read-Only
You should avoid tying ThreatQ integrations to an individual user’s account. For instance, create an user account named integrations_user to install integrations. This future-proofs the user account against employee turnover. In addition, add a group email to the user profile so that multiple employees receive email notifications about the integration. If a login/password is required on the provider side, you might also want to specify a non-user specific account.
ThreatQ also allows you to control access to data collections, dashboards, and investigations by assigning sharing permissions
Adding Data
To begin using ThreatQ to manage and enrich your threat intel, you must configure integrations that allow you to ingest data into the Threat Library. ThreatQuotient recommends you configure the following open source integrations (OSINT):
The ThreatQ Marketplace allows you to download these integrations and others that support the ingestion of additional data feeds.
After you download an integration, you can use the My Integrations page to install and configure it.
ThreatQ publishes frequent updates and new integrations each month. We recommend you periodically review your installed integrations and any associated filters to make sure they are providing the intel you need.
As with the ThreatQ platform, we recommend you upgrade to the most recent integration version after thorough user acceptance and soak testing.
Managing Your Data
The key to data management in ThreatQ is maintaining focus. You need to hone in on the threats that affect your organization and filter out noise. ThreatQ provides many tools for doing just that. In the early days of your implementation, we recommend you focus on Dashboards, the Threat Library, Scoring, and Threat Library Audits.
Dashboards
Each time you log into ThreatQ, your initial view is the Overview Dashboard.
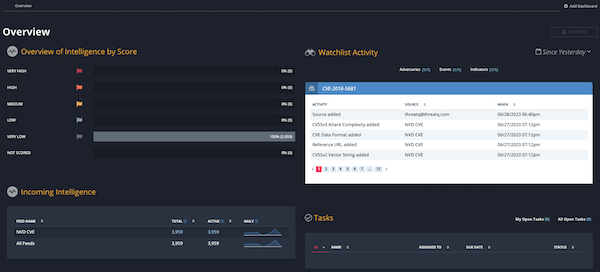
This dashboard consists of four widgets, Overview of Intelligence by Score, Incoming Intelligence, Watchlist Activity, and Tasks. As a whole, these widgets give you a high-level view of your threat intel and system activity.
You can also create your own custom dashboards that you can share with other users. These custom dashboards pull data from saved Threat Library searches known as Data Collections.
The data is then displayed using system widgets that allow you to control the data visualization and the frequency of updates.
Threat Library
The Threat Library is the central hub for organizing, managing and searching your threat intel. It consists of:
- Search fields - These fields allow you to filter and search your Threat Library data as well as save Threat Library searches as data collections.
- Object type menu - This menu allows you to view the data in your Threat Library by object type, such as indicator, adversary, or malware.
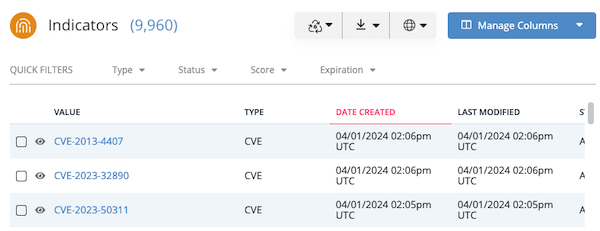
- Results list - The results list displays the objects that match your current search and object type selection. You can customize this view by adding or removing columns. In addition, you can export your results to a CSV or STIX file as well as delete/update multiple objects in the results list.
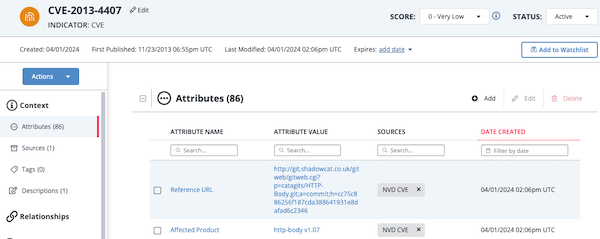
- Object details view - You can click an item in your results list to view its object details page and update it.
Threat Library Audits
With the volume of threat activity and intel, one of the biggest challenges customers face is filtering out noise to maintain focus. ThreatQ provides several methods for methods that support automatic and periodic Threat Library audits.
We recommend that you set up a review schedule for your system objects and use bulk delete processes and/or a data retention policy to remove noise. In addition, you can configure CDF filters to ensure the data you ingest is more relevant to your objectives and set up indicator expiration policies to automatically deprecate stale intelligence based on source, indicator type, and age.
Scoring
ThreatQ’s automatic scoring system allows you to focus on relevant threat intelligence by creating scoring rules for ingested objects by indicator type, indicator source, attributes, and adversary relationships.
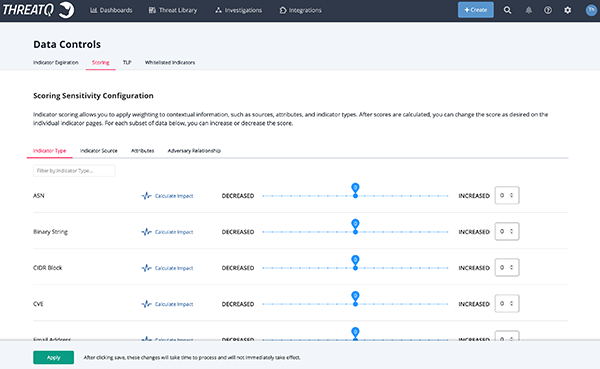
Optimizing scoring is an ongoing effort. You should periodically review and update your scoring to reflect changes in your industry and organization such as the addition of new intelligence feeds or tools.
Monitoring ThreatQ
At minimum, we recommend the following methods for monitoring ThreatQ system health:
- Use the ThreatQ Monitoring Platform to monitor system resources and logs.
- Ensure your internal network monitoring system and Ops team monitor the ThreatQ platform. This monitoring should include platform health (storage and CPU utilization) as well as Critical System process monitoring.
- Use
/healthURLs for simple monitoring. - Ensure that at least one user receives in app or email feed health notifications.
- Keep your ThreatQ version current by upgrading to the latest release after user acceptance and soak testing.
Additional Resources
Implementing a threat intelligence platform is a challenging effort. As you go through this process, ThreatQuotient Customer Success and Customer Support are available to assist with any questions.