Commands
This topic contains a list of commands you can execute from ThreatQ's command line interface (CLI). These commands are grouped by their primary area of impact, Integration, System Object, or System-wide.
Integration Commands
Add/Upgrade CDF
ThreatQuotient recommends that you use the user interface to add or upgrade integrations.
Use the steps below to add or upgrade a Configuration Driven Feed (CDF). The command creates connectors for each feed defined in the feed definition file.
install a CDF - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
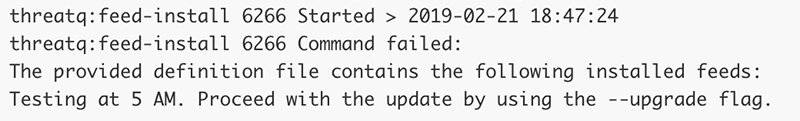
sudo php artisan threatq:feed-install <Feed Definition File>The application will notify you if the feed(s) in the feed definition file already exists in the system and will cancel the installation. See the Upgrade a CDF and Changes in User Configurations sections below for more information.
-
Bring the application out of maintenance mode - see the Maintenance Mode section.
install a CDF - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:feed-install /var/lib/threatq/misc/<Feed Definition File>The application will notify you if the feed(s) in the feed definition file already exists in the system and will cancel the installation. See the Upgrade a CDF and Changes in User Configurations sections below for more information.

-
Bring the application out of maintenance mode - see the Maintenance Mode section.
This command can be used to update a feed's Category and Namespace. If the category exists on the appliance, the command updates both fields and links the feed to the designated category. ThreatQ confirms that the defined category exists before completing the update command. If the category does not exist, ThreatQ does not update the feed.
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
sudo php artisan threatq:feed-install <Feed Definition File> --upgrade -
Bring the application out of maintenance mode - see the Maintenance Mode section.
Upgrade a CDF - ThreatQ v6
This command can be used to update a feed's Category and Namespace. If the category exists on the appliance, the command updates both fields and links the feed to the designated category. ThreatQ confirms that the defined category exists before completing the update command. If the category does not exist, ThreatQ does not update the feed.
-
SSH to your ThreatQ installation.
-
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:feed-install /var/lib/threatq/misc/<Feed Definition File> --upgrade -
Bring the application out of maintenance mode - see the Maintenance Mode section.
Changes in User Configurations
When upgrading an existing feed using the --upgrade flag, the application will compare the existing version of the feed with the new version for differences in the user configuration. If a difference is detected, the application will inform you that the current user configuration for that feed will be overwritten. The application will require user input to continue with the feed upgrade.

ThreatQ recommends that you create a copy of the existing configuration values before proceeding with the upgrade.
Command Flag Help - ThreatQ v5
You can also see a full list of command flags using the following command while under the /var/www/api directory:
Command Flag Help - ThreatQ v6
View Feed Queues
Before upgrading a feed, ThreatQ recommends that you allow the previous implementation of the feed to complete processing downloaded data to avoid any data loss. The threatq:list-queues command allows you to confirm that the feed's queues have been cleared.
View Feed Queues - ThreatQ v5
- Run the following command:
/var/www/api/artisan threatq:list-queues -p feeds
- Locate and confirm that the feed’s Indicators and Reports rows display a value of "0" for the Messages Ready and Messages Unacknowledged columns.
The queues should be cleared, reporting 0 values, before proceeding with the update.
This command is deprecated in ThreatQ v6
System Object Commands
Delete Adversary Descriptions
Due to the introduction of multiple description support, this command is not needed by customers on ThreatQ v5.21 or later.
The adversary-descriptions-cleanup command allows you to delete duplicated adversary descriptions and orphaned adversary description values. By default, the adversary-descriptions-cleanup command deletes 1,000 adversary descriptions at a time. If there are performance concerns with deleting this many adversaries at a time, you can use the optional delete-limit parameter to specify an integer value as the limit for the number of adversary descriptions deleted at a time. For example, you can run the command with a delete-limit of 100 to delete 100 orphaned/duplicate adversary descriptions at a time.
Setting the delete-limit parameter too high may hinder performance.
Delete Adversary Descriptions - ThreatQ v5
-
SSH to your ThreatQ installation.
- To delete adversary descriptions in batches of 1,000, run the following command:
sudo /var/www/api/artisan threatq:adversary-descriptions-cleanup
-
To specify the number of adversary descriptions to be deleted at a time, run the following command:
sudo /var/www/api/artisan threatq:adversary-descriptions-cleanup --delete-limit numberThe number variable above represents the maximum number of adversary descriptions you want to delete at a time. The following example command deletes a maximum of 100 adversary descriptions at a time.Example:
sudo /var/www/api/artisan threatq:adversary-descriptions-cleanup --delete-limit 100
This command is deprecated in ThreatQ v6
Merge Attributes
The Attribute Management page also allows you to merge attribute keys.
The Merge Attributes command allows you to merge an existing attribute to a new or different existing attribute name. This is useful when an attribute key is outdated or entered incorrectly.
You can add the --source parameter to only merge attributes that have a specific source(s). If the source identified in the command does not exist, or the parameter is not included, the command merges all OLD-NAME attributes into MERGE-NAME.
If the MERGE-NAME attribute in the command does not exist, it is automatically created upon executing the command.
Merge Attributes - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Place the application into maintenance mode - see the Maintenance Mode topic.
-
Run the following command:
sudo php artisan threatq:merge-attributes --old-name='OLD-NAME' --merge-name='MERGE-NAME' --source='SOURCE'The
--sourceparameter is optional. You can omit this parameter in order to target all attributes with theOLD-NAME. -
Bring the application out of maintenance mode - see the Maintenance Mode topic.
Merge Attributes - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Place the application into maintenance mode - see the Maintenance Mode topic.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:merge-attributes --old-name='OLD-NAME' --merge-name='MERGE-NAME' --source='SOURCE'The
--sourceparameter is optional. You can omit this parameter in order to target all attributes with theOLD-NAME. - Bring the application out of maintenance mode - see the Maintenance Mode topic.
Merge Attribute without using --source
The attribute Cuontry is merged into the Country attribute. So if you have an instance of this attribute name (with value), Cuontry: US, on an object, after running the command, the attribute value would appear as Country: US on that object.
ThreatQ v5 Example
ThreatQ v6 Example
Merge Attribute using --source
The attribute Cuontry , if it has a source of CrowdStrike, is merged into the Country attribute. So if you have an instance of this attribute name (with value), Cuontry: US, on an object, after running the command, the attribute value appears as Country: US on that object.
ThreatQ v5 Example
ThreatQ v6 Example
The attribute Cuontry , if it has a source of CrowdStrike, is merged into the Country attribute. So if you have an instance of this attribute name (with value), Cuontry: US, on an object, after running the command, the attribute value appears as Country: US on that object.
Merge Attribute using --source (multiple sources)
The attribute Cuontry , if it has a source of CrowdStrike or McAfee ATD, is merged into the Country attribute. So if you have an instance of this attribute name (with value), Cuontry: US, on an object, after running the command, the attribute value appears as Country: US on that object.
ThreatQ v5 Example
ThreatQ v6 Example
Source Consolidation
Use the steps below to consolidate/deduplicate similarly named sources and to remove unused sources from the ThreatQ application. A source that have been removed or merged will have its data mapped to a new source.
The command does not require recalculation of scoring.
Source Consolidation - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Place the application into maintenance mode - see the Maintenance Mode topic.
-
Run the following command:
sudo php artisan threatq:consolidate-sources -
Bring the application out of maintenance mode - see the Maintenance Mode topic.
Source Consolidation - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Place the application into maintenance mode - see the Maintenance Mode topic.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:consolidate-sources -
Bring the application out of maintenance mode - see the Maintenance Mode topic.
Example Scenario:
- User manually adds ABC as a source.
- User enables ABC.
There are now two ABC sources in the system. - User runs consolidation command.
- The application merges the sources and remaps any items linked to the correct source.
Source Merge
Use the steps below to merge a user-created source (source origin) with another source (source destination). After merging, the source origin is deleted and source changes are reflected in the Audit log (Example: Source A becomes Source B).
The command does not affect date stamps nor does it require a recalculation of scoring.
Source Merge - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
sudo php artisan threatq:merge-sources --origin-source=“<source a>” --destination-source=“<source b>” -
Bring the application out of maintenance mode - see the Maintenance Mode section.
Source Merge - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:merge-sources --origin-source="<source a>" --destination-source="<source b>" -
Bring the application out of maintenance mode - see the Maintenance Mode section.
| Example Scenario | Details |
|---|---|
| Merge user-created source (origin source) with a system source (destination source). |
|
| Merge system source (origin source) with a user-created source (destination source). |
|
| Merge user-created source (origin source) with a system source (destination source) with duplicate records. |
|
| Merge user-created source (origin source) with a system source (destination source) with an assigned TLP. |
|
Convert TLP
Use the following command to update all object sources and object attribute sources that have Traffic Light Protocol (TLP) stored as an object attribute. This command will not affect TLP attributes that have already been converted. Users should use this command for new incoming data, such as migrating data into the system, which has TLP attributes but no TLP set.
Convert TLP - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
sudo php artisan threatq:convert-tlp-attributes -
Bring the application out of maintenance mode - see the Maintenance Mode section.
Convert TLP - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:convert-tlp-attributes -
Bring the application out of maintenance mode - see the Maintenance Mode section.
Use Scenarios:
Object has one or more TLP Attributes with an invalid TLP (not currently in the TLP options)
- If the Object has just one TLP Attribute - none of its Sources or Attribute Sources will be updated.
- If the Object has more than one TLP Attribute - any Sources or Attribute Sources that match the Attribute Source of the TLP Attribute will not be updated.
Object has a single valid TLP Attribute
-
All of the Object Sources and Object Attribute Sources will be updated to match the value of the TLP Attribute.
Object has multiple TLP Attributes
- Each TLP Attribute will be evaluated separately.
- Any Object Sources or Object Attribute Sources whose source matches that of the TLP Attribute will be updated with the value of the TLP Attribute.
- Any Object Sources or Object Attribute Sources whose sources do not match will not be updated.
- If there are no matches at all between the source of the TLP Attribute and any of the Object Sources or Object Attribute Sources, a new Object Source will be added using the Attribute's TLP value. Each of the Object Attributes will receive a new Object Attribute Source with the TLP value as well.
Update TLP Designations
Use the following command to update the Traffic Light Protocol (TLP) schema for an object source, object attribute source, and object description source with the source's default TLP designation.
See Traffic Light Protocol (TLP) topic for more details on setting a default TLP designation for a source.
You should use this command to update your system to match default TLP configurations, specifically attributes and sources that were added to the Threat Library prior to the release of the TLP feature introduced with ThreatQ 4.11. This command will override previous TLP schema settings for a source including ones set by users. You are prompted to confirm the action after entering the command. All updates are recorded in the audit log.
The command updates using the default TLP designation. If a default designation is set to None, all references to the source will be updated to None.
Update All Sources - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Run the following command:
sudo php artisan threatq:apply-tlp-defaultsThe application will warn you that this action is not reversible and will require user confirmation before proceeding. - Type Yes to confirm and proceed with the action.
The application will automatically be placed into maintenance mode. After the command has completed its operation, the application will automatically be brought out of maintenance mode.
Update All Sources - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:apply-tlp-defaultsThe application will warn you that this action is not reversible and will require user confirmation before proceeding. - Type Yes to confirm and proceed with the action.
The application will automatically be placed into maintenance mode. After the command has completed its operation, the application will automatically be brought out of maintenance mode.
Update a Specific Source - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Run the following command:
sudo php artisan threatq:apply-tlp-defaults --sources="<your source>"You can apply the command to multiple sources by listing the sources in a comma-delimited format.
The application will warn you that this action is not reversible and will require user confirmation before proceeding.
Example: --sources="CrowdStrike, AlienVault" - Type Yes to confirm and proceed with the action.
The application will automatically be placed into maintenance mode. After the command has completed its operation, the application will automatically be brought out of maintenance mode.
Update a Specific Source - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:apply-tlp-defaults --sources="<your source>"You can apply the command to multiple sources by listing the sources in a comma-delimited format.
The application will warn you that this action is not reversible and will require user confirmation before proceeding.
Example: --sources="CrowdStrike, AlienVault" - Type Yes to confirm and proceed with the action.
The application will automatically be placed into maintenance mode. After the command has completed its operation, the application will automatically be brought out of maintenance mode.
Indicator and Signature Statuses Overrides
The following commands allow you to change status handling on indicators and signatures updated via feed ingestion. When you run the artisan command to enable this functionality:
- An existing indicator’s status is overridden with the default status configured in the CDF.
- An existing signature’s status is overridden with the default status of Active.
A second artisan command disables this functionality and returns your system to default handling of indicator and signature expiration updates.
Enable Indicator and Signature Status Overrides - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api - Run the following commands:
sudo php artisan threatq:configuration --key consumer.connectors_override_status --value 1
sudo php artisan cache:clear
Enable Indicator and Signature Status Overrides - ThreatQ v6
-
SSH to your ThreatQ installation.
- Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:configuration --key consumer.connectors_override_status --value 1 kubectl exec –n threatq --stdin --tty deployment/api-schedule-run -- ./artisan cache:clear
Disable Indicator and Signature Status Overrides - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api - Run the following commands:
sudo php artisan threatq:configuration --key consumer.connectors_override_status --delete
sudo php artisan cache:clear
Disable Indicator and Signature Status Overrides - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Run the following commands:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:configuration --key consumer.connectors_override_status --delete kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan cache:clear
System-Level Commands
Airgap Import
See the threatq:sync-import topic.
Airgap Export
See the threatq:sync-export topic.
Allow Cross-Origin Resource Sharing for Specific Hostnames
ThreatQ's explicit domain access restrictions prevent cross-origin resource sharing (CORS) attacks. This allows API requests from ThreatQ and third-party integrations but blocks cross-origin JavaScript requests unless you use the following command to specifically configure a list of allowed hosts.
Allow Cross-Origin Resource Sharing for Specific Hostnames - ThreatQ v5
-
SSH to your ThreatQ installation.
- Run the following command:
sudo php artisan threatq:configuration --key=cors.allowed_hosts --value https://www.site-a.com,https://www.site-b.com
The value parameter allows you to enter a single domain or multiple domains separated by a comma.
Single Domain Example:
sudo php artisan threatq:configuration --key=cors.allowed_hosts --value https://www.example.comMultiple Domains Example:
sudo php artisan threatq:configuration --key=cors.allowed_hosts --value https://www.example.com,https://www.my-allowed-host.com
Allow Cross-Origin Resource Sharing for Specific Hostnames - ThreatQ v6
-
SSH to your ThreatQ installation.
- Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:configuration --key=cors.allowed_hosts --value https://www.site-a.com,https://www.site-b.com
The value parameter allows you to enter a single domain or multiple domains separated by a comma.
Single Domain Example:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:configuration --key=cors.allowed_hosts --value https://www.example.comMultiple Domains Example:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:configuration --key=cors.allowed_hosts --value https://www.example.com,https://www.my-allowed-host.com
Disable Export Logging
The exports.disable_logging configuration option allows you to disable export logging. However, if a differential parameter is included as a URL parameter. the export logging process continues regardless of this configuration.
Disable Export Logging - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Run the following command to disable export logging:
sudo php artisan threatq:configuration --key exports.disable_logging --value 1 - To turn logging back on, run the following command:
sudo php artisan threatq:configuration --key exports.disable_logging --value 0
Disable Export Logging - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Run the following command to disable export logging:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:configuration --key exports.disable_logging --value 1 - To turn logging back on, run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:configuration --key exports.disable_logging --value 0
LDAP Diagnostic Searches
This command runs LDAP diagnostic searches for authentication and authorization using the LDAP configuration stored in the database. Methods for searching are contained in try/catch blocks so that stack traces are printed to the debug output. You can run this command with or without the --test-user parameter. This parameter allows you to use a known username on the LDAP server to test authentication and group searching.
The test connection and bind aspects of this command work for the anonymous LDAP configuration. However, all other aspects, including test user authentication and group searching, only work with the authenticated bind LDAP configuration.
This command has only been tested and confirmed for use with AD server configurations.
To perform basic connect and bind authentication tests - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api - Run the following command:
sudo php artisan threatq:ldap-debug
To perform basic connect and bind authentication tests - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:ldap-debug
To perform basic connect and bind authentication as well as authentication with the test username - ThreatQ v5
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api - Run the following command:
sudo php artisan threatq:ldap-debug --test-user=username
Example:
sudo php artisan threatq:ldap-debug --test-user=administrator -
When prompted, enter the username's password.
Regardless of whether authentication is successful, an attempt is made to pull the LDAP user entry for the username. If authentication is successful, a group search (authorization) is performed as well.
To perform basic connect and bind authentication as well as authentication with the test username - ThreatQ v6
-
SSH to your ThreatQ installation.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:ldap-debug --test-user=usernameExample:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:ldap-debug --test-user=administrator -
When prompted, enter the username's password.
Regardless of whether authentication is successful, an attempt is made to pull the LDAP user entry for the username. If authentication is successful, a group search (authorization) is performed as well.
Auto Configuration MariaDB Command
The Auto Configuration MariaDB command will execute a script that will update your MariaDB configurations based on your available system resources. The script is executed automatically during the platform install/upgrade process but can be executed manually by using the command below. You will typically use this command after making a change to the size of your ThreatQ instance or system memory.
MariaDB will need to be restarted after the script has completed its updates.
This command is deprecated in ThreatQ v6
System ThreatQ Purge
Read this section carefully before running the ThreatQ Purge Command. After running this command, your threat intelligence data cannot be recovered.
The ThreatQ Purge command will permanently delete all object-related threat intelligence data from your ThreatQ installation, including audit logs. It will maintain any configuration-related settings, such as expiration, scoring, and so on.
Running the ThreatQ Purge Command - ThreatQ v5
The ThreatQ Purge command will permanently delete all object-related threat intelligence data from your ThreatQ installation, including audit logs. It will maintain any configuration-related settings, such as expiration, scoring, and so on.
-
SSH to your ThreatQ installation.
-
Navigate to the api directory using the following command:
cd /var/www/api -
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
sudo php artisan threatq:purge-threat-intelligence - You will be presented the following prompt:
You are about to erase all of your data, are you sure?
- Enter Yes or No.
-
Bring the application out of maintenance mode - see the Maintenance Mode section.
Running the ThreatQ Purge Command - ThreatQ v6
The ThreatQ Purge command will permanently delete all object-related threat intelligence data from your ThreatQ installation, including audit logs. It will maintain any configuration-related settings, such as expiration, scoring, and so on.
-
SSH to your ThreatQ installation.
-
Place the application into maintenance mode - see the Maintenance Mode section.
-
Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:purge-threat-intelligence - You will be presented the following prompt: You are about to erase all of your data, are you sure?
- Enter Yes or No.
-
Bring the application out of maintenance mode - see the Maintenance Mode section.
Reset User Password
You cannot reset a SAML or LDAP user's password from the command line.
If you have root access to your ThreatQ installation, you can reset any user's password from the command line.
Reset User Password - ThreatQ v5
- SSH to your ThreatQ installation as root.
- Navigate to the api directory:
cd /var/www/api - Run the following command:
sudo php artisan threatq:password-reset - At the prompt, enter the email address or username for the user whose password you are resetting.
- At the prompt, enter the new password.
- At the prompt, re-enter the new password to confirm.
Reset User Password - ThreatQ v6
- SSH to your ThreatQ installation as root.
- Run the following command:
kubectl exec --namespace threatq --stdin --tty deployment/api-schedule-run -- ./artisan threatq:password-reset
- At the prompt, enter the email address or username for the user whose password you are resetting.
- At the prompt, enter the new password.
- At the prompt, re-enter the new password to confirm.