Flashpoint Ignite CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 3.4.1 |
| Compatible with ThreatQ Versions | >= 5.12.0 |
| Support Tier | ThreatQ Supported |
Introduction
The Flashpoint Ignite CDF delivers actionable threat intelligence in the form of compromised Adversaries, Attack Patterns, Compromised Cards, Indicators, Malware, Reports and Vulnerabilities.
The integration ingests threat intelligence data from the following feeds:
- Flashpoint Ignite - ingests compromised Reports and any Indicators, Adversaries, Malware, Vulnerabilities and Attack Patterns.
- Flashpoint Ignite Community Ransomware - requests article and conversation data gathered by Flashpoint Ignite regarding Ransomware.
- Flashpoint Ignite Indicators - ingests indicators requested from Flashpoint Ignite.
- Flashpoint Ignite Media Sources - ingests media data that has been analyzed by Flashpoint Ignite Optical Character Recognition (OCR) process.
- Flashpoint Ignite Fraud Mitigation - ingests compromised credit cards from illicit communities and data breaches.
The integration ingests the following system object types:
- Adversaries
- Adversary Attributes
- Attack Patterns
- Compromised Card (custom object)
- Indicators
- Indicator Attributes
- Malware
- Reports
- Vulnerabilities
Prerequisites
The Flashpoint Ignite CFD requires the following:
- Flashpoint Ignite API Key.
- Compromised Card custom object.
Compromised Card Custom Object
The integration requires the Compromised Card custom object.
Use the steps provided to install the custom object.
When installing the custom objects, be aware that any in-progress feed runs will be cancelled, and the API will be in maintenance mode.
- Download the integration bundle from the ThreatQ Marketplace.
- Unzip the bundle and locate the custom object files.
The custom object files will typically consist of a JSON definition file, install.sh script, and a images folder containing the svg icons.
- SSH into your ThreatQ instance.
- Set your install pathway environment variable. This command will retrieve the install pathway from your configuration file and set it as variable for use during this installation process.
INSTALL_CONF="/etc/threatq/platform/install.conf" if [ -f "$INSTALL_CONF" ]; then source "$INSTALL_CONF" fi MISC_DIR="${INSTALL_BASE_PATH:-/var/lib/threatq}/misc"
- Navigate to the tmp folder using the environment variable:
cd $MISC_DIR
- Upload the custom object files, including the images folder.
The directory structure should resemble the following:
- install.sh
- <custom_object_name>.json
- images (directory)
- <custom_object_name>.svg
- Run the following command:
kubectl exec -it deployment/api-schedule-run -n threatq -- sh /var/lib/threatq/misc/install.sh /var/lib/threatq/misc
The installation script will automatically put the application into maintenance mode, move the files to their required directories, install the custom object, update permissions, bring the application out of maintenance mode, and restart dynamo.
- Delete the install.sh, definition json file, and images directory from step 6 after the object has been installed as these files are no longer needed.
Use the following steps to install the custom objects in ThreatQ v5:
- Download the integration zip file from the ThreatQ Marketplace and unzip its contents.
- SSH into your ThreatQ instance.
- Navigate to tmp directory:
cd /tmp/
- Create a new directory:
mkdir ignite_cdf
- Upload the compromised_card.json and install.sh script into this new directory.
- Create a new directory called images within the ignite_cdf directory.
mkdir images
- Upload the compromised_card.svg.
- Navigate to the /tmp/ignite_cdf.
The directory should resemble the following:
- tmp
- ignite_cdf
- compromised_card.json
- install.sh
- images
- compromised_card.svg
- ignite_cdf
- tmp
- Run the following command to ensure that you have the proper permissions to install the custom object:
chmod +x install.sh
- Run the following command:
sudo ./install.sh
You must be in the directory level that houses the install.sh and json files when running this command.
The installation script will automatically put the application into maintenance mode, move the files to their required directories, install the custom object, update permissions, bring the application out of maintenance mode, and restart dynamo.
- Remove the temporary directory, after the custom object has been installed, as the files are no longer needed:
rm -rf ignite_cdf
Installation
The CDF requires the installation of the Compromised Card custom object before installing the actual CDF. See the Prerequisites chapter for more details. The custom object must be installed prior to installing the CDF. Attempting to install the CDF without the custom object will cause the CDF install process to fail.
Perform the following steps to install the integration:
The same steps can be used to upgrade the integration to a new version.
- Log into https://marketplace.threatq.com/.
- Locate and download the integration zip file.
- Extract the contents of the zip and install the required Compromised Card custom object.
- Navigate to the integrations management page on your ThreatQ instance.
- Click on the Add New Integration button.
- Upload the integration yaml file using one of the following methods:
- Drag and drop the file into the dialog box
- Select Click to Browse to locate the integration on your local machine
- Select the individual feeds to install, when prompted, and click Install.
ThreatQ will inform you if the feed already exists on the platform and will require user confirmation before proceeding. ThreatQ will also inform you if the new version of the feed contains changes to the user configuration. The new user configurations will overwrite the existing ones for the feed and will require user confirmation before proceeding.
- The feed(s) will be added to the integrations page. You will still need to configure and then enable the feed.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Flashpoint Ignite Parameters
Parameter Description API Key Your Flashpoint API Key. Parse for Selected Indicators Select the types of indicators to parse out of the report body. Options include: - CVEs
- MD5 Hashes
- SHA-1 Hashes
- SHA-256 Hashes
- SHA-512 Hashes
- IP Addresses
Save Actor Profile As Determines whether a Report containing a Tag with an 'Actor Profile' value should be ingested as an Adversary or as an Intrusion Set. Enable SSL Verification When checked, validates the host-provided SSL certificate. This option is enabled by default. Disable Proxies Enable this option if the feed should not honor proxies set in the ThreatQ UI.
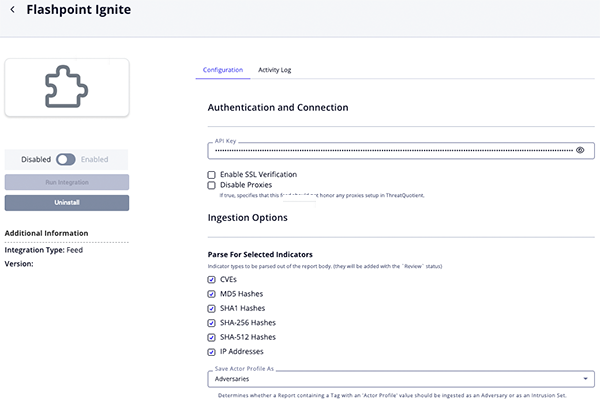
Flashpoint Ignite Community Ransomware Parameters
Parameter Description API Key Your Flashpoint API Key. Related IoCs Filter Select the IoCs to ingest into the ThreatQ platform. Options include: - Email Address
- IP Address
- FQDN
Append Translation to the Description If a translation is available, it will added to the description. Search Query Optional - This query allows you to specify additional keywords that the returned result must contain. Enable SSL Verification When checked, validates the host-provided SSL certificate. This option is enabled by default. Disable Proxies Enable this option if the feed should not honor proxies set in the ThreatQ UI.
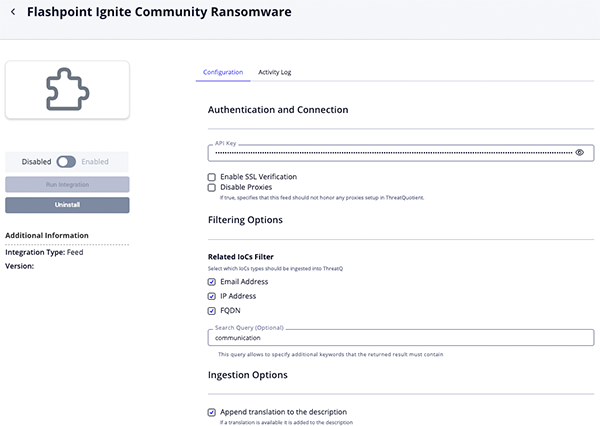
Flashpoint Ignite Indicators Parameters
Parameter Description API Key Your Flashpoint API Key. Indicator Type Filter Select the types of indicators to ingest into ThreatQ. Options include: - MD5 Hashes (default)
- SHA-1 Hashes (default)
- SHA-256 Hashes (default)
- SHA-512 Hashes (default)
- URLs (default)
- Domains (default)
- IP Address (default)
- Email Addresses (default)
Flashpoint Sources Select which Flashpoint-provided sources to ingest into ThreatQ. Options include: - Flashpoint Analyst (default)
- Flashpoint APT (default)
- Flashpoint Collab (default)
- Flashpoint Detection (default)
- Flashpoint Extraction (default)
- Flashpoint Infected Hosts (default)
Minimum Score Filter indicators by their minimum score tier. Options include: - Informational (default)
- Suspicious
- Malicious
Enable SSL Verification When checked, validates the host-provided SSL certificate. This option is enabled by default. Disable Proxies Enable this option if the feed should not honor proxies set in the ThreatQ UI.
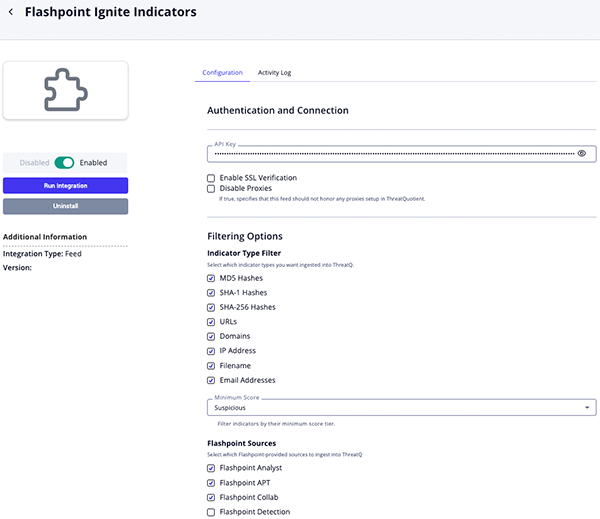
Flashpoint Ignite Media Sources Parameters
Parameter Description API Key Your Flashpoint API Key. Search Query Optional - This query allows to specify additional keywords that the returned media must contain. Context Filter Select the pieces of enrichment context to ingest. Options include: - Source
- Source Type
- Platform URL
- Tags
Enable SSL Verification When checked, validates the host-provided SSL certificate. This option is enabled by default. Disable Proxies Enable this option if the feed should not honor proxies set in the ThreatQ UI.
Flashpoint Ignite Card Fraud Mitigation Parameters
Parameter Description API Key Your Flashpoint API Key. BIN Filter Optional - The BINs that you want to ingest compromised credit cards for. Context Filter Select which pieces of context to bring into ThreatQ with each compromised card. Options include: - Account Number
- BIN
- CVV
- Last 4 Digits
- Site
- Release Name
- Owner First Name
- Owner Full Name
- Sale Price
- Source Type
- Source
- Data Type
- Last Observed At
- First Observed At
- Expiration
- Owner City
- Owner Region
- Owner Country
- Owner Zip Code
- Site Uri
Enable SSL Verification When checked, validates the host-provided SSL certificate. This option is enabled by default. Disable Proxies Enable this option if the feed should not honor proxies set in the ThreatQ UI. 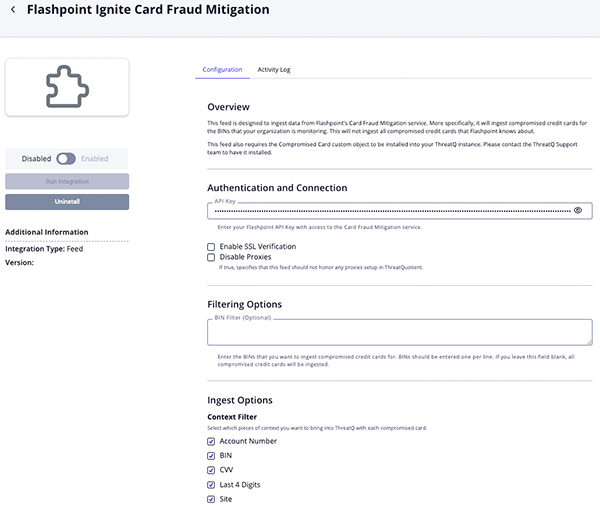
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
Flashpoint Ignite
The Flashpoint Ignite feed ingests compromised Reports and any related Indicators, Adversaries, Malware, Vulnerabilities and Attack Patterns.
GET https://api.flashpoint.io/finished-intelligence/v1/reports
Sample Response:
{
"total": 20,
"limit": 1,
"count": 1,
"skip": 0,
"data": [
{
"id": "XWnZwZYsS1WzljFH2SqIeA",
"title": "Coronavirus (COVID-19) Threats (Analyst Knowledge Page)",
"summary": "Risks concerning the coronavirus (COVID-19) began in early January 2020, shortly after the virus began to receive media attention.",
"tags": [
"Cybercrime",
"Knowledge Base",
"Malware",
"Events"
],
"body": "<html><head></head><body class=\"c47 c60\"><div><p class=\"c51 c10 c55\"><span class=....",
"title_asset": "/assets/9vXqarKJRPubHLa8UUntAA",
"title_asset_id": "9vXqarKJRPubHLa8UUntAA",
"assets": [
"/assets/agEIfiLjSe6e7FXcuPiaLg",
"/assets/2c2At8cZTT--JcGvqYUKOw",
"/assets/6ofKfKcER5aqROXTtSEZsA"
],
"asset_ids": [
"agEIfiLjSe6e7FXcuPiaLg",
"2c2At8cZTT--JcGvqYUKOw"
],
"sources": [
{
"original": "https://fp.tools/api/v4/indicators/event/5e7a40ba-e198-4e44-90f5-007b0a212811",
"platform_url": null,
"source": null,
"source_id": null,
"type": "External",
"title": "https://fp.tools/api/v4/indicators/event/5e7a40ba-e198-4e44-90f5-007b0a212811"
},
{
"original": "https://fp.tools/api/v4/indicators/event/5e7a471c-6f7c-4097-a4d0-061c0a212913",
"platform_url": null,
"source": null,
"source_id": null,
"type": "External",
"title": "https://fp.tools/api/v4/indicators/event/5e7a471c-6f7c-4097-a4d0-061c0a212913"
}
],
"is_featured": false,
"ingested_at": "2020-07-31T19:44:52.090+00:00",
"posted_at": "2020-07-31T19:44:52.090+00:00",
"platform_url": "https://fp.tools/home/intelligence/reports/report/XWnZwZYsS1WzljFH2SqIeA#detail",
"notified_at": null,
"updated_at": "2020-07-31T19:44:52.090+00:00",
"version_posted_at": "2020-07-31T19:40:01.041+00:00",
"published_status": "published"
}
]
}ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| .data[].title | Report.Value | N/A | .data[].ingested_at | 'Coronavirus (COVID-19) Threats (Analyst Knowledge Page)' | Extracted value between " if " is available else trimmed Actor Profile: / Actor Profile Update: from the value, only applicable if .tags[] contains Actor Profile as an item |
| .data[].body | Report.Description | N/A | N/A | <html><head></head><body class=\"c47 c60\"><div><p class=\"c51 c10 c55\"><span class=.... |
Formatted and trimmed |
| .data[].summary | Report.Attribute | Summary | .data[].ingested_at | 'Risks concerning the coronavirus (COVID-19) began in early January 2020, shortly after...' | Stripped HTML tags |
| .data[].tags | Report.Tag | Tag | N/A | ['Cybercrime', 'Knowledge Base', 'Malware', 'Events'] | If .tags[] contains Actor Profile as an item, the report will be ingested as selected by the user (see Save Actor Profile As user field) |
| .data[].sources[].title | Report.Attribute | Source | .data[].ingested_at | ['External, https://fp.tools/api/ v4/indicators/event/ 5e7a40ba-e198-4e44 -90f5-007b0a212811', ...] |
Converted to '.type, .title', added only if title is present |
| .data[].asset_ids[] | Report.Attribute | Asset | .data[].ingested_at | https://api.flash |
Converted to https://api.flashpoint.io/finished-intelligence/v1/assets/<asset_id>?size=orig |
| .data[].published_status | Report.Attribute | Published Status | .data[].ingested_at | 'published' | N/A |
| .data[].platform_url | Report.Attribute | Platform URL | .data[].ingested_at | https://fp.tools/ |
N/A |
| .data[].is_featured | Report.Attribute | Is Featured | .data[].ingested_at | false | N/A |
| .data[].body | Indicator.Value | MD5 | .data[].ingested_at | 492c423824351f f8dc1ed4bba761 d200 |
Extracted using regex |
| .data[].body | Indicator.Value | SHA1 | .data[].ingested_at | 2dab955dab3fb f895047d74b5d 232ab444e9d0d2 |
Extracted using regex |
| .data[].body | Indicator.Value | SHA256 | .data[].ingested_at | d028e64bf4ec9 7dfd655ccd115 7a5b96515d461 a710231ac8a529 d7bdb936ff3 |
Extracted using regex |
| .data[].body | Indicator.Value | SHA512 | .data[].ingested_at | 6473dac67b751 94deeaef37103 bba17936f6c16 ffcd2a7345a5a4 6756996fad748 a97f36f8fd4be4 e1f264ece31377 3cc5596099d68e 71344d8135f50e 5d8971 |
Extracted using regex |
| .data[].body | Indicator.Value | IP Address | .data[].ingested_at | 167.114.242.226 | Extracted using regex |
| .data[].body | Indicator.Value | CVE | .data[].ingested_at | CVE-2022-26143 | Extracted using regex |
Flashpoint Ignite Community Ransomware
The Flashpoint Ignite Community Ransomware feed requests article and conversation data gathered by Flashpoint Ignite regarding Ransomware.
POST https://api.flashpoint.io/sources/v2/communities
Sample Body:
{
"query": "communication",
"page": 0,
"size": 100,
"include": {
"type": [
"ransomware"
],
"date": {
"start": "2024-04-01T00:00:00Z",
"end": "2024-04-25T00:00:00Z"
}
}
}Sample Response:
{
"items": [
{
"id": "hN2MrDM8VtGvSv0Q48ReZQ",
"author": "CiphBit",
"date": "2024-04-06T00:00:00Z",
"enrichments": {
"location": [
{
"country_code": "EG",
"name": "Arab Republic of Egypt",
"lat": 27.0,
"long": 30.0
}
],
"url_domains": [
"vietnamnet.vn"
],
"ip_addresses": [
"179.61.12.162"
],
"email_addresses": [
"cyberoutlaw@cock.li"
],
"translation": {
"language": "english",
"message": "TermoPlastic S.R.L \n post date, Apr 6, 2024 \n It's a company.."
}
},
"first_observed_at": "2024-04-06T05:00:10Z",
"last_observed_at": "2024-05-07T01:03:47Z",
"message": "TermoPlastic S.R.L \n post date, Apr 6, 2024 \n Est una compania...",
"message_id": "TermoPlastic S.R.L",
"native_id": "TermoPlastic S.R.L",
"site": "CiphBit Ransomware Blog",
"site_actor_handle": "CiphBit",
"site_source_uri": "ciphbitqyg26jor7eeo6xieyq7reouctefrompp6ogvhqjba7uo4xdid.onion",
"site_title": "CiphBit Ransomware Blog",
"sort_date": "2024-04-06T00:00:00Z",
"title": "TermoPlastic S.R.L",
"type": "ransomware"
}
],
"size": 1,
"total": {
"value": 1,
"relation": "="
}
}ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| .items[].type, .items[].title | Report.Value | N/A | .items[].date | Flashpoint Ignite Ransomware: TermoPlastic S.R.L | Format: Flashpoint Ignite <type>: <title> |
| .data[].message | Report.Description | N/A | N/A | TermoPlastic S.R.L \n post date, Apr 6, 2024 \n Est una compania... |
Formatted. |
| .data[].enrichments. translation.message |
Report.Description | N/A | N/A | TermoPlastic S.R.L \n post date, Apr 6, 2024 \n It's a company... |
Formatted, User-configurable |
| .data[].site | Report.Attribute | Source | .items[].date | CiphBit Ransomware Blog | N/A |
| .data[].enrichments .location.country_code |
Report.Attribute | Country Code | .items[].date | EG | N/A |
| .data[].enrichments. location.name |
Report.Attribute | Location | .items[].date | Arab Republic of Egypt | N/A |
| .data[].enrichments. url_domains |
Related Indicator.Value | FQDN | .items[].date | vietnamnet.vn | User-configurable |
| .data[].enrichments .ip_addresses |
Related Indicator.Value | IP Address | .items[].date | 179.61.12.162 | User-configurable |
| .data[].enrichments email_addresses |
Related Indicator.Value | Email Address | .items[].date | cyberoutlaw@cock.li | User-configurable |
| .data[].author | Related Adversary.Value | N/A | .items[].date | CiphBit | N/A |
Flashpoint Ignite Indicators
The Flashpoint Ignite Indicators feed ingests indicators requested from Flashpoint Ignite.
https://api.flashpoint.io/technical-intelligence/v2/indicators
Sample Response:
{
"items": [
{
"id": "b7VCngwQUiGrNWozMuGfrQ",
"type": "file",
"value": "5f67558aab5387235a7efb0633cd0823a6aba2f106bee5dbc083a931989410e7",
"href": "https://api.flashpoint.io/technical-intelligence/v2/indicators/b7VCngwQUiGrNWozMuGfrQ",
"entity_type": "indicator",
"score": {
"value": "malicious",
"last_scored_at": "2025-05-08T16:30:08.190000"
},
"modified_at": "2025-05-08T16:30:08.190000",
"created_at": "2025-05-08T16:15:14.671000",
"last_seen_at": "2025-05-08T16:15:14.671000",
"sort_date": "2025-05-08T16:15:14.671000",
"platform_urls": {
"ignite": "https://app.flashpoint.io/cti/malware/iocs/b7VCngwQUiGrNWozMuGfrQ"
},
"hashes": {
"md5": null,
"sha1": "956782c65420f85ceb29867ee7e0db2684f3fe9d",
"sha256": "5f67558aab5387235a7efb0633cd0823a6aba2f106bee5dbc083a931989410e7"
},
"sightings": [
{
"source": "external_malware_bazaar",
"sighted_at": "2025-05-08T16:15:14.671000",
"tags": [
"file_type:exe",
"malware:dcrat",
"source:external_malware_bazaar"
]
}
],
"latest_sighting": {
"source": "external_malware_bazaar",
"sighted_at": "2025-05-08T16:15:14.671000",
"tags": [
"file_type:exe",
"malware:dcrat",
"source:external_malware_bazaar"
]
},
"total_sightings": 1
}
]
}ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| .items[].value | Indicator.Value | .items[].type | .data[].created_at | '5f67558aab5387235a7efb0 633cd0823a6aba2f106bee5 dbc083a931989410e7' |
Indicator type is extracted based on value length. See Indicator map below. |
| .items[].id | Indicator.Attribute | Flashpoint ID | .data[].created_at | 'b7VCngwQUiGrNWozMuGfrQ' | N/A |
| .items[].score.value | Indicator.Attribute | Score | .data[].created_at | 'malicious' | Updatable |
| .items[].platform_urls.ignite | Indicator.Attribute | Flashpoint Link | .data[].created_at | 'https://app.flashpoint.io/cti/m alware/iocs/b7VCngwQUiGrNW ozMuGfrQ' |
N/A |
| .items[].modified_at | Indicator.Attribute | Modified At | .data[].created_at | '2025-05-08T16:30:08.190000' | Updatable |
| .items[].last_seen_at | Indicator.Attribute | Last Seen At | .data[].created_at | '2025-05-08T16:15:14.671000' | Updatable |
| .items[].latest_sighting.tags | Indicator.Tag | N/A | .data[].created_at | 'file_type:exe' | N/A |
| .items[].hashes | Related Indicator.Value | MD5/SHA-1/SHA-256 | .data[].created_at | '956782c65420f85ceb29867e e7e0db2684f3fe9d' |
Relates the indicators with value different than items[].value. The type od the indicator is the items[].hashes key and the value is the items[].hashes value. |
Indicator map
URL: URL domain: FQDN ipv4: IP Address file: Hash. See Hash map extracted_config: Filename, URL, FQDN, IP Addresses. See Extracted Config Note.
Hash map
Type is determined based on the Hash length:32: md5 40: sha-1 64: sha-256.
Extracted Config Note
Extracted_config is a special Flashpoint indicator type, that might have the value in this format:
"{\"Port\": \"3000\", \"ServerID\": \"vagina\", \"Password\": \"1234\", \"Install_Flag\": \"TRUE\", \"Install_Directory\": \"HostManager\", \"Install_Name\": \"HostManager.exe\", \"ActiveX_Startup\": \"{AL887A2X-5730-5620-121P-H80DXJR5ECUY}\", \"Enable_Message_Box\": \"FALSE\", \"Activate_Keylogger\": \"TRUE\", \"Keylogger_Enable_FTP\": \"FALSE\", \"FTP_Directory\": \"./logs/\", \"FTP_UserName\": \"ftp_user\", \"FTP_Password\": \"none\", \"FTP Port\": \"21\", \"FTP_Interval\": \"30\", \"Persistance\": \"TRUE\", \"Hide_File\": \"TRUE\", \"Change_CreationDate\": \"TRUE\", \"Mutex\": \"UDPMQ83G21587O\", \"MeltFile\": \"TRUE\", \"Startup_Policies\": \"Policies\", \"USB_Spread\": \"1000\", \"P2P_Spread\": \"none\", \"GoogleChrome_Passwords\": \"http://www.server.com/sqlite3.dll\", \"Domain\": [\"mw2jtag.no-ip.info\"]}"
The indicators are extracted by parsing this value. We might have indicators like: Filename, URL, FQDN, IP Addresses, Email Address. The first parsed indicator will act as main indicator and will have the attributes described in the mapping table, and the rest of the indicators found will act as related indicators.
Flashpoint Ignite Media Sources
The Flashpoint Ignite Media Sources feed ingests media data that has been analyzed by Flashpoint Ignite Optical Character Recognition (OCR) process. The OCR process returns any text, classifications, or logos found within the media that are available for search. The output of the OCR process is ingested as a ThreatQ Report.
POST https://api.flashpoint.io/sources/v2/media
Sample Body:
{
"query": "checks",
"page": 0,
"size": 50,
"include": {
"date": {
"start": "2024-04-25T00:00:00Z",
"end": "2024-04-27T00:00:00Z"
}
}
}
Sample Response
{
"items": [
{
"author": "TollaG",
"author_id": "7093587118",
"id": "YB3lxHk5XUa9Wa_WmDGMbQ",
"date": "2024-04-21T03:52:54Z",
"media_id": "3NoHlK5CVt2ah7EabvQ1lw",
"media_type": "image",
"phash": "9037b7c06a8dcd2e",
"platform_url": "https://app.flashpoint.io/to/media/NEd3Y5sjUSOInCRm6eifdQ?include.date=all+time",
"site": "Telegram",
"sort_date": "2024-04-21T03:52:54Z",
"safe_search": "moderate",
"size": 80719,
"storage_uri": "gs://kraken-datalake-media/artifacts/a9/a9cd128156c43f24f20cf67c58f36535d66d50708b5357a5ff124453c4f5b00d",
"title": "Loaders and Carders(worldwide)",
"title_id": "1454251053",
"extracted_classifications": [
"Communication Device",
"Font",
"Portable communications device"
],
"extracted_text": [
"MARKET\nDDARKNET MARKET\nDARKNET MARKET\nDOPIETAT\nDARKNET MARKET\nC\nRegistered Email\nDARKNET\nEnter password here\nDARKNET MARKET\nLogin to Logsnow.world\nFast and Easy\nDARK DARKNET MARKET\nLOGIN\nForgot your password?\nDEWAN LHKKNE:\nDon't have an account? Sign Up",
"MARKET",
"DDARKNET",
"MARKET",
"DARKNET",
"MARKET",
"DOPIETAT",
"DARKNET",
"MARKET",
"C",
"Registered",
"Email",
"DARKNET",
"Enter",
"password",
"here",
"DARKNET",
"MARKET",
"Login",
"to",
"Logsnow.world",
"Fast",
"and",
"Easy",
"DARK",
"DARKNET",
"MARKET",
"LOGIN",
"Forgot",
"your",
"password",
"?",
"DEWAN",
"LHKKNE",
":",
"Don't",
"have",
"an",
"account",
"?",
"Sign",
"Up"
],
"image_uri": "gs://kraken-datalake-media/artifacts/a9/a9cd128156c43f24f20cf67c58f36535d66d50708b5357a5ff124453c4f5b00d",
"image_sha": "129bff58f43bef754584edeba1a5fcb5922a5b25",
"type": "chat"
},
{
"author": "Caesarin0",
"id": "odQGJdatWLKef78bmwUFUA",
"date": "2024-04-20T19:51:41Z",
"file_name": "/hy4t7009vovc1.png",
"media_id": "ITDg001BU_yuyZfsPrftPA",
"media_type": "image",
"phash": "95330fbc7a8c620f",
"parent_container_name": "bleach",
"site": "Reddit",
"sort_date": "2024-04-20T19:51:41Z",
"safe_search": "moderate",
"section": "bleach",
"section_id": "bleach",
"size": 102860,
"storage_uri": "gs://kraken-datalake-media/artifacts/3c/3cb4835991439191d99e4762d149fc8f73e645ae1df0e3a3d787b76a6b821e24",
"title": "Theory: Aizen doesn't have a bankai",
"title_id": "1c8wtu1",
"extracted_classifications": [
"Joint",
"Shoulder",
"Human"
],
"extracted_text": [
"...KYÔKA\nSUIGETSU.\nSHATTER\n\"\nSEE.",
"...",
"KYÔKA",
"SUIGETSU",
".",
"SHATTER",
"\"",
"SEE",
"."
],
"image_uri": "gs://kraken-datalake-media/artifacts/3c/3cb4835991439191d99e4762d149fc8f73e645ae1df0e3a3d787b76a6b821e24",
"image_sha": "3db5dfc1050d2a444874bc094bd3ce85becbbb5a",
"type": "reddit"
}
],
"size": 50,
"total": {
"value": 5000,
"relation": ">"
}
}ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| items[].site, .items[].title |
Report.Value | N/A | .items[].date | Flashpoint Ignite Media: Telegram - Loaders and Carders(worldwide) | Values are concatenate and prepended with Flashpoint Ignite Media |
| .data[].extracted_ text[0] |
Report.Description | N/A | N/A | MARKET\nDDARKNET MARKET\nDARKNET MARKET\nDOPIETAT\nDARKNET MARKET\nC\nRegistered Email... |
Formatted. |
| .data[].extracted_ classifications[] |
Report.Tag | Tag | N/A | ['Communication Device', 'Font', 'Portable communications device'] | User-configurable. |
| .data[].site | Report.Attribute | Source | .items[].date | Telegram | User-configurable. |
| .data[].platform_ url |
Report.Attribute | Platform URL | .items[].date | https://app.flashpoint.io/to/ media/NEd3Y5sjUSOInCRm6eifdQ?include.date=all+time |
User-configurable. |
| .data[].type | Report.Attribute | Source Type | .items[].date | Chat | User-configurable. |
| .data[].author | Related Adversary.Value | N/A | .items[].date | TollaG | N/A |
Flashpoint Ignite Card Fraud Mitigation
The Flashpoint Ignite Card Fraud Mitigation feed detects and ingests compromised credit cards from illicit communities and data breaches.
POST https://api.flashpoint.io/sources/v2/fraud
Sample Request Body:
{
"page": 0,
"size": 10000,
"include": {
"date": {
"after": "2023-01-10T00:00:00Z"
}
}
}Sample Response:
{
"size": 7,
"total": {
"value": 5000,
"relation": ">"
},
"items": [
{
"author": "fernando_club",
"bin": 517800,
"card": {
"expiration": "01/26"
},
"cardholder": {
"location": {
"city": "LIVERMORE",
"country": "US",
"region": "CA",
"zip_code": "94550"
}
},
"date": "2024-03-19T19:29:41Z",
"first_observed_at": "2024-03-19T19:29:41Z",
"last_observed_at": "2024-03-19T19:29:41Z",
"prices": [
24
],
"release": {
"name": "March, 2024",
"id": "6brA7geGXBehI1uON0iMFg"
},
"site": "Fernando Club",
"author_alias": [
"fernando_club"
],
"site_source_uri": "fernandogoods.biz",
"id": "rdPOB562X6-BywkMhVHy0g",
"source_type": "shop",
"type": "partial_card_cvv"
},
{
"author": "CC CHEAPLUXURY SCRAPE",
"bin": 470881,
"card": {
"cvv": 614,
"expiration": "08/2024",
"number": 4708810311302243
},
"created_at": "2024-07-11T05:24:46Z",
"date": "2024-07-11T05:24:46Z",
"first_observed_at": "2024-07-11T05:24:47.297485Z",
"last4": 2243,
"last_observed_at": "2024-07-11T05:24:47.297485Z",
"site": "Telegram",
"account_number": "031130224",
"author_alias": [
"CC CHEAPLUXURY SCRAPE"
],
"site_source_uri": "web.telegram.org",
"id": "yPYaOyqHWLSBYAiHi5_qYQ",
"source_type": "chat",
"type": "full_card"
}
]
}ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| .items[].card.number | Card.Value | N/A | .items[].date | 4708810311302243 |
If items[].card.number is available |
| .items[].bin, .items[].last4, items[].card.expiration, items[].card.cvv | Card.Value | N/A | .items[].date | 517800\| 26\|01 |
If items[].card.number is not available |
| .items[].account_number | Card.Attribute | Account Number | .items[].date | 031130224 |
User-configurable |
| .items[].bin | Card.Attribute | BIN | .items[].date | 470881 |
User-configurable |
| .items[].card.cvv | Card.Attribute | CVV | .items[].date | 614 |
User-configurable |
| .items[].last4 | Card.Attribute | Last 4 Digits | .items[].date | 2243 |
User-configurable |
| .items[].site | Card.Attribute | Site | .items[].date | Telegram |
User-configurable |
| .items[].release.name | Card.Attribute | Release Name | .items[].date | March, 2024 |
User-configurable |
| .items[].prices[] | Card.Attribute | Sale Price | .items[].date | 24 |
User-configurable |
| .items[].source_type | Card.Attribute | Source Type | .items[].date | chat |
User-configurable |
| .items[].author | Card.Attribute | Source | .items[].date | CC CHEAPLUXURY SCRAPE |
User-configurable |
| .items[].type | Card.Attribute | Data Type | .items[].date | full_card |
User-configurable |
| .items[].last_observed_at | Card.Attribute | Last Observed At | .items[].date | 2024-07-11 05:24:47.297485 |
Timestamp, User-configurable, Updatable |
| .items[].first_observed_at | Card.Attribute | First Observed At | .items[].date | 2024-07-11 05:24:47.297485 |
Timestamp, User-configurable |
| .items[].card.expiration | Card.Attribute | Expiration | .items[].date | 08/2024 |
User-configurable |
| .items[].cardholder.name.first | Card.Attribute | Owner First Name | .items[].date | N/A | User-configurable |
| .items[].cardholder.name.full_name | Card.Attribute | Owner Full Name | .items[].date | N/A | User-configurable |
| .items[].cardholder.location.city | Card.Attribute | Owner City | .items[].date | LIVERMORE |
User-configurable |
| .items[].cardholder.location.region | Card.Attribute | Owner Region | .items[].date | CA |
User-configurable |
| .items[].cardholder.location.country | Card.Attribute | Owner Country | .items[].date | US |
User-configurable |
| .items[].cardholder.location.zip_code | Card.Attribute | Owner Zip code | .items[].date | 94550 |
User-configurable |
| .items[].site_source_uri | Card.Attribute | Flashpoint Link | .items[].date | web.telegram.org |
User-configurable |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
Flashpoint Ignite
| Metric | Result |
|---|---|
| Run Time | 4 minutes |
| Reports | 71 |
| Report Attributes | 1,413 |
| Adversaries | 1 |
| Adversary Attributes | 0 |
| Indicators | 1,101 |
| Indicator Attributes | 27,453 |
| Malware | 16 |
| Attack Patterns | 0 |
| Vulnerabilities | 0 |
Flashpoint Ignite Community Ransomware
| Metric | Result |
|---|---|
| Run Time | 8 minutes |
| Adversaries | 46 |
| Reports | 856 |
| Report Attributes | 1,980 |
| Indicators | 3,921 |
Flashpoint Ignite Indicators
| Metric | Result |
|---|---|
| Run Time | 1 minute |
| Indicators | 2,066 |
| Indicator Attributes | 5,814 |
Flashpoint Ignite Media Sources
| Metric | Result |
|---|---|
| Run Time | 2 minutes |
| Adversaries | 818 |
| Reports | 647 |
| Report Attributes | 2,394 |
Flashpoint Ignite Card Fraud Mitigation
| Metric | Result |
|---|---|
| Run Time | 8 minutes |
| Compromised Cards | 4,571 |
| Card Attributes | 51,599 |
Known Issues / Limitations
-
MITRE ATT&CK attack patterns must have already been ingested by a previous run of the MITRE ATT&CK feeds in order for MITRE ATT&CK attack patterns to be extracted and related. MITRE ATT&CK attack patterns are ingested from the following feeds:
- MITRE Enterprise ATT&CK
- MITRE Mobile ATT&CK
- MITRE PRE-ATT&CK
-
The API used by Flashpoint Ignite Media Sources, Flashpoint Ignite Community Ransomware and Flashpoint Ignite Card Fraud Mitigation only returns the latest 10000 records.
Change Log
- Version 3.4.1 rev-a
- Guide Update - updated custom object installation steps for ThreatQ v6 instances.
- Version 3.4.1
- Flashpoint Ignite Indicators feed - added the following configuration parameter:
- Flashpoint Sources - select which Flashpoint-provided sources to ingest into ThreatQ.
- The configuration screen layout for all feeds has been updated to enhance the overall user experience.
- Flashpoint Ignite Indicators feed - added the following configuration parameter:
- Version 3.4.0
- Removed the Flashpoint Ignite Events feed.
- Removed ingestion of related events from the Flashpoint Ignite feed due to endpoint deprecation.
- Added a new feed: Flashpoint Ignite Indicators.
- Version 3.3.7
- Flashpoint Ignite Media Sources feed - resolved a filter mapping error that would occur when the
authorkey is missing.
- Flashpoint Ignite Media Sources feed - resolved a filter mapping error that would occur when the
- Version 3.3.6
- Flashpoint Ignite Community Ransomware feed - resolved a
TypeError ("'NoneType' object is not iterable")error, which resulted in blank descriptions.
- Flashpoint Ignite Community Ransomware feed - resolved a
- Version 3.3.5
- Added a new configuration parameter, Content Filter, to the Flashpoint Ignite Media Sources feed. This parameter allows you to select the pieces of enriched data to ingest.
- The Flashpoint Ignite Media Sources feed now ingests
Authorsas adversaries.Authorswere previously ingested as identities.
- Version 3.3.4
- Resolved a pagination issue with the Flashpoint Ignite Media Sources feed.
- Version 3.3.3
- Resolved an issue where descriptions were truncated which resulted in elements such as tables and images being removed. Descriptions will no longer be truncated and table and image elements will now be included.
- Threat Actors are now mapped as Adversaries instead of Identity objects.
- Version 3.3.2
- Added a new feed: Flashpoint Ignite Card Fraud Mitigation. This new feed ingests compromised card objects and requires the Compromised Card custom object.
- Added the following parameters to all feeds:
- Disable Proxies
- Enable SSL Verification
- Version 3.3.1
- Added a new feed: Flashpoint Ignite Community Ransomware.
- Version 3.3.0
- Migrated the feeds to the Flashpoint Ignite API.
- Added new feed: Flashpoint Ignite Media Sources.
- Added a new Known Issue - the API used by
Flashpoint Ignite Media Sourcesonly returns the latest 10000 records. - Updated minimum ThreatQ version to 5.12.0
- Updated integration name from Flashpoint CDF to Flashpoint Ignite CDF.
- Version 3.2.0
- Fixed a pagination issue.
- Updated maximum number of skipped items to 10,000.
- Added IOC Type filtering support for Flashpoint Events. See the Configuration chapter for more details.
- Version 3.1.0
- Fixed an issue with blank descriptions.
- Added indicator parsing for the report body (hashes, CVEs, and IPs). See the ThreatQ Mapping and Configuration chapters for further details.
- Tags are now ingested as Tags within ThreatQ. Previously, these tags were ingested as attributes into the ThreatQ platform.
- Version 3.0.1
- Fixes KeyError for
Attribute
- Fixes KeyError for
- Version 3.0.0
- Mapping Changed
- CDF Rewritten
- Removed the Ingest Related Reports user field
-
Version 2.1.0
- Ingest data as Adversaries or Intrusion Set
- Add the Ingest Related Reports user field
- Removed the attribute 'Notified At'
- Add published_at to Reports and Report Attributes
- Filter the
<div>and<img>from the .body JSON key
- Version 2.0.2
- Header Enhancements
- Version 2.0.1
- Fix the error with the JSON Parsing
- Version 2.0.0
- Ingest IPs from new endpoint
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Flashpoint Ignite CDF Guide v3.4.1 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.4.0 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.7 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.6 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.5 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.4 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.3 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.2 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.1 | 5.12.0 or Greater |
| Flashpoint Ignite CDF Guide v3.3.0 | 5.12.0 or Greater |
| Flashpoint CDF Guide v3.2.0 | 4.28.0 or Greater |
| Flashpoint CDF Guide v3.1.0 | 4.28.0 or Greater |
| Flashpoint CDF Guide v2.0.2 | 4.21.1 or Greater |
| Flashpoint CDF Guide v2.0.1 | 4.21.1 or Greater |
| Flashpoint CDF Guide v2.0.0 | 4.21.1 or Greater |
| Flashpoint CDF Guide v1.0.1 | 4.21.1 or Greater |