Current ThreatQ Version Filter
Upgrading
The following steps are the standard way to upgrade the App and Add-On.
App Upgrade Steps
- Follow the standard Splunkbase upgrade steps to upgrade the app.
Wait for the upgrade process to complete before proceeding with the next step.
- Navigate to Info > Edit App Configuration > Account.
- Configure the account for the app to perform workflow actions and AR actions.
- Review and configure the Proxy and a Logging settings if needed.
If you are upgrading to a newer version of the App component and are currently using Enterprise Support matching, you will need to run the threatq_cleanup_es_lookups saved search once to remove the old data prior to upgrading. All the threat intelligence data will be automatically added upon upgrade using the Enterprise Security's REST APIs.
Add-On Upgrade Steps
- Navigate to the ThreatQuotient Add-on for Splunk.
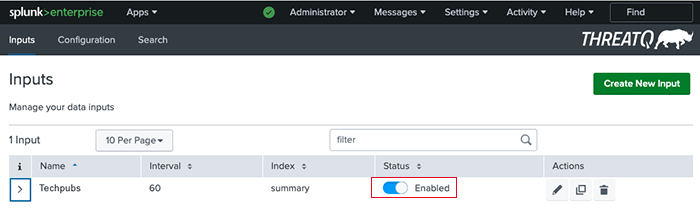
- Navigate to the Inputs page and disable any existing inputs.
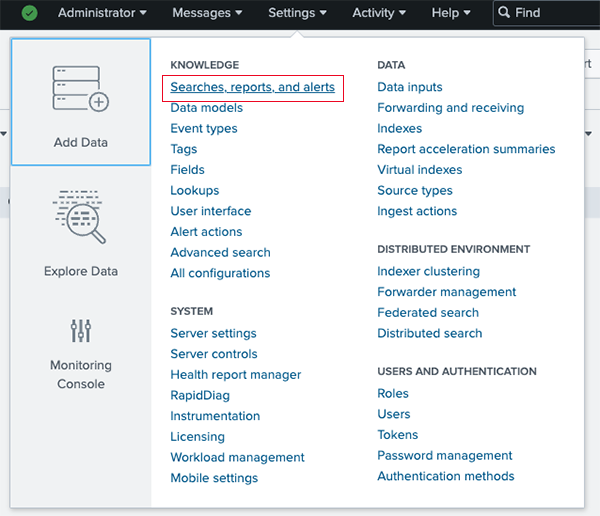
- Navigate to Settings > Searches, Reports, and Alerts.
- Delete any existing alerts.
- Follow the standard Splunkbase upgrade steps to upgrade the Add-on.
Wait for the upgrade process to complete before proceeding with the next step.
- Navigate back to the ThreatQuotient Add-on for Splunk.
- Navigate to the Inputs page and enable any existing input or create a new input in the fields supplied.