abuse.ch Malwarebazaar Action
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.1.0 |
| Compatible with ThreatQ Versions | >= 5.6.0 |
| ThreatQ TQO License Required | Yes |
| Support Tier | ThreatQ Supported |
Introduction
The abuse.ch Malwarebazaar action submits data collections containing MD5, SHA-1 and SHA-256 IOCs to abuse.ch MalwareBazaar and returns Indicators, TTPs and Malware. Then, abuse.ch MalwareBazaar queries the submitted objects for enrichment and returns related threat intelligence to be ingested into the ThreatQ library.
The action can perform the following function:
- abuse.ch MalwareBazaar - submits indicators to abuse.ch MalwareBazaar to be enriched with related threat intelligence.
The action is compatible with the following indicator types:
- MD5
- SHA-1
- SHA-256
The action returns the following enriched system objects:
- Indicators
- Indicator Attributes
- Indicator Tags
- Malware
- TTP
This action is intended for use with ThreatQ TDR Orchestrator (TQO). An active TQO license is required for this feature.
Prerequisites
The action requires the following:
- An active ThreatQ TDR Orchestrator (TQO) license.
- A data collection containing at least one of the following indicator types:
- MD5
- SHA-1
- SHA-256
- Abuse.ch ThreatFox API Key.
Installation
This action can be installed in the My Integration section of your ThreatQ instance. See the Installing an Action topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Actions option from the Category dropdown (optional).
- Click on the action entry to open its details page.
- Enter the following parameters under the Configuration tab:
The configurations set on this page will be used as the default settings when inserting this action into a new workflow. Updating the configurations on this page will not update any instances of this action that have already been deployed to a workflow. In that scenario, you must update the action’s configurations within the workflow itself.
Parameter Description Auth Key Your Abuse.ch ThreatFox Auth Key. Enable SSL Certificate Verification Enable this parameter if the feed should validate the host-provided SSL certificate. Disable Proxies Enable this parameter if the feed should not honor proxies set in the ThreatQ UI. Ingest MalwareBazaar Tags As Select how to ingest tags returned by the action. Options include: - Tags (default)
- Attributes
- Both
Supporting Context Select the pieces of context to bring into ThreatQ. Options include: - Fuzzy Hash
- SHA-256 Hash
- SHA-384 Hash
- SHA1 Hash
- MD5 Hash
- First Seen
- Last Seen
- Malware sample's file name
- File size in bytes
- MIME Type
- File type
- Reporter
- Country Code
- Related Malware
- Tags
- Delivery Method
- Reference
- YARA Rule Name
- Related C2 Servers
- Related TTP
Objects Per Run The max number of objects per run to send to this action. The max value for this parameter is 50,000. 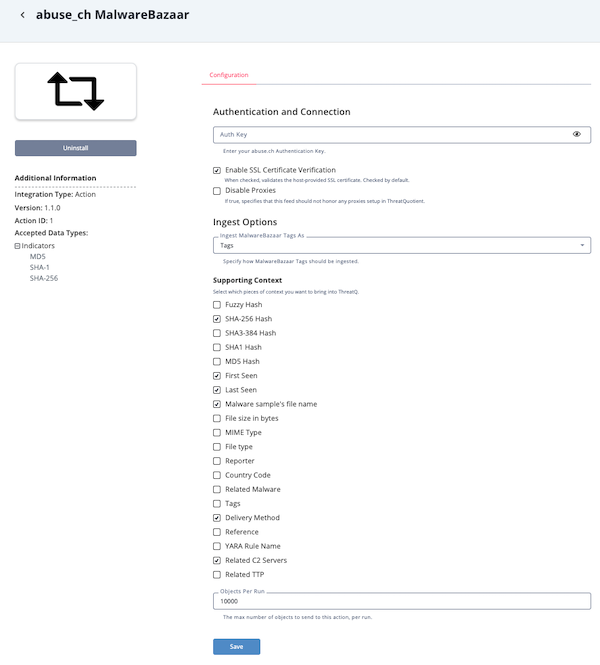
- Review any additional settings, make any changes if needed, and click on Save.
Action Functions
The action provides the following functions
| Function | Description | Object Type | Object Subtype |
|---|---|---|---|
| abuse_ch MalwareBazaar | Enriches IOCs using MalwareBazaar's API | Indicators | MD5, SHA-1, SHA-256 |
abuse_ch MalwareBazaar
The abuse_ch MalwareBazaar function enriches MD5, SHA-1 and SHA-256 IOCs using MalwareBazaar's API.
POST https://mb-api.abuse.ch/api/v1/
Sample Body:
Form URL-Encoded
query=get_info&hash=9cee5522a7ca2bfca7cd3d9daba23e9a30deb6205f56c12045839075f7627297Sample Response:
{
"data": [
{
"anonymous": 0,
"archive_pw": null,
"code_sign": [
{
"algorithm": "sha384WithRSAEncryption",
"cscb_listed": true,
"cscb_reason": "Quakbot",
"issuer_cn": "Sectigo Public Code Signing CA R36",
"serial_number": "626735ed30e50e3e0553986d806bfc54",
"subject_cn": "FISH ACCOUNTING and TRANSLATING LIMITED",
"thumbprint": "a1488004ec967faf6c66f55440bbde0de47065490f7c758f3ca1315bb0ef3b97",
"thumbprint_algorithm": "SHA256",
"valid_from": "2022-10-26T00:00:00Z",
"valid_to": "2023-10-26T23:59:59Z"
}
],
"comment": null,
"comments": null,
"delivery_method": "Web Download",
"dhash_icon": "b671d4ccccd46e8c",
"file_information": [
{
"context": "cape",
"value": "https://www.capesandbox.com/analysis/337299/"
}
],
"file_name": "hindmost.temp",
"file_size": 177664,
"file_type": "docx",
"file_type_mime": "application\/msword",
"first_seen": "2021-01-22 15:23:01",
"gimphash": null,
"imphash": "1726357b6fc2d768227af59ffbcbdfa8",
"intelligence": {
"clamav": [
"SecuriteInfo.com.Win32.DangerousSig.15426.26845.UNOFFICIAL"
],
"downloads": "314",
"mail": null,
"uploads": "2"
},
"last_seen": "2021-05-01 01:07:44",
"md5_hash": "09a815f48d8a5319d88f2b8b2e4b02ab",
"ole_information": [],
"origin_country": "FR",
"reporter": "Cryptolaemus1",
"sha1_hash": "d1dfe82775c1d698dd7861d6dfa1352a74551d35",
"sha256_hash": "9cee5522a7ca2bfca7cd3d9daba23e9a30deb6205f56c12045839075f7627297",
"sha3_384_hash": "0896178675b3349f6890ac1a270c185ca8d2ced319768f8922e9d6b967239704fa6579d61251f3b00b01d4baaf0e9d74",
"signature": "Heodo",
"ssdeep": "24576:AXYkbOvnDF9dnJEd+5F6bRGiJzN8gvd4rmwd2eZL/v2mWG2mWYY:XHnDF9dnJEd+5F6bR/JzN863q/v2mWGl",
"tags": [
"1669024152",
"BB07",
"dll",
"FISH ACCOUNTING TRANSLATING LIMITED",
"Qakbot",
"Quakbot",
"signed"
],
"telfhash": null,
"tlsh": "T156256BA296149435F86CECBD243DA6062829FCB11696B583F2C07DA3B4F35D138E7E47",
"vendor_intel": {
"ANY.RUN": {
"analysis_url": "https://app.any.run/tasks/57bbe8c6-a6f2-4512-8753-4416faf461df",
"date": "2022-12-06 13:51:23",
"file_name": "file",
"malware_family": null,
"tags": [
"dll"
],
"verdict": "No threats detected"
},
"CAPE": {
"detection": "QakBot",
"link": "https://www.capesandbox.com/analysis/337299/"
},
"CERT-PL_MWDB": {
"detection": null,
"link": "https://mwdb.cert.pl/sample/085f0f3f25b1328d153a7c56125e1d8a4d43bc882fe3f250d742ea5247850c02/"
},
"FileScan-IO": {
"confidence": "1",
"report_link": "https://www.filescan.io/uploads/637cf7a59c57db591d88be50/reports/1e634ed6-197b-49e8-a47b-5fbf4eaf3299/overview",
"threatlevel": "0.5",
"verdict": "SUSPICIOUS"
},
"InQuest": {
"details": [
{
"category": "info",
"description": "Found a Windows Portable Executable (PE) binary. Depending on context, the presence of a binary is suspicious or malicious.",
"title": "Windows PE Executable"
}
],
"url": null,
"verdict": "UNKNOWN"
},
"Intezer": {
"analysis_url": "https://analyze.intezer.com/analyses/4e162ffe-f59c-4db7-ba51-a23a7a35627f?utm_source=MalwareBazaar",
"family_name": "Qakbot",
"verdict": "malicious"
},
"ReversingLabs": {
"first_seen": "2022-11-22 16:24:10",
"scanner_count": "26",
"scanner_match": "16",
"scanner_percent": "61.54",
"status": "MALICIOUS",
"threat_name": "Win32.Backdoor.Quakbot"
},
"Spamhaus_HBL": [
{
"detection": "suspicious",
"link": "https://www.spamhaus.org/hbl/"
}
],
"Triage": {
"link": "https://tria.ge/reports/221122-twcr3sdd6y/",
"malware_config": [
{
"c2": "84.35.26.14:995",
"extraction": "c2",
"family": "qakbot"
},
{
"c2": "174.45.15.123:443",
"extraction": "c2",
"family": "qakbot"
}
],
"malware_family": "qakbot",
"score": "10",
"signatures": [
{
"score": "10",
"signature": "Qakbot/Qbot"
},
{
"score": null,
"signature": "Suspicious behavior: EnumeratesProcesses"
},
{
"score": null,
"signature": "Suspicious behavior: MapViewOfSection"
},
{
"score": null,
"signature": "Process spawned unexpected child process"
}
],
"tags": [
"family:qakbot",
"botnet:bb07",
"campaign:1669024152",
"banker",
"stealer",
"trojan"
]
},
"UnpacMe": [
{
"detections": [],
"link": "https://www.unpac.me/results/9383daac-5a50-4b25-ad6d-6212a407fa6c/",
"md5_hash": "742d7c33eed01381114e981abad801fb",
"sha1_hash": "44f665c1408004ae67c7f4c50f80d61af6076d7c",
"sha256_hash": "b7bd1dee74653a2f1871f9a589f2e17697ddc014b55f7e158e296601f6e00eb0"
},
{
"detections": [
"Qakbot",
"win_qakbot_auto"
],
"link": "https://www.unpac.me/results/9383daac-5a50-4b25-ad6d-6212a407fa6c/",
"md5_hash": "cf7dcbd42a3e3b61c697e93450f78585",
"sha1_hash": "38b2ccbc8abdd59b5cb25acce730ce26c403c589",
"sha256_hash": "01747eb0f7df63b9df7aeff2dc51e43264adc05b4c16f4908f38352405e31342"
},
{
"detections": [],
"link": "https://www.unpac.me/results/9383daac-5a50-4b25-ad6d-6212a407fa6c/",
"md5_hash": "09a815f48d8a5319d88f2b8b2e4b02ab",
"sha1_hash": "e6601cb30205c8e790ac4511f0d6362b80dbb9f5",
"sha256_hash": "085f0f3f25b1328d153a7c56125e1d8a4d43bc882fe3f250d742ea5247850c02"
}
],
"VMRay": {
"malware_family": "QBot",
"report_link": "https://www.vmray.com/analyses/_mb/085f0f3f25b1/report/overview.html",
"verdict": "malicious"
},
"YOROI_YOMI": {
"detection": "Malicious File",
"score": "0.87"
},
"vxCube": {
"behaviour": [
{
"rule": "Unauthorized injection to a system process",
"threat_level": "suspicious"
},
{
"rule": "Creating a window",
"threat_level": "neutral"
},
{
"rule": "Searching for the window",
"threat_level": "neutral"
},
{
"rule": "\u0421reating synchronization primitives",
"threat_level": "neutral"
},
{
"rule": "Launching a process",
"threat_level": "neutral"
},
{
"rule": "Searching for synchronization primitives",
"threat_level": "neutral"
},
{
"rule": "Modifying an executable file",
"threat_level": "neutral"
}
],
"maliciousness": "62",
"verdict": "suspicious2"
}
},
"yara_rules": [
{
"author": "Didier Stevens (@DidierStevens)",
"description": "Contains a valid Bitcoin address",
"reference": "",
"rule_name": "BitcoinAddress"
},
{
"author": "kevoreilly",
"description": "QakBot Payload",
"reference": "",
"rule_name": "QakBot"
},
{
"author": "anonymous",
"description": "",
"reference": "",
"rule_name": "QbotStuff"
},
{
"author": "",
"description": "Detects unpacked or memory-dumped QBot samples",
"reference": "",
"rule_name": "unpacked_qbot"
},
{
"author": "Felix Bilstein - yara-signator at cocacoding dot com",
"description": "Detects win.qakbot.",
"reference": "",
"rule_name": "win_qakbot_auto"
},
{
"author": "Felix Bilstein - yara-signator at cocacoding dot com",
"description": "Detects win.qakbot.",
"reference": "",
"rule_name": "win_qakbot_malped"
}
]
}
],
"query_status": "ok"
}ThreatQuotient provides the following default mapping for this function:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Normalization | Published Date | Examples | |
|---|---|---|---|---|---|---|
.data[0].tags |
Indicator.Tag / Indicator.Attribute | N/A / Tag | N/A / .first_seen |
BB07 |
User-configurable. | |
.data[0].vendor_intel.Triage.tags |
Indicator.Tag / Indicator.Attribute | N/A / Tag | N/A / .first_seen |
botnet:bb07 |
User-configurable. | |
.data[0].vendor_intel['ANY.RUN'].tag[] |
Indicator.Tag / Indicator.Attribute | N/A / Tag | N/A / .first_seen |
dll |
User-configurable. | |
.data[0].first_seen |
Indicator.Attribute | First Seen | .first_seen |
2021-01-22 15:23:01 |
User-configurable. | |
.data[0].last_seen |
Indicator.Attribute | Last Seen | .first_seen |
2021-05-01 01:07:44 |
User-configurable. | |
.data[0].file_size |
Indicator.Attribute | File Size (bytes) | .first_seen |
177664 |
User-configurable. | |
.data[0].file_type_mime |
Indicator.Attribute | MIME Type | .first_seen |
application\/msword |
User-configurable. | |
.data[0].file_type |
Indicator.Attribute | File Type | .first_seen |
docx |
User-configurable. | |
.data[0].reporter |
Indicator.Attribute | Reporter | .first_seen |
Cryptolaemus1 |
User-configurable. | |
.data[0].origin_country |
Indicator.Attribute | Origin Country | .first_seen |
FR |
User-configurable. | |
.data[0].delivery_method |
Indicator.Attribute | Delivery Method | .first_seen |
Web Download |
User-configurable. | |
.data[0].file_information.value |
Indicator.Attribute | Reference | .first_seen |
https://www.capesandbox.com/analysis/337299/ |
User-configurable. | |
.data[0].yara_rules[].rule_name |
Indicator.Attribute | Rule Name | .first_seen |
win_qakbot_malped |
User-configurable. | |
.data[0].vendor_intel.Triage.malware_config.c2 |
Indicator.Attribute | Port | .first_seen |
995 |
User-configurable. If .vendor_intel.Triage.malware_config.extraction is c2 |
|
.data[0].md5_hash |
Related Indicator.Value | MD5 | .first_seen |
09a815f48d8a5319d88f2b8b2e4b02ab |
User-configurable. | |
.data[0].sha1_hash |
Related Indicator.Value | SHA-1 | .first_seen |
d1dfe82775c1d698dd7861d6dfa1352a74551d35 |
User-configurable. | |
.data[0].sha256_hash |
Related Indicator.Value | SHA-256 | .first_seen |
9cee5522a7ca2bfca7cd3d9daba23e9a30deb6205f56c12045839075f7627297 |
User-configurable. | |
.data[0].sha3_384_hash |
Related Indicator.Value | SHA-384 | .first_seen |
0896178675b3349f6890ac1a270c185ca8d2ced319768f8922e9d6b967239704fa6579d61251f3b00b01d4baaf0e9d74 |
User-configurable. | |
.data[0].file_name |
Related Indicator.Value | Filename | .first_seen |
hindmost.temp |
User-configurable. | |
.data[0].vendor_intel.Triage.malware_config.c2 |
Related Indicator.Value | URL | .first_seen |
N/A | User-configurable. If .vendor_intel.Triage.malware_config.extraction is dropper |
|
.data[0].vendor_intel.Triage.malware_config.c2 |
Related Indicator.Value | IP Address | .first_seen |
84.35.26.14 |
User-configurable. If .vendor_intel.Triage.malware_config.extraction is c2 |
|
.data[0].value.vendor_intel.Triage.signatures.signature |
Related TTP.Value | N/A | .first_seen |
Process spawned unexpected child process |
User-configurable. | |
.data[0].signature |
Related Malware.Value | N/A | .first_seen |
Heodo |
User-configurable. | |
.data[0].ssdeep |
Related Indicator.Value | Fuzzy Hash | .first_seen |
24576:AXYkbOvnDF9dnJEd+5F6bRGiJzN8gvd4rmwd2eZL/v2mWG2mWYY:XHnDF9dnJEd+5F6bR/JzN863q/v2mWGl |
User-configurable. |
Enriched Data
Object counts and action runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
| Metric | Result |
|---|---|
| Run Time | 2 minute |
| Indicators | 150 |
| Indicator Attributes | 1,456 |
| Indicator Tags | 25 |
| Malware | 76 |
| TTP | 35 |
Use Case Example
- A user submits a data collection using the abuse.ch MalwareBazaar action to the abuse.ch MalwareBazaar with a data collection containing 350 system objects (100 MD5, 75 SHA-1, 75 SHA-256).
- The abuse.ch MalwareBazaar queries the submitted data.
- The action returns the submitted data collection enriched with the following:
- 99 Indicators
- 30 Indicator Attributes
- 20 Indicator Tags
- 3 Malware
- 5 TTP
Change Log
- Version 1.1.0
- Adds support for authenticating with the API.
- Adds the ability to enable SSL certificate verification.
- Adds the ability to disable proxies.
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| abuse.ch Malwarebazaar Action Guide v1.1.0 | 5.6 or Greater |
| abuse.ch Malwarebazaar Action Guide v1.0.0 | 5.6 or Greater |