About User Management
Default ThreatQ Role: Administrative or Maintenance
Custom Role - Action Permissions: Administrative Functions - Edit User Management
ThreatQ provides several user roles, each containing a set of permissions for accessing system functionality. You create user accounts and then assign them to a user role. The user role determines each account's set of permissions.
After you create a user account, you can use the Edit User screen to further customize its account maintenance and display settings.
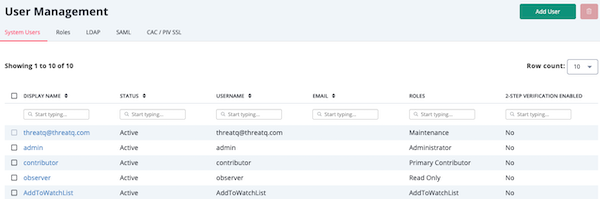
The User Management page allows you to manage user logins and permissions as well as configure authentication methods.
ThreatQ provides several default user roles, each containing a set of permissions for accessing system functionality. In addition you can create custom roles which allow more granular control over action-level permissions. For each user account you create, you can:
- Assign a default user role which defines the user’s permissions.
OR - Assign a custom role which specifies action-level permissions.
Example: User Account with Default User Role
User Account = Jane_Smith
Default Role = Administrator
Example: User Account with Custom Role
User Account = Jane_Doe
Custom Role = TQX Restricted
Action Permissions = No permission to edit Data Exchange feeds
After you create a user account, you can use the Edit User screen to further customize its account maintenance and display settings.
User Roles
ThreatQ provides four user roles: Maintenance, Administrator, Primary Contributor, and Read Only. Maintenance and Administrator user roles provide access to the entire ThreatQ user interface as well as the ability to edit all data. The Primary Contributor role provides limited editing capabilities. And, the Read Only role allows users to view but not edit data.
See the Default User Roles section for more information on each user role.
Custom Roles
You can use action permissions to create custom roles that customize user access and provide more robust role-based action control (RBAC). This approach to managing user access allows you to ensure that users have the access they need and to minimize their exposure to data and functions to which they do not require access.
See the Custom User Roles topic for more information on creating and updating custom roles.
Action Permissions
Action permissions allow you to customize a user’s ThreatQ permissions by enabling or blocking certain actions. ThreatQ provides action permissions for: Administrative Functions, Artifact Management, Objects & Context, Data Controls, Integrations, Orchestration, and Data Exchange.
Access to any area of ThreatQ not covered by Action Permissions defaults to the access level defined for the Primary Contributor default role.
See the Action Permissions section for more information on each permission’s options.
Custom Roles and Sharing Permissions
- Action permissions defined in a custom user role influence sharing permission options for dashboards, data collections, and investigations:
- If your custom role specifies view-only access to dashboards, you can only be added to a dashboard as a viewer.
- If your custom role specifies view-only access to data collections, you can only be added to a data collection as a viewer.
- If your custom role specifies view-only access to investigations, you can only be added to an investigation as a viewer.
In addition, the Sharing modal lists a view-only icon next to your name and only includes your name in searches with the Viewer filter enabled.
- View-only sharing permissions for all users take precedence over action permissions defined in a custom user role For example, even if your custom user role gives you Create, Edit, Delete permissions for data collections, you cannot edit or delete a data collection with a permission level of Everybody (Public).
Custom Roles and API Updates
ThreatQ enforces the action permissions associated with the user’s custom role when the user account sends a write request via the API.
For example, tquser1 does not have Create/Edit/Delete permission for object attributes and sends a write request that includes attributes. As a result, ThreatQ returns an error.
Custom Roles and Integrations/TQO Workflows
Custom role permissions control access to the pages that allow you to execute manual runs of integrations or TQO workflows. However, custom roll permissions do not apply to the objects and object context created/ingested. A manual feed or workflow run can ingest system objects and any type of associated context regardless of the permissions of the authenticated user who initiated the run.
When you update an instance’s ThreatQ license, each user account that has permission to access the User Management page will receive the following in-app notification to update all roles to include newly available permissions:
Due to a recent upgrade, some role permission configuration options for users may have changed. Visit the User Management page to update your settings.
This notification includes a link to the Role tab in the User Management page. The notification is sent for every license update, regardless of whether features were added or removed.
If your license update involves removing a product, any action permissions defined in custom user roles are also removed and must be manually added if you add the product at a later date. For instance, if your current license includes ThreatQ Investigations and you update to a new license that does not, any investigation action permission defined in a custom user role is removed.