Current ThreatQ Version Filter
Viewing the Activity Log
Default ThreatQ Role: Administrative or Maintenance
Custom Role - Action Permissions: See the TQO Requirements topic.
You can review the activity log for workflow in the workflow builder page.
- Open the workflow within the builder.
- Click on the Activity Log tab located above the node graph.
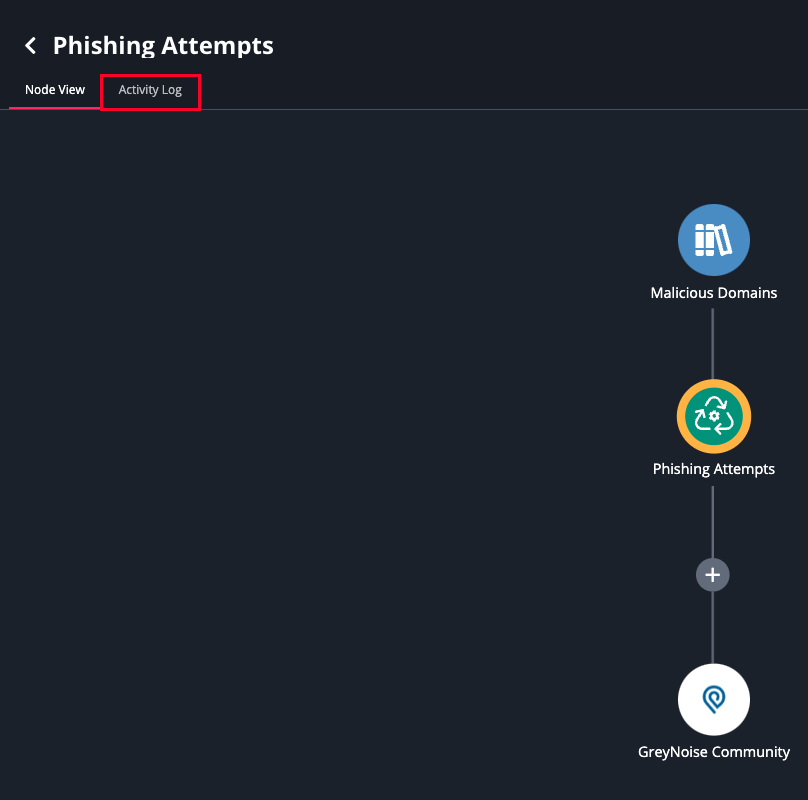
The Activity Log will load.
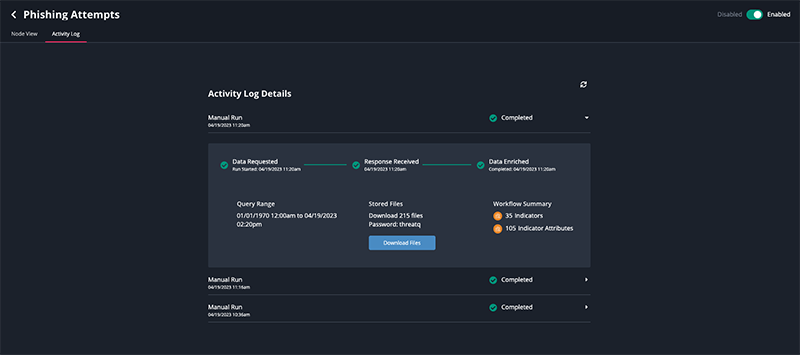
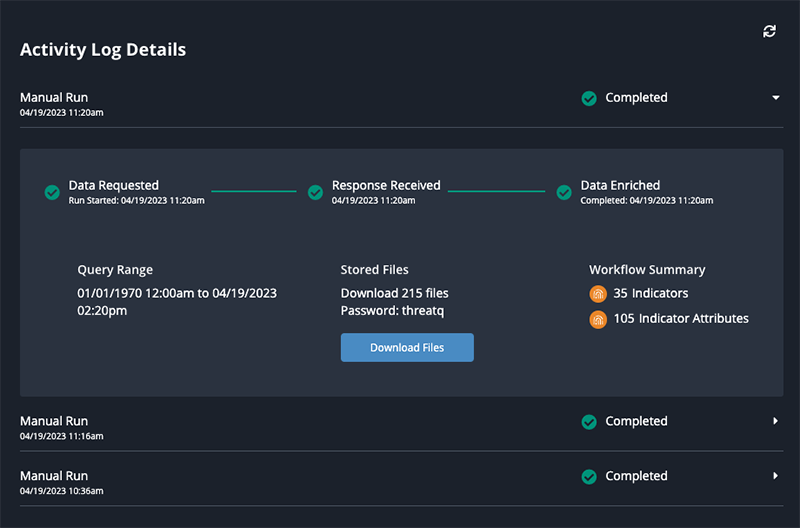
Activity Log Details
The Activity Log provides the following run information:
| Field | Description |
|---|---|
| Type of Run | Whether the run was a scheduled or manual run. |
| Data Requested | The timestamp of when the data was requested. |
| Response Received | The timestamp of when a response from the provider was received. |
| Data Enriched | The timestamp of when the action enrichment was completed. |
| Query Range | The dataset range for the information. |
| Stored Files | Files downloaded during the run and the password to open the files. If the workflow encountered errors, you can click the Download Files button to download a zip file(s) containing the error log(s). When you open the zip file(s) you are prompted to enter the Password displayed above the Download Files button. |
| Workflow Summary | A breakdown of the specific types of system objects were ingested during the run. |