About the TAXII Server
Default ThreatQ Role: Administrative or Maintenance
Custom Role - Action Permissions: Data Exchange - Edit Data Exchange Feeds
Trusted Automated eXchange of Intelligence Information (TAXII) is a transport protocol for transmitting threat intelligence data over HTTPS. The data transported by TAXII is formatted and stored using the Structured Threat Information eXpression (STIX) language.
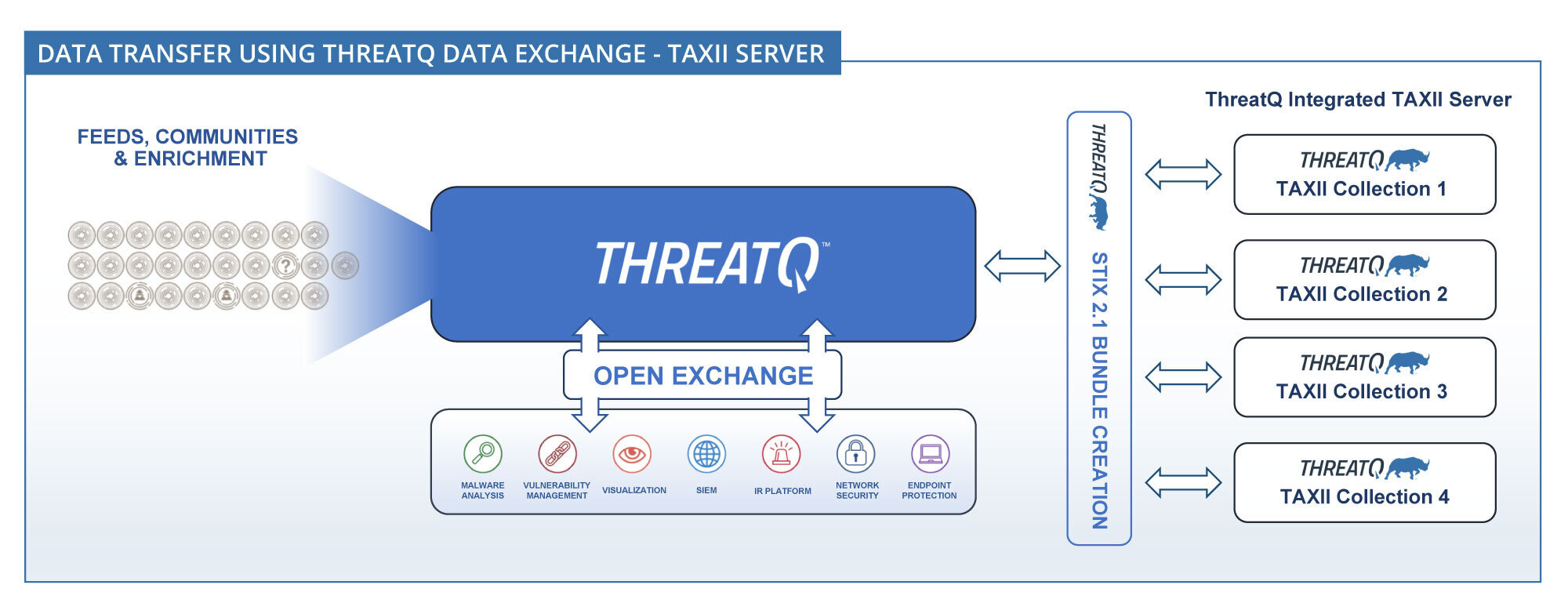
ThreatQ Data Exchange (TQX) allows you to configure a TAXII server, create a TAXII collection to specify the STIX object information you want to share, and add TAXII user credentials to control access to the TAXII collection files.
How It Works
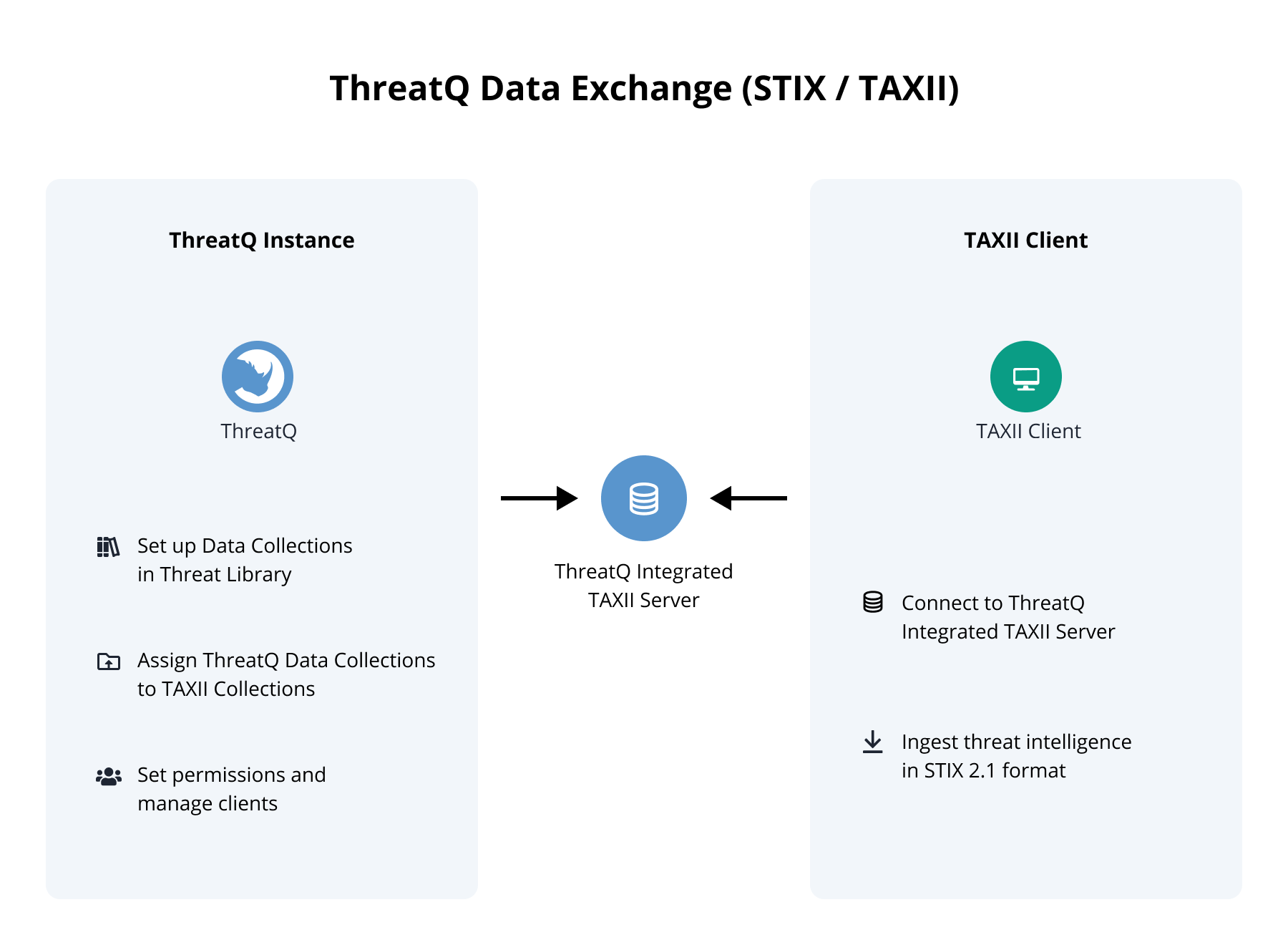
Tips and Tricks
- The data collection associated with a TAXII collection can include other object types but must include at least one STIX object type and the TAXII collection will only pull STIX object data. If you update the data collection so that it no longer contains STIX objects, the TAXII collection will be empty after the next run.
- TQX updates the objects included in a TAXII collection by searching the Threat Library for objects that match the collection criteria and have a modified_at date later than the last Threat Library search.
- When a TAXII collection is created, the first data pull will occur within 5 minutes. The next data pull will occur 24 hours after the first data pull started, unless:
- The data collection changes.
- The TAXII collection is disabled, and then re-enabled after 5 minutes have passed.
- The threatq-taxii server is restarted.
Due to the time required to populate the data for a TAXII collection, it is not available immediately after a data pull.
- Each TAXII collection run pulls data on the most recently modified 50K of each STIX object type. For example, if your data collection includes 250K objects, of which 75K are adversaries, 80K are campaigns, and the remainder are not STIX objects, the TAXII collection run will pull information on the most recently modified 50K adversaries and 50K campaigns.
- TAXII Server exports include up to 1,000 relationships per object.
Objects with more than 1,000 relationships return them in an indeterminate order. As a result, there is no sort method available to determine which of the relationships are included in the TAXII Server export.
- Currently, TQX only supports the use of a Third Party application to access STIX data from your TAXII server. TQX does not support the use of the TAXII server to transfer STIX object data between ThreatQ instances.
- If you delete the data collection associated with a TAXII collection, the TAXII collection is automatically disabled.
- STIX exports include an object's confidence value as attributes as long as the confidence value falls within the range from zero to one hundred.
- The data collection associated with a TAXII collection can include other object types but must include at least one STIX object type and the TAXII collection will only pull STIX object data. If you update the data collection so that it no longer contains STIX objects, the TAXII collection will be empty after the next run.
- Currently, TAXII collections are published daily and include the full result set from the selected data collection, not a delta.
- When a TAXII collection is created, the first data pull will occur within 5 minutes. The next data pull will occur 24 hours after the first data pull started, unless:
- The data collection changes.
- The TAXII collection is disabled, and then re-enabled after 5 minutes have passed.
- The threatq-taxii server is restarted.
Due to the time required to populate the data for a TAXII collection, it is not available immediately after a data pull.
- Each TAXII collection run pulls data on the most recently modified 50K of each STIX object type. For example, if your data collection includes 250K objects, of which 75K are adversaries, 80K are campaigns, and the remainder are not STIX objects, the TAXII collection run will pull information on the most recently modified 50K adversaries and 50K campaigns.
- TAXII collections do not include additional context of relational data for STIX objects.
- Currently, TQX only supports the use of a Third Party application to access STIX data from your TAXII server. TQX does not support the use of the TAXII server to transfer STIX object data between ThreatQ instances.
- If you delete the data collection associated with a TAXII collection, the TAXII collection is automatically disabled.
- STIX exports include an object's confidence value as attributes as long as the confidence value falls within the range from zero to one hundred.
STIX Objects
ThreatQ TAXII collections can include the following system objects:
|
|
|
For indicators, you can create STIX export bundles for the following indicator types:
|
|
|
|
Tips and Tricks
- STIX files generated from TAXII data collections:
- Include up to 1,000 relationships per object.
Objects with more than 1,000 relationships return them in an indeterminate order. As a result, there is no sort method available to determine which of the relationships are included in the TAXII Server export.
- Include an object's confidence value as an attribute as long as the confidence value falls within the range from zero to one hundred.
- Include an object's primary description only. If an object has multiple descriptions, only the primary description is included.
- Include indicator expiration timestamps in the valid_until field.
- Include up to 1,000 relationships per object.
- When you export system objects with the following location keys as attributes to a STIX file, the export process converts these attributes to STIX location objects: latitude, region, city, longitude, country, street address, precision, administrative area, postal code. STIX imports of location objects convert these objects to attributes.
- When you export an infrastructure object that includes Kill Chain: attributes to a STIX file, these attributes are exported as Kill Chain Phase information.
ThreatQ TAXII collections can include the following system objects:
|
|
|
For indicators, you can create STIX export bundles for the following indicator types:
|
|
|
|
Tips and Tricks
- STIX files generated from TAXII data collections:
- Do not include related objects.
- Include an object's confidence value as an attribute as long as the confidence value falls within the range from zero to one hundred.
- Include an object's primary description only. If an object has multiple descriptions, only the primary description is included.
ThreatQ Object Attribute Mapping
When you generate a STIX bundle based on a ThreatQ TAXII data collection, system object attributes are labelled based on STIX data mapping requirements. The following tables provide mapping information for key data elements and will be expanded upon in conjunction with system enhancements.
The following mappings apply to all ThreatQ system objects:
| ThreatQ Object Property | STIX Property |
|---|---|
| Confidence | confidence |
| Primary Description | description |
| Source | external reference |
The following table lists the STIX properties corresponding to specific ThreatQ object types.
| ThreatQ Object Type | STIX Properties | |
|---|---|---|
| Malware |
|
|
| Threat Actor |
|
|
| Attack Pattern |
|
|
| Identity |
|
|
| Intrusion Set |
|
|
| Tool |
|
|