ThreatQ Signature Operation
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 6.11.2 |
| Support Tier | ThreatQ Supported |
Introduction
The ThreatQ Signature Operation integration is designed to streamline the transformation and deployment of detection logic by converting Sigma rules (Custom Type signatures in ThreatQ) into KQL (Kusto Query Language) signatures. These KQL signatures can be seamlessly exported to Microsoft Azure Sentinel for immediate operational use. This simplifies detection rule management, enhances interoperability, and helps security teams accelerate threat response within their existing threat intelligence workflows.
The integration performs the following actions:
- Convert – transforms a Sigma rule into a KQL (Kusto Query Language) query and creates a new signature linked to the original object.
- Export to Sentinel – deploys the generated KQL rule to Microsoft Azure Sentinel and saves it in the specified workspace for use under the Log Queries tab.
The integration is compatible with ThreatQ Custom type signatures.
Prerequisites
The following required to run the Export to Sentinel action:
- An Azure Sentinel Workspace.
- Microsoft Azure Credentials including:
- Azure Tenant ID
- Azure Client ID
- Azure Client Secret
- Azure Subscription ID
- Azure Resource Group
- Azure Workspace Name
The user account needs to have the Log Analytics Contributor and Log Analytics Reader roles added.
Installation
Perform the following steps to install the integration:
The same steps can be used to upgrade the integration to a new version.
- Log into https://marketplace.threatq.com/.
- Locate and download the integration file.
- Navigate to the integrations management page on your ThreatQ instance.
- Click on the Add New Integration button.
- Upload the integration file using one of the following methods:
- Drag and drop the file into the dialog box
- Select Click to Browse to locate the integration file on your local machine
ThreatQ will inform you if the operation already exists on the platform and will require user confirmation before proceeding. ThreatQ will also inform you if the new version of the operation contains changes to the user configuration. The new user configurations will overwrite the existing ones for the operation and will require user confirmation before proceeding.
The operation is now installed and will be displayed in the ThreatQ UI. You will still need to configure and then enable the operation.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Operation option from the Type dropdown (optional).
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description Azure Tenant ID The Directory (Tenant) ID for your Azure Active Directory. Azure Client ID The Application (Client) ID for the registered Azure app used to authenticate. Azure Client Secret The Client Secret associated with the Azure app. This is used for secure authentication. Azure Subscription ID The Subscription ID under which the Azure Sentinel resources are deployed. Azure Resource Group The name of the Resource Group containing the Azure Sentinel workspace. Azure Workspace Name The name of the Azure Sentinel (Log Analytics) workspace.
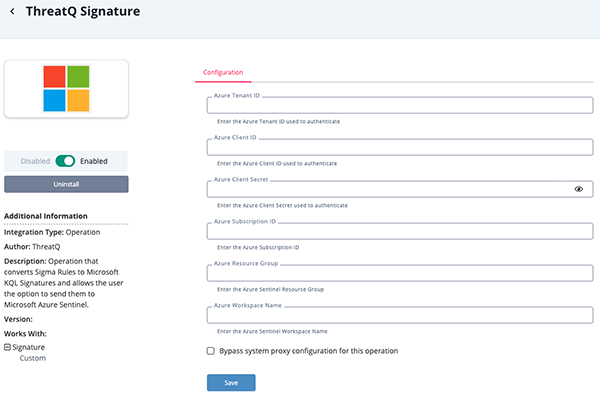
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
Actions
The operation provides the following actions:
| Action | Description | Object Type | Object Subtype |
|---|---|---|---|
| Convert | Transforms a Sigma rule into a KQL (Kusto Query Language) query and creates a new signature linked to the original object. | Signature | Custom |
| Export to Sentinel | Deploys the generated KQL rule to Microsoft Azure Sentinel and saves it in the specified workspace for use under the Log Queries tab. | Signature | Custom |
Convert
The Convert action transforms a Sigma rule into a KQL (Kusto Query Language) query and creates a new signature linked to the original object. This new object will be tagged with kql.
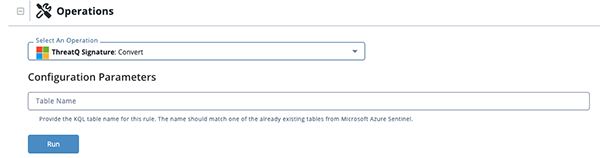
Configuration Run Parameter
The following configuration run parameter is available after selecting the Convert action.
| Parameter | Description |
|---|---|
| Table Name | The KQL table name for this rule. An example of a table name is RiskyUsers. |
Export to Sentinel
The Export to Sentinel action deploys the generated KQL rule to Microsoft Azure Sentinel and saves it in the specified workspace for use under the Log Queries tab.
To run the query in Azure, navigate to the Sentinel Workspace > Logs > Queries Hub > Category: Other and then select the query you want to run.
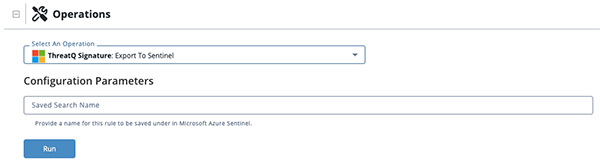
Configuration Run Parameter
The following configuration run parameter is available after selecting the Export to Sentinel action.
| Parameter | Description |
|---|---|
| Saved Search Name | The name under which the rule will be saved in Microsoft Azure Sentinel. You can also provide an existing name to update a previous saved search. |
Known Issues / Limitations
- Once a Sigma Rule has been converted to KQL and a new signature is created, that existing signature will not be updated by running the convert action.
- You can send a Sigma Rule to Microsoft Azure Sentinel as the ThreatQ platform does not currently support specific Signature types.
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| ThreatQ Signature Operation Guide v1.0.0 | 6.11.2 or Greater |