Palo Alto Networks Wildfire Operation
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.2.0 |
| Compatible with ThreatQ Versions | >= 3.6.0 |
| Support Tier | ThreatQ Supported |
Introduction
The ThreatQuotient for Palo Alto Wildfire Operation allows a ThreatQ user to ability to submit files to Wildfire, retrieve the report, and query Wildfire for a verdict on a hash.
The operation provides the following actions:
- Submit File - submits a file to Wildfire’s file analysis engine.
- Get Report - queries Wildfire for any hits on a hash.
- Get Verdict - queries Wildfire for any hits on a hash and returns a single attribute of the verdict. Possible verdicts include Malware, Phishing, Grayware, Benign
The operation is compatible with Files and MD5 and SHA-256 type Indicators.
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Operation option from the Type dropdown (optional).
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description Wildfire Host Your Wildfire on premise URL. The cloud URL is set as the default. API Key Your Wildfire API Key from Palo Alto. - Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
Actions
The operation provides the following actions:
| Action | Description | Object Type | Object Subtype |
|---|---|---|---|
| Submit File | Submits a file to Wildfire’s file analysis engine. | File | See the supported File Types table |
| Get Report | Queries Wildfire for any hits on a hash. | Indicator | MD5, SHA-256 |
| Get Verdict | Queries Wildfire for any hits on a hash and returns a single attribute of the verdict. | Indicator | MD5, SHA-256 |
Submit File
The Submit File action allows you to submit a file to Wildfire’s file analysis engine. The response will include the hashes for the given file so you can relate them and fetch the report once the analysis is finished.
Example Output
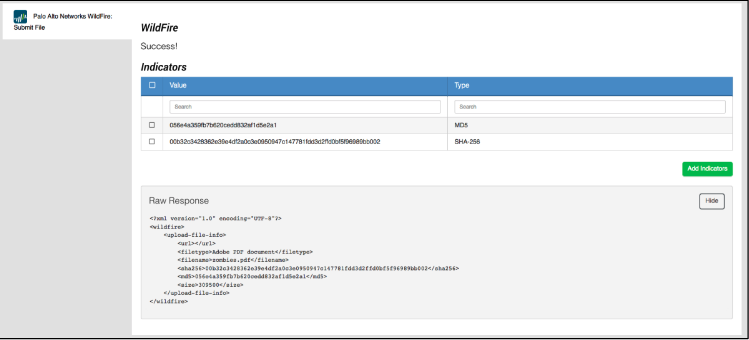
Supported File Types
The following are the file types support for Palo Alto Wildfire:
| File Types Supported | Wildfire Global Cloud | Wildfire Private Could (wildfire appliance) |
|---|---|---|
| Links contained in emails | Yes | Yes |
| Android Application Package (APK) | Yes | No |
| Java Archive (JAR) | Yes | Yes |
| Microsoft Office | Yes | Yes |
| Portable Executable (PE) | Yes | Yes |
| Portable Document Format (PDF) | Yes | Yes |
| Mac OS X Files | Yes | No |
| Linux (ELF) Files | Yes | No |
| Archive (RAR, 7-Zip) | Yes | No |
Get Report
The Get Report action action allows you to query Wildfire for any hits on a hash. If found, it will return a report for the hash in two forms. First, it will download a PDF report, and then upload and relate it to the ThreatQ hash. Second, it will parse the returned XML report and display some results immediately to your operation results window. Here is an example result when you run the action.
Example Output
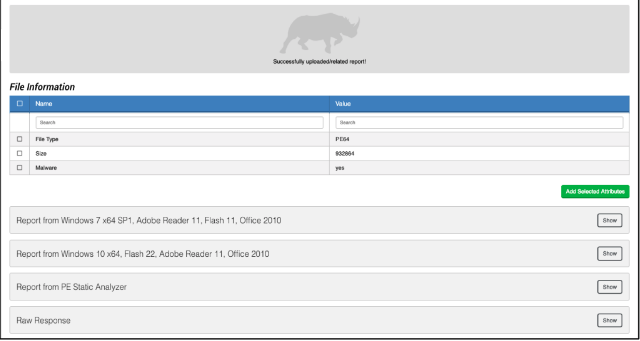
Get Verdict
The Get Verdict action allows you to query Wildfire for any hits on a hash. If found, it will return a single attribute informing you of the verdict on the hash. The available verdicts are: Malware, Grayware, Phishing, or Benign.
Example Output
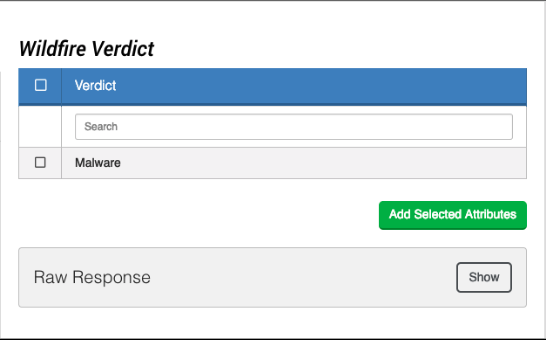
Change Log
- Version 1.2.0
- N/A
- Version 1.1.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Palo Alto Wildfire Operation Guide v1.2.0 | 3.6.0 or Greater |
| Palo Alto Wildfire Operation Guide v1.1.0 | 3.6.0 or Greater |