McAfee Active Response (AR) Operation
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 2.0.3 |
| Compatible with ThreatQ Versions | >= 4.31.0 |
| Support Tier | ThreatQ Supported |
Introduction
The McAfee Active Response (AR) Operation enables users to enrich indicators from McAfee AR.
The operation provides the following actions:
- Query Hash - queries McAfee Active Response for sightings of hashes on deployed agents.
- Query Netflow - queries McAfee Active Response for traffic related to an IP Address, either as a source or destination.
The operation is compatible with the following indicator types:
- IP Address
- MD5
- SHA-1
- SHA-256
Prerequisites
The following items are required to run the McAfee AR Operation.
- A route between ThreatQ and McAfee ePO.
- The following McAfee products:
- ePO with an installed Active Response extension.
- Active Response server connected to ePO.
- McAfee DXL and Active Response SDKs installed in ThreatQ. This is performed after installing the operation and before configuring it in the ThreatQ UI.
Installing McAfee DXL and Active Response SDKs
Follow the steps below for the configuration.
- SSH into ThreatQ.
- Activate Python 3.5:
source /opt/threatq/python/bin/activate
- Install the McAfee DXL and AR SDKs:
pip install dxlclient dxlmarclient
- Generate certificates for authenticating the connection between ThreatQ and McAfee ePO.
Before executing the commands, confirm that you have the hostname/IP address, username and password for ePO available.
source /opt/threatq/python/bin/activate
cd /var/tmp
python -m dxlclient provisionconfig /var/tmp/dxl_certs/ <McAfee ePO Hostname or IP Address> threatq-certs - Change the owner of the generated files to
apache. This is the system user that ThreatQ uses to execute the operations in the UI.sudo chown -R apache:apache dxl_certs/
- Add the generated certificates to the trusted store in McAfee ePO:
- Log into ePO as an admin via the UI.
- Navigate to Server Settings -> DXL Topic Authorization.
- Click on the Edit button in the lower right corner and select the topics:
TIE Server Set Enterprise ReputationTIE Server External Reputation Provider EventActive Response Server API
- With the topics selected, click on Actions, located in the lower-left corner, and select Send Certificates.
- Select the entry in the certificate list called
threatq-certsand click OK. - Click Save when you return to the previous page.
- Log out of ePO.
- Log into the ThreatQ UI to configure and then enable the operation.
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Operation option from the Type dropdown (optional).
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description Certificate Path Enter the path to the certificate for McAfee MAR.
The default is/var/tmp/dxl_certs/.ePO IP Enter the host or IP address for ePO. ePO Port Enter the ePO communication port.
The default is 8443, which can be changed if needed.ePO Username Enter the username for ePO. ePO Password Enter the password for ePO. MAR Result Limit The maximum number of items to return from MAR.
The default value is 20.
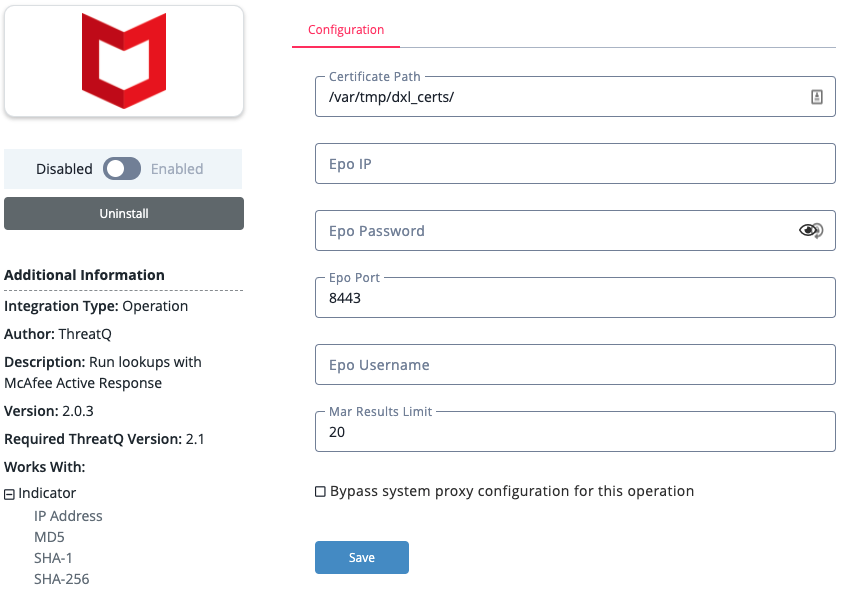
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
Actions
The operation provides the following actions:
| Action | Description | Object Type | Object Subtype |
|---|---|---|---|
| Query Hash | Queries McAfee Active Response for sightings of hashes on deployed agents | Indicator | MD5, SHA-1, SHA-256 |
| Query Netflow | Queries McAfee Active Response for traffic related to an IP Address, either as a source or destination | Indicator | IP Address |
Query Hash
The Query Hash action queries McAfee Active Response for sightings of hashes on deployed agents. The operation uses the McAfee SDK to execute the search actions on ePO.
Query Netflow
The Query Netflow action queries McAfee Active Response for traffic related to an IP Address, either as a source or destination. The operation uses the McAfee SDK to execute the search actions on ePO.
This action has the following configutation options:
| Option | Description |
|---|---|
| Destination IP | Search for the IP Address as a destination IP. |
| Source IP | Search for the IP Address as a source IP. |
Change Log
- Version 2.0.3
- Updated ThreatQ UI configurations for the operation
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| McAfee Active Response (AR) Operation Guide v2.0.3 | 4.31.0 or Greater |