Cuckoo Sandbox Operation
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 3.6.0 |
| Support Tier | ThreatQ Supported |
Introduction
The ThreatQuotient for Cuckoo Operation allows a ThreatQ user to submit files and FQDNs/URLs to their Cuckoo Sandbox instance. The file will be sandboxed by executing one action, and the report for the sandboxing will be downloaded by executing another action.
The operation provides the following action:
- Submit - submits the selected file to your Cuckoo Sandbox instance to be sandboxed.
- Get Reports - downloads the sandbox report on the object.
The operation is compatible with Attachments as well as FQDN and URL Indicator types.
This operation supports the following fields/reports:
- JSON Report parsing
- HTML Report download/upload
- General Information
- Target Information
- Network Information
- Signatures (as attributes)
- Dropped Files
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Operation option from the Type dropdown (optional).
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description Host URL The Host or IP of your Cuckoo Sandbox instance. Api URL The Host or IP of your Cuckoo Sandbox API instance. API Key Your API token from Cuckoo Sandbox (if Bearer token is enabled). - Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
Usage
This operation applies to attachments/files, FQDNs, and URLs within ThreatQ. You will not be able to scan any other object type.
- Find a Malware Sample or FQDN/URL in ThreatQ that you want scanned
- Navigate to its'
Operationssection- You should see a
Cuckoo Sandboxentry
- You should see a
- When you run the
Submitoperation, you will get a popup window asking you if you want to re-submit the file. If this is your first run on the current ThreatQ object, ignore it and run it. If you have already ran theSubmitoperation on the ThreatQ object, then you will choose whether you want to resubmit the file, or not. Selecting no will abort the submission.Once the file is ran, the result should be similar to this:
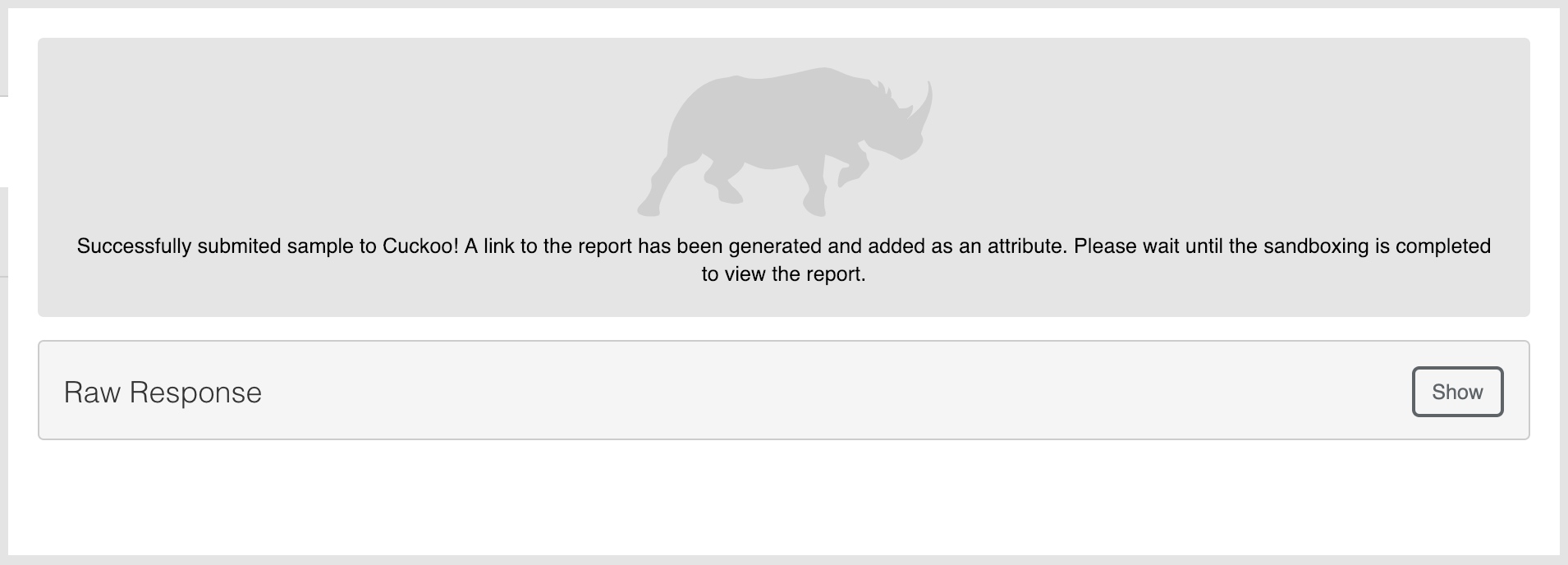
You must run the
Submitoperation before running theGet Reportsoperation. However, if you have a report you want in ThreatQ but do not want to rescan it, you can add an attribute to the ThreatQ object to have it fetch the report.- Attribute Name: Cuckoo Report Link
- Attribute Value: http://<cuckoo-host>/analysis/<scan-id>/summary
- When you run the
Get Reportsoperation, the plugin will look for anyCuckoo Task Summary Links in the ThreatQ object's attributes. If it finds one, it will use that link to get the reports associated with it. It will download the report, upload it to ThreatQ, and then relate it to the current ThreatQ object.
Once the operation is ran, this should be the result:
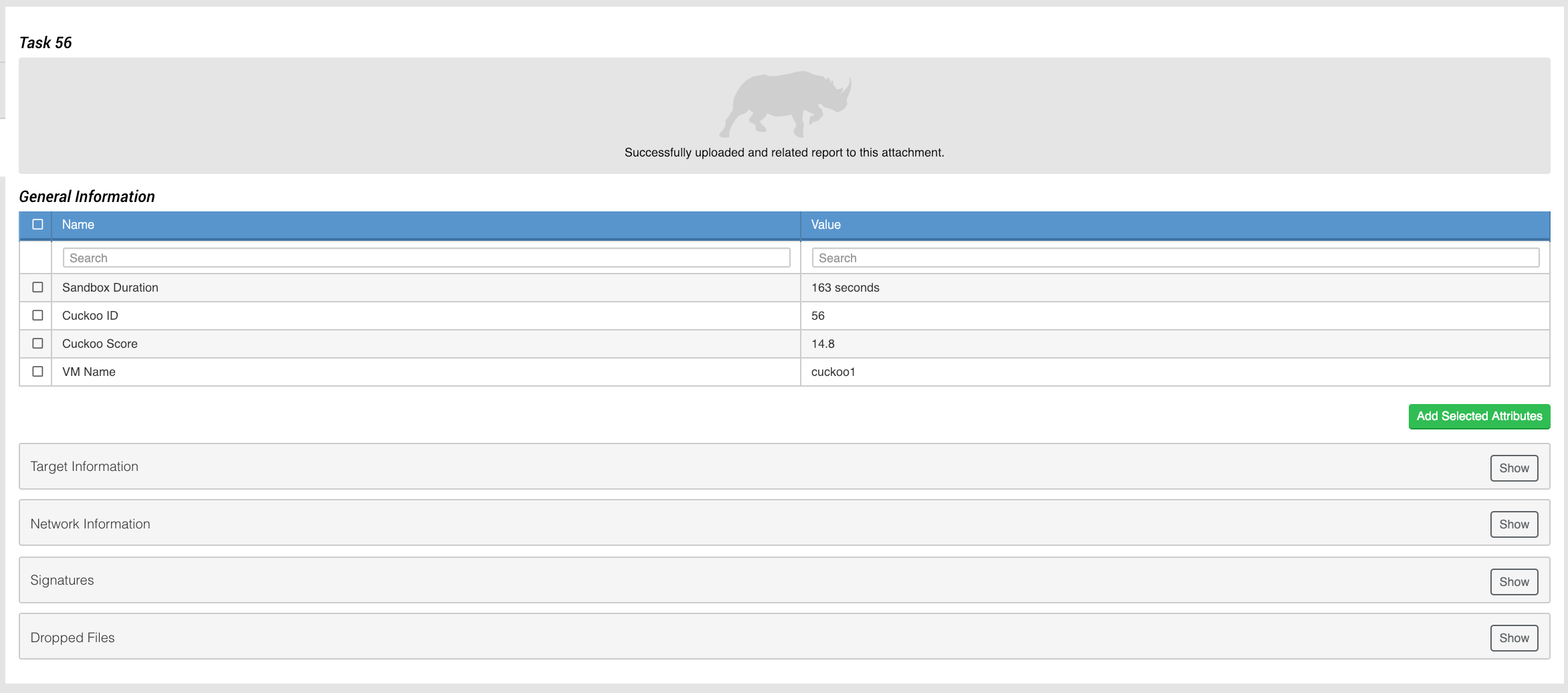
Reports will automatically be downloaded and related to the ThreatQ object. Refresh the page to see the relationship
If you get an error saying there is no HTML report, or you get an empty response back, it probably means the sandboxing is not finished.
Known Issues / Limitations
- By default, the JSON report is enabled. The HTML report will only be downloaded if you have enabled HTML reporting in Cuckoo. This operation does not support the PDF reporting because the formatting in it is not handled as well as it is in the HTML report.
- You must run the
Submitoperation before running theGet Reportsoperation. However, if you have a report you want in ThreatQ but do not want to rescan it, you can add an attribute to the ThreatQ object to have it fetch the report.- Attribute Name: Cuckoo Report Link
- Attribute Value: http:///analysis//summary
- Reports will automatically be downloaded and related to the ThreatQ object. Refresh the page to see the relationship
- If you get an error saying there is no HTML report, or you get an empty response back, it probably means the sandboxing is not finished.
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Cuckoo Sandbox Operation Guide v1.0.0 | 3.6.0 or Greater |