Cisco Umbrella Investigate Operation
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 2.0.0 |
| Compatible with ThreatQ Versions | >= 4.57.0 |
| Support Tier | ThreatQ Supported |
Introduction
The Cisco Umbrella Investigate Operation for ThreatQuotient enables a user to enrich indicators in ThreatQ with context from Cisco Umbrella.
The operation provides the following actions:
- Enrich - enriches a domain with contextual or historical metadata.
- Get Samples - retrieves Cisco Threat Grid samples that are related to a given domain, IP, or URL.
- Reverse WHOIS - retrieves domains related to a given email address.
- Get Associated Names - retrieves domains related to a given IP Address.
- Latest Malicious Domains - retrieves a list of malicious domains related to a given IP Address.
The operation is compatible with the following indicator types:
- Email Address
- FQDN
- IP Address
- URL
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Operation option from the Type dropdown (optional).
- Click on the integration entry to open its details page.
- Enter the following parameter under the Configuration tab:
Parameter Description API Key Your Cisco Umbrella Investigate API Key.
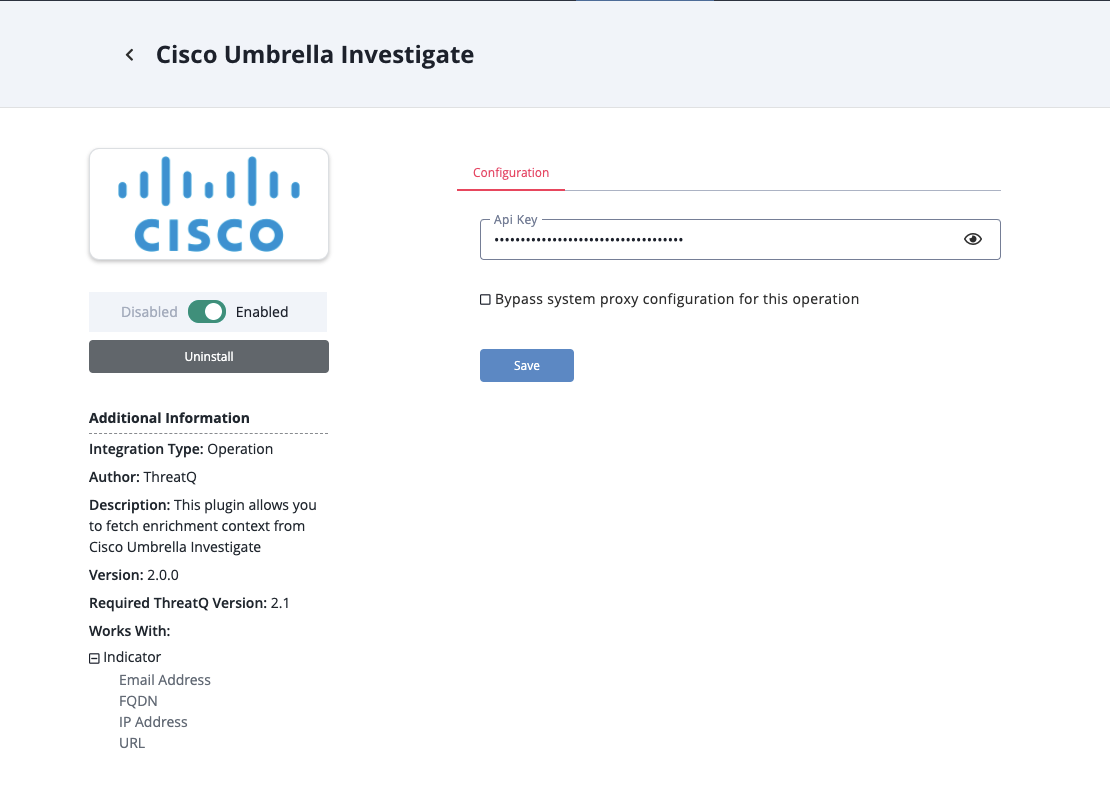
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
Actions
The operation provides the following actions:
| Action | Description | Object Type | Object Subtype |
|---|---|---|---|
| Enrich | Enriches a domain with contextual or historical metadata. | Indicator | FQDN |
| Get Samples | Retrieves Cisco Threat Grid samples that are related to a given domain, IP, or URL. | Indicator | FQDN, IP Address, URL |
| Reverse WHOIS | Retrieves domains related to a given email address. | Indicator | Email Address |
| Get Associated Names | Retrieves domains related to a given IP Address. | Indicator | IP Address |
| Latest Malicious Domains | Retrieves a list of malicious domains related to a given IP Address. | Indicator | IP Address |
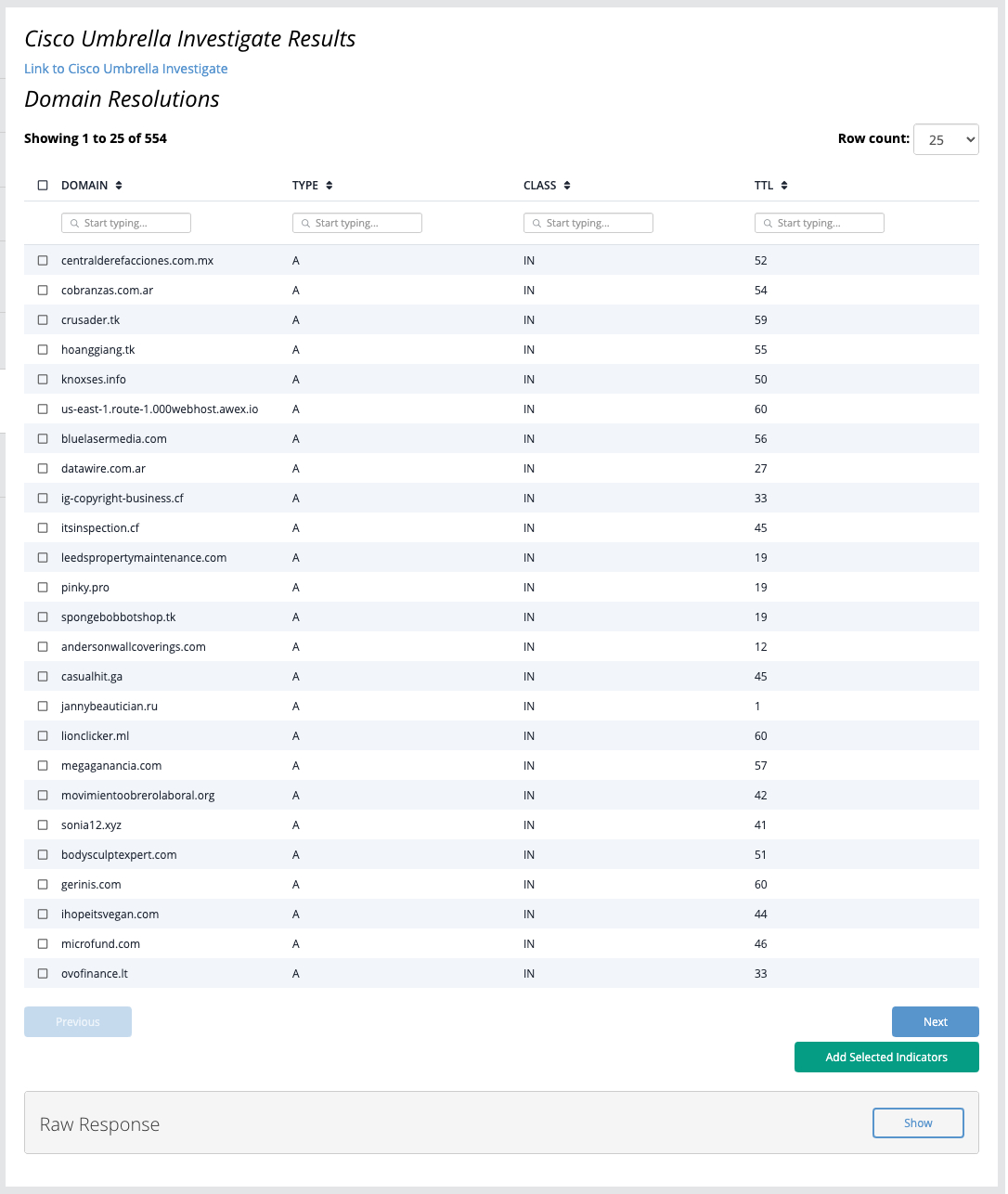
Enrich
The Enrich action enriches a domain with contextual or historical metadata.
Action Parameters
The following configuration option is provided when using the action on an object:
| Parameter | Description |
|---|---|
| Select Enrichment Options | Select one or more enrichment options (API Endpoints) to use to fetch metadata. Options include:
|
Enrich Example Result
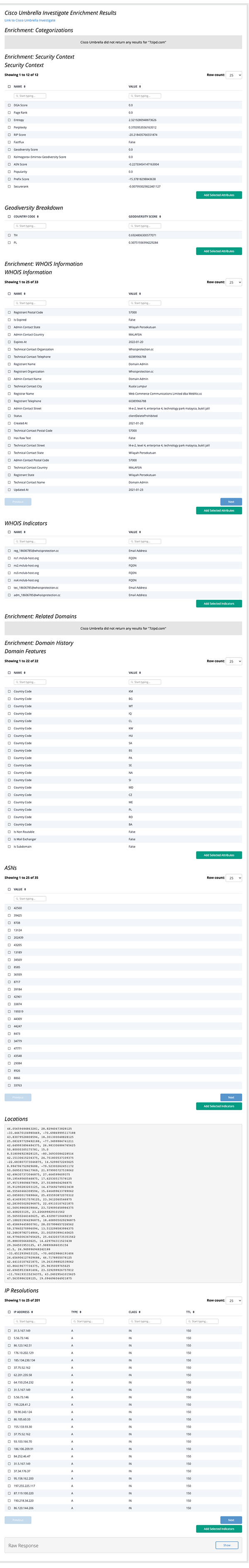
Get Samples
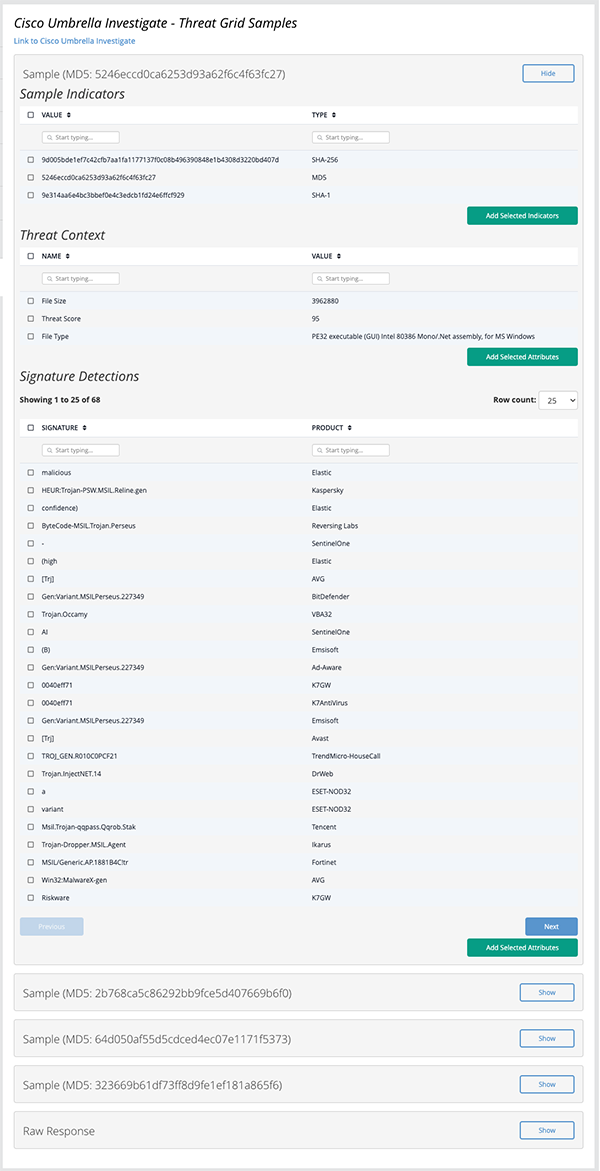
The Get Samples action fetches Cisco Threat Grid samples that are related to a given domain, IP, or URL.
Get Samples Example Result
Reverse WHOIS
The Reverse WHOIS action fetches domains related to a given email address.
Reverse WHOIS Example Result
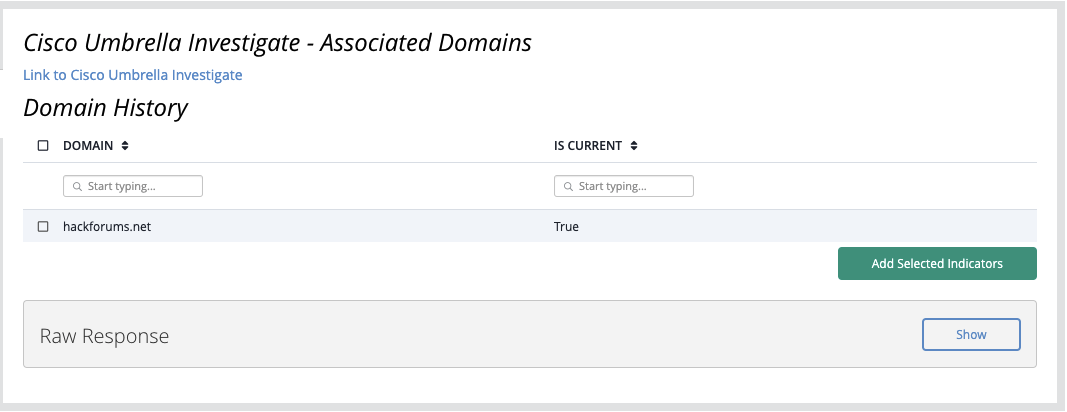
Get Associated Names
The Get Associated Names action fetches domains related to a given IP Address.
Get Associated Names Example Result
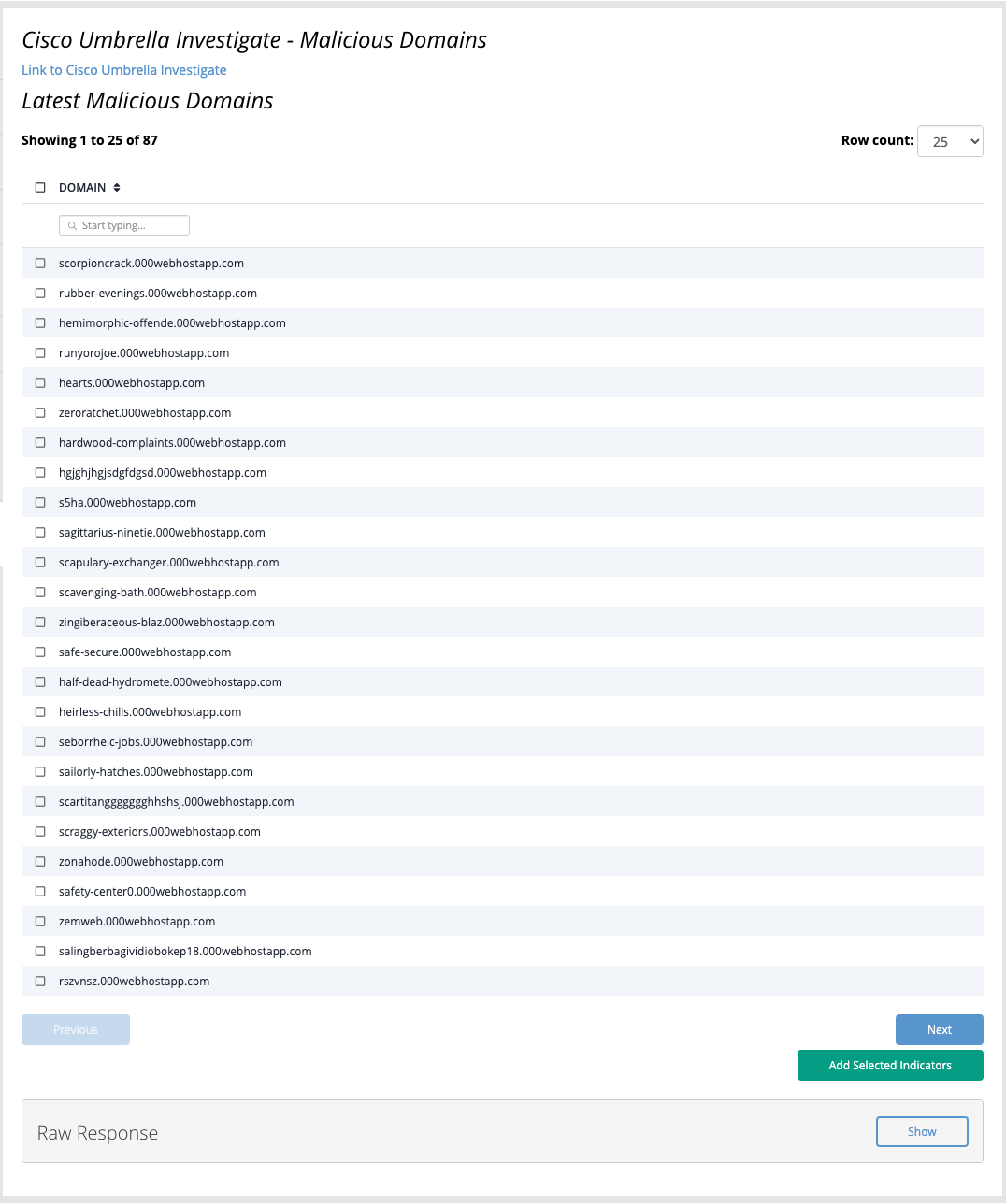
Latest Malicious Domains
The Latest Malicious Domains action fetches a list of malicious domains related to a given IP Address.
Latest Malicious Domains Example Result
Change Log
- Version 2.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Cisco Umbrella Investigate Operation Guide v2.0.0 | 4.57.0 or Greater |