ThreatQ Google Chrome Extension
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.1.0 |
| Compatible with ThreatQ Versions | >= 5.6.0 |
| Minimum ThreatQ User Account Role | Primary Contributor |
| Supported Browsers | Google Chrome |
| Compatible with Google Chrome Versions | >=87.x.x |
| Support Tier | Developer Supported |
| Support Contact | chrome-team@threatq.com |
| Google Chrome Store | https://chrome.google.com/webstore/detail/threatq-extension/kaoghaifdcjeaabfbdggomcpdgdfdjlm |
Introduction
The Chrome Extension to give an analyst integration capabilities on any browser page, with ThreatQ.
The ThreatQ Chrome Extension gives analysts a quick and easy to use assistant while navigating web pages. The extension will allow analysts to perform quick lookups, automatically extract information from web pages, and ultimately, conduct thorough investigations.
Analysts will be able to quickly identify key pieces threat intelligence from web pages, and immediately figure out if they are relevant to their threat hunt or investigation. Additional context can be added to tracked threat objects and can be synced directly with a ThreatQ instance. Reports can be built directly from web pages and imported into ThreatQ, along with any relevant attribution, tags, and relationships.
The extension will be able to assist analysts in numerous ways, making them more efficient by giving them the tools they need to do their work.
Installation
- Navigate to the Chrome Web Store and search for
ThreatQ.You can also navigate directly to the entry using the following link:
https://chrome.google.com/webstore/detail/threatq-extension/kaoghaifdcjeaabfbdggomcpdgdfdjlm - Click on the ThreatQ Extension listing if you used the Chrome Web Store search method. Otherwise, skip to step 3.
- Click on the Add to Chrome button.
The extension will now be installed on your browser. You will still need to configure the extension.
Configuration
Use the following steps to configure the ThreatQ Chrome Extension. You will first need to pin the extension to your browser's toolbar. Once the extension has been pinned, you will be able to access the extension's UI by clicking on the ThreatQ rhino icon.
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
Connection Options
- Once the extension popup is open, click on the Config tab.
- In the Connection tab, you will configure your Authentication Settings:
Parameter Description ThreatQ Host Enter your ThreatQ host (schema optional). Do not provide any URL paths. ThreatQ Username Enter the username for the account you want to use with the extension. To authenticate and act on behalf of the user when executing actions against ThreatQ. ThreatQ Password Enter the password associated with the above user account. ThreatQ OAuth Client ID Enter your API Credentials found in your user profile within ThreatQ.
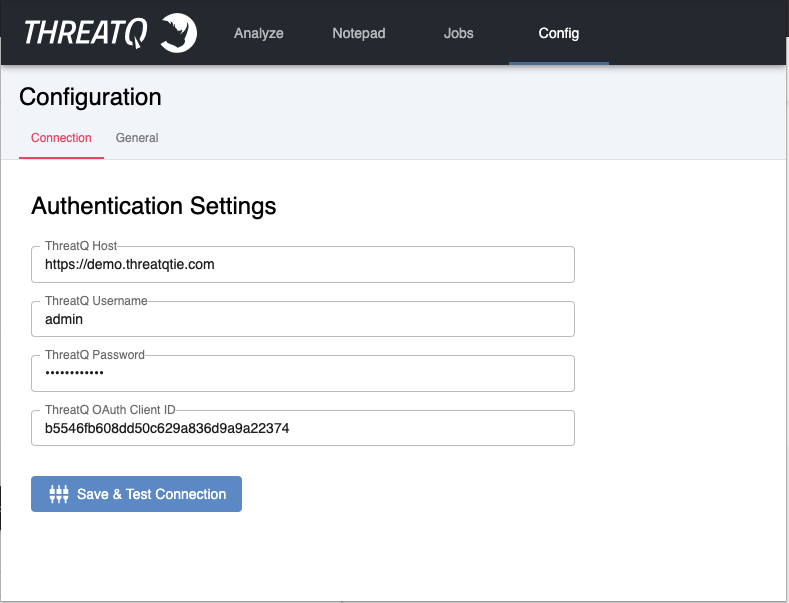
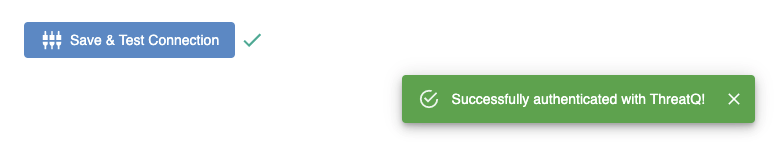
- Once you have entered your credentials, click on the Save & Test Connection button. If everything connects, you will see a green popup message saying you have successfully authenticated with your ThreatQ instance.
General Options
- Click on the Config tab and select General.
- Enter the following parameters:
Parameter Description Background Scanning Enabling this will allow the extension to automatically scan your current browser page for indicators, preloading them into the Analyze page within the extension popup. Default Indicator Status The status to give indicators that are quickly added via the Chrome Extension. Default Whitelist Status You can set a custom Whitelist status for indicators that you mark Whitelisted. This can be used if your ThreatQ workflow includes a different status class for Whitelisted indicators. Investigation Name This is the name of the investigation that you can sync with your Notepad. If the investigation does not already exist, you will be prompted to create it when you choose to sync your notepad with the investigation.Default Source Name This field allows you to set a default source name for all objects loaded into the Chrome Extension. Upon uploading selected objects to ThreatQ, this default source name will be applied.
Usage
This section will provide you with details on how you can use the ThreatQ Chrome Extension.
Entry Points
Once the ThreatQ Chrome Extension is installed, there are a few entry points to using the extension. Below are the entry points, along with a brief description.
Extensions Toolbar Popup
The extension can be accessed via your Chrome browser's toolbar, to the right of your URL bar. If you do not see a ThreatQ icon, you may need to click the puzzle piece icon and pin the ThreatQ Extension.
Right Click (no selection)
You'll also notice that when you right click a webpage, you now have a new context menu entry for ThreatQ. If nothing is selected when you make the right-click action, you will be given the following context menu options:
| Parameter | Description |
|---|---|
| Highlight Indicators | Selecting this will highlight all indicators on your current web page . |
| Highlight Threat Actors | Selecting this will highlight all “standardized” Threat Actor names on your current web page. This includes APTs, TEMPs, UNCs, DEVs, TAs, Threat-Groups, and CrowdStrike Actors. |
| Highlight MITRE Techniques | Selecting this will highlight all MITRE ATT&CK Techniques on your current web page. The techniques must be in their “TID” form. |
| Highlight MITRE Tactics | Selecting this will highlight all MITRE Tactics on your current web page. Example: Exfiltration, Execution, Persistence, etc. |
| Open ThreatQ | Selecting this will quickly open the linked ThreatQ instance in a new tab. |
All highlight options will modify the HTML of your current web page, adding in a box around each item found. Hovering over an item will show an interactive tool tip that you can use to view information about the highlighted item, as well as perform actions on the highlighted item.
Right Click (with selection)
The right-click actions are a bit different if you have actual text selected by your cursor. If text is selected, you will be able to perform actions such as:
| Parameter | Description |
|---|---|
| Quick Search | Selecting this perform a quick search against ThreatQ. You will receive an OS-level notification if the selection was found or not. If the selection was found, the result will be added to your Notepad. |
| Create Report | Selecting this will take all the selected text/HTML, and create a report for it within the extension’s Notepad. This will maintain all HTML formatting, which you’ll be able to view within the extension’s object details popup (eye icon next to each record). A source name will automatically be detected and applied to the Report object.
Additional context can be added to the report before upload, such as tags, attributes, sources, etc. |
| Import Indicators | electing this will take all the selected text and send it to ThreatQ’s Indicator Import workflow.
This requires the authenticated user in the Chrome Extension to match the user you use to login via the UI. |
| Add to Notepad | Selecting this will add the selected text to the extension’s Notepad page. |
| Add to Analyze | Selecting this will add the selected text to the extension’s Analyze page. |
Tabs & Layout
There are four main tabs in the extension:
Analyze
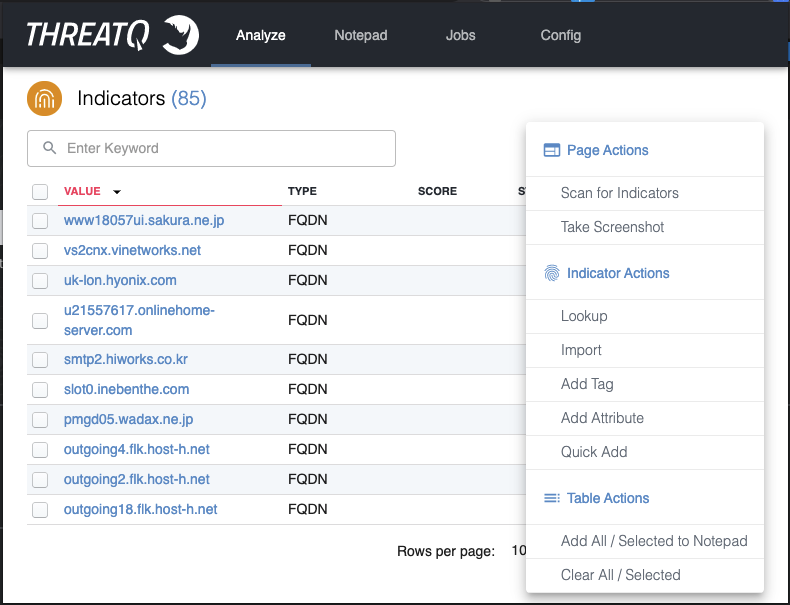
The Analyze tab will reflect your current browser tab, and the data in it only persists while you stay in the same browser tab, when Background Scanning is enabled. When you change tabs, the extension will automatically scan the webpage for indicators, and present them in the Analyze tab to be interacted with. If the Scan for Indicators optionis enabled, those items will persist in the Analyze tab until you manually clear it. On the Analyze page, you will be able to add context back to ThreatQ, perform lookups, or add an indicator to your Notepad.
Notepad
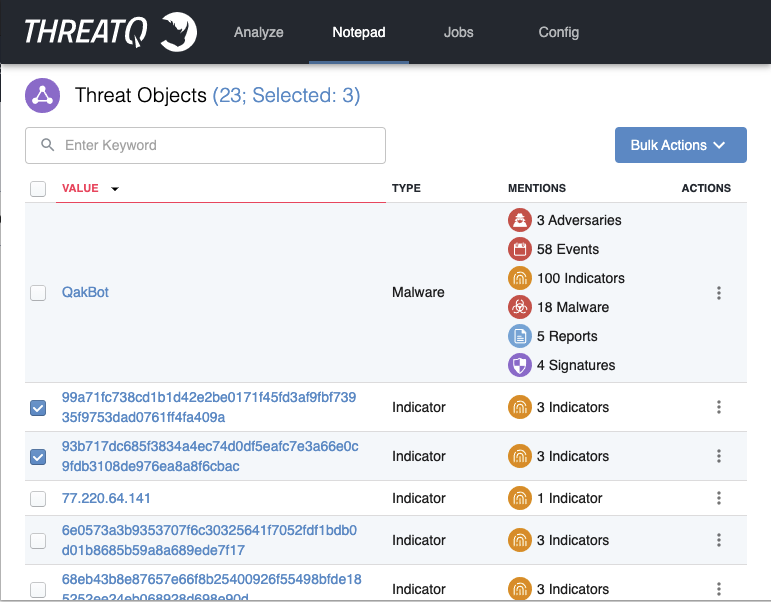
The Notepad tab is a cache and storage for indicators and other entities that you have curated and saved, to be investigated. To add an indicator or entity to this extension tab, either use the extension's right-click actions or the Bulk Actions in the Analyze tab. Once data is in your notepad, it will persist even when you close your browser. From this tab, you can sync data with your investigations, find mentions using the ThreatQ Threat Library, view the object's details, add relationships, add attributes, and more.
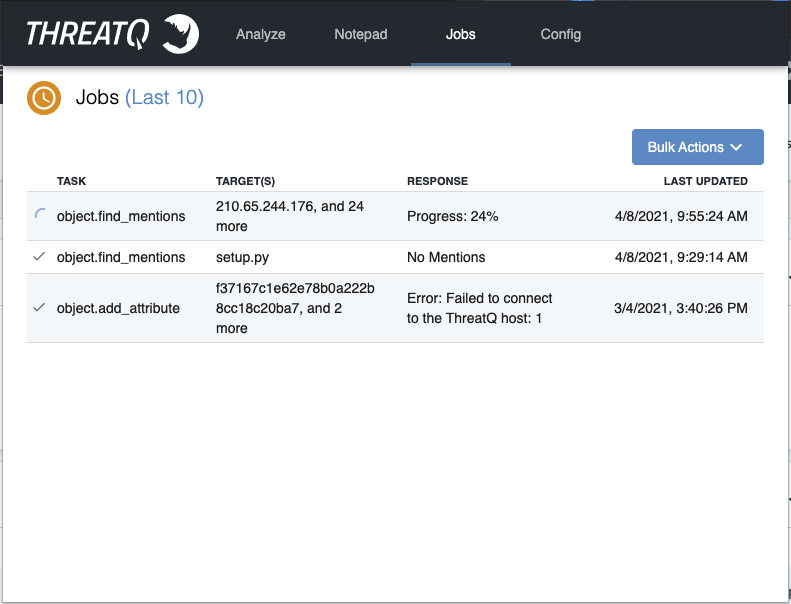
Jobs
The Jobs tab will show any background tasks that are being executed, in the execution queue, or have finished executing. Any bulk action or right click action you take will create a job to handle the action, and you will be able to see them listed in this tab. You will be able to see the status and response for each task, which can give you visibility into what the extension is currently "working on." You are also given Bulk Actions on this page to retry failed jobs or manage the jobs table.
Config
This extension tab is where you will configure your connection to ThreatQ, as well as setup some general configuration options. For more information, see the Configuration section.
Bulk Actions
Throughout the extension's popup window, you will see a drop-down called, Bulk Actions. These are actions you can execute in bulk, either on the selected items from the table, or all of the items from the table. The following Bulk Actions are available:
Analyze Bulk Actions
Page Actions
| Action | Details |
|---|---|
| Scan for Indicator | This will scan your current page for indicators and place anything found into the Analyze tab's table. Background Scanning does not need to be on for this feature. |
Indicator Actions
| Action | Details |
|---|---|
| Lookup | This will perform a lookup for the selected (or all) indicators. If found, the score and status will be added to the entry within the table. |
| Import | This action is the same as the Import Indicator(s) right-click action. It will take all the selected (or all) indicators, and run them through the ThreatQ Indicator Import workflow in a new tab. |
| Add Tag | This action will allow you to bulk add tags to indicators within the analyze tab. |
| Add Attribute | This action will allow you to bulk add attributes to indicators within the analyze tab. |
| Upload | This action will quickly upload the indicator. No indicator import workflow. It will use the defaults you set for the status and immediately add the indicator to ThreatQ. |
| Inter-relate Selected | This action will relate all selected indicators to each other, within ThreatQ. |
| Create Event with Selected | This action will create an event for the selected indicators, within ThreatQ. You will be prompted for details for the Event. |
Table Actions
| Action | Details |
|---|---|
| Add All / Selected to Notepad | This will add the selected (or all) indicators to your notepad. The indicators will not be removed from the Analyze page until you change tabs. |
| Clear All / Selected | This will clear the selected (or all) indicators in your analyze table. |
Notepad Bulk Actions
You can perform the following Note Bulk Actions:
Object Actions
| Action | Details |
|---|---|
| Find Mentions | This action will perform a Threat Library mentions lookup, and return a list of object counts for the given indicator or other threat object. |
| Add Tag | This action will allow you to bulk add tags to objects within the notepad tab. |
| Add Relationship | This action will allow you to bulk add relationships to objects within the notepad tab. |
| Add Attribute | This action will allow you to bulk add attributes to objects within the notepad tab. |
| Upload | This action will quickly add the object. No object import workflow. It will use the defaults you set in your configuration. |
| Inter-Relate Selected | This action will relate all selected objects to each other, within ThreatQ. |
Investigation Actions
| Action | Details |
|---|---|
| Sync | This will sync your configured investigation with your notepad. Anything in the notepad and not in the investigation will get added to the investigation. Anything in the investigation and not in your notepad will get added to your notepad. |
| Reset | This action will reset your investigation by removing all nodes, and then adding only the nodes from your notepad. |
| Open | This action will open your investigation's workbench in a new tab. |
| Add Selected | This action will add the selected objects to your configured investigation. |
Table Actions
| Action | Details |
|---|---|
| Clear All / Selected | This will clear the selected (or all) objects in your notepad table. |
Filtering
After intelligence is added to either your Analyze tab or Notepad tab, you will be able to filter the data down using the search box above the tables. Click on the search bar and type in a term to use to search your table.
This search field persists when you close the extension. If you notice object counts are off, it could be because you still have a search term entered.
Troubleshooting / FAQ
-
Save & Text Connection fails
If your connection fails when saving your ThreatQ connection configuration, it is most likely due to the host not being reachable. Confirm that your hostname is reachable from your local machine. To test this, you can open up terminal or command prompt and try to ping the hostname. If it fails, that is why the extension cannot connect. If it succeeds, the issue may lie elsewhere. If that is the case, try to configure theThreatQ Hostwith the IP for your ThreatQ instance instead of the hostname. Sometimes that may solve the connection issues. -
The extension is not parsing indicators
If indicators are not being parsed, it might be because theBackground Scanningoption in the extension'sConfig -> Generaltab is turned off. For indicators to be parsed, that option must be turned on. If indicators are still not being parsed, it could be an unsupported indicator type. If that is the case, please contact our support team so we can add the new type to be parsed. -
The Highlight Indicators button doesn't work
In order for this to work,Background Scanningneeds to be turned on as well. If it is not, nothing will be highlighted. It is also worth noting that the size of the page you are looking at does effect how long it takes to scan and highlight the indicators. If the page is exceptionally long (i.e. a Cisco Talos Threat Roundup blog), this can take a long time. On the contrary, a smaller blog or website may only take a second to parse and highlight the indicators. -
How do I import a large block of text?
To import indicators in bulk into ThreatQ, you can use the right-click actions from the extension. Simply select the text you want to import/parse. Then right click the selection and clickThreatQ -> Import Indicator(s). Doing so should redirect you to ThreatQ, where you can use the Indicator Import workflow to parse and import the indicators. This is done in order to leverage the existing workflow and features of the indicator import, so you can do things such as add related context, tags, and relationships.
Uninstalling the Extension
To uninstall the extension, follow these steps:
- Open your Chrome Browser
- Click on the
puzzle pieceicon to the right of your browser's URL bar - Select the button at the bottom labelled,
Manage Extensions - When on the extensions page, you can uninstall the extension by clicking the
Removebutton within the extension's card entry.
An alternative to would be to right click the ThreatQ rhino icon and selecting the Remove from Chrome... option.
Change Log
- Version 1.1.0
- Updated the extension to Chrome’s Manifest v3 Standards.
- Switched from localStorage to an IndexedDB to allow you to store more information in the extension.
- Added tooltips to highlighted items.
- Added an Object Details popup to Analyze/Notepad objects.
- You can now view tags, sources, attributes, and descriptions.
- Added additional tags, sources, and attributes.
- Added improved efficiency of Indicator Highlighting (via right-click).
- Added MITRE Technique Highlighting (via right-click).
- Added MITRE Tactic Highlighting (via right-click).
- Added Threat Actor Highlighting (via right-click).
- The extension now allows users to re-upload objects if new context has been added to it.
- Added improved stability of bulk-actions and connection to ThreatQ.
- Added the ability to inter-relate selected objects.
- Added the ability to create an event from selected objects.
- Added the ability to create a report from selected text (via right-click).
- Added the ability to parse PDFs for Indicators.
- Added the ability to manually create objects for the Notepad.
- Added the ability to set a default source name for objects loaded into the extension.
- Performed various package and dependency upgrades.
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| ThreatQ Google Chrome Extension Guide v1.1.0 | 5.6.0 or Greater |
| ThreatQ Google Chrome Extension Guide v1.0.0 | 4.25.0 or Greater |