FireEye HX Alerts Connector
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.1 |
| Compatible with ThreatQ Versions | >= 4.35.0 |
| Python Version | 3.6 |
| Support Tier | ThreatQ Supported |
Introduction
The FireEye HX Alerts Connector for ThreatQ enables the automatic ingestion of alerts and relevant indicators/context from FireEye, into ThreatQ.
The integration ingests the following system objects:
- Events
- Indicators
Prerequisites
Review the following requirements before attempting to install the connector.
FireEye HX and API
The FireEye HX Alerts connector requires a deployed instance of FireEye HX and that the API is network accessible by ThreatQ.
Time Zone
The time zone steps are for ThreatQ v5 only. ThreatQ v6 users should skip these steps.
You should ensure all ThreatQ devices are set to the correct time, time zone, and date (UTC is recommended), and using a clock source available to all.
To identify which time zone is closest to your present location, use the timedatectl command with the list-timezones command line option.
For example, enter the following command to list all available time zones in Europe:
Europe/Amsterdam
Europe/Athens
Europe/Belgrade
Europe/Berlin
Enter the following command, as root, to change the time zone to UTC:
Integration Dependencies
The integration must be installed in a python 3.6 environment.
The following is a list of required dependencies for the integration. These dependencies are downloaded and installed during the installation process. If you are an Air Gapped Data Sync (AGDS) user, or run an instance that cannot connect to network services outside of your infrastructure, you will need to download and install these dependencies separately as the integration will not be able to download them during the install process.
Items listed in bold are pinned to a specific version. In these cases, you should download the version specified to ensure proper function of the integration.
| Dependency | Version | Notes |
|---|---|---|
| threatqsdk | >=1.8.2 | N/A |
| threatqcc | >=1.4.1 | N/A |
| python-dateutil | N/A | N/A |
Installation
Upgrading Users - Review the Change Log for updates to configuration parameters before updating. If there are changes to the configuration file (new/removed parameters), you must first delete the previous version's configuration file before proceeding with the install steps listed below. Failure to delete the previous configuration file will result in the connector failing.
- Download the connector integration file from the ThreatQ Marketplace.
- Transfer the connector whl file to the
/tmp/directory on your instance. - SSH into your instance.
- Move the connector whl file from its
/tmp/location to the following directory:/opt/tqvenv - Navigate to the custom connector container:
kubectl exec -n threatq -it deployments/custom-connectors -- /bin/bash
- Create your python 3 virtual environment:
python3.6 -m venv /opt/tqvenv/<environment_name>
- Active the new environment:
source /opt/tqvenv/<environment_name>/bin/activate
- Run the pip upgrade command:
pip install --upgrade pip
- Install the required dependencies:
pip install setuptools==59.6.0 threatqsdk threatqcc
- Install the connector:
pip install /opt/tqvenv/tq_conn_fireeye_hx_alerts-<version>-py3-none-any.whl
- Perform an initial run of the connector:
/opt/tqvenv/<environment_name>/bin/tq-conn-fireeye-hx-alerts --cron="0 */2 * * *"
The
--cronargument above is used to generate a cron job for the connector. After running the command above, the cronjob will be created under the /etc/cron.d/ directory. This entry will initially be commented out upon creation - see the CRON chapter for more details. - Enter the following parameters when prompted:
Parameter Description ThreatQ Host Leave this field blank as it will be set dynamically. ThreatQ Client ID This is the OAuth id that can be found at Settings Gear → User Management → API details within the user’s details. ThreatQ Username This is the Email Address of the user in the ThreatQ System for integrations. ThreatQ Password The password for the above ThreatQ account. Status This is the default status for objects that are created by this Integration. Example Output
/opt/tqvenv/<environment_name>/bin/tq-conn-fireeye-hx-alerts --cron="0 */2 * * *" ThreatQ Host: ThreatQ Client ID: <ClientID> ThreatQ Username: <EMAIL ADDRESS> ThreatQ Password: <PASSWORD> Status: Review Connector configured. Set information in UI
You will still need to configure and then enable the connector.
- Navigate to the ThreatQ Marketplace and download the .whl file for the integration.
- Create the following directory:
mkdir /opt/tqvenv/
- Install python 3.6:
sudo yum install -y python36 python36-libs python36-devel python36-pip
- Create a virtual environment:
python3.6 -m venv /opt/tqvenv/<environment_name>
- Activate the virtual environment:
source /opt/tqvenv/<environment_name>/bin/activate
- Run the pip upgrade command:
pip install --upgrade pip
- Install the required dependencies:
pip install threatqsdk threatqcc setuptools==59.6.0
- Transfer the whl file to the
/tmpdirectory on your ThreatQ instance. - Install the connector on your ThreatQ instance:
pip install /tmp/tq_conn_fireeye_hx_alerts-<version>-py3-none-any.whl
A driver called
tq-conn-fireeye-hx-alertswill be installed. After installing, a script stub will appear in/opt/tqvenv/<environment_name>/bin/tq-conn-fireeye-hx-alerts. - Once the application has been installed, a directory structure must be created for all configuration, logs and files, using the
mkdir -pcommand. Use the commands below to create the required directories:mkdir -p /etc/tq_labs/ mkdir -p /var/log/tq_labs/ - Perform an initial run using the following command:
/opt/tqvenv/<environment_name>/bin/tq-conn-fireeye-hx-alerts -ll /var/log/tq_labs/ -c /etc/tq_labs/ -v3
- Enter the following parameters when prompted:
Parameter Description ThreatQ Host This is the host of the ThreatQ instance, either the IP Address or Hostname as resolvable by ThreatQ. ThreatQ Client ID This is the OAuth id that can be found at Settings Gear → User Management → API details within the user’s details. ThreatQ Username This is the Email Address of the user in the ThreatQ System for integrations. ThreatQ Password The password for the above ThreatQ account. Status This is the default status for objects that are created by this Integration. Example Output
/opt/tqvenv/<environment_name>/bin/tq-conn-fireeye-hx-alerts -ll /var/log/tq_labs/ -c /etc/tq_labs/ -v3 ThreatQ Host: <ThreatQ Host IP or Hostname> ThreatQ Client ID: <ClientID> ThreatQ Username: <EMAIL ADDRESS> ThreatQ Password: <PASSWORD> Status: Review Connector configured. Set information in UI
You will still need to configure and then enable the connector.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Labs option from the Category dropdown (optional).
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description FireEye HX Host/IP Enter the hostname or IP address, including port (if required), for your FireEye HX instance. FireEye HX API Username Enter your FireEye HX login username. Confirm that the user account is an API user, and not a regular user account, when configuring a username/password. To create/view user accounts, log into FireEye HX, and navigate to Admin -> Appliance Settings -> User Accounts.
FireEye HX API Password Enter your FireEye HX login password. Verify SSL Enable or disable SSL verification for your FireEye HX host.
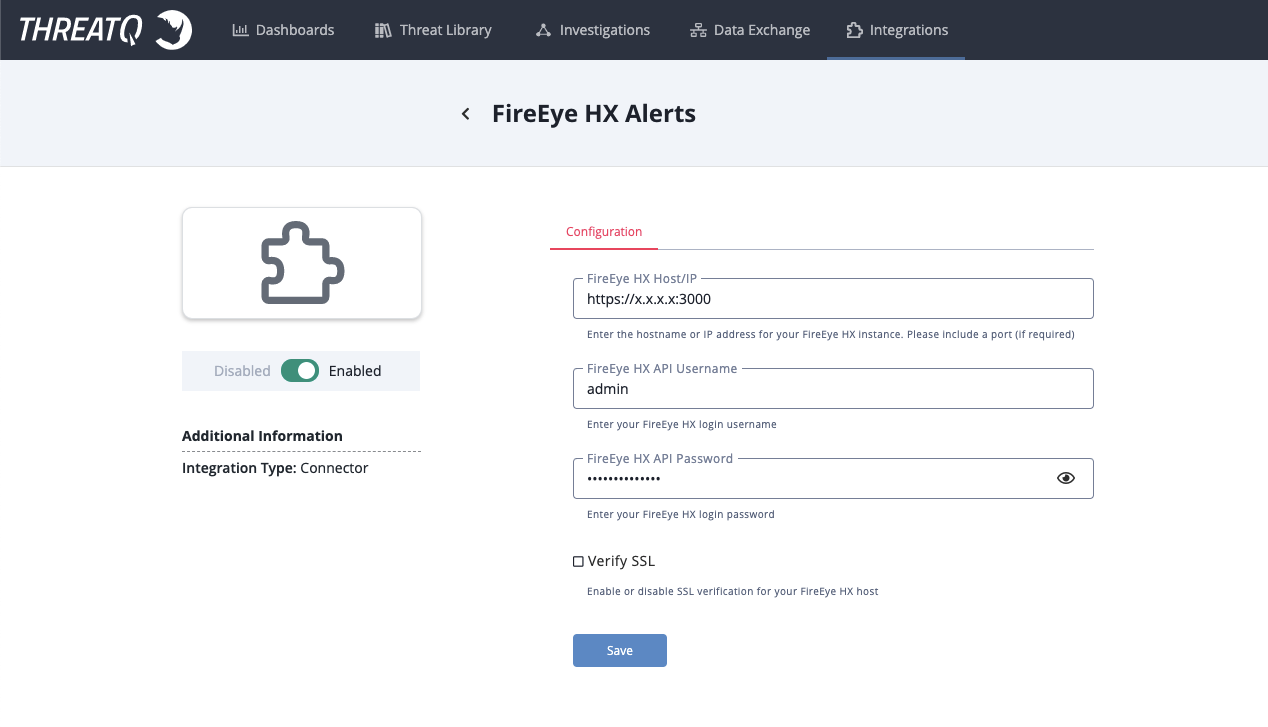
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
Usage
Use the following command to execute the driver:
Command Line Arguments
This connector supports the following custom command line arguments:
| Argument | Description |
|---|---|
h --help |
Shows the help message and exits. |
-v |
Sets the log verbosity (3 means everything). |
-c |
The path to the directory where you want to store your config file. |
-ll |
The path to the directory where you want to store your logs. |
-ep --external-proxy |
A flag to enable the use of the system proxy, configured in ThreatQ |
| --cron | ThreatQ v6 Only - creates a CRON entry for the connector based on a pre-loaded ThreatQ template. See the CRON section for more details. |
Accessing Connector Logs
ThreatQ version 6 aggregates the logs for all custom connectors to its output container. You can access the container's log using the following command:
The connector log directory was created in 10 of the installation process and is identified using the -ll argument flag when executing the driver.
Accessing Connector Configuration
The custom connector configuration file can be found in the following directory: /etc/tq_labs/.
The custom connector configuration file was created in step 10 of the install process and identified using the -c argument flag when executing the driver.
CRON
The addition of the --cron argument in the initial run of connector, performed during the install process, resulted in the creation of a cron job file for the connector in the following directory: /etc/cron.d/. The contents of the file will resemble the following structure:
The {schedule} will be replaced with the cron settings you entered with the --cron flag and the {executable} will be replaced for with the connector's driver command.
You will also see a # at the beginning of the file. This comments out the job. This allows you to configure the custom connector in the ThreatQ UI first. After you have configured the connector in ThreatQ, you can remove the # from the file content's in order to activate the cron job.
To summarize this process:
- Install the connector and perform an initial run using the
--cronargument to create the cron job. - Complete the connector's configuration settings in the ThreatQ UI.
- Access the connector's cron file in the
/etc/cron.d/directory and remove the # from the beginning of the file.
Automatic CRON configuration has been removed from this script. To run this script on a recurring basis, use CRON or some other jobs scheduler. The argument in the CRON script must specify the config and log locations.
Add an entry to your Linux crontab to execute the connector at a recurring interval. Depending on how quickly you need updates, this can be run multiple times a day (no more than once an hour) or a few times a week.
In the example below, the command will execute the connector every two hours.
- Log into your ThreatQ host via a CLI terminal session.
- Enter the following command:
crontab -e
This will enable the editing of the crontab, using vi. Depending on how often you wish the cronjob to run, you will need to adjust the time to suit the environment.
- Enter the commands below:
Every 2 Hours Example
0 */2 * * * /opt/tqvenv/<environment_name>/bin/tq-conn-fireeye-hx-alerts -c /etc/tq_labs/ -ll /var/log/tq_labs/ -v3 - Save and exit CRON.
FireEye HX Alert Example
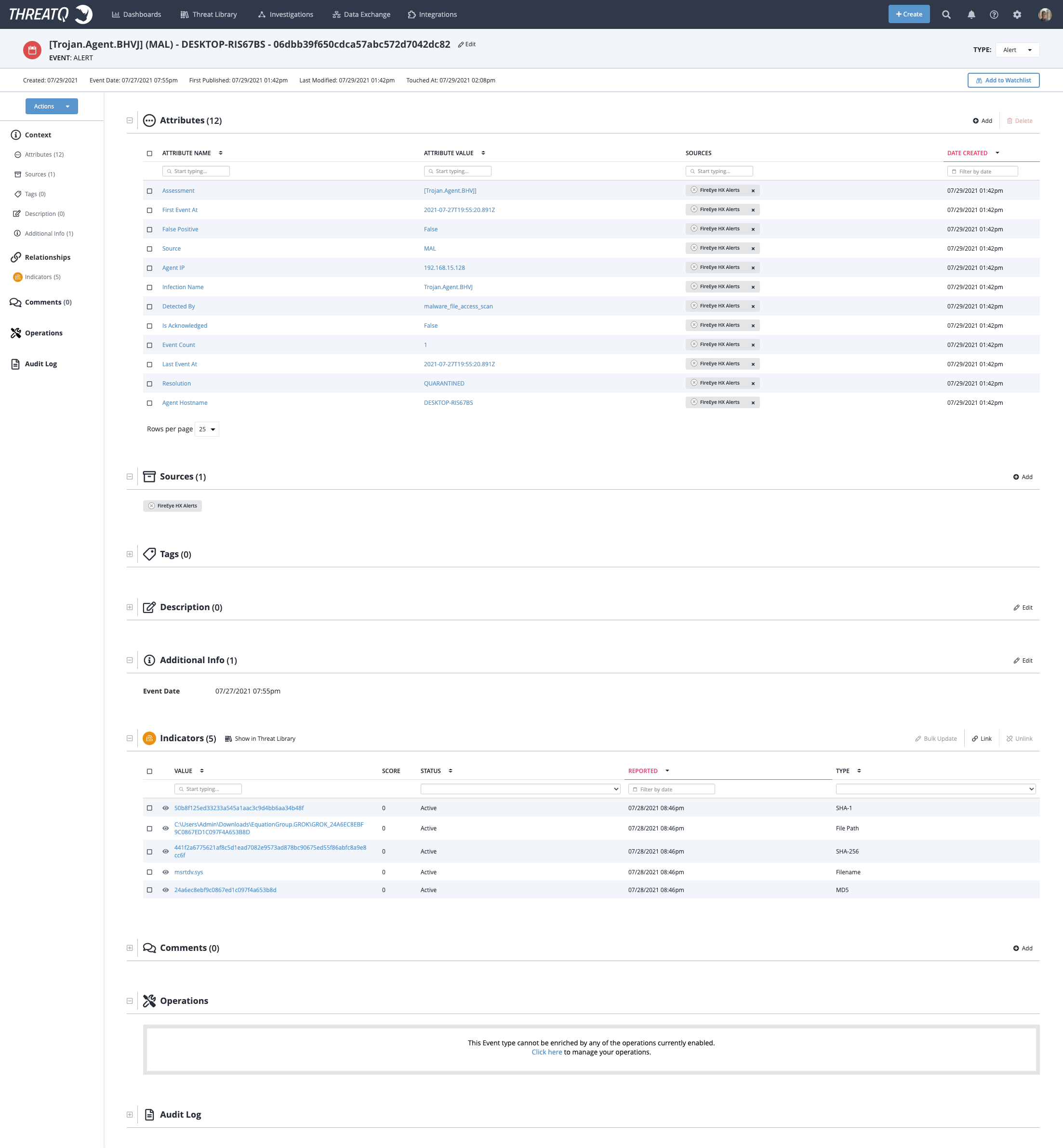
FireEye HX Indicator Example
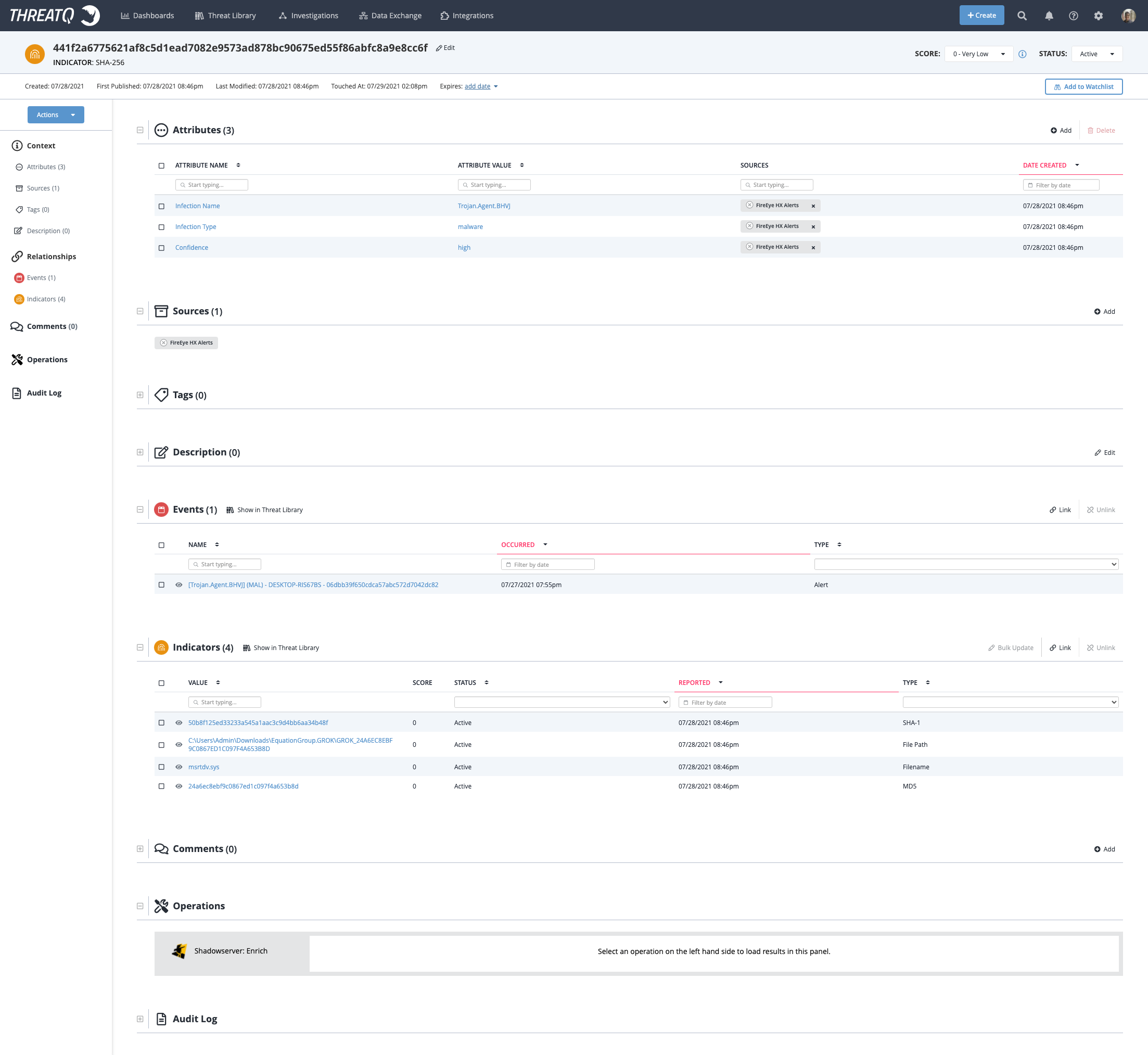
ThreatQ Mapping
Sample Response:
2021-07-29 14:02:50 - threatqcc.custom_connector DEBUG: Using Current working directory for config path
2021-07-29 14:02:50 - tq_conn_fireeye_hx_alerts DEBUG: Private Connection Established
2021-07-29 14:02:50 - fireeye_hx_alerts INFO: Fetching alerts from FireEye HX (2021-06-25T00:00:00.000Z - 2021-07-29T14:02:50.000Z)
2021-07-29 14:02:54 - fireeye_hx_alerts INFO: Parsing 6 alerts from FireEye HX
2021-07-29 14:02:54 - fireeye_hx_alerts INFO: Uploading alert, [[Trojan.Agent.BHVJ] (MAL) - DESKTOP-RIS67BS - 06dbb39f650cdca57abc572d7042dc82] with [5] indicator(s) to ThreatQ...
2021-07-29 14:03:01 - fireeye_hx_alerts INFO: Uploading alert, [[EICAR-Test-File (not a virus)] (MAL) - DESKTOP-RIS67BS - 44501e068f39b6d7749e8ff5447e08bf] with [4] indicator(s) to ThreatQ...
2021-07-29 14:03:08 - fireeye_hx_alerts INFO: Uploading alert, [[EICAR-Test-File (not a virus)] (MAL) - DESKTOP-RIS67BS - f62d937e9b168f88be7fd41d8a3320a7] with [4] indicator(s) to ThreatQ...
2021-07-29 14:03:14 - fireeye_hx_alerts INFO: Uploading alert, [[EICAR-Test-File (not a virus)] (MAL) - DESKTOP-RIS67BS - 89931c062f6be0f969b5ab1e8efab490] with [4] indicator(s) to ThreatQ...
2021-07-29 14:03:20 - fireeye_hx_alerts INFO: Uploading alert, [[Address 140.82.113.4 connected] No Github (IOC) - DESKTOP-RIS67BS - db092a2c710aed74ed31ff568e4d5d0b] with [1] indicator(s) to ThreatQ...
2021-07-29 14:03:28 - fireeye_hx_alerts INFO: Uploading alert, [[Address 140.82.113.4 connected] No Github (IOC) - DESKTOP-RIS67BS - 584c59c2febc3c47ec494558bfc8fa8f] with [1] indicator(s) to ThreatQ...
2021-07-29 14:03:37 - tq_conn_fireeye_hx_alerts INFO: [::] Completed execution of the FireEye HX Alerts Connector in 46 seconds.ThreatQuotient provides the following default mapping for this endpoint:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
.assessment, .source, ._id |
Event Title | Alert | .first_event_at |
[Trojan.Agent.BHVJ] (MAL) - DESKTOP-RIS67BS - 06dbb39f650cdca57a |
Key value's are formatted together to form a title |
.last_alert.event_values. |
Indicator Value | MD5 | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | SHA-256 | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | SHA-1 | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | File Path | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | File Size | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | Filename | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Hidden | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Temporary | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Read-only | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Packed | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is System File | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | MD5 | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | SHA-256 | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | SHA-1 | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | File Path | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | File Size | .created_at |
N/A | N/A |
.last_alert.event_values. |
Indicator Value | Filename | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Hidden | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Temporary | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Read-only | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is Packed | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Is System File | .created_at |
N/A | N/A |
.last_alert.event_values. |
Attribute | Confidence | .created_at |
high | N/A |
.last_alert.event_values. |
Attribute | Infection Type | .created_at |
malware | N/A |
.last_alert.event_values. |
Attribute | Infection Name | .created_at |
Trojan.Agent.BHVJ | N/A |
.last_alert.event_type |
Attribute | Event Type | .created_at |
N/A | N/A |
.last_alert.resolution |
Attribute | Resolution | .created_at |
QUARANTINE | N/A |
.last_alert.md5values[] |
Indicator Value | MD5 | .created_at |
N/A | N/A |
.last_alert.agent.hostname |
Attribute | Agent Hostname | .created_at |
DESKTOP-RIS67BS | N/A |
.last_alert.event_values. |
Indicator Value | IP Address | .created_at |
N/A | N/A |
.acknowledgement.acknowledged |
Attribute | Is Acknowledged | .created_at |
false | N/A |
.acknowledgement.acknowledged_by |
Attribute | Acknowledged By | .created_at |
false | N/A |
.grouped_by.detected_by |
Attribute | Detected By | .created_at |
malware_file_access_scan | N/A |
.grouped_by.infection-name |
Attribute | Infection Name | .created_at |
Trojan.Agent.BHVJ | N/A |
.grouped_by.host.hostname |
Attribute | Agent Hostname | .created_at |
DESKTOP-RIS67BS | N/A |
.grouped_by.host.primary |
Attribute | Agent IP | .created_at |
N/A | N/A |
.grouped_by.md5sum |
Indicator Value | MD5 | .created_at |
N/A | N/A |
.grouped_by.file-path |
Indicator Value | File Path | .created_at |
N/A | N/A |
.dispositions[].disposition |
Attribute | Disposition | .created_at |
N/A | N/A |
.source |
Attribute | Source | .created_at |
IOC | N/A |
.has_fp_disposition |
Attribute | False Positive | .created_at |
false | N/A |
.assessment |
Attribute | Assessment | .created_at |
[Trojan.Agent.BHVJ] |
N/A |
.file_full_path |
Indicator Value | File Path | .created_at |
N/A | N/A |
.first_event_at |
Attribute | First Event At | .created_at |
2021-07-24T19:54:24.000Z | N/A |
.last_event_at |
Attribute | Last Event At | .created_at |
2021-07-24T19:54:24.000Z | N/A |
.stats.events |
Attribute | Event Count | .created_at |
6 | N/A |
Average Connector Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
| Metric | Result |
|---|---|
| Run Time | 46 seconds |
| Events | 6 |
| Event Attributes | 70 |
| Indicators | 19 |
| Indicator Attributes | 53 |
Change Log
- Version 1.0.1 rev-a
- Guide Update - Added ThreatQ 6x documentation.
- Version 1.0.1
- The connector will now disable the proxy if one is not provided.
- Version 1.0.0
- Initial Release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| FireEye HX Alerts Connector Guide v1.0.1 | 4.35.0 or Greater |