Kaspersky APT DEMO CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 4.37.0 |
| Support Tier | ThreatQ Supported |
Introduction
The Kaspersky APT DEMO CDF ingest threat intelligence data used in malicious APT campaigns from Kaspersky Threat Intelligence.
The CDF includes the following feeds:
- Kaspersky APT IPs DEMO - ingests
IP Addressindicators and attributes. - Kaspersky APT URLs DEMO - ingests indicators and attributes.
- Kaspersky APT Hashes DEMO - ingests hash indicators and attributes.
The integration ingests the following system object types:
- Indicators
- Indicator Attributes
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description Kaspersky PEM You Kaspersky Client Certificate for authentication. Entries The number of entries to be retrieved. The default setting is 10,000.
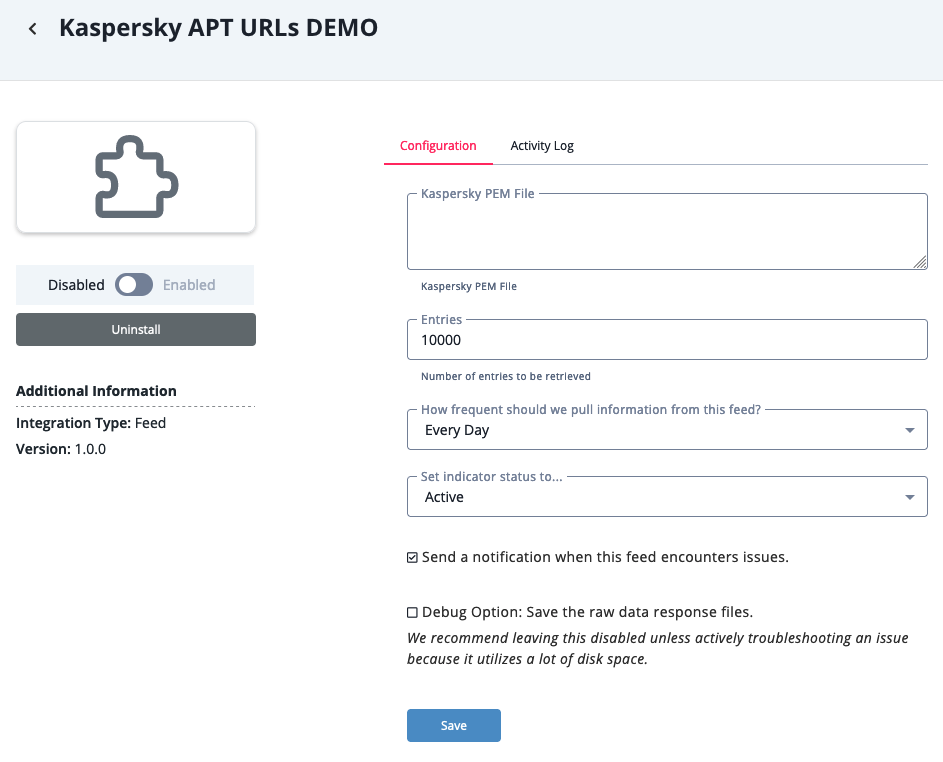
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
Kaspersky APT IPs DEMO
The Kaspersky APT IPs DEMO feed ingests IP Address indicators and attributes.
GET https://wlinfo.kaspersky.com/api/v1.0/feeds/142/updates
Sample Response:
[
{
"detection_date": "20.04.2017 00:00",
"id": 16453205,
"ip": "69.64.59.133",
"publication_name": "ShadowBrokers Lost in translation leak - SWIFT attacks analysis"
},
...
]ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| [].ip | Indicator.Value | IP Address | [].detection_date | 69.64.59.133 | N/A |
| [].publication_name | Indicator.Attribute | Publication | [].detection_date | ShadowBrokers Lost in translation leak - SWIFT attacks analysis | N/A |
Kaspersky APT URLs DEMO
The Kaspersky APT URLs DEMO feed ingests indicators and attributes.
GET https://wlinfo.kaspersky.com/api/v1.0/feeds/143/updates
Sample Response:
[
{
"detection_date": "09.03.2017 00:00",
"id": 16451625,
"mask": "ec2-52-74-203-151.ap-southeast-1.compute.amazonaws.com",
"publication_name": "APT10 Spearphishes Japanese Policy Experts late 2016 to early 2017",
"type": 2
},
...
]ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| [].mask | Indicator.Value | See Kaspersky Type Mapping table | [].detection_date | ec2-52-74-203-151.ap-southeast-1.compute.amazonaws.com | N/A |
| [].publication_name | Indicator.Attribute | Publication | [].detection_date | ShadowBrokers Lost in translation leak - SWIFT attacks analysis | N/A |
Kaspersky APT Hashes DEMO
The Kasperky APT Hashes DEMO feed ingests hash indicators and attributes.
GET https://wlinfo.kaspersky.com/api/v1.0/feeds/144/updates
Sample Response:
[
{
"detection_date": "23.06.2017 00:00",
"id": 16456071,
"MD5": "F805882CC276B583D9CA7E16AD957E7B",
"publication_name": "Ismdoor - possible Shamoon attack vector found in Saudi Arabia",
"SHA1": "2E4DB721DBD2ACEFD851BEDF95492BF789F588FD",
"SHA256": "D76024256AC35424EB02B6A47565F8859B12050F5DE49EF16DEC449A61DA1EFC"
},
...
]ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| ].MD5 | Indicator.Value | MD5 | [].detection_date | F805882CC276B58 3D9CA7E16AD957E 7B |
Inter-related with other hash Indicators |
| [].SHA1 | Indicator.Value | SHA-1 | [].detection_date | 2E4DB721DBD2ACEF D851BEDF95492BF78 9F588FD |
Inter-related with other hash Indicators |
| [].SHA256 | Indicator.Value | SHA256 | [].detection_date | D76024256AC35424EB0 2B6A47565F8859B12050 F5DE49EF16DEC449A61D A1EFC |
Inter-related with other hash Indicators |
| [].publication_name | Indicator.Attribute | Publication | [].detection_date | ShadowBrokers Lost in translation leak - SWIFT attacks analysis | N/A |
Kaspersky Type Mapping
| [].Type Value | Indicator Type Value | Notes |
|---|---|---|
| 1, 2 | FQDN | N/A |
| 3, 4 | URL | N/A |
| 19 | FQDN | Value is formatted with lstrip('*.') |
| 20 | URL | Value is formatted with rstrip('/*') |
| 21 | URL | Value is formatted with rstrip('*') |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
Kaspersky APT URLs
| Metric | Result |
|---|---|
| Run Time | < 1 minute |
| Indicators | 42 |
| Indicator Attributes | 42 |
Kaspersky APT IPs
| Metric | Result |
|---|---|
| Run Time | < 1 minute |
| Indicators | 35 |
| Indicator Attributes | 35 |
Kaspersky APT Hashes
| Metric | Result |
|---|---|
| Run Time | < 1 minute |
| Indicators | 431 |
| Indicator Attributes | 431 |
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Kaspersky APT DEMO CDF Guide v1.0.0 | 4.37.0 or Greater |