KELA Monitor CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 4.28.0 |
| Support Tier | Developer Supported |
| Support Email | support@ke-la.com |
| Support Web | https://ke-la.com/contact-us/ |
Introduction
The KELA Monitor integrations allows a user to automatically load new incidents from the KELA monitoring platform directly to the ThreatQ platform.
The monitor integrations are according to their matched KELA modules:
- KELA Monitor Leaked Credentials
- KELA Monitor Compromised Accounts
- KELA Monitor Instant Messaging
- KELA Monitor Hacking Discussions
- KELA Monitor Network Vulnerabilities
Each integration creates its own threat objects of type Incidents, together with other objects depending on the integration.
Prerequisites
Review the following requirements before attempting to install the integration.
KELA API Key
All integrations require the use of an API Key that can be obtained from within the KELA platform, by clicking on the gear icon on the left side bar, and then choosing the Generate API key option.
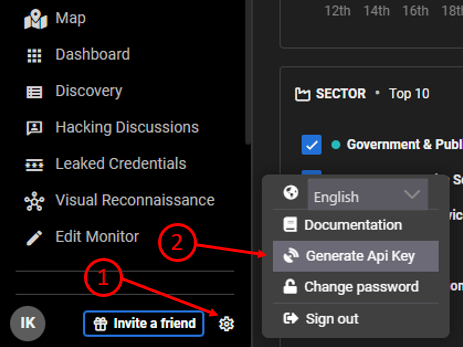
Key will be presented on the opened window.
KELA Monitor ID
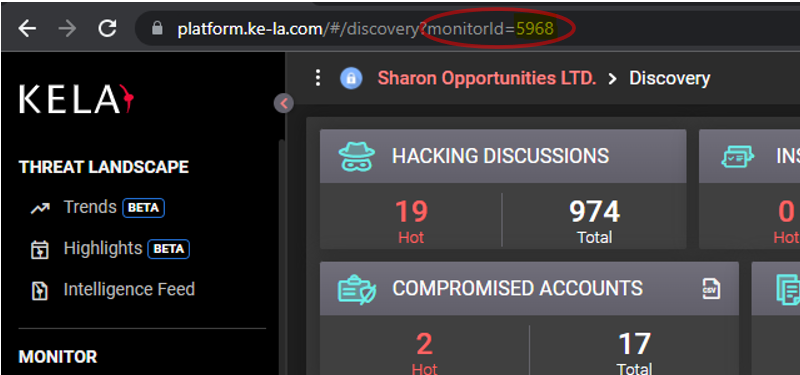
For monitoring integrations, there is also a need for the getting the monitor ID from the KELA platform. This ID can be obtained from the URL when going into the monitor in the platform.
Example: The URL for monitor ID 5968 will look as follows:
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description API Key
(All feeds)Your KELA API Key. See the KELA API Key section for more information. Workspace ID
(All feeds)Your Monitor ID. See the KELA Monitor ID section for more information. Company/Organization Name
(All feeds)The company or organization name that the monitor is associated with. This field is not required but may be useful in multi-tenant implementations for separation of alerts.
Captured Passwords
(KELA Monitor Leaked Credentials, KELA Monitor Compromised Accounts, KELA Monitor Instant Messaging feeds only)When enabled, passwords will be captured from KELA if they are available. Capture Dump Descriptions
(KELA Monitor Leaked Credentials feed only)Retrieved the detail description for leaked credentials coming from leaked dumps for each related dump. Enabling this feature will slow down feed pull execution.
Capture Identified Hostnames as Indicators
(KELA Monitor Leaked Credentials and KELA Monitor Compromised Accounts feeds only)Enable/disable the option to capture Identified Hostnames as Indicators. Ingest CVEs as...
(KELA Monitor Network Vulnerabilities feed only)Configure how CVEs will be ingested. Options include: - Indicators (default)
- Vulnerability
Hostnames as Indicators
(KELA Monitor Network Vulnerabilities feed only)Enable/disable the ingestion of Hostnames as Indicators. IPs as Indicators
(KELA Monitor Network Vulnerabilities feed only)Enable/disable the ingestion of IPs as Indicators.
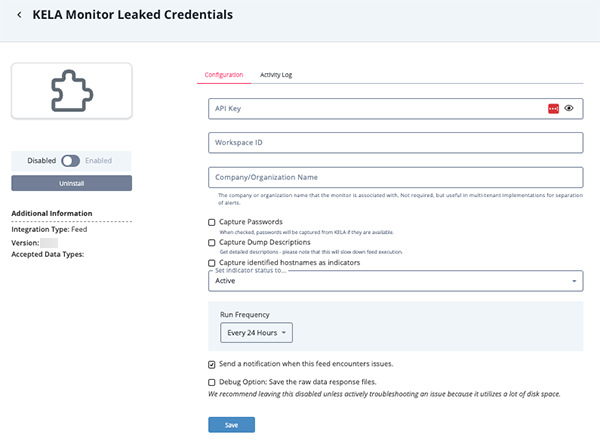
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
Known Issues / Limitations
- KELA Monitor Leaked Credentials feed - enabling the Capture Dump Descriptions configuration option will slow down feed pull execution.
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| KELA Monitor CDF Guide v1.0.0 | 4.28.0 or Greater |