Flashpoint Ignite Compromised Accounts CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.1.2 |
| Compatible with ThreatQ Versions | >= 5.10.0 |
| Support Tier | ThreatQ Supported |
Introduction
The Flashpoint Ignite Compromised Accounts CDF integration for ThreatQ enables the automatic ingestion of an organization's compromised credentials into ThreatQ. Ultimately, tracking the accounts to link them to internal incidents as well as mitigating potential future breaches.
The integration provides the following feed:
- Flashpoint Ignite Compromised Accounts - ingests Compromised Accounts as the main object and Events as related objects.
The integration ingests the following system objects:
- Compromised Account (custom object)
- Events
- Malware
Prerequisites
The following is required to install and run the integration:
- A Flashpoint API Key.
- The Compromised Account custom object installed on your ThreatQ instance.
Compromised Account Custom Object
The integration requires the Compromised Account custom object.
For export purposes, the system name for Compromised Account objects is account.
When installing the custom objects, be aware that any in-progress feed runs will be cancelled, and the API will be in maintenance mode.
- Download the integration bundle from the ThreatQ Marketplace.
- Unzip the bundle and locate the custom object files.
The custom object files will typically consist of a JSON definition file, install.sh script, and a images folder containing the svg icons.
- SSH into your ThreatQ instance.
- Set your install pathway environment variable. This command will retrieve the install pathway from your configuration file and set it as variable for use during this installation process.
INSTALL_CONF="/etc/threatq/platform/install.conf" if [ -f "$INSTALL_CONF" ]; then source "$INSTALL_CONF" fi MISC_DIR="${INSTALL_BASE_PATH:-/var/lib/threatq}/misc"
- Navigate to the tmp folder using the environment variable:
cd $MISC_DIR
- Upload the custom object files, including the images folder.
The directory structure should resemble the following:
- install.sh
- <custom_object_name>.json
- images (directory)
- <custom_object_name>.svg
- Run the following command:
kubectl exec -it deployment/api-schedule-run -n threatq -- sh /var/lib/threatq/misc/install.sh /var/lib/threatq/misc
The installation script will automatically put the application into maintenance mode, move the files to their required directories, install the custom object, update permissions, bring the application out of maintenance mode, and restart dynamo.
- Delete the install.sh, definition json file, and images directory from step 6 after the object has been installed as these files are no longer needed.
Use the following steps to install the custom objects in ThreatQ v5:
- Download the integration zip file from the ThreatQ Marketplace and unzip its contents.
- SSH into your ThreatQ instance.
- Navigate to tmp directory:
cd /tmp/
- Create a new directory:
mkdir flashpoint_cdf
- Upload the account.json and install.sh script into this new directory.
- Create a new directory called images within the flashpoint_cdf directory.
mkdir images
- Upload the account.svg.
- Navigate to the /tmp/flashpoint_cdf.
The directory should resemble the following:
- tmp
- flashpoint_cdf
- account.json
- install.sh
- images
- account.svg
- flashpoint_cdf
- tmp
- Run the following command to ensure that you have the proper permissions to install the custom object:
chmod +x install.sh
- Run the following command:
sudo ./install.sh
You must be in the directory level that houses the install.sh and json files when running this command.
The installation script will automatically put the application into maintenance mode, move the files to their required directories, install the custom object, update permissions, bring the application out of maintenance mode, and restart dynamo.
- Remove the temporary directory, after the custom object has been installed, as the files are no longer needed:
rm -rf flashpoint_cdf
Installation
The CDF requires the installation of the Compromised Account custom object before installing the actual CDF. See the Prerequisites chapter for more details. The custom object must be installed prior to installing the CDF. Attempting to install the CDF without the custom object will cause the CDF install process to fail.
Perform the following steps to install the integration:
The same steps can be used to upgrade the integration to a new version.
- Log into https://marketplace.threatq.com/.
- Locate and download the integration zip file.
- Extract the files and install the Compromised Account custom object.
- Navigate to the integrations management page on your ThreatQ instance.
- Click on the Add New Integration button.
- Upload the yaml file using one of the following methods:
- Drag and drop the file into the dialog box
- Select Click to Browse to locate the file on your local machine
ThreatQ will inform you if the feed already exists on the platform and will require user confirmation before proceeding. ThreatQ will also inform you if the new version of the feed contains changes to the user configuration. The new user configurations will overwrite the existing ones for the feed and will require user confirmation before proceeding.
- The feed will be added to the integrations page. You will still need to configure and then enable the feed.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description API Key Your Flashpoint API Key Excluded Domains A comma-separated list of domains to exclude from search results. Hide Compromised Passwords Enable/disable the ingestion of the compromised account passwords. Ingested Context Select which pieces of context you want brought in with the alerts. Options include: - Breach Source
- Breach Source Type
- Breach Type
- Affected Domain
- Affected Email
- Is Fresh Flag
- Seen Count
- Raw Credentials
- Breached Password
- Matched Queries
- First Observed At
Ingest Account Objects Enable/disable the creation of Compromised Account objects for the affected accounts related to the breach. Account Context Select which pieces of context to ingest with the compromised account. Options include: - Breached Password (default)
- Affected Domain (default)
- First Observed At (default)
- Flashpoint URL (default)
- Installed Software (default)
- Additional Extracted Metadata (default)
- Infection Data (default)
- Machine Information (default)
- ISP (default)
Relate Malware to the Account Enable this parameter to relate Malware objects for the affected accounts. This parameter is enabled by default. Enable SSL Certificate Verification Enable this parameter for the feed to validate the host-provided SSL certificate. Disable Proxies Enable this option if the feed should not honor proxies set in the ThreatQ UI.
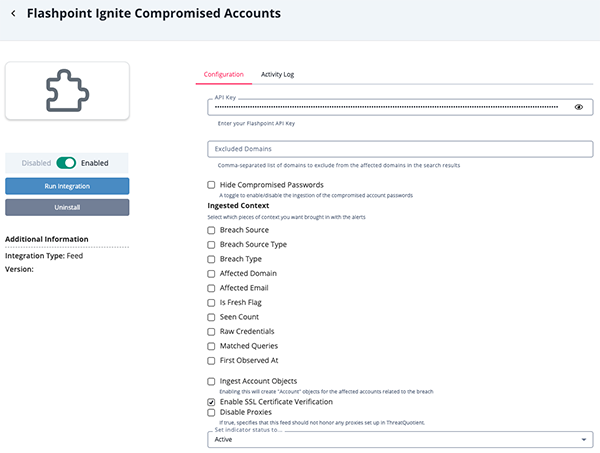
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
Flashpoint Ignite Compromised Accounts
The Flashpoint Ignite Compromised Accounts feed for ThreatQ enables the automatic ingestion of an organization's compromised credentials into ThreatQ.
GET https://api.flashpoint.io/sources/v1/noncommunities/search
Sample Response:
{
"hits": {
"hits": [
{
"_id": "EMX6QiiPW-ay8-5d732GqB",
"_source": {
"basetypes": [
"credential-sighting"
],
"body": {
"raw": "someone@threatq.com:<some password>"
},
"breach": {
"_header": {},
"basetypes": [
"breach"
],
"breach_type": "credential",
"created_at": {
"date-time": "2021-06-25T23:57:31Z",
"timestamp": 1624665451
},
"first_observed_at": {
"date-time": "2021-06-25T23:57:31Z",
"timestamp": 1624665451
},
"fpid": "ESiczBZVW0Kx3Fxpybfd4B",
"published_at_ts": "2021-06-25 23:57:31",
"source": "https://www.virustotal.com/gui/file/bd5e65fecff172bce63fb054c85953f93e63baf863456e571df4dfe52da85d3b/details",
"source_type": "VirusTotal",
"title": "Compromised Users from VirusTotal: Compressed File \"bd5e65fecff172bce63fb054c85953f93e63baf863456e571df4dfe52da85d3b\" Jun252021"
},
"credential_record_fpid": "iCb5b0mfXvqk0QVJnL6jTw",
"customer_id": "0013l00002MH03tAAD",
"domain": "threatq.com",
"email": "someone@threatq.com",
"extraction_id": "DxEdSTXwWR6ouuZc3e7veA",
"extraction_record_id": "zEv0ARXyVVuMUEUkDcLzTA",
"fpid": "EMX6QiiPW-ay8-5d732GqA",
"header_": {
"indexed_at": 1625842497,
"pipeline_duration": 63793061697
},
"is_fresh": false,
"last_observed_at": {
"date-time": "2021-06-25T23:57:31Z",
"timestamp": 1624665451
},
"last_observed_at_ts": "2021-06-25 23:57:31",
"password": "<some password>",
"password_complexity": {
"has_lowercase": true,
"has_number": true,
"has_symbol": false,
"has_uppercase": false,
"length": 6
},
"published_at_ts": "2021-06-25 23:57:31",
"times_seen": 1
},
"_type": "_doc",
"matched_queries": [
"dat.edm.org.r"
]
}
],
"max_score": null,
"total": 1
},
"timed_out": false,
"took": 18
}ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
._source.breach.title |
Related Event.Value | Alert | ._source.breach.created_at |
N/A | N/A |
._source.breach.victim |
Related Event.Attribute | Victim | ._source.breach.created_at |
someone@threatq.com | N/A |
._source.breach.source |
Related Event.Attribute | Source | ._source.breach.created_at |
https://www.virustotal. com/gui/file/xxxx |
User-configurable |
._source.breach.source_type |
Related Event.Attribute | Source Type | ._source.breach.created_at |
VirusTotal | User-configurable |
._source.breach.breach_type |
Related Event.Attribute | Breach Type | ._source.breach.created_at |
credential | User-configurable |
._source.affected_domain |
Related Event.Attribute | Affected Domain | ._source.breach.created_at |
auction.rihago.auction | User-configurable |
._source.email |
Related Event.Attribute | Affected Email | ._source.breach.created_at |
someone@threatq.com | User-configurable |
._source.is_fresh |
Related Event.Attribute | Is Fresh | ._source.breach.created_at |
false | User-configurable; Updatable |
._source.times_seen |
Related Event.Attribute | Seen Count | ._source.breach.created_at |
1 | User-configurable; Updatable |
._source.body.raw |
Related Event.Attribute | Raw Credentials | ._source.breach.created_at |
someone@threatq.com: <some password> |
User-configurable |
.matched_queries |
Related Event.Attribute | Matched Query | ._source.breach.created_at |
dat.edm.org.r | User-configurable |
._source.breach.first_observed_at.date-time |
Related Event.Attribute | First Observed At | ._source.breach.created_at |
2021-06-25T23:57:31Z | User-configurable |
._source.email |
Account.Value | Account | ._source.last_observed_at |
someone@threatq.com | The custom object must be installed |
._source.password |
Account.Attribute | Password | ._source.last_observed_at |
Hunter2 | N/A |
._source.affected_domain |
Account.Attribute | Affected Domain | ._source.last_observed_at |
auction.rihago.auction | N/A |
._source.credential_record_fpid + _source.fpid |
Account.Attribute | Flashpoint URL | ._source.last_observed_at |
https://app.flashpoint. io/cti/ato/credential/iC b5b0mfXvqk0QVJnL6jT w::EMX6QiiPW-ay8-5d7 32GqA |
Constructed as https://app.flashpoint.io/ cti/ato/credential/{{_source.credential_ record_fpid}}::{{_source.fpid}} |
._source.infected_host_attributes.installed_software.name |
Account.Attribute | Installed Software | ._source.last_observed_at |
Windows Defender | User-Configurable. |
._source.infected_host_attributes.host_id |
Account.Attribute | Host ID | ._source.last_observed_at |
D7E97AF1168849AEC 589C51AF308360B |
User-Configurable. If Additional Extracted Metadata is checked in Account Context |
._source.infected_host_attributes.ip |
Account.Attribute | IP | ._source.last_observed_at |
102.88.33.186 | User-Configurable. If Additional Extracted Metadata is checked in Account Context |
._source.infected_host_attributes.ipv4 |
Account.Attribute | IPV4 | ._source.last_observed_at |
102.88.33.186 | User-Configurable. If Additional Extracted Metadata is checked in Account Context |
._source.infected_host_attributes.location.continent_name |
Account.Attribute | Continent | ._source.last_observed_at |
Africa | User-Configurable. If Infection Data is checked in Account Context |
._source.infected_host_attributes.location.country_name |
Account.Attribute | Country | ._source.last_observed_at |
Nigeria | User-Configurable. If Infection Data is checked in Account Context |
._source.infected_host_attributes.location.city_name |
Account.Attribute | City | ._source.last_observed_at |
Lagos | User-Configurable. If Infection Data is checked in Account Context |
._source.infected_host_attributes.machine.os |
Account.Attribute | Operation System | ._source.last_observed_at |
Windows 10 Enterprise x64 | User-Configurable. If Machine Information is checked in Account Context |
._source.infected_host_attributes.machine.user |
Account.Attribute | Local Username | ._source.last_observed_at |
Tosin | User-Configurable. If Machine Information is checked in Account Context |
._source.infected_host_attributes.machine.extra[].value |
Account.Attribute | ._source.infected_host_attributes.machine.extra[].key |
._source.last_observed_at |
Filelocation: C:\\Users\\Tosin\\AppData\\Local\\Temp\\1000169001\\flesh.exe |
User-Configurable. If Machine Information is checked in Account Context |
._source.infected_host_attributes.isp.autonomous_system_number |
Account.Attribute | ASN Number | ._source.last_observed_at |
29465 | User-Configurable. If ISP is checked in Account Context |
._source.infected_host_attributes.isp.connection_type |
Account.Attribute | Connection Type | ._source.last_observed_at |
Cellular | User-Configurable. If ISP is checked in Account Context |
._source.infected_host_attributes.isp.autonomous_system_organization |
Account.Attribute | Organization Name | ._source.last_observed_at |
MTN NIGERIA Communication limited | User-Configurable. If ISP is checked in Account Context |
._source.infected_host_attributes.isp.organization |
Account.Attribute | AS Organization | ._source.last_observed_at |
MTN Nigeria | User-Configurable. If ISP is checked in Account Context |
._source.infected_host_attributes.malware.family |
Related Malware.Value | Malware | ._source.last_observed_at |
readline_stealer | User-Configurable. If Relate Malware to the account is checked |
._source.infected_host_attributes.malware.version |
Related Malware.Attribute | Malware Version | ._source.last_observed_at |
Premium logs https://t.me/ stealerforum |
User-Configurable. If Relate Malware to the account is checked |
._source.infected_host_attributes.malware.scanned_at.date-time |
Related Malware.Attribute | Scan Timestamp | ._source.last_observed_at |
2024-01-10T21:47:01 | User-Configurable. If Relate Malware to the account is checked |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
| Metric | Result |
|---|---|
| Run Time | 1 minute |
| Account Attributes | 209 |
| Compromised Accounts | 44 |
| Events | 6 |
| Event Attributes | 246 |
| Malware | 1 |
| Malware Attributes | 3 |
Known Issues / Limitations
- Due to "lag time" between when a breach is first observed and when the entry appears on the Flashpoint API, we now back-date the feed's last run time by 12 hours. This is to account for that "lag time". It may cause some alerts to be re-ingested, but they will be de-duplicated, so there shouldn't be any concerns.
- For consecutive runs at an interval of 1 minute, we can receive 429 and we recommend waiting 3 or 5 minutes and then repeating.
Change Log
- Version 1.1.2 rev-a
- Guide Update - updated custom object installation steps for ThreatQ v6 instances.
- Version 1.1.2
- Added the option to ingest
Host Data. - Added the following configuration parameters:
- Account Context - select which pieces of context to ingest with the compromised account.
- Relate Malware to the Account - relate Malware objects for the affected accounts.
- Added the option to ingest
- Version 1.1.1
- The feed now correctly ingests the
Affected Domainattribute from Flashpoint. - Added a rule to update
Is FreshandIs Freshattributes if it already exists in the ThreatQ platform. - Added new configuration parameters: Enable SSL Verification and Disable Proxies.
- Added two new known limitation entries regarding lag times and consecutive runs.
- Updated the text for the Exclude Domains configuration parameter field.
- The feed now correctly ingests the
- Version 1.1.0
- The integration now uses the Flashpoint Ignite Compromised Accounts endpoint.
- Updated the name of integration to Flashpoint Ignite Compromised Accounts.
- Updated the minimum ThreatQ version to 5.10.0
- Version 1.0.1
- Fixed an issue with lag time between when a breach was first observed and when the entry appeared in the Flashpoint API.
- Updated the support tier for the integration from Not Actively Supported to ThreatQ Supported.
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Flashpoint Ignite Compromised Account CDF v1.1.2 | 5.10 or Greater |
| Flashpoint Ignite Compromised Account CDF v1.1.1 | 5.10 or Greater |
| Flashpoint Ignite Compromised Account CDF v1.1.0 | 5.10 or Greater |
| Flashpoint Compromised Account CDF v1.0.1 | 4.35 or Greater |
| Flashpoint Compromised Account CDF v1.0.0 | 4.35 or Greater |