Flashpoint Ignite Alerts CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.2.7 |
| Compatible with ThreatQ Versions | >= 5.12.1 |
| Support Tier | ThreatQ Supported |
Introduction
The Flashpoint Ignite Alerts CDF for ThreatQ enables the automatic ingestion of an alert within Flashpoint.
The integration ingests threat intelligence data from the following endpoint:
- Flashpoint Ignite Alerts - ingests Ignite Alert data into the ThreatQ platform.
The integration ingests following object types:
- Adversaries
- Events
- Event Attributes
- Indicators
- Vulnerabilities
Installation
Perform the following steps to install the integration:
The same steps can be used to upgrade the integration to a new version.
- Log into https://marketplace.threatq.com/.
- Locate and download the integration yaml file.
- Navigate to the integrations management page on your ThreatQ instance.
- Click on the Add New Integration button.
- Upload the integration yaml file using one of the following methods:
- Drag and drop the file into the dialog box
- Select Click to Browse to locate the file on your local machine
ThreatQ will inform you if the feed already exists on the platform and will require user confirmation before proceeding. ThreatQ will also inform you if the new version of the feed contains changes to the user configuration. The new user configurations will overwrite the existing ones for the feed and will require user confirmation before proceeding.
- The feed will be added to the integrations page. You will still need to configure and then enable the feed.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameter under the Configuration tab:
Parameter Description API Key Your Flashpoint Ignite Alerts API Key. API Options Optional - Enter a line-separated list of query IDs to filter alerts. Ingest Highlights Enable this parameter to ingest highlights. Link Adversaries to Alerts Enable this parameter to link ingested adversaries to alerts. This parameter is disabled by default. Save CVE Data as Select how to ingest CVEs as into the ThreatQ platform. Options include: - Indicators
- Vulnerabilities
Enable SSL Verification Enable this parameter to validate the host-provided SSL certificate. This parameter is enabled by default. Disable Proxies Enable this option if the feed should not honor proxies set in the ThreatQ UI.
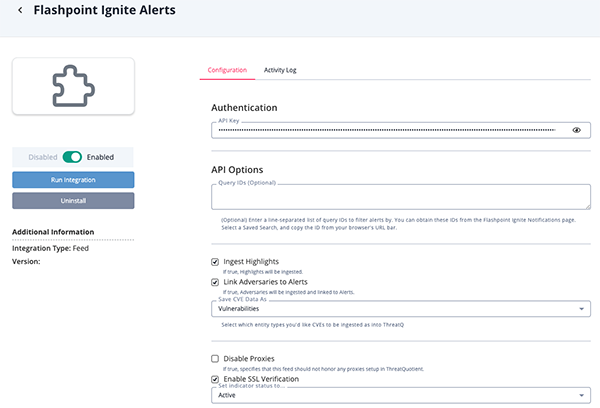
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
Flashpoint Ignite Alerts
The Flashpoint Ignite Alerts feed enables the automatic ingestion Ignite Alert data into the ThreatQ platform as Events, Indicators, and Vulnerabilities.
GET https://api.flashpoint.io/alert-management/v1/notifications
Sample Response:
{
"items": [
{
"id": "8a45bd35-1fac-4b35-aa27-630ab3821507",
"resource": {
"id": "LIjNc-xrVUynzUwsoqPfVw",
"basetypes": [
"chat",
"conversation",
"message",
"telegram"
],
"title": "𝗕𝗜𝗚𝗙𝗔𝗧𝗖𝗛𝗔𝗧™️💰",
"sort_date": "2024-06-03T20:15:07Z",
"site": {
"title": "Telegram"
},
"container": {
"name": "𝗕𝗜𝗚𝗙𝗔𝗧𝗖𝗛𝗔𝗧™️💰",
"native_id": "1213408970",
"title": "𝗕𝗜𝗚𝗙𝗔𝗧𝗖𝗛𝗔𝗧™️💰"
},
"site_actor": {
"names": {
"handle": "RISK"
},
"native_id": "5375938422"
},
"created_at": {
"date-time": "2024-06-03T20:15:07+00:00",
"raw": "1717445707",
"timestamp": 1717445707
}
},
"reason": {
"id": "218f7b12-8c85-474e-8013-98d014e99c8c",
"name": "Insider Threat Alerts",
"text": "(\"I am an employee\" OR \"i'm an employee\" OR \"i can get access\" OR \"i have access to\" OR \"i work at\" OR \"i work for\" OR inny OR \"i'm employed at\" OR \"my occupation is\") NOT arsenal",
"origin": "two-face",
"details": {
"sources": [
"communities"
],
"params": {
"sort": "relevancy",
"exclude": {},
"include": {
"date": {
"end": "now",
"label": "Last 7 Days",
"start": "now-7d"
}
}
}
},
"entity": {
"id": "001o000000igOLYAA2",
"name": "ThreatQ",
"type": "organization"
}
},
"status": null,
"generated_at": "2024-06-03T20:16:12.875144Z",
"created_at": "2024-06-03T20:16:14.716472Z",
"tags": {},
"highlights": {
"body.text/plain": [
"Nah I need 6 figs stims tho can fly you out where inny at"
]
},
"highlight_text": "Nah I need 6 figs stims tho can fly you out where inny at",
"data_type": "chat",
"parent_data_type": null,
"source": "communities",
"is_read": false
}
],
"pagination": {
"next": "https://api.flashpoint.io/alert-management/v1/notifications?created_after=now-7d&created_before=nowATsize=25&cursor=1717444021.230215",
"first": "https://api.flashpoint.io/alert-management/v1/notifications?created_after=now-7d&created_before=nowATsize=25&cursor=1717445812.558666"
}
}
ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
Alert: .items[].reason.name + .items[]., .items[].resource., .items[].resource.site_actor., items[].resource.title[:147]+ items[]..id
|
Event.Title | Alert | .generated_at |
Alert: Insider Threat Alerts... | Keys are used conditionally based on what's available |
.items[].highlights |
Event.Description | N/A | N/A | Nah I need 6 figs stims tho can fly you out where <mark>inny</mark> at... | Description is html formatted with available data |
.items[].status |
Event.Attribute | Status | .generated_at |
N/A | Updatable |
.items[].created_at |
Event.Attribute | Created At | .generated_at |
2024-06-03T20:16:14.716472Z | |
.items[].data_type |
Event.Attribute | Data Type | .generated_at |
chat | N/A |
.items[].source |
Event.Attribute | Source | .generated_at |
communities | N/A |
.items[].is_read |
Event.Attribute | Is Read | .generated_at |
False | Updatable |
.items[].reason.entity.name |
Event.Attribute | Entity | .generated_at |
ThreatQ | N/A |
.items[].reason.name |
Event.Attribute | Category | .generated_at |
Insider Threat Alerts | Updatable |
.items[].reason.text |
Event.Attribute | Search Text | .generated_at |
(\"I am an employee\" OR \"i'm an employee\" OR \"i can get access... | N/A |
.items[].resource.basetypes |
Event.Attribute | Base Type | .generated_at |
chat, conversation | N/A |
.items[].resource.container.title |
Event.Attribute | Container Title | .generated_at |
𝗕𝗜𝗚𝗙𝗔𝗧𝗖𝗛𝗔𝗧™️💰 | N/A |
.items[].soresourceurce.container.container.title |
Event.Attribute | Container Title | .generated_at |
N/A | N/A |
.items[].resource.container.name |
Event.Attribute | Container Name | .generated_at |
𝗕𝗜𝗚𝗙𝗔𝗧𝗖𝗛𝗔𝗧™️💰 | N/A |
.items[].resource.container.container.name |
Event.Attribute | Container Name | .generated_at |
N/A | N/A |
.items[].resource.site.title |
Event.Attribute | Site Title | .generated_at |
Telegram | N/A |
.items[].highlights[].body.text/plain / .items[].highlight_text |
Event.Attribute | Alert Highlights | .generated_at |
Nah I need 6 figs stims tho can fly you out where <mark>inny</mark> at | .items[].highlights[].body.text/plain joined by < /br> or .items[].highlight_text, User-configurable |
.items[].highlights[].body.text/plain / .items[].highlight_text |
Related Vulnerability/Indicator | CVE | .generated_at |
CVE-2025-12389 | CVE values mentioned in .items[].highlights[].body.text/plain or .items[].highlight_text, User-configurable |
.items[].resource.site_actor.names.handle |
Event.Attribute | Site Actor | .generated_at |
RISK | N/A |
.items[].resource.site_actor.names.aliases[] |
Event.Attribute | Site Actor | .generated_at |
N/A | N/A |
.items[].resource.site_actor.names.handle |
Adversary.Value | Adversary | .generated_at |
RISK | User-configurable |
.items[].resource.site_actor.names.aliases[] |
Adversary.Value | Adversary | .generated_at |
N/A | User-configurable |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
| Metric | Result |
|---|---|
| Run Time | 1 minute |
| Adversaries | 24 |
| Events | 25 |
| Event Attributes | 442 |
| Vulnerabilities | 3 |
Change Log
- Version 1.2.7
- Resolved an issue where missing container and title information would cause feed runs to fail with an
error applying filtererror message.
- Resolved an issue where missing container and title information would cause feed runs to fail with an
- Version 1.2.6
- The integration now ingests adversary object types.
- Added a new configuration parameter:
- Link Adversaries to Alerts - link ingested adversaries to alerts.
- Version 1.2.5
- Resolved an issue with incorrect Flashpoint Ignite links for Media type events.
- Version 1.2.4
- Flashpoint Ignite links to alert descriptions are now ingested as descriptions in ThreatQ.
- Version 1.2.3
- Site Actors are no longer ingested as related Adversaries.
- Context information will no longer be included in the description and will now be saved as attributes.
- Added a new configuration parameter:
- Save CVE Data As - select if CVEs should be ingested as Indicators or Vulnerabilities.
- Version 1.2.2
- Added a new configuration parameter: Ingest Highlights. Users can use this setting to control if the feed will ingest
Alert Highlightsattribute. - Removed HTML tags from the
Alert Highlightsattribute.
- Added a new configuration parameter: Ingest Highlights. Users can use this setting to control if the feed will ingest
- Version 1.2.1
- Updated the style for Event descriptions.
- Added
Search TextandAlert Highlightsattributes to Events. - Added Actors as related Adversaries.
- Added two new configuration parameters: Disable Proxies and Enable SSL Verification.
- Version 1.2.0
- Updated the feed to use Flashpoint Ignite Alerts endpoint.
- Alerts now include rich text descriptions containing alert highlights and metadata.
- Alert Titles have been improved.
- The Flashpoint Link attribute has been replaced with a link within the description.
- Rebranded the integration to FlashPoint Ignite Alerts CDF.
- Updated the minimum ThreatQ version to v5.12.1.
- Updated the feed to use Flashpoint Ignite Alerts endpoint.
- Version 1.1.1
- Long alert bodies, which would trigger feed errors, are now truncated.
- Version 1.1.0
- Optimized integration code to improve overall performance and upgraded support tier from Not Supported to ThreatQ Supported.
- Version 1.0.0
- Initial Release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Flashpoint Ignite Alerts CDF Guide v1.2.7 | 5.12.1 or Greater |
| Flashpoint Ignite Alerts CDF Guide v1.2.6 | 5.12.1 or Greater |
| Flashpoint Ignite Alerts CDF Guide v1.2.5 | 5.12.1 or Greater |
| Flashpoint Ignite Alerts CDF Guide v1.2.4 | 5.12.1 or Greater |
| Flashpoint Ignite Alerts CDF Guide v1.2.3 | 5.12.1 or Greater |
| Flashpoint Ignite Alerts CDF Guide v1.2.2 | 5.12.1 or Greater |
| Flashpoint Ignite Alerts CDF Guide v1.2.1 | 5.12.1 or Greater |
| Flashpoint Ignite Alerts CDF Guide v1.2.0 | 5.12.1 or Greater |
| Flashpoint Alerts CDF Guide v1.1.1 | 4.38.0 or Greater |
| Flashpoint Alerts CDF Guide v1.1.0 | 4.38.0 or Greater |
| Flashpoint Alerts CDF Guide v1.0.0 | 4.38.0 or Greater |