Enzoic CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 5.20.0 |
| Support Tier | ThreatQ Supported |
Introduction
Enzoic is a security platform that helps prevent account takeover and fraud through compromised credential detection and password policy enforcement.
The Enzoic CDF for ThreatQ enables the automatic ingestion of all public exposures, or exposures pertaining to a particular domain. These exposures will be ingested as Events, which can be used to alert you of any new exposures that are discovered.
The integration provides the following feeds:
- Enzoic Exposures - ingests all public Exposures from the Enzoic API.
- Enzoic Exposures by Domain - ingests all Exposures and users for a specified domain from the Enzoic API.
The integration ingests the following system object types:
- Identities
- Identity Attributes
- Events
- Event Attributes
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description API Key Your Enzoic API Key. API Secret Your Enzoic API Secret. Require Exposed Password When enabled, the feeds will only ingest exposures that contain a password. Require Category
(Exposures feed only)When enabled, the feed will only ingest exposures that contain a category.
Example: Exposures listed asUnspecifiedwill not be ingested.Minimum Entries
(Exposures feed only)The minimum number of entries an exposure must have in order to be ingested into the platform. Minimum Affected Domains
(Exposures feed only)The minimum number of affected domains an exposure must have in order to be ingested into the platform. Account Domain
(Exposures by Domain feed only)The domain to return exposures. You must have permission to view exposures for the domain.
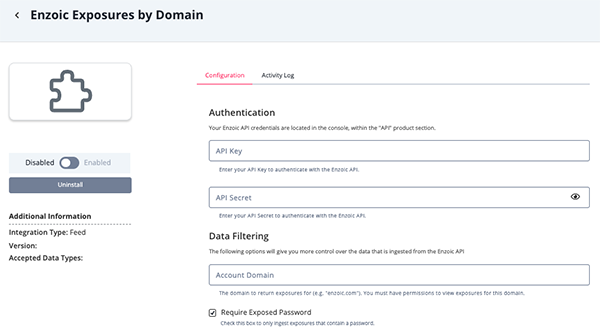
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
Enzoic Exposures
The Enzoic Exposures feed ingests all public Exposures from the Enzoic API.
GET https://api.enzoic.com/v1/exposures-by-date
Sample Response:
{
"count": 3,
"pagingToken": null,
"exposures": [
{
"category": "Unspecified",
"date": "2023-05-16T00:00:00.000Z",
"dateAdded": "2023-05-16T07:02:13.000Z",
"domainsAffected": 10,
"entries": 60,
"exposedData": ["Emails", "Passwords"],
"id": "64632a759c64dcd3258785f0",
"passwordType": "Cleartext",
"source": "Messaging Services",
"sourceFileCount": 1,
"sourceURLs": ["telegram client"],
"title": "Telegram File Download #2528 on Channel #-1001780683792"
},
{
"category": "Unspecified",
"date": "2023-05-16T00:00:00.000Z",
"dateAdded": "2023-05-16T10:54:30.000Z",
"domainsAffected": 2,
"entries": 59,
"exposedData": ["Emails", "Passwords"],
"id": "646360e61368b1a3e91333f8",
"passwordType": "Cleartext",
"source": "Messaging Services",
"sourceFileCount": 1,
"sourceURLs": [],
"title": "Telegram Message #45216 on Channel #-1001227389993"
},
{
"category": "Unspecified",
"date": "2023-05-16T00:00:00.000Z",
"dateAdded": "2023-05-16T13:08:57.000Z",
"domainsAffected": 4,
"entries": 9,
"exposedData": ["Emails", "Passwords"],
"id": "646380694b721434189ae7e5",
"passwordType": "Cleartext",
"source": "Messaging Services",
"sourceFileCount": 1,
"sourceURLs": [],
"title": "Telegram File Download #2531 on Channel #-1001780683792"
}
]
}ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
.title |
Event.Title | Exposure | .dateAdded |
funsurveys.net |
N/A |
.category |
Event.Attribute | Category | .dateAdded |
Manufacturing |
N/A |
.domainsAffected |
Event.Attribute | Domains Affected | .dateAdded |
683 |
If the attribute already exists, the value will be updated. |
.entries |
Event.Attribute | Entries | .dateAdded |
5123 |
If the attribute already exists, the value will be updated. |
.exposedData |
Event.Attribute | Exposed Data | .dateAdded |
Emails |
N/A |
.passwordType |
Event.Attribute | Exposed Password Type | .dateAdded |
Cleartext |
N/A |
.source |
Event.Attribute | Source | .dateAdded |
Cybercrime Forums |
N/A |
.sourceURLs[] |
Event.Attribute | Source URL | .dateAdded |
N/A | N/A |
Enzoic Exposures by Domain
The Enzoic Exposures by Domain feed ingests all Exposures & users for a specified domain, from the Enzoic API.
GET https://api.enzoic.com/v1/exposures-for-domain-users
Sample Response:
{
"count": 1,
"pagingToken": "598e5b844eb6d82ea07c5783",
"users": [
{
"username": "sample@email.tst",
"exposures": ["57dc11964d6db21300991b78"]
}
]
}ThreatQuotient provides the following default mapping for this feed:
The majority of the mapping for this feed will be under the Enzoic Exposure by ID supplemental feed.
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes | |
|---|---|---|---|---|---|---|
.users[].username |
Identity.Value | N/A | N/A | N/A | N/A | N/A |
| N/A | Identity.Attribute | Is Exposed | N/A | N/A | true |
N/A |
Enzoic Exposures by ID Supplemental
The Enzoic Exposures by ID supplemental feed fetches a given Exposure by ID from the Enzoic API.
GET https://api.enzoic.com/v1/exposure-details?id={ exposure_id }
Sample Response:
{ "id": "57dc11964d6db21300991b78", "title": "funsurveys.net", "entries": 5123, "date": "2015-05-01T00:00:00.000Z", "category": "Manufacturing", "source": "Cybercrime Forums", "passwordType": "Cleartext", "exposedData": [ "Emails", "Passwords" ], "dateAdded": "2016-09-16T15:36:54.000Z", "sourceURLs": [ "https://www.someplace.com" ], "domainsAffected": 683, "sourceFileCount": 1 }
ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes | |
|---|---|---|---|---|---|---|
.title |
Event.Title | Exposure | .dateAdded |
funsurveys.net |
N/A | |
.category |
Event.Attribute | Category | .dateAdded |
Manufacturing |
N/A | |
.domainsAffected |
Event.Attribute | Domains Affected | .dateAdded |
683 |
If the attribute already exists, the value will be updated. | |
.entries |
Event.Attribute | Entries | .dateAdded |
5123 |
If the attribute already exists, the value will be updated. | |
.exposedData |
Event.Attribute | Exposed Data | .dateAdded |
Emails |
N/A | |
.passwordType |
Event.Attribute | Exposed Password Type | .dateAdded |
Cleartext |
N/A | |
.source |
Event.Attribute | Source | .dateAdded |
Cybercrime Forums |
N/A | |
.sourceURLs[] |
Event.Attribute | Source URL | .dateAdded |
N/A | N/A |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
Enzoic Exposures
| Metric | Result |
|---|---|
| Run Time | 1 minute |
| Events | 3 |
| Event Attributes | 21 |
Enzoic Exposures by Domain
| Metric | Result |
|---|---|
| Run Time | 1 minute |
| Identities | 3 |
| identity Attributes | 3 |
| Events | 3 |
| Event Attributes | 21 |
Known Issues / Limitations
- Enzoic Exposures - due to an Enzoic API limitation, the exposure feed can only return exposures found in the past 30 days.
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Enzoic CDF Guide v1.0.0 | 5.20.0 or Greater |