CTM360 HackerView CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 4.58.1 |
| Support Tier | ThreatQ Supported |
Introduction
The CTM360 HackerView CDF provides a feed that ingests incidents and related indicators of compromise from CTM360 HackerView.
The integration provides the following feed:
- CTM360 HackerView - ingests incidents with related indicators of compromise.
The integration ingests the following system objects:
- Events - type Incident
- Indicators - IP Addresses and FQDNs
Prerequisites
An API Key for CTM360 HackerView is required by the integration.
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description API Host Enter the CTM360 hostname without https://. The default is hackerview.ctm360.com.API Key Enter your API Key for authentication. Verify Host SSL When enabled, the integration will validate the server certificate.
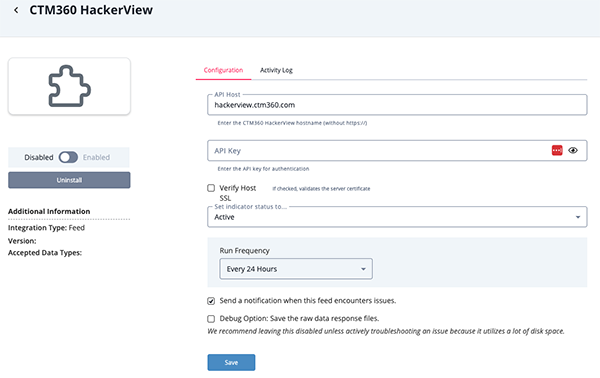
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
The CTM360 HackerView feed returns the incidents and related IOCs (FQDN and URL).
GET https://hackerview.ctm360.com/api/v2/issues
Sample Response:
{
"success": true,
"message": "Ok",
"issues": [
{
"severity": "medium",
"fixing_effort": "Moderate",
"issue_type": [
"IT Hygiene"
],
"issue_category": [
"IP Reputation"
],
"potential_attack_type": [],
"cwe": [],
"issue_name": "IP Blacklisted",
"meta": {
"first_seen": "23-04-2023 23:41:54",
"last_seen": "23-04-2023 23:41:54",
"environments": [
"Web servers"
],
"hosts": [
"gateway.example.com"
],
"ip": "223.197.225.224",
"ip_type": "dedicated",
"ticket_id": "HVI-12887306",
"business_unit": [],
"technologies": [
"Lighttpd"
],
"discovery_source": [
"ssl_certificate"
],
"asset_type": "ip",
"asset": "223.197.225.224",
"brand": "ISS Enterprise"
},
"detail": "[\"224.225.197.223.b.barracudacentral.org\", \"224.225.197.223.spam.dnsbl.sorbs.net\"]",
"progress_status": "New",
"status": "active",
"assigned_to": "unassigned",
"potential_impact": [],
"hackerview_link": "https://hackerview.ctm360.com/issues/issues_found/overview/e2d72bc443a977751eb5f2e474464672/46"
},
{
"severity": "medium",
"fixing_effort": "Moderate",
"issue_type": [
"Vulnerability"
],
"issue_category": [
"Common Vulnerabilities"
],
"potential_attack_type": [],
"cwe": [],
"issue_name": "Medium Severity CVE Detected",
"cve_id": "CVE-2022-22707",
"meta": {
"first_seen": "23-04-2023 23:41:54",
"last_seen": "23-04-2023 23:41:54",
"environments": [
"Web servers"
],
"hosts": [
"gateway.example.com"
],
"ip": "223.197.225.224",
"ip_type": "dedicated",
"ticket_id": "HVI-59434846",
"business_unit": [],
"technologies": [
"Lighttpd"
],
"discovery_source": [
"ssl_certificate"
],
"asset_type": "ip",
"asset": "223.197.225.224",
"brand": "ISS Enterprise"
},
"detail": null,
"progress_status": "New",
"status": "active",
"assigned_to": "unassigned",
"potential_impact": [],
"hackerview_link": "https://hackerview.ctm360.com/issues/issues_found/overview/995e6cfb7dc33282f04323aeabdeae37/202222707"
}
]
}
ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| issues[].issue_type[] | Event Attributes | Issue Type | ["Vulnerability"] | N/A | |
| issues[].issue_category[] | Event Attributes | Issue Category | ["Common Vulnerabilities"] | N/A | |
| issues[].potential_attack_type[] | Event Attributes | Potential Attack Type | ["Brute Force Attack", "Data Leakage"] | N/A | |
| issues[].potential_impact[] | Event Attributes | Potential Impact | ["Loss of Integrity","Loss of Confidentiality","Loss of Availability","Access Control Issues"] |
N/A | |
| issues[].severity | Event Attributes | Severity | medium | N/A | |
| issues[].fixing_effort | Event Attributes | Fixing Effort | Moderate | N/A | |
| issues[].hackerview_link | Event Attributes | HackerView Link | https://hackerview.ctm360.com/ issues/issues_found/overview/99 5e6cfb7dc33282f04323aeabdeae3 7/202222707 |
N/A | |
| issues[].progress_status | Event Attributes | Progress Status | New | N/A | |
| issues[].status | Event Attributes | Status | active | N/A | |
| issues[].assigned_to | Event Attributes | Assigned To | unassigned | N/A | |
| issues[].meta{}.environments[] | Indicator Attributes | Environments | ["Web servers"] | N/A | |
| issues[].meta{}.technologies[] | Indicator Attributes | Technologies | ["Lighttpd"] | N/A | |
| issues[].meta{}.discovery_source[] | Indicator Attributes | Discovery Source | ["ssl_certificate"] | N/A | |
| issues[].meta{}.brand[] | Indicator Attributes | Brand | ISS Enterprise | N/A | |
| issues[].meta{}.ip_type[] | Indicator Attributes | IP Type | Dedicated | N/A | |
| issues[].meta{}.last_seen[] | Indicator Attributes | Last Seen | 27-04-2023 23:27:18 | N/A | |
| issues[].meta{}.first_seen[] | Indicator Attributes | First Seen | 27-04-2023 23:27:18 | N/A | |
| issues[].meta{}.asset | Indicator | IP Address/FQDN | 49.12.128.248 | N/A | |
| issues[].cve_id | Indicator | CVE | CVE-2023-28625 | N/A | |
| issues[].issue_name (Ticket ID: issues[].meta{}.ticket_id) | Event | Event Name | SSH Uses Weak Cipher (Ticket ID: HVI-57067419) | N/A |
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| CTM360 HackerView CDF Guide v1.0.0 | 4.58.1 or Greater |