CISA ICS Advisories CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 4.52.0 |
| Support Tier | ThreatQ Supported |
Introduction
The CISA ICS Advisories CDF consumes data provided by the CISA to notify organizations about threats that exist on the Internet.
The integration provides the following feeds:
- CISA ICS Advisories - ingests threat intelligence from CISA and creates ThreatQ reports and related indicators.
The integration ingests the following system objects:
- Indicators
- Indicator Attributes
- Reports
- Report Attributes
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the OSINT option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description Verify Host SSL When enabled, the integration will validate the host-provided SSL certificate. This parameter is enabled by default. Parse for Selected Indicators Select the type of indicators to parse. Options include: - CVEs
- MD5
- Hashes
- SHA-1 Hashes
- SHA-256 Hashes
- SHA-512 Hashes
- IP Addresses
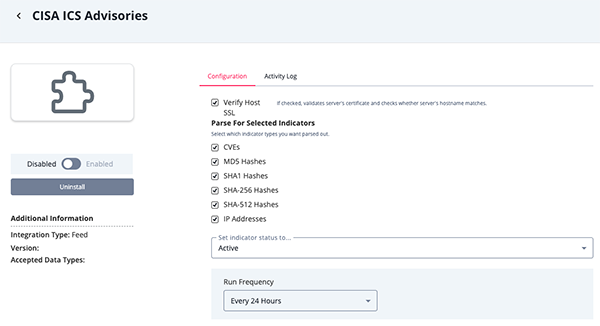
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
CISA ICS Advisories
The CISA ICS Advisories feed consumes data provided by the CISA to create reports and related indicators.
GET https://www.cisa.gov/cybersecurity-advisories/ics-advisories.xml
Sample Response:
<?xml version="1.0" encoding="utf-8"?>
<rss xmlns:dc="http://purl.org/dc/elements/1.1/" version="2.0" xml:base="https://www.cisa.gov/">
<channel>
<title>ICS Advisories</title>
<link>https://www.cisa.gov/</link>
<description/>
<language>en</language>
<item>
<title>Carlo Gavazzi Powersoft</title>
<link>https://www.cisa.gov/news-events/ics-advisories/icsa-23-138-01</link>
<description><h2>1. EXECUTIVE SUMMARY</h2>
<ul><li><strong>CVSS v3 7.5</strong></li>
<li><strong>ATTENTION:</strong> Exploitable remotely/low attack complexity/public exploits are available</li>
<li><strong>Vendor:</strong> Carlo Gavazzi</li>
<li><strong>Equipment:</strong> Powersoft</li>
<li><strong>Vulnerabilities:</strong> Path Traversal</li>
</ul><h2>2. RISK EVALUATION</h2>
<p>Successful exploitation of this vulnerability could allow an attacker to access and retrieve any file from the server. </p>
<h2>3. TECHNICAL DETAILS</h2>
<h3>3.1 AFFECTED PRODUCTS</h3>
<p>The following versions of Carlo Gavazzi Powersoft, an energy management software, are affected:</p>
<ul><li>Powersoft: Versions 2.1.1.1 and prior</li>
</ul><h3>3.2 VULNERABILITY OVERVIEW</h3>
<p><strong>3.2.1 <a href="https://cwe.mitre.org/data/definitions/22.html" rel="noreferrer noopener" target="_blank">IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22</a></strong></p>
<p>Carlo Gavazzi Powersoft versions 2.1.1.1 and prior have a directory traversal vulnerability that can allow an attacker to access and retrieve any file through specially crafted GET requests to the server.</p>
<p><a href="http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017-20184" rel="noreferrer noopener" target="_blank">CVE-2017-20184</a> has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been calculated; the CVSS vector string is (<a href="https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N" rel="noreferrer noopener" target="_blank">AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N</a>).</p>
<h3>3.3 BACKGROUND</h3>
<ul><li><strong>CRITICAL INFRASTRUCTURE SECTORS: </strong>Critical Manufacturing</li>
<li><strong>COUNTRIES/AREAS DEPLOYED:</strong> Worldwide</li>
<li><strong>COMPANY HEADQUARTERS LOCATION: </strong>Switzerland</li>
</ul><h3>3.4 RESEARCHER</h3>
<p>CISA discovered a public proof-of-concept as authored by James Fitts.</p>
<h2>4. MITIGATIONS</h2>
<p>Carlo Gavazzi will not issue a fix as this product is end-of-life.</p>
<p>Users should contact <a href="https://www.gavazziautomation.com/nsc/HQ/EN/our_sales_network" rel="noreferrer noopener" target="_blank">Carlo Gavazzi</a> for more information.</p>
<p>CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability. Specifically, users should:</p>
<ul><li>Minimize network exposure for all control system devices and/or systems, and ensure they are <a href="https://www.cisa.gov/uscert/ics/alerts/ICS-ALERT-10-301-01" rel="noreferrer noopener" target="_blank">not accessible from the Internet</a>.</li>
<li>Locate control system networks and remote devices behind firewalls and isolate them from business networks.</li>
<li>When remote access is required, use secure methods, such as virtual private networks (VPNs), recognizing VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize VPN is only as secure as its connected devices.</li>
</ul><p>CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.</p>
<p>CISA also provides a section for <a href="https://us-cert.cisa.gov/ics/Recommended-Practices" rel="noreferrer noopener" target="_blank">control systems security recommended practices</a> on the ICS webpage at <a href="https://cisa.gov/ics" rel="noreferrer noopener" target="_blank">cisa.gov/ics</a>. Several CISA products detailing cyber defense best practices are available for reading and download, including <a href="https://us-cert.cisa.gov/sites/default/files/recommended_practices/NCCIC_ICS-CERT_Defense_in_Depth_2016_S508C.pdf" rel="noreferrer noopener" target="_blank">Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies</a>.</p>
<p>Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at <a href="https://cisa.gov/ics" rel="noreferrer noopener" target="_blank">cisa.gov/ics</a> in the technical information paper, <a href="https://www.cisa.gov/uscert/ics/tips/ICS-TIP-12-146-01B" rel="noreferrer noopener" target="_blank">ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies</a>.</p>
<p>Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.</p>
</description>
<pubDate>Thu, 18 May 23 12:00:00 +0000
</pubDate>
<dc:creator>CISA</dc:creator>
<guid isPermaLink="false">/node/18185</guid>
</item>
</channel>
</rss>ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| .rss.channel.item[].title | Report Title | N/A | .rss.channel.item[].pubDate | Carlo Gavazzi Powersoft: Thu, 18 May 23 12:00:00 +0000 | PubDate is appended to the title |
| .rss.channel.item[].description | Report Description | N/A | N/A | As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens ... | Description is formatted and truncated |
| .rss.channel.item[].link | Report Attribute | URL | .rss.channel.item[].pubDate | https://www.cisa.gov/news-events/ics-advisories/icsa-23-138-01 | N/A |
| N/A | Report Attribute | CISA Feed Name | .rss.channel.item[].pubDate | ICS Advisories | N/A |
| .rss.channel.item[].description | Report Attribute | Vendor | .rss.channel.item[].pubDate | Carlo Gavazzi | Attribute parsed from description |
| .rss.channel.item[].description | Report Attribute | Equipment | .rss.channel.item[].pubDate | Powersoft | Attribute parsed from description |
| .rss.channel.item[].description | Report Attribute | CVSS Score | .rss.channel.item[].pubDate | 7.5 | Attribute parsed from description |
| .rss.channel.item[].description | Indicator Value | IP Address, CVE, MD5, SHA-1, SHA-256, or SHA-512 | .rss.channel.item[].pubDate | CVE-2017-20184 | Indicators are parsed out of the description and ingested based on Parse For Selected Indicators selection |
| N/A | Indicator Attribute | CISA Activity | .rss.channel.item[].pubDate | True | N/A |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
| Metric | Result |
|---|---|
| Run Time | 1 min |
| Reports | 10 |
| Report Attributes | 50 |
| Indicators | 40 |
| Indicator Attributes | 40 |
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| CISA ICS Advisories CDF Guide v1.0.0 | 4.52.0 or Greater |