CISA Bulletins CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.1 |
| Compatible with ThreatQ Versions | >= 4.52.0 |
| Support Tier | ThreatQ Supported |
Introduction
The CISA Bulletins CDF consumes data provided by the CISA to notify organizations about threats that exist on the Internet.
The integration provides the following feeds:
- CISA Bulletins - creates a ThreatQ Alert Event and ingests related objects.
The integration ingests the following system objects:
- Events
- Event Attributes
- Indicators
- Indicator Attributes
- TTPs
- TTP Attributes
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the OSINT option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description Verify Host SSL When enabled, the integration will validate the host-provided SSL certificate. This parameter is enabled by default. Parse for Selected Indicators Select the type of indicators to parse. Options include: - CVEs
- MD5
- Hashes
- SHA-1 Hashes
- SHA-256 Hashes
- SHA-512 Hashes
- IP Addresses
This parameter does not apply to parsed STIX files.
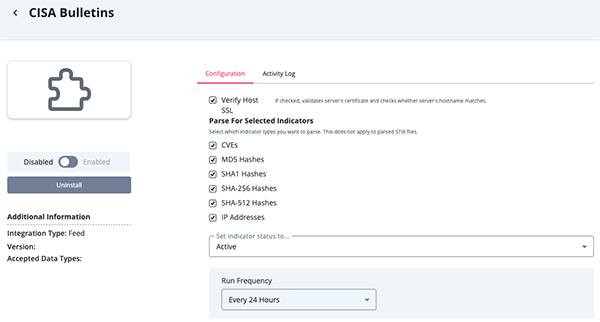
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
CISA Bulletins
The CISA Bulletins feed creates a ThreatQ Alert Event and ingests related objects.
GET https://www.cisa.gov/cybersecurity-advisories/bulletins.xml
CISA Bulletins, Get Report HTML (Supplemental) and Get Attachment (Supplemental) feeds bring in information about current security issues, vulnerabilities and exploits into ThreatQ.
Sample Response (XML):
<?xml version="1.0" encoding="utf-8"?>
<rss xmlns:dc="https://purl.org/dc/elements/1.1/" version="2.0" xml:base="https://www.cisa.gov/">
<channel>
<title>Bulletins</title>
<link>https://www.cisa.gov/</link>
<description/>
<language>en</language>
<item>
<title>Vulnerability Summary for the Week of May 8, 2023</title>
<link>https://www.cisa.gov/news-events/bulletins/sb23-135</link>
<description><h3>Summary</h3>
<p><em>Note: This joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These #StopRansomware advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware. Visit </em><a href="https://www.cisa.gov/stopransomware"><em>stopransomware.gov</em></a><em> to see all #StopRansomware advisories and learn more about other ransomware threats and no-cost resources.</em></p>
<p>The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Cyber Security Centre (ACSC) are releasing this joint Cybersecurity Advisory to disseminate known BianLian ransomware and data extortion group IOCs and TTPs identified through FBI and ACSC investigations as of March 2023.</p>
<table><tbody><tr><td>
<div>
<p><strong>Actions to take today to mitigate cyber threats from BianLian ransomware and data extortion: </strong><br />
• Strictly limit the use of RDP and other remote desktop services.<br />
• Disable command-line and scripting activities and permissions.<br />
• Restrict usage of PowerShell and update Windows PowerShell or PowerShell Core to the latest version.</p>
</div>
</td>
</tr></tbody></table><p>BianLian is a ransomware developer, deployer, and data extortion cybercriminal group that has targeted organizations in multiple U.S. critical infrastructure sectors since June 2022. They have also targeted Australian critical infrastructure sectors in addition to professional services and property development. The group gains access to victim systems through valid Remote Desktop Protocol (RDP) credentials, uses open-source tools and command-line scripting for discovery and credential harvesting, and exfiltrates victim data via File Transfer Protocol (FTP), Rclone, or Mega. BianLian group actors then extort money by threatening to release data if payment is not made. BianLian group originally employed a double-extortion model in which they encrypted victims’ systems after exfiltrating the data; however, around January 2023, they shifted to primarily exfiltration-based extortion.</p>
<p>FBI, CISA, and ACSC encourage critical infrastructure organizations and small- and medium-sized organizations to implement the recommendations in the Mitigations section of this advisory to reduce the likelihood and impact of BianLian and other ransomware incidents.</p>
<p>Download the PDF version of this report (710kb):</p>
</description>
<pubDate>Mon, 15 May 2023 08:09:48 EDT</pubDate>
<dc:creator>CISA</dc:creator>
<guid isPermaLink="false">/node/18173</guid>
</item>
</channel>
</rss>
ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| .rss.channel.item[].title | Event.Title | N/A | .rss.channel.item[]. pubDate |
Vulnerability Summary for the Week of May 8, 2023 | N/A |
| N/A | Event.Type | Alert | N/A | Alert | N/A |
| .rss.channel.item[].description | Event.Description | N/A | N/A | Note: This joint Cybersecurity Advisory (CSA) is part | Depending on the description length, the value can be replaced by the actual article's HTML. That HTML is get by Get Report HTML (Supplemental) feed |
| .rss.channel.item[].pubDate | Event.Happened_at | N/A | N/A | Mon, 15 May 2023 08:09:48 EDT | N/A |
| N/A | Event.Attribute/ Indicator.Attribute |
CISA Bulletins | .rss.channel.item[]. pubDate |
True | N/A |
| N/A | Event.Attribute | Alert type | .rss.channel.item[]. pubDate |
CISA Bulletins | N/A |
| .rss.channel.item[].link | Event.Attribute | URL | .rss.channel.item[]. pubDate |
https://www.cisa.gov/news-events/bulletins/sb23-135 | N/A |
| .rss.channel.item[].description | Event.Attribute | PDF Link | .rss.channel.item[]. pubDate |
N/A | The link is extracted from the article's description |
| .rss.channel.item[].description | Event.Attribute | Stix Link | .rss.channel.item[]. pubDate |
N/A | The link is extracted from the article's description |
| .rss.channel.item[].description | Indicator.Value | IP Address, CVE, MD5, SHA-1, SHA-256, or SHA-512 | .rss.channel.item[]. pubDate |
N/A | Indicators are parsed out of the description |
| STIX File | (Indicator,TTP,Incident).value | Indicator, TTP, Incident | .rss.channel.item[]. pubDate |
N/A | STIX file is get by the Get Attachment (Supplemental) feed and then it's parsed for the indicators, TTPs, and incidents |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
| Metric | Result |
|---|---|
| Run Time | 5 hours |
| Events | 10 |
| Event Attributes | 30 |
| Indicators | 6,859 |
| Indicator Attributes | 6,859 |
| TTPs | 37 |
| TTP Attributes | 37 |
Change Log
- Version 1.0.1
- Removed the inter-related relationships flag which caused a large amount of relationships to be created. Indicators will now only be related to their respective events.
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| CISA Bulletins CDF v1.0.1 | 4.52 or Greater |
| CISA Bulletins CDF v1.0.0 | 4.52 or Greater |