ANY.RUN CDF
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 4.34.0 |
| Support Tier | Not Actively Supported |
Introduction
The ANY.RUN CDF for ThreatQ enables a ThreatQ user to automatically ingest malware samples, malware analysis reports, and related IOCs from samples that your organization submitted to ANY.RUN. The integration then parses the data and ingests it into ThreatQ.
The integration provides the Any.Run feed, which utilizes five endpoints when performing a run:
- Analysis Endpoint (JSON) - Returns a rolling history of your organization's submissions to the ANY.RUN sandbox. It does not include the actual reports
- Report Endpoint (JSON) - Returns the actual report/analysis results for a given task
- IOC Endpoint (JSON) - Returns IOCs related to a given analysis.
- Analysis HTML Report (Attachment) - Returns an HTML file containing a formatted report for the given sample. See the Known Issues / Limitations topic for important details regarding this endpoint.
- TQ Attachments Endpoint (TQ) - Allows you to search for an existing report for a sample to avoid uploading duplicate reports.
Installation
This integration can be installed in the My Integration section of your ThreatQ instance. See the Adding an Integration topic for more details.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Commercial option from the Category dropdown (optional).
- Click on the integration entry to open its details page.
- Enter the following parameter under the Configuration tab:
Parameter Description API Key Your ANY.RUN API Key for authentication
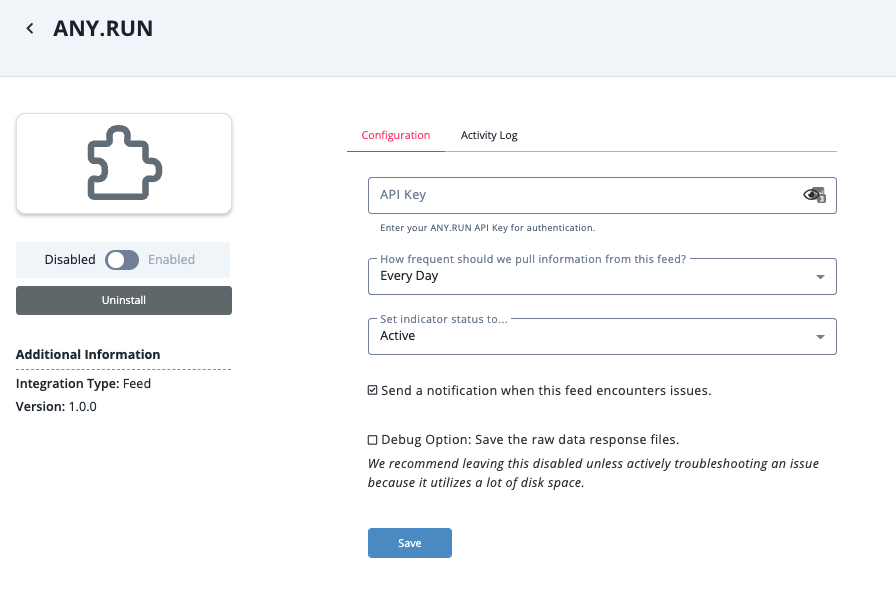
- Review any additional settings, make any changes if needed, and click on Save.
- Click on the toggle switch, located above the Additional Information section, to enable it.
ThreatQ Mapping
ANY.RUN
The ANY.RUN feed will fetch the reports and malware samples from ANY.RUN, then parse the data and add them into ThreatQ. This feed is fairly complicated. In order to complete, it needs to fetch 3 different JSON endpoints, 1 attachment endpoint, and 1 TQ endpoint. Below are the reasonings for each:
- Analysis Endpoint (JSON): This endpoint will return a rolling history of your organization's submissions to the ANY.RUN sandbox. It does not include the actual reports
- Report Endpoint (JSON): Returns the actual report/analysis results for a given task
- IOC Endpoint (JSON): Returns IOCs related to a given analysis
- Analysis HTML Report (Attachment): This endpoint will return an HTML file containing a nicely formatted report for the given sample.
- TQ Attachments Endpoint (TQ): This endpoint allows us to search for an existing report for a sample. if it exists, we don't want to re-upload it.
Analysis Endpoint (JSON)
In addition, the Analysis Endpoint (history) does not allow you to filter by date. As a result, we need to filter by date within the filter section of the CDF. Another fault of the endpoint is it returns a single date field. This date reflects the date the sample was submitted. There is no date when the analysis was finished, and the analysis only shows up in the Analysis Endpoint when the analysis is finished. This leaves room for reports to be "missed". As a result, we not only check the date for filtering, but we also apply a 1 hour offset. We'll let ThreatQ handle all the de-duplication.
GET https://api.any.run/v1/analysis
Sample Response:
{
"error": false,
"data": {
"tasks": [
{
"verdict": "Suspicious activity",
"name": "2aa0b2d90346ba275235c8f86981eec3a320b194-filelists.xml.gz",
"related": "https://app.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77",
"pcap": "https://content.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77/download/pcap",
"file": "https://content.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77/download/files/1e4a5669-378a-49c6-845b-08a16e46bfce",
"json": "https://api.any.run/report/26357aef-3279-4c63-8216-c4e302756b77/summary/json",
"misp": "https://api.any.run/report/26357aef-3279-4c63-8216-c4e302756b77/summary/misp",
"tags": [],
"date": "2020-05-21T18:19:50.603Z",
"hashes": {
"ssdeep": "3072:R3Kdd6ydBPWmNCWu7ltAVkMmGGlcVB8ykFtALH+8ukqKSEX6exUn0nF2Qy2:R6ddbdBPjwuVkM8y8ArHgEqsnF2Qh",
"head_hash": "1e3fe6584090935cd35b7b969b5dd2a5",
"sha256": "bcc3e05d6049c28e98a80a1bc1f2de8257293e7cb1c1456d328fd94199a18fa3",
"sha1": "2aa0b2d90346ba275235c8f86981eec3a320b194",
"md5": "364754de96718625f9df7e333370e825"
}
}
]
}
}
Report Endpoint (JSON)
The Report Endpoint (JSON) feed returns the actual report/analysis results for a given task.
GET https://api.any.run/report/<Analysis ID>/summary/json
Sample Response:
{
"mitre": [
{
"name": "Credentials in Files",
"phases": [
"credential-access"
],
"id": "T1081"
}
],
"counters": {
"registry": {
"delete": 0,
"write": 103,
"read": 1153,
"total": 1256
},
"files": {
"malicious": 0,
"suspicious": 7,
"text": 3,
"unknown": 0
},
"network": {
"threats": 0,
"dns": 3,
"connections": 2,
"http": 1
},
"processes": {
"malicious": 0,
"suspicious": 1,
"monitored": 6,
"total": 45
}
},
"incidents": [
{
"process": "88ea0c86-e428-4fb3-80b2-beb79400c632",
"events": [
{
"time": 1590085239479,
"image": "C:\\Program Files\\Internet Explorer\\iexplore.exe",
"cmdChild": "\"C:\\Program Files\\Internet Explorer\\iexplore.exe\" SCODEF:620 CREDAT:78849 /prefetch:2",
"cmdParent": "\"C:\\Program Files\\Internet Explorer\\iexplore.exe\" -nohome"
}
],
"mitre": [
"T1106"
],
"count": 1,
"firstSeen": 1590085239479,
"source": "Unknown",
"desc": "Suspicious actions",
"title": "Application launched itself",
"threatLevel": 0
}
],
"debugStrings": [],
"network": {
"threats": [],
"connections": [
{
"reputation": "whitelisted",
"time": 1590085245334,
"process": "88ea0c86-e428-4fb3-80b2-beb79400c632",
"asn": "Microsoft Corporation",
"country": "US",
"protocol": "tcp",
"port": 80,
"ip": "204.79.197.200"
}
],
"httpRequests": [
{
"country": "US",
"reputation": "whitelisted",
"body": {
"response": {
"hashes": {
"sha256": "6d8a01dc7647bc218d003b58fe04049e24a9359900b7e0cebae76edf85b8b914",
"sha1": "ea13848d33c2c7f4f4baa39348aeb1dbfad3df31",
"md5": "9fb559a691078558e77d6848202f6541"
},
"permanentUrl": "https://content.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77/download/files/8f03dca7-0893-49f2-bf12-6f09899b86bc",
"threatLevel": "LOW",
"type": "image",
"size": 237
}
},
"process": "88ea0c86-e428-4fb3-80b2-beb79400c632",
"httpCode": 200,
"status": "RESPONDED",
"proxyDetected": false,
"port": 80,
"ip": "204.79.197.200",
"url": "http://www.bing.com/favicon.ico",
"host": "www.bing.com",
"method": "GET",
"time": 1590085245337
}
],
"dnsRequests": [
{
"reputation": "whitelisted",
"ips": [
"204.79.197.200",
"13.107.21.200"
],
"domain": "www.bing.com",
"time": 1590085244307
},
{
"reputation": "shared",
"ips": [
"13.107.5.80"
],
"domain": "api.bing.com",
"time": 1590085244311
}
]
},
"modified": {
"registry": [
{
"time": 1590085207729,
"process": "4a29ff5a-7cc6-4496-b374-d3091261da74",
"operation": "write",
"value": "",
"name": "ShellExtBMP",
"key": "HKEY_CURRENT_USER\\Software\\WinRAR\\Interface\\Themes"
}
],
"files": [
{
"permanentUrl": "https://content.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77/download/files/1ca3a0df-9669-46dc-af2c-ff0a725ee404",
"hashes": {
"md5": "664c6804e1bfbc59c093b6e02a3994a5",
"sha1": "d8a2cdf67f677e034be0473771f694daa1025329",
"sha256": "a9e945a4ae5f78769ee8b1905dac2f647ec7b245b1be4c3c1ca2d612946d5aae",
"head_hash": "664c6804e1bfbc59c093b6e02a3994a5",
"ssdeep": "12:rlxAFLNtsDrEgm8G/7KFLcklXDrEgm8Gn7qjNlgOjgaRE4:reAG8vcklTG8pNl2aRT"
},
"info": {
"file": "application/CDFV2"
},
"process": "88ea0c86-e428-4fb3-80b2-beb79400c632",
"threatLevel": "MID",
"type": "binary",
"size": 3584,
"filename": "C:\\Users\\admin\\AppData\\Local\\Microsoft\\Internet Explorer\\Recovery\\Active\\{C52EA11F-9B8F-11EA-972D-5254004A04AF}.dat",
"time": 1590085257073
}
]
},
"processes": [
{
"modules": [
{
"image": "c:\\windows\\system32\\cfgmgr32.dll",
"time": 1590085207651
}
],
"exitCode": 0,
"status": "COMPLETED",
"scores": {
"specs": {
"privEscalation": false,
"stealing": true,
"networkLoader": false,
"network": false,
"lowAccess": false,
"knownThreat": false,
"injects": false,
"exploitable": false,
"executableDropped": false,
"debugOutput": false,
"crashedApps": false,
"autoStart": false
},
"loadsSusp": false,
"injected": false,
"dropped": false,
"monitoringReason": "Main process",
"verdict": {
"threatLevelText": "Suspicious activity",
"threatLevel": 1,
"score": 52
}
},
"context": {
"userName": "admin",
"integrityLevel": "MEDIUM",
"rebootNumber": 0
},
"versionInfo": {
"version": "5.60.0",
"description": "WinRAR archiver",
"company": "Alexander Roshal"
},
"times": {
"monitoringSince": 1590085207589,
"terminate": 1590085252901,
"start": 1590085207589
},
"mainProcess": true,
"fileType": "UNKNOWN",
"fileName": "WinRAR.exe",
"commandLine": "\"C:\\Program Files\\WinRAR\\WinRAR.exe\" \"C:\\Users\\admin\\AppData\\Local\\Temp\\2aa0b2d90346ba275235c8f86981eec3a320b194-filelists.xml.gz\"",
"image": "C:\\Program Files\\WinRAR\\WinRAR.exe",
"uuid": "4a29ff5a-7cc6-4496-b374-d3091261da74",
"ppid": 372,
"pid": 2464
}
],
"environments": {
"hotfixes": [
{
"title": "KB976902"
}
],
"software": [
{
"version": "12.0.21005",
"title": "Microsoft Visual C++ 2013 x86 Additional Runtime - 12.0.21005"
}
],
"internetExplorer": { "redacted": true },
"os": {
"bitness": 32,
"softSet": "complete",
"servicePack": "1",
"major": "7",
"productType": "Client",
"variant": "Professional",
"product": "Windows",
"build": 7601,
"title": "Windows 7 Professional Service Pack 1 (build: 7601, 32 bit)"
}
},
"analysis": {
"content": {
"screenshots": [ "redacted" ],
"pcap": {
"permanentUrl": "https://content.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77/download/pcap",
"present": true
},
"video": { "redacted": true },
"mainObject": {
"info": {
"trid": [
{
"filetype": "GZipped data",
"extension": ".z/gz/gzip",
"procent": 100
}
],
"exif": {
"ZIP": {
"ArchivedFileName": "/u01/basecamp/www/ol7_x86_64_addons/.repodata/filelists.xml",
"OperatingSystem": "unknown",
"ExtraFlags": "Maximum Compression",
"ModifyDate": "0000:00:00 00:00:00",
"Flags": "FileName",
"Compression": "Deflated"
}
},
"mime": "application/gzip",
"file": "gzip compressed data, was \"/u01/basecamp/www/ol7_x86_64_addons/.repodata/filelists.xml\", max compression",
"ext": "gz"
},
"hashes": {
"ssdeep": "3072:R3Kdd6ydBPWmNCWu7ltAVkMmGGlcVB8ykFtALH+8ukqKSEX6exUn0nF2Qy2:R6ddbdBPjwuVkM8y8ArHgEqsnF2Qh",
"sha256": "bcc3e05d6049c28e98a80a1bc1f2de8257293e7cb1c1456d328fd94199a18fa3",
"sha1": "2aa0b2d90346ba275235c8f86981eec3a320b194",
"md5": "364754de96718625f9df7e333370e825"
},
"filename": "2aa0b2d90346ba275235c8f86981eec3a320b194-filelists.xml.gz",
"permanentUrl": "https://content.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77/download/files/1e4a5669-378a-49c6-845b-08a16e46bfce",
"type": "file"
}
},
"scores": {
"specs": {
"notStarted": false,
"privEscalation": false,
"torUsed": false,
"suspStruct": false,
"stealing": true,
"staticDetections": false,
"spam": false,
"serviceLauncher": false,
"rebooted": false,
"networkThreats": false,
"networkLoader": false,
"multiprocessing": true,
"memOverrun": false,
"lowAccess": false,
"exploitable": false,
"executableDropped": false,
"debugOutput": false,
"crashedTask": false,
"crashedApps": false,
"cpuOverrun": false,
"autostart": false,
"injects": false
},
"verdict": {
"threatLevelText": "Suspicious activity",
"threatLevel": 1,
"score": 97
}
},
"options": { "redacted": true },
"tags": [],
"creationText": "2020-05-21T18:19:50.603Z",
"creation": 1590085190603,
"duration": 60,
"sandbox": {
"plan": {
"name": "Tester"
},
"name": "ANY.RUN - Interactive Sandbox"
},
"reports": {
"graph": "https://content.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77/graph",
"HTML": "https://api.any.run/report/26357aef-3279-4c63-8216-c4e302756b77/summary/html",
"MISP": "https://api.any.run/report/26357aef-3279-4c63-8216-c4e302756b77/summary/misp",
"IOC": "https://api.any.run/report/26357aef-3279-4c63-8216-c4e302756b77/ioc/json"
},
"permanentUrl": "https://app.any.run/tasks/26357aef-3279-4c63-8216-c4e302756b77",
"uuid": "26357aef-3279-4c63-8216-c4e302756b77"
}
}
ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| data.mitre[].id/name | Object Value | Attack Pattern | data.analysis.creationText | T1011 - Some MITRE Attack Technique | The ID and name are formatted together |
| data.mitre[].phases[] | Attribute | Tactic | data.analysis.creationText | Exploitation | N/A |
| data.analysis.content.mainObject.url | Indicator Value | URL | data.analysis.creationText | N/A | If the object type is a URL |
| data.analysis.content.mainObject.filename | Indicator Value | Filename | data.analysis.creationText | N/A | If the object type is a File |
| data.analysis.content.mainObject.hashes.md5 | Indicator Value | MD5 | data.analysis.creationText | N/A | If the object type is a File |
| data.analysis.content.mainObject.hashes.sha1 | Indicator Value | SHA-1 | data.analysis.creationText | N/A | If the object type is a File |
| data.analysis.content.mainObject.hashes.sha256 | Indicator Value | SHA-256 | data.analysis.creationText | N/A | If the object type is a File |
| data.analysis.content.mainObject.url/filename | Attachment Title | Malware Analysis Report | data.analysis.creationText | ANY.RUN Analysis Report for [name] | The name here depends on the sample type. The name will also be stripped of any special characters |
| data.analysis.permanentUrl | Attribute | Analysis Link | data.analysis.creationText | N/A | N/A |
| data.analysis.scores.verdict.score | Attribute | ANY.RUN Score | data.analysis.creationText | 10 | N/A |
| data.analysis.scores.verdict.threatLevel | Attribute | Threat Level Code | data.analysis.creationText | N/A | This is a number |
| data.analysis.scores.verdict.threatLevelText | Attribute | Threat Level | data.analysis.creationText | High | This is the human-readable threat level |
| data.analysis.content.pcap.permanentUrl | Attribute | PCAP Link | data.analysis.creationText | N/A | N/A |
| data.environments.os.title | Attribute | Analysis Environment | data.analysis.creationText | Windows 10 64 bit (service pack 1) | N/A |
| data.analysis.tags | Tag | N/A | data.analysis.creationText | N/A | Only works for attachments at the moment |
IOC Endpoint
The IOC Endpoint feed returns IOCs related to a given analysis.
GET https://api.any.run/report/<Analysis ID>/ioc/json
Sample Response:
[
{
"category": "DNS requests",
"type": "domain",
"ioc": "qdnhomtiptkgjha.co.uk",
"reputation": 0
},
{
"category": "Connections",
"type": "ip",
"ioc": "212.71.250.4",
"reputation": 2
}
]
ThreatQuotient provides the following default mapping for this feed:
| Feed Data Path | ThreatQ Entity | ThreatQ Object Type or Attribute Key | Published Date | Examples | Notes |
|---|---|---|---|---|---|
| data[].ioc | Object Value | Indicator | Taken from parent report | N/A | Type is determined by other path |
| data[].type | Object Type | Indicator | N/A | N/A | Mapped to ThreatQ types |
| data[].category | Attribute | Category | Taken from parent report | DNS request | N/A |
| data[].reputation | Attribute | Reputation | Taken from parent report | Suspicious | N/A |
Average Feed Run
Object counts and Feed runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and Feed runtime may vary based on system resources and load.
Feed runs depend on the number of samples that your organization submits within 1 hour.
Known Issues / Limitations
- Malware samples and malware analysis reports are not related to each other. This is caused by a limitation with attachments endpoint.
- The
Analysis Endpoint(history) does not allow you to filter by date. As a result, you will need to filter by date within the filter section of the CDF. Another limitation is that the endpoint returns a single date field. This date reflects the date the sample was submitted. There is no date when the analysis was finished, and the analysis will only appear in theAnalysis Endpointwhen the analysis is finished. This may result in missing reports.
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| ANY.RUN CDF Guide v1.0.0 | 4.34 or Greater |