Current ThreatQ Version Filter
Macros
The following macros are used in most of the saved searches this App is configured with (available under Settings > Advanced Search > Search Macros).
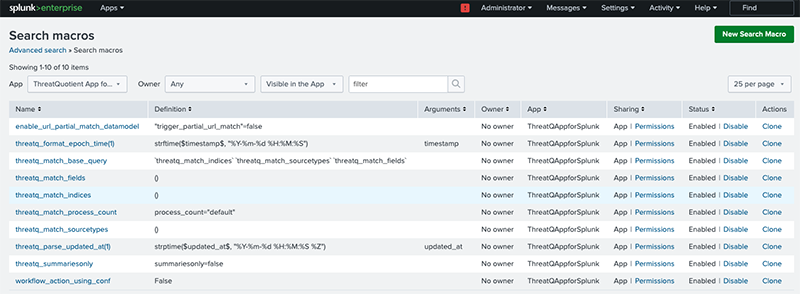
The description of some of these search macros is provided below.
| Saved Search Macro | Description |
|---|---|
| threatq_index | Configures the name of the Splunk index that all ThreatQ indicators are mapped to. |
| threatq_match_indices | Configures which Splunk indices are considered for matching. The users can apply more specific filters here. |
| threatq_match_sourcetypes | Configures which sourcetypes should be excluded from matching (the sourcetype threatq:indicators is automatically excluded). |
| threatq_match_process_count | Determines the number of cpu cores utilized for processing the saved searches that are responsible for finding evidence of sightings. |
| enable_url_partial_match_ datamodel |
Configures partial URL indicator matching for the Datamodel. The default setting is False.
This macro should be set to True if URL indicators are sent to Splunk with a scheme. http://, https:// |
| threatq_match_base_query | Allows you to alter the base query used for matching. Sub macros included are:
|
| threatq_match_fields | Allows you to match based on specific fields. |