Deployment Methods
The following describes and illustrates the most common deployments for the app within a Stand-Alone, Distributed, and Cloud Splunk environment.
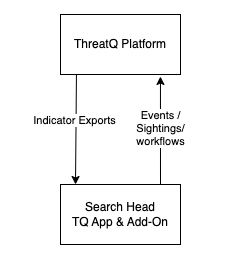
Stand-Alone Environment
Deploying in a Stand-Alone environment involves installing both the App and Add-On on the Search head.
Distributed Environment
Distributed environments with a cluster of search heads will need to have the Add-On and App both configured on the master node. The Splunk App deployer will then propagate the configuration settings to all nodes.
For heavy data, it is suggested to install the add-on on the separate Heavy Forwarder and the app on the Search head for optimal performance.
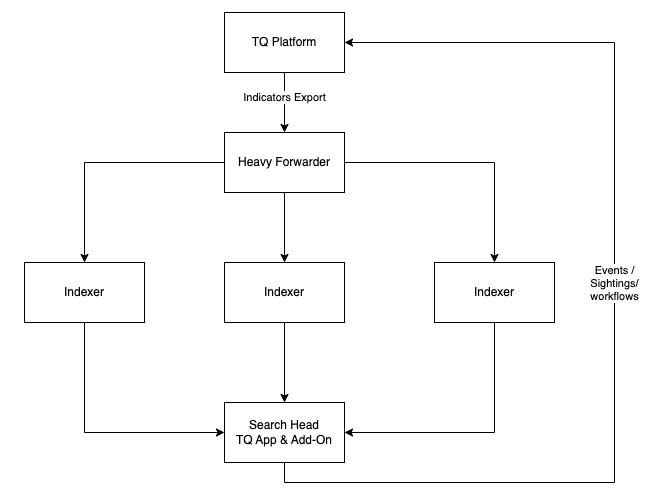
Option 1
This option for a distributed environment is to have both the App and Add-On installed on the Search Head.
In this scenario, the KVStore configuration option for the Add-On is not required.
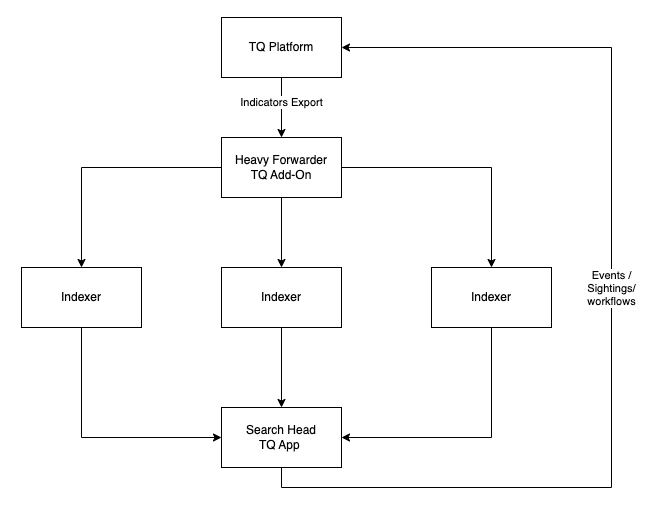
Option 2
This option for a distributed environment has the App installed on the Search Head while the Add-On is installed on the Heavy Forwarder. From this location, the Add-On extracts indicators from your ThreatQ appliance and forwards them to the configured Splunk index.
In this scenario, the KVStore configuration option for the Add-On is required and must point to the Search Head.
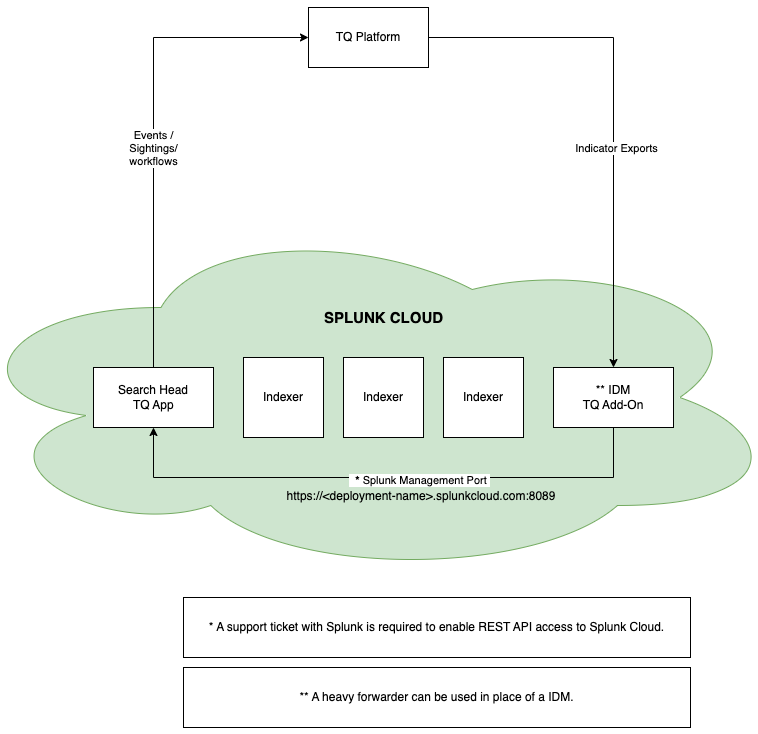
Cloud Environment
Deploying in a cloud environment requires that the App be installed on the Search Head. The Add-On must be installed on the IDM or Heavy Forwarder.
It is important to note that a support ticket must be created with Splunk to access the Splunk REST API, which will allow communication between the Search Head and IDM/Heavy Forwarder.