ThreatQ Intel Requirement Mapper Action
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 5.12.1 |
| ThreatQ TQO License Required | Yes |
| Support Tier | ThreatQ Supported |
Introduction
The ThreatQ Intel Requirement Mapper action is designed to automatically map your Intel Requirements to incoming threat intelligence. This saves your team time by allowing them to focus on the most critical threats and take action to mitigate threats/prevent future attacks.
The integration provides the following action:
- ThreatQ Intel Requirement Mapper - automatically maps your Intel Requirements to incoming threat intelligence.
The action is compatible with the following system object types:
- Adversary
- Campaign
- Event
- Incident
- Malware
- Report
The action returns the following enriched system objects:
- Adversary
- Campaign
- Event
- Incident
- Intel Requirement (custom object)
- Malware
- Report
This action is intended for use with ThreatQ TDR Orchestrator (TQO). An active TQO license is required for this feature.
Prerequisites
- An active ThreatQ TDR Orchestrator (TQO) license.
- A data collection containing at least one of the following object types:
- Adversary
- Campaign
- Event
- Incident
- Malware
- Report
- The Intel Requirement custom object installed on your ThreatQ instance.
Intel Requirement Custom Object
The integration requires the Intel Requirement custom object.
Use the steps provided to install the Intel Requirement custom object.
When installing the custom objects, be aware that any in-progress feed runs will be cancelled, and the API will be in maintenance mode.
- Download the integration bundle from the ThreatQ Marketplace.
- Unzip the bundle and locate the custom object files.
The custom object files will typically consist of a JSON definition file, install.sh script, and a images folder containing the svg icons.
- SSH into your ThreatQ instance.
- Set your install pathway environment variable. This command will retrieve the install pathway from your configuration file and set it as variable for use during this installation process.
INSTALL_CONF="/etc/threatq/platform/install.conf" if [ -f "$INSTALL_CONF" ]; then source "$INSTALL_CONF" fi MISC_DIR="${INSTALL_BASE_PATH:-/var/lib/threatq}/misc"
- Navigate to the tmp folder using the environment variable:
cd $MISC_DIR
- Upload the custom object files, including the images folder.
The directory structure should resemble the following:
- install.sh
- <custom_object_name>.json
- images (directory)
- <custom_object_name>.svg
- Run the following command:
kubectl exec -it deployment/api-schedule-run -n threatq -- sh /var/lib/threatq/misc/install.sh /var/lib/threatq/misc
The installation script will automatically put the application into maintenance mode, move the files to their required directories, install the custom object, update permissions, bring the application out of maintenance mode, and restart dynamo.
- Delete the install.sh, definition json file, and images directory from step 6 after the object has been installed as these files are no longer needed.
- Download the integration zip file from the ThreatQ Marketplace and unzip its contents.
- SSH into your ThreatQ instance.
- Navigate to tmp directory:
cd /tmp/
- Create a new directory:
mkdir intel_act
- Upload the intel_requirement.json and install.sh script into this new directory.
- Create a new directory called images within the intel_act directory.
mkdir images
- Upload the intel_requirement.svg.
- Navigate to the /tmp/intel_act.
The directory should resemble the following:
- tmp
- intel_act
- intel_requirement.json
- install.sh
- images
- intel_requirement.svg
- intel_act
- tmp
- Run the following command to ensure that you have the proper permissions to install the custom object:
chmod +x install.sh
- Run the following command:
sudo ./install.sh
You must be in the directory level that houses the install.sh and json files when running this command.
The installation script will automatically put the application into maintenance mode, move the files to their required directories, install the custom object, update permissions, bring the application out of maintenance mode, and restart dynamo.
- Remove the temporary directory, after the custom object has been installed, as the files are no longer needed:
rm -rf intel_act
Installation
The action requires the installation of Intel Requirement custom object. The custom object must be installed prior to installing the action. Attempting to install the action without the custom object will cause the install process to fail. See the Prerequisites chapter for more details.
Perform the following steps to install the integration:
The same steps can be used to upgrade the integration to a new version.
- Log into https://marketplace.threatq.com/.
- Locate and download the compressed action and extract its files.
- Install the required Intel Requirement custom object if you have not done so already.
- Navigate to the integrations management page on your ThreatQ instance.
- Click on the Add New Integration button.
- Upload the action zip file using one of the following methods:
- Drag and drop the zip file into the dialog box
- Select Click to Browse to locate the zip file on your local machine
ThreatQ will inform you if the action already exists on the platform and will require user confirmation before proceeding. ThreatQ will also inform you if the new version of the action contains changes to the user configuration. The new user configurations will overwrite the existing ones for the action and will require user confirmation before proceeding.
You will still need to configure the action.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Actions option from the Category dropdown (optional).
- Click on the action entry to open its details page.
- Enter the following parameters under the Configuration tab:
The configurations set on this page will be used as the default settings when inserting this action into a new workflow. Updating the configurations on this page will not update any instances of this action that have already been deployed to a workflow. In that scenario, you must update the action’s configurations within the workflow itself.
Parameter Description Use Intel 471's General Intelligence Requirements Enable this parameter for action to use Intel 471's General Intelligence Requirements (GIRs) to map to your incoming threat intelligence. Disable this parameter to only use your own custom mappings. This parameter is enabled by default. General Intel Requirement ID Whitelist (Recommended) Enter the line separated list of Intel 471 General Intel Requirement (GIRs) IDs to match on. ThreatQuotient strongly recommends against leaving this parameter blank as it will result in matching against all Intel Requirement keywords (~2200). This parameter is only accessible if the Use Intel 471's General Intelligence Requirements field is enabled.
Custom Intel Requirement Mapping Enter the line separated list of custom mappings to match on.Each mapping should be the keyword to match on, followed by a colon, and then the Intel Requirement ID and Value to map to, separated by a hyphen.
This user field supports up to 16k characters. If your mapping is larger than that, please split this workflow into multiple to avoid mapping issues.This mapping will also be used in addition to the Intel 471 General Intelligence Requirements when enabled.
Objects Per Run The max number of objects to send to this action per run.
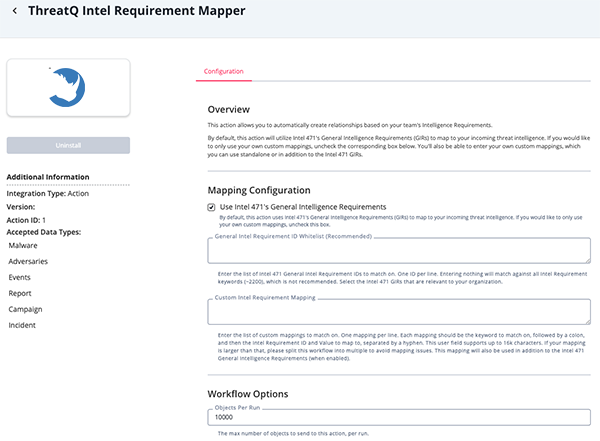
- Review any additional settings, make any changes if needed, and click on Save.
Actions
The following action is available:
| Action | Description | Object Type | Object Subtype |
|---|---|---|---|
| ThreatQ Intel Requirement Mapper | Automatically map your Intel Requirements to incoming threat intelligence | Malware, Adversary, Event, Campaign, Incident, Report | N/A |
ThreatQ Intel Requirement Mapper
The ingested data for the action depends on the selected objects and content.
If the Use Intel 471's General Intelligence Requirements parameter is enabled, the action searches for the keywords present in the list in all the descriptions and attributes of a ThreatQ object. The found keywords are then mapped to the corresponding Intel 471's General Intelligence Requirements and are related to the object. See full list of GIRs in the Intel 471's General Intelligence Requirements section of this guide.
All the list entries follow the pattern: <Text>: <ID> - <Value>.
Examples include:
# <Text>: <ID> - <Value>
malware: 1 - Malware
proxy malware: 1.1.13 - Proxy malware
fraud: 4 - Fraud, Identity Theft and Unauthorized AccessA subset of Intel 471's General Intelligence Requirements can be added to the user configuration General Intel Requirement ID Whitelist (Recommended). Use this to select the Intel 471 GIRs that are relevant to your organization.
Examples include:
1
4.1.6
2.1.1.1A custom mapping can be specified in user configuration Custom Intel Requirement Mapping. One mapping per line. Each mapping should be the keyword to match on, followed by a colon, and then the Intel Requirement ID and Value to map to, separated by a hyphen. This user field supports up to 16k characters. If your mapping is larger than that, please split this workflow into multiple to avoid mapping issues. This mapping will also be used in addition to the Intel 471 General Intelligence Requirements (when enabled).
Examples include:
elf malware: 1 - Malware
nmap: 1.3.11.2 - Network scannersIntel 471 General Intelligence Requirements (GIRs)
malware: 1 - Malware
malicious software: 1 - Malware
virus: 1 - Malware
trojan: 1 - Malware
worm: 1 - Malware
spyware: 1 - Malware
adware: 1 - Malware
infected software: 1 - Malware
malware variant: 1.1 - Malware variants
types of malware: 1.1 - Malware variants
malware strains: 1.1 - Malware variants
malicious variants: 1.1 - Malware variants
virus types: 1.1 - Malware variants
trojan variants: 1.1 - Malware variants
worm variants: 1.1 - Malware variants
ransomware: 1.1.1 - Ransomware malware
ransom malware: 1.1.1 - Ransomware malware
encrypting ransomware: 1.1.1 - Ransomware malware
data hostage: 1.1.1 - Ransomware malware
ransom payment: 1.1.1 - Ransomware malware
file encryption malware: 1.1.1 - Ransomware malware
atm malware: 1.1.10 - ATM malware
atm trojan: 1.1.10 - ATM malware
cash machine malware: 1.1.10 - ATM malware
atm infection: 1.1.10 - ATM malware
atm skimming: 1.1.10 - ATM malware
iot malware: 1.1.11 - Internet of Things (IoT) malware
internet of things malware: 1.1.11 - Internet of Things (IoT) malware
smart device malware: 1.1.11 - Internet of Things (IoT) malware
connected device malware: 1.1.11 - Internet of Things (IoT) malware
iot attack: 1.1.11 - Internet of Things (IoT) malware
iot infection: 1.1.11 - Internet of Things (IoT) malware
dos malware: 1.1.12 - Denial of service (DoS) malware
dos trojan: 1.1.12 - Denial of service (DoS) malware
network flooding: 1.1.12 - Denial of service (DoS) malware
dos tool: 1.1.12 - Denial of service (DoS) malware
proxy malware: 1.1.13 - Proxy malware
proxy trojan: 1.1.13 - Proxy malware
proxy server attack: 1.1.13 - Proxy malware
proxy infection: 1.1.13 - Proxy malware
network proxy malware: 1.1.13 - Proxy malware
destructive malware: 1.1.14 - Destructive malware
data destruction malware: 1.1.14 - Destructive malware
wiper malware: 1.1.14 - Destructive malware
malware with destruction: 1.1.14 - Destructive malware
data wiping malware: 1.1.14 - Destructive malware
cryptomining malware: 1.1.15 - Cryptomining malware
crypto miner malware: 1.1.15 - Cryptomining malware
mining trojan: 1.1.15 - Cryptomining malware
cryptojacking: 1.1.15 - Cryptomining malware
unauthorized mining: 1.1.15 - Cryptomining malware
cryptomining attack: 1.1.15 - Cryptomining malware
clipper malware: 1.1.16 - Clipper malware
clipper trojan: 1.1.16 - Clipper malware
clipboard malware: 1.1.16 - Clipper malware
clipper virus: 1.1.16 - Clipper malware
clipboard hijacking: 1.1.16 - Clipper malware
data exfiltration malware: 1.1.17 - Drainer malware
drainer malware: 1.1.17 - Drainer malware
data drainer: 1.1.17 - Drainer malware
drain malware: 1.1.17 - Drainer malware
drainer trojan: 1.1.17 - Drainer malware
mobile malware: 1.1.2 - Mobile malware
mobile virus: 1.1.2 - Mobile malware
mobile trojan: 1.1.2 - Mobile malware
smartphone malware: 1.1.2 - Mobile malware
mobile device infection: 1.1.2 - Mobile malware
mobile app malware: 1.1.2 - Mobile malware
rat malware: 1.1.3 - Remote access trojan (RAT) malware
remote access trojan: 1.1.3 - Remote access trojan (RAT) malware
remote control malware: 1.1.3 - Remote access trojan (RAT) malware
rat tool: 1.1.3 - Remote access trojan (RAT) malware
remote administration trojan: 1.1.3 - Remote access trojan (RAT) malware
banking malware: 1.1.4 - Banking trojan malware
banking trojan: 1.1.4 - Banking trojan malware
financial trojan: 1.1.4 - Banking trojan malware
banking virus: 1.1.4 - Banking trojan malware
online banking malware: 1.1.4 - Banking trojan malware
financial data theft malware: 1.1.4 - Banking trojan malware
information stealer: 1.1.5 - Information-stealer malware
data theft malware: 1.1.5 - Information-stealer malware
info-stealing malware: 1.1.5 - Information-stealer malware
credential stealer: 1.1.5 - Information-stealer malware
password stealer: 1.1.5 - Information-stealer malware
loader malware: 1.1.6 - Loader malware
malware loader: 1.1.6 - Loader malware
trojan downloader: 1.1.6 - Loader malware
payload loader: 1.1.6 - Loader malware
malware dropper: 1.1.6 - Loader malware
infection loader: 1.1.6 - Loader malware
botnet malware: 1.1.7 - Botnet malware
bot malware: 1.1.7 - Botnet malware
botnet infection: 1.1.7 - Botnet malware
zombie network: 1.1.7 - Botnet malware
bot army: 1.1.7 - Botnet malware
botnet attack: 1.1.7 - Botnet malware
worm malware: 1.1.8 - Worm malware
network worm: 1.1.8 - Worm malware
self-replicating malware: 1.1.8 - Worm malware
worm infection: 1.1.8 - Worm malware
worm attack: 1.1.8 - Worm malware
network spreading malware: 1.1.8 - Worm malware
pos malware: 1.1.9 - Point-of-sale (PoS) malware
point-of-sale malware: 1.1.9 - Point-of-sale (PoS) malware
pos infection: 1.1.9 - Point-of-sale (PoS) malware
payment terminal malware: 1.1.9 - Point-of-sale (PoS) malware
retail malware: 1.1.9 - Point-of-sale (PoS) malware
maas: 1.2 - Malware-as-a-service (MaaS)
malware-as-a-service: 1.2 - Malware-as-a-service (MaaS)
rental malware: 1.2 - Malware-as-a-service (MaaS)
malware service: 1.2 - Malware-as-a-service (MaaS)
maas platform: 1.2 - Malware-as-a-service (MaaS)
malware renting: 1.2 - Malware-as-a-service (MaaS)
multifunctional maas: 1.2.1 - Multifunctional malware-as-a-service (MaaS)
versatile maas: 1.2.1 - Multifunctional malware-as-a-service (MaaS)
multi-featured maas: 1.2.1 - Multifunctional malware-as-a-service (MaaS)
all-in-one malware service: 1.2.1 - Multifunctional malware-as-a-service (MaaS)
multi-capability maas: 1.2.1 - Multifunctional malware-as-a-service (MaaS)
raas: 1.2.2 - Ransomware-as-a-service (RaaS)
ransomware-as-a-service: 1.2.2 - Ransomware-as-a-service (RaaS)
ransomware rental: 1.2.2 - Ransomware-as-a-service (RaaS)
ransomware service: 1.2.2 - Ransomware-as-a-service (RaaS)
ransomware platform: 1.2.2 - Ransomware-as-a-service (RaaS)
ransomware leasing: 1.2.2 - Ransomware-as-a-service (RaaS)
malware development: 1.3 - Malware development, support and delivery
malware support: 1.3 - Malware development, support and delivery
malware delivery: 1.3 - Malware development, support and delivery
malware creation: 1.3 - Malware development, support and delivery
malware distribution: 1.3 - Malware development, support and delivery
malware maintenance: 1.3 - Malware development, support and delivery
malware install: 1.3.1 - Malware installs
malware installation: 1.3.1 - Malware installs
malware setup: 1.3.1 - Malware installs
infectious installation: 1.3.1 - Malware installs
trojan install: 1.3.1 - Malware installs
exploit kit: 1.3.10 - Exploit kits
exploit pack: 1.3.10 - Exploit kits
vulnerability kit: 1.3.10 - Exploit kits
exploit toolkit: 1.3.10 - Exploit kits
malware exploit kit: 1.3.10 - Exploit kits
illicit tool use: 1.3.11 - Illicit use of legitimate tools and software
legitimate tool misuse: 1.3.11 - Illicit use of legitimate tools and software
malicious tool use: 1.3.11 - Illicit use of legitimate tools and software
software abuse: 1.3.11 - Illicit use of legitimate tools and software
legitimate software exploitation: 1.3.11 - Illicit use of legitimate tools and software
post-exploitation framework: 1.3.11.1 - Post-exploitation frameworks
post-exploit tool: 1.3.11.1 - Post-exploitation frameworks
post-compromise framework: 1.3.11.1 - Post-exploitation frameworks
post-hack toolkit: 1.3.11.1 - Post-exploitation frameworks
post-intrusion framework: 1.3.11.1 - Post-exploitation frameworks
network scanner: 1.3.11.2 - Network scanners
port scanner: 1.3.11.2 - Network scanners
vulnerability scanner: 1.3.11.2 - Network scanners
network probing: 1.3.11.2 - Network scanners
scanning tool: 1.3.11.2 - Network scanners
credential tool: 1.3.11.3 - Authentication and credential tools
authentication tool: 1.3.11.3 - Authentication and credential tools
password tool: 1.3.11.3 - Authentication and credential tools
credential hacking tool: 1.3.11.3 - Authentication and credential tools
authentication bypass tool: 1.3.11.3 - Authentication and credential tools
active directory tool: 1.3.11.4 - Active Directory tools
ad tool: 1.3.11.4 - Active Directory tools
directory service tool: 1.3.11.4 - Active Directory tools
active directory exploitation: 1.3.11.4 - Active Directory tools
ad hacking tool: 1.3.11.4 - Active Directory tools
remote access tool: 1.3.11.5 - Remote access tools
rat: 1.3.11.5 - Remote access tools
remote control tool: 1.3.11.5 - Remote access tools
remote administration tool: 1.3.11.5 - Remote access tools
remote hacking tool: 1.3.11.5 - Remote access tools
seo: 1.3.11.6 - Search engine optimization (SEO)
search engine optimization: 1.3.11.6 - Search engine optimization (SEO)
seo abuse: 1.3.11.6 - Search engine optimization (SEO)
seo manipulation: 1.3.11.6 - Search engine optimization (SEO)
search ranking manipulation: 1.3.11.6 - Search engine optimization (SEO)
anti-detect tool: 1.3.11.7 - Anti-detect tools
detection evasion tool: 1.3.11.7 - Anti-detect tools
stealth tool: 1.3.11.7 - Anti-detect tools
obfuscation tool: 1.3.11.7 - Anti-detect tools
anti-detection software: 1.3.11.7 - Anti-detect tools
malvertising: 1.3.2 - Malvertising
malicious ads: 1.3.2 - Malvertising
malicious advertising: 1.3.2 - Malvertising
infected ads: 1.3.2 - Malvertising
ad malware: 1.3.2 - Malvertising
advertisement malware: 1.3.2 - Malvertising
malicious code: 1.3.3 - Malware source code
malware source code: 1.3.3 - Malware source code
malware code: 1.3.3 - Malware source code
source code leak: 1.3.3 - Malware source code
malware programming: 1.3.3 - Malware source code
malicious script: 1.3.3 - Malware source code
web-inject: 1.3.4 - Web-injects
browser inject: 1.3.4 - Web-injects
web injection: 1.3.4 - Web-injects
html inject: 1.3.4 - Web-injects
malicious inject: 1.3.4 - Web-injects
ats: 1.3.4.1 - Automatic transfer systems (ATSs)
automatic transfer system: 1.3.4.1 - Automatic transfer systems (ATSs)
bank transfer malware: 1.3.4.1 - Automatic transfer systems (ATSs)
automatic transaction malware: 1.3.4.1 - Automatic transfer systems (ATSs)
ats malware: 1.3.4.1 - Automatic transfer systems (ATSs)
malware crypting: 1.3.5 - Malware crypting
encryption malware: 1.3.5 - Malware crypting
cryptor: 1.3.5 - Malware crypting
malware obfuscation: 1.3.5 - Malware crypting
encrypted malware: 1.3.5 - Malware crypting
counter antivirus: 1.3.6 - Counter antivirus (CAV)
antivirus evasion: 1.3.6 - Counter antivirus (CAV)
av evasion: 1.3.6 - Counter antivirus (CAV)
cav tool: 1.3.6 - Counter antivirus (CAV)
antivirus bypass: 1.3.6 - Counter antivirus (CAV)
rogue certificate: 1.3.7 - Rogue certificates
fake certificate: 1.3.7 - Rogue certificates
illicit certificate: 1.3.7 - Rogue certificates
malicious certificate: 1.3.7 - Rogue certificates
certificate forgery: 1.3.7 - Rogue certificates
rogue code-signing: 1.3.7.1 - Rogue code-signing certificates
fake code-signing: 1.3.7.1 - Rogue code-signing certificates
illicit code-signing: 1.3.7.1 - Rogue code-signing certificates
malicious code-signing: 1.3.7.1 - Rogue code-signing certificates
code-signing forgery: 1.3.7.1 - Rogue code-signing certificates
rogue web certificate: 1.3.7.2 - Rogue web certificates
fake web certificate: 1.3.7.2 - Rogue web certificates
illicit web certificate: 1.3.7.2 - Rogue web certificates
malicious web certificate: 1.3.7.2 - Rogue web certificates
web certificate forgery: 1.3.7.2 - Rogue web certificates
malware spamming: 1.3.8 - Malware spamming
spam malware: 1.3.8 - Malware spamming
malicious spam: 1.3.8 - Malware spamming
email malware: 1.3.8 - Malware spamming
spam infection: 1.3.8 - Malware spamming
spam trojan: 1.3.8 - Malware spamming
traffic redistribution: 1.3.9 - Traffic redistribution system
traffic rerouting: 1.3.9 - Traffic redistribution system
malicious traffic: 1.3.9 - Traffic redistribution system
traffic hijacking: 1.3.9 - Traffic redistribution system
network traffic manipulation: 1.3.9 - Traffic redistribution system
exploit: 2 - Vulnerabilities and Exploits
security flaw: 2 - Vulnerabilities and Exploits
system weakness: 2 - Vulnerabilities and Exploits
exploit code: 2 - Vulnerabilities and Exploits
vulnerability disclosure: 2 - Vulnerabilities and Exploits
vulnerability: 2.1 - Vulnerabilities
security hole: 2.1 - Vulnerabilities
software flaw: 2.1 - Vulnerabilities
exploit risk: 2.1 - Vulnerabilities
security gap: 2.1 - Vulnerabilities
system vulnerability: 2.1.1 - Operating system (OS) vulnerabilities
os vulnerability: 2.1.1 - Operating system (OS) vulnerabilities
operating system flaw: 2.1.1 - Operating system (OS) vulnerabilities
os exploit: 2.1.1 - Operating system (OS) vulnerabilities
security patch os: 2.1.1 - Operating system (OS) vulnerabilities
desktop os vulnerability: 2.1.1.1 - Desktop or server OS vulnerabilities
server os vulnerability: 2.1.1.1 - Desktop or server OS vulnerabilities
pc os flaw: 2.1.1.1 - Desktop or server OS vulnerabilities
system os security: 2.1.1.1 - Desktop or server OS vulnerabilities
mobile os vulnerability: 2.1.1.2 - Mobile OS vulnerabilities
smartphone os flaw: 2.1.1.2 - Mobile OS vulnerabilities
mobile exploit: 2.1.1.2 - Mobile OS vulnerabilities
mobile system vulnerability: 2.1.1.2 - Mobile OS vulnerabilities
mobile os security: 2.1.1.2 - Mobile OS vulnerabilities
health care vulnerability: 2.1.10 - Health care systems-related vulnerabilities (deprecated)
healthcare vulnerability: 2.1.10 - Health care systems-related vulnerabilities (deprecated)
healthcare system flaw: 2.1.10 - Health care systems-related vulnerabilities (deprecated)
medical system vulnerability: 2.1.10 - Health care systems-related vulnerabilities (deprecated)
healthcare exploit: 2.1.10 - Health care systems-related vulnerabilities (deprecated)
medical data security: 2.1.10 - Health care systems-related vulnerabilities (deprecated)
cryptocurrency vulnerability: 2.1.11 - Cryptocurrency and exchanges vulnerabilities
crypto exchange flaw: 2.1.11 - Cryptocurrency and exchanges vulnerabilities
crypto security hole: 2.1.11 - Cryptocurrency and exchanges vulnerabilities
blockchain vulnerability: 2.1.11 - Cryptocurrency and exchanges vulnerabilities
crypto exploit: 2.1.11 - Cryptocurrency and exchanges vulnerabilities
software vulnerability: 2.1.2 - Software and web application vulnerabilities
web app vulnerability: 2.1.2 - Software and web application vulnerabilities
application flaw: 2.1.2 - Software and web application vulnerabilities
software exploit: 2.1.2 - Software and web application vulnerabilities
web application security: 2.1.2 - Software and web application vulnerabilities
browser exploit: 2.1.2.1 - Web browser vulnerabilities
browser vulnerability: 2.1.2.1 - Web browser vulnerabilities
web browser flaw: 2.1.2.1 - Web browser vulnerabilities
browser security hole: 2.1.2.1 - Web browser vulnerabilities
browser patch: 2.1.2.1 - Web browser vulnerabilities
office software vulnerability: 2.1.2.2 - Office or productivity software vulnerabilities
productivity software flaw: 2.1.2.2 - Office or productivity software vulnerabilities
office exploit: 2.1.2.2 - Office or productivity software vulnerabilities
productivity software security: 2.1.2.2 - Office or productivity software vulnerabilities
office patch: 2.1.2.2 - Office or productivity software vulnerabilities
open source vulnerability: 2.1.2.3 - Open source software library vulnerabilities
library vulnerability: 2.1.2.3 - Open source software library vulnerabilities
open source flaw: 2.1.2.3 - Open source software library vulnerabilities
library exploit: 2.1.2.3 - Open source software library vulnerabilities
open source security: 2.1.2.3 - Open source software library vulnerabilities
protocol vulnerability: 2.1.3 - Protocol vulnerabilities
network protocol flaw: 2.1.3 - Protocol vulnerabilities
protocol exploit: 2.1.3 - Protocol vulnerabilities
protocol security hole: 2.1.3 - Protocol vulnerabilities
protocol patch: 2.1.3 - Protocol vulnerabilities
server exploit: 2.1.4 - Server platform vulnerabilities
server platform vulnerability: 2.1.4 - Server platform vulnerabilities
server flaw: 2.1.4 - Server platform vulnerabilities
server security: 2.1.4 - Server platform vulnerabilities
platform patch: 2.1.4 - Server platform vulnerabilities
database vulnerability: 2.1.4.1 - Database server vulnerabilities
db server flaw: 2.1.4.1 - Database server vulnerabilities
database exploit: 2.1.4.1 - Database server vulnerabilities
database security hole: 2.1.4.1 - Database server vulnerabilities
db patch: 2.1.4.1 - Database server vulnerabilities
web server vulnerability: 2.1.4.2 - Web server vulnerabilities
web server flaw: 2.1.4.2 - Web server vulnerabilities
web server exploit: 2.1.4.2 - Web server vulnerabilities
web server security: 2.1.4.2 - Web server vulnerabilities
web server patch: 2.1.4.2 - Web server vulnerabilities
email server vulnerability: 2.1.4.3 - Email server vulnerabilities
email server flaw: 2.1.4.3 - Email server vulnerabilities
email exploit: 2.1.4.3 - Email server vulnerabilities
email server security: 2.1.4.3 - Email server vulnerabilities
email server patch: 2.1.4.3 - Email server vulnerabilities
cms vulnerability: 2.1.4.4 - Content management server vulnerabilities
content management flaw: 2.1.4.4 - Content management server vulnerabilities
cms exploit: 2.1.4.4 - Content management server vulnerabilities
content management security: 2.1.4.4 - Content management server vulnerabilities
cms patch: 2.1.4.4 - Content management server vulnerabilities
app server vulnerability: 2.1.4.5 - Application server vulnerabilities
application server flaw: 2.1.4.5 - Application server vulnerabilities
app server exploit: 2.1.4.5 - Application server vulnerabilities
application server security: 2.1.4.5 - Application server vulnerabilities
app server patch: 2.1.4.5 - Application server vulnerabilities
identity server vulnerability: 2.1.4.6 - Identity management or authentication server vulnerabilities
authentication server flaw: 2.1.4.6 - Identity management or authentication server vulnerabilities
identity management exploit: 2.1.4.6 - Identity management or authentication server vulnerabilities
authentication security hole: 2.1.4.6 - Identity management or authentication server vulnerabilities
identity server patch: 2.1.4.6 - Identity management or authentication server vulnerabilities
network appliance vulnerability: 2.1.5 - Network appliance or endpoint vulnerabilities
endpoint vulnerability: 2.1.5 - Network appliance or endpoint vulnerabilities
network device flaw: 2.1.5 - Network appliance or endpoint vulnerabilities
endpoint exploit: 2.1.5 - Network appliance or endpoint vulnerabilities
network security patch: 2.1.5 - Network appliance or endpoint vulnerabilities
cloud vulnerability: 2.1.6 - Cloud computing or storage vulnerabilities
cloud security flaw: 2.1.6 - Cloud computing or storage vulnerabilities
cloud exploit: 2.1.6 - Cloud computing or storage vulnerabilities
cloud storage vulnerability: 2.1.6 - Cloud computing or storage vulnerabilities
cloud patch: 2.1.6 - Cloud computing or storage vulnerabilities
hardware vulnerability: 2.1.7 - Hardware vulnerabilities
device security flaw: 2.1.7 - Hardware vulnerabilities
hardware exploit: 2.1.7 - Hardware vulnerabilities
hardware security: 2.1.7 - Hardware vulnerabilities
device patch: 2.1.7 - Hardware vulnerabilities
ics vulnerability: 2.1.8 - Industrial control systems (ICS) or supervisory control and data acquisition (SCADA) vulnerabilities (deprecated)
scada vulnerability: 2.1.8 - Industrial control systems (ICS) or supervisory control and data acquisition (SCADA) vulnerabilities (deprecated)
industrial control flaw: 2.1.8 - Industrial control systems (ICS) or supervisory controland data acquisition (SCADA) vulnerabilities (deprecated)
scada exploit: 2.1.8 - Industrial control systems (ICS) or supervisory control and data acquisition (SCADA) vulnerabilities (deprecated)
ics security: 2.1.8 - Industrial control systems (ICS) or supervisory control and data acquisition (SCADA) vulnerabilities (deprecated)
iot vulnerability: 2.1.9 - IoT-related vulnerabilities
internet of things flaw: 2.1.9 - IoT-related vulnerabilities
iot exploit: 2.1.9 - IoT-related vulnerabilities
smart device vulnerability: 2.1.9 - IoT-related vulnerabilities
iot security: 2.1.9 - IoT-related vulnerabilities
exploit development: 2.2 - Exploit development
exploit creation: 2.2 - Exploit development
vulnerability exploitation: 2.2 - Exploit development
exploit coding: 2.2 - Exploit development
exploit engineering: 2.2 - Exploit development
poc exploit: 2.2.1 - Proof-of-concept (PoC) exploit code
proof-of-concept exploit: 2.2.1 - Proof-of-concept (PoC) exploit code
poc code: 2.2.1 - Proof-of-concept (PoC) exploit code
exploit example: 2.2.1 - Proof-of-concept (PoC) exploit code
vulnerability poc: 2.2.1 - Proof-of-concept (PoC) exploit code
malicious infrastructure: 3 - Malicious Infrastructure
cyber infrastructure: 3 - Malicious Infrastructure
iaas: 3.1 - Infrastructure-as-a-service (IaaS)
infrastructure-as-a-service: 3.1 - Infrastructure-as-a-service (IaaS)
iaas abuse: 3.1 - Infrastructure-as-a-service (IaaS)
cloud infrastructure: 3.1 - Infrastructure-as-a-service (IaaS)
iaas exploit: 3.1 - Infrastructure-as-a-service (IaaS)
bulletproof hosting: 3.1.1 - Bulletproof hosting (BPH) services
bph service: 3.1.1 - Bulletproof hosting (BPH) services
bph provider: 3.1.1 - Bulletproof hosting (BPH) services
secure hosting: 3.1.1 - Bulletproof hosting (BPH) services
bph abuse: 3.1.1 - Bulletproof hosting (BPH) services
malicious proxy: 3.1.2 - Proxy services
proxy service: 3.1.2 - Proxy services
proxy provider: 3.1.2 - Proxy services
proxy abuse: 3.1.2 - Proxy services
proxy exploit: 3.1.2 - Proxy services
domain registration: 3.1.3 - Domain registration services
domain service: 3.1.3 - Domain registration services
domain abuse: 3.1.3 - Domain registration services
malicious domain: 3.1.3 - Domain registration services
domain exploit: 3.1.3 - Domain registration services
botnet service: 3.1.4 - Botnet services
botnet provider: 3.1.4 - Botnet services
botnet operation: 3.1.4 - Botnet services
botnet management: 3.1.4 - Botnet services
botnet abuse: 3.1.4 - Botnet services
infrastructure abuse: 3.2 - Legitimate infrastructure repurposed for malicious activity
legitimate infrastructure: 3.2 - Legitimate infrastructure repurposed for malicious activity
infrastructure repurpose: 3.2 - Legitimate infrastructure repurposed for malicious activity
infrastructure misuse: 3.2 - Legitimate infrastructure repurposed for malicious activity
malicious repurposing: 3.2 - Legitimate infrastructure repurposed for malicious activity
criminal infrastructure: 3.3 - Dedicated criminal infrastructure
malware hosting: 3.3 - Dedicated criminal infrastructure
dedicated infrastructure: 3.3 - Dedicated criminal infrastructure
cybercriminal infrastructure: 3.3 - Dedicated criminal infrastructure
criminal network: 3.3 - Dedicated criminal infrastructure
fraud: 4 - Fraud, Identity Theft and Unauthorized Access
identity theft: 4 - Fraud, Identity Theft and Unauthorized Access
unauthorized access: 4 - Fraud, Identity Theft and Unauthorized Access
financial fraud: 4 - Fraud, Identity Theft and Unauthorized Access
identity fraud: 4 - Fraud, Identity Theft and Unauthorized Access
fraud supply chain: 4.1 - Fraud supply chain monetization
fraud monetization: 4.1 - Fraud supply chain monetization
fraud profit: 4.1 - Fraud supply chain monetization
criminal supply chain: 4.1 - Fraud supply chain monetization
fraud operation: 4.1 - Fraud supply chain monetization
cashout: 4.1.1 - Cashout
cash-out: 4.1.1 - Cashout
cash withdrawal: 4.1.1 - Cashout
fraudulent cashout: 4.1.1 - Cashout
document fraud: 4.1.10 - Document fraud
fake documents: 4.1.10 - Document fraud
document forgery: 4.1.10 - Document fraud
document falsification: 4.1.10 - Document fraud
fraudulent documents: 4.1.10 - Document fraud
insurance fraud: 4.1.11 - Insurance fraud (deprecated)
insurance scam: 4.1.11 - Insurance fraud (deprecated)
fraudulent insurance claim: 4.1.11 - Insurance fraud (deprecated)
insurance deception: 4.1.11 - Insurance fraud (deprecated)
insurance falsification: 4.1.11 - Insurance fraud (deprecated)
registration fraud: 4.1.12 - Registration fraud
fake registration: 4.1.12 - Registration fraud
registration scam: 4.1.12 - Registration fraud
registration deception: 4.1.12 - Registration fraud
fraudulent registration: 4.1.12 - Registration fraud
reshipping fraud: 4.1.13 - Reshipping fraud
reshipment scam: 4.1.13 - Reshipping fraud
package reshipping: 4.1.13 - Reshipping fraud
reshipping scheme: 4.1.13 - Reshipping fraud
fraudulent reshipping: 4.1.13 - Reshipping fraud
payroll fraud: 4.1.14 - Payroll fraud scam
payroll scam: 4.1.14 - Payroll fraud scam
payroll deception: 4.1.14 - Payroll fraud scam
fraudulent payroll: 4.1.14 - Payroll fraud scam
payroll scheme: 4.1.14 - Payroll fraud scam
refund fraud: 4.1.15 - Refund fraud
refund scam: 4.1.15 - Refund fraud
fraudulent refund: 4.1.15 - Refund fraud
refund deception: 4.1.15 - Refund fraud
refund scheme: 4.1.15 - Refund fraud
money laundering: 4.1.2 - Money laundering
laundered funds: 4.1.2 - Money laundering
illegal money transfer: 4.1.2 - Money laundering
financial laundering: 4.1.2 - Money laundering
laundering operation: 4.1.2 - Money laundering
crypto exchange fraud: 4.1.2.1 - Cryptocurrency exchange fraud
cryptocurrency fraud: 4.1.2.1 - Cryptocurrency exchange fraud
crypto fraud: 4.1.2.1 - Cryptocurrency exchange fraud
exchange scam: 4.1.2.1 - Cryptocurrency exchange fraud
crypto laundering: 4.1.2.1 - Cryptocurrency exchange fraud
crypto exchange scam: 4.1.2.1 - Cryptocurrency exchange fraud
mules: 4.1.3 - Mules and networks
money mule: 4.1.3 - Mules and networks
mule network: 4.1.3 - Mules and networks
fraud mule: 4.1.3 - Mules and networks
money mule operation: 4.1.3 - Mules and networks
drop account: 4.1.4 - Drop accounts and fund transfers
fund transfer fraud: 4.1.4 - Drop accounts and fund transfers
fraudulent account: 4.1.4 - Drop accounts and fund transfers
drop account scam: 4.1.4 - Drop accounts and fund transfers
illegal fund transfer: 4.1.4 - Drop accounts and fund transfers
prepaid card fraud: 4.1.5 - Prepaid or gift card fraud
gift card fraud: 4.1.5 - Prepaid or gift card fraud
prepaid scam: 4.1.5 - Prepaid or gift card fraud
gift card scam: 4.1.5 - Prepaid or gift card fraud
fraudulent prepaid card: 4.1.5 - Prepaid or gift card fraud
travel fraud: 4.1.6 - Travel fraud
travel scam: 4.1.6 - Travel fraud
fake travel booking: 4.1.6 - Travel fraud
travel deception: 4.1.6 - Travel fraud
fraudulent travel: 4.1.6 - Travel fraud
hospitality fraud: 4.1.7 - Hospitality fraud
hotel scam: 4.1.7 - Hospitality fraud
hospitality scam: 4.1.7 - Hospitality fraud
hospitality deception: 4.1.7 - Hospitality fraud
fraudulent hospitality: 4.1.7 - Hospitality fraud
tax fraud: 4.1.8 - Tax fraud and scams
tax scam: 4.1.8 - Tax fraud and scams
tax evasion: 4.1.8 - Tax fraud and scams
tax deception: 4.1.8 - Tax fraud and scams
fraudulent tax: 4.1.8 - Tax fraud and scams
bec: 4.1.9 - Business email compromise (BEC)
business email compromise: 4.1.9 - Business email compromise (BEC)
email fraud: 4.1.9 - Business email compromise (BEC)
corporate email scam: 4.1.9 - Business email compromise (BEC)
email deception: 4.1.9 - Business email compromise (BEC)
access breach: 4.2 - Compromised data or access
compromised data: 4.2 - Compromised data or access
data compromise: 4.2 - Compromised data or access
payment card fraud: 4.2.1 - Payment card fraud
credit card fraud: 4.2.1 - Payment card fraud
debit card fraud: 4.2.1 - Payment card fraud
card skimming: 4.2.1 - Payment card fraud
card scam: 4.2.1 - Payment card fraud
online card skimming: 4.2.1.1 - Online payment card skimming
payment card skimming: 4.2.1.1 - Online payment card skimming
web skimming: 4.2.1.1 - Online payment card skimming
card data theft: 4.2.1.1 - Online payment card skimming
online skimming: 4.2.1.1 - Online payment card skimming
compromised credentials: 4.2.2 - Compromised credentials
stolen credentials: 4.2.2 - Compromised credentials
credential breach: 4.2.2 - Compromised credentials
credential compromise: 4.2.2 - Compromised credentials
credential list: 4.2.2.1 - Credential combination list(s)
combination list: 4.2.2.1 - Credential combination list(s)
stolen credential list: 4.2.2.1 - Credential combination list(s)
password list: 4.2.2.1 - Credential combination list(s)
username and password list: 4.2.2.1 - Credential combination list(s)
compromised pii: 4.2.3 - Compromised personally identifiable information (PII)
pii breach: 4.2.3 - Compromised personally identifiable information (PII)
personal data breach: 4.2.3 - Compromised personally identifiable information (PII)
stolen pii: 4.2.3 - Compromised personally identifiable information (PII)
pii compromise: 4.2.3 - Compromised personally identifiable information (PII)
compromised phi: 4.2.3.1 - Compromised protected health information (PHI)
phi breach: 4.2.3.1 - Compromised protected health information (PHI)
health data breach: 4.2.3.1 - Compromised protected health information (PHI)
stolen phi: 4.2.3.1 - Compromised protected health information (PHI)
phi compromise: 4.2.3.1 - Compromised protected health information (PHI)
compromised ip: 4.2.4 - Compromised intellectual property (IP)
intellectual property breach: 4.2.4 - Compromised intellectual property (IP)
ip theft: 4.2.4 - Compromised intellectual property (IP)
stolen ip: 4.2.4 - Compromised intellectual property (IP)
ip compromise: 4.2.4 - Compromised intellectual property (IP)
system compromise: 4.2.5 - Compromised network or system access
network access breach: 4.2.5 - Compromised network or system access
system access breach: 4.2.5 - Compromised network or system access
compromised access: 4.2.5 - Compromised network or system access
network compromise: 4.2.5 - Compromised network or system access
cloud access breach: 4.2.5.1 - Compromised cloud service provider access
cloud provider breach: 4.2.5.1 - Compromised cloud service provider access
cloud service compromise: 4.2.5.1 - Compromised cloud service provider access
cloud access compromise: 4.2.5.1 - Compromised cloud service provider access
business intelligence breach: 4.2.6 - Compromised business intelligence
intelligence theft: 4.2.6 - Compromised business intelligence
stolen bi: 4.2.6 - Compromised business intelligence
business data compromise: 4.2.6 - Compromised business intelligence
bi compromise: 4.2.6 - Compromised business intelligence
account takeover: 4.3 - Account takeover (ATO)
ato: 4.3 - Account takeover (ATO)
account hijacking: 4.3 - Account takeover (ATO)
account theft: 4.3 - Account takeover (ATO)
account compromise: 4.3 - Account takeover (ATO)
call center fraud: 4.3.1 - Call centers
call center scam: 4.3.1 - Call centers
call center compromise: 4.3.1 - Call centers
fraudulent call center: 4.3.1 - Call centers
account checking: 4.3.2 - Account checking and credential stuffing
credential stuffing: 4.3.2 - Account checking and credential stuffing
account validation: 4.3.2 - Account checking and credential stuffing
account checking fraud: 4.3.2 - Account checking and credential stuffing
credential stuffing attack: 4.3.2 - Account checking and credential stuffing
account-checking file: 4.3.2.1 - Account-checking configuration file(s)
configuration file: 4.3.2.1 - Account-checking configuration file(s)
account checking config: 4.3.2.1 - Account-checking configuration file(s)
credential stuffing file: 4.3.2.1 - Account-checking configuration file(s)
account brute forcing: 4.3.3 - Account brute forcing
password brute forcing: 4.3.3 - Account brute forcing
account attack: 4.3.3 - Account brute forcing
brute force attack: 4.3.3 - Account brute forcing
account brute force: 4.3.3 - Account brute forcing
password spraying: 4.3.3.1 - Password spraying
password attack: 4.3.3.1 - Password spraying
credential spraying: 4.3.3.1 - Password spraying
password brute force: 4.3.3.1 - Password spraying
account spraying: 4.3.3.1 - Password spraying
sim swapping: 4.3.4 - Subscriber identity module (SIM) swapping
sim swap fraud: 4.3.4 - Subscriber identity module (SIM) swapping
sim attack: 4.3.4 - Subscriber identity module (SIM) swapping
sim hijacking: 4.3.4 - Subscriber identity module (SIM) swapping
subscriber module attack: 4.3.4 - Subscriber identity module (SIM) swapping
social engineering: 4.4 - Social engineering
human hacking: 4.4 - Social engineering
psychological manipulation: 4.4 - Social engineering
social hacking: 4.4 - Social engineering
social deception: 4.4 - Social engineering
phishing: 4.4.1 - Phishing
phishing attack: 4.4.1 - Phishing
email phishing: 4.4.1 - Phishing
phishing scam: 4.4.1 - Phishing
phishing attempt: 4.4.1 - Phishing
spear-phishing: 4.4.2 - Spear-phishing
targeted phishing: 4.4.2 - Spear-phishing
spear-phishing attack: 4.4.2 - Spear-phishing
spear-phishing scam: 4.4.2 - Spear-phishing
spear-phishing attempt: 4.4.2 - Spear-phishing
vishing: 4.4.3 - Vishing
voice phishing: 4.4.3 - Vishing
phone scam: 4.4.3 - Vishing
vishing attack: 4.4.3 - Vishing
vishing attempt: 4.4.3 - Vishing
social media scam: 4.4.4 - Social media scams
social media fraud: 4.4.4 - Social media scams
social network scam: 4.4.4 - Social media scams
social media deception: 4.4.4 - Social media scams
social media hacking: 4.4.4 - Social media scams
smishing: 4.4.5 - Smishing
sms phishing: 4.4.5 - Smishing
text message scam: 4.4.5 - Smishing
smishing attack: 4.4.5 - Smishing
smishing attempt: 4.4.5 - Smishing
callback phishing: 4.4.6 - Callback phishing
callback scam: 4.4.6 - Callback phishing
callback attack: 4.4.6 - Callback phishing
callback deception: 4.4.6 - Callback phishing
phone callback phishing: 4.4.6 - Callback phishing
access control bypass: 4.5 - Access control bypass
access bypass: 4.5 - Access control bypass
control bypass: 4.5 - Access control bypass
access compromise: 4.5 - Access control bypass
authentication bypass: 4.5.1 - Multifactor authentication (MFA) bypass
mfa bypass: 4.5.1 - Multifactor authentication (MFA) bypass
multifactor bypass: 4.5.1 - Multifactor authentication (MFA) bypass
mfa compromise: 4.5.1 - Multifactor authentication (MFA) bypass
security bypass: 4.5.1 - Multifactor authentication (MFA) bypass
otp bypass: 4.5.1.1 - One-time password (OTP) bypass
one-time password bypass: 4.5.1.1 - One-time password (OTP) bypass
otp compromise: 4.5.1.1 - One-time password (OTP) bypass
password bypass: 4.5.1.1 - One-time password (OTP) bypass
otp attack: 4.5.1.1 - One-time password (OTP) bypass
ai fraud: 4.6 - Artificial intelligence (AI) fraud
artificial intelligence fraud: 4.6 - Artificial intelligence (AI) fraud
machine learning fraud: 4.6 - Artificial intelligence (AI) fraud
ai manipulation: 4.6 - Artificial intelligence (AI) fraud
ai deception: 4.6 - Artificial intelligence (AI) fraud
algorithmic fraud: 4.6 - Artificial intelligence (AI) fraud
ai exploitation: 4.6 - Artificial intelligence (AI) fraud
deepfake: 4.6.1 - Deepfake technology
deepfake technology: 4.6.1 - Deepfake technology
synthetic media: 4.6.1 - Deepfake technology
fake videos: 4.6.1 - Deepfake technology
fake audio: 4.6.1 - Deepfake technology
ai-generated content: 4.6.1 - Deepfake technology
deepfake fraud: 4.6.1 - Deepfake technology
deepfake scam: 4.6.1 - Deepfake technology
chatbot abuse: 4.6.2 - Chatbot abuse
automated abuse: 4.6.2 - Chatbot abuse
ai abuse: 4.6.2 - Chatbot abuse
chatbot manipulation: 4.6.2 - Chatbot abuse
bot fraud: 4.6.2 - Chatbot abuse
automated fraud: 4.6.2 - Chatbot abuse
chatbot exploitation: 4.6.2 - Chatbot abuse
access classification: 4.7 - Access classification
access control: 4.7 - Access classification
access category: 4.7 - Access classification
access type: 4.7 - Access classification
classification of access: 4.7 - Access classification
wholesale access: 4.7.1 - Wholesale access
bulk access: 4.7.1 - Wholesale access
large scale access: 4.7.1 - Wholesale access
mass access: 4.7.1 - Wholesale access
network wholesale: 4.7.1 - Wholesale access
data wholesale: 4.7.1 - Wholesale access
specified access: 4.7.2 - Specified access
access specification: 4.7.2 - Specified access
specific access: 4.7.2 - Specified access
access criteria: 4.7.2 - Specified access
defined access: 4.7.2 - Specified access
adversary tactics: 5 - Adversary Tactics and Activities
adversary activities: 5 - Adversary Tactics and Activities
cyber tactics: 5 - Adversary Tactics and Activities
attacker techniques: 5 - Adversary Tactics and Activities
threat tactics: 5 - Adversary Tactics and Activities
pre-attack tactics: 5.1 - Pre-attack tactics
pre-attack activities: 5.1 - Pre-attack tactics
attack preparation: 5.1 - Pre-attack tactics
pre-attack planning: 5.1 - Pre-attack tactics
reconnaissance: 5.1.1 - Reconnaissance and information gathering tactic
intelligence collection: 5.1.1 - Reconnaissance and information gathering tactic
recon activity: 5.1.1 - Reconnaissance and information gathering tactic
pre-attack recon: 5.1.1 - Reconnaissance and information gathering tactic
build capabilities: 5.1.2 - Build capabilities tactic
capability development: 5.1.2 - Build capabilities tactic
tool building: 5.1.2 - Build capabilities tactic
attack tool development: 5.1.2 - Build capabilities tactic
capability preparation: 5.1.2 - Build capabilities tactic
post-attack tactics: 5.2 - Post-attack tactics
post-attack activities: 5.2 - Post-attack tactics
post-exploit tactics: 5.2 - Post-attack tactics
post-compromise actions: 5.2 - Post-attack tactics
initial access: 5.2.1 - Initial access tactic
initial compromise: 5.2.1 - Initial access tactic
first access: 5.2.1 - Initial access tactic
initial breach: 5.2.1 - Initial access tactic
entry point attack: 5.2.1 - Initial access tactic
command and control: 5.2.10 - Command and control tactic
c2 tactic: 5.2.10 - Command and control tactic
c2 activity: 5.2.10 - Command and control tactic
command channel: 5.2.10 - Command and control tactic
control server: 5.2.10 - Command and control tactic
exfiltration: 5.2.11 - Exfiltration tactic
data exfiltration: 5.2.11 - Exfiltration tactic
data extraction: 5.2.11 - Exfiltration tactic
exfil tactics: 5.2.11 - Exfiltration tactic
impact tactic: 5.2.12 - Impact tactic
system impact: 5.2.12 - Impact tactic
destructive activity: 5.2.12 - Impact tactic
disruptive action: 5.2.12 - Impact tactic
impact operation: 5.2.12 - Impact tactic
defacement: 5.2.12.1 - Defacement technique
website defacement: 5.2.12.1 - Defacement technique
content defacement: 5.2.12.1 - Defacement technique
visual tampering: 5.2.12.1 - Defacement technique
defacement attack: 5.2.12.1 - Defacement technique
denial of service: 5.2.12.2 - Denial of service (DoS) technique
dos attack: 5.2.12.2 - Denial of service (DoS) technique
service disruption: 5.2.12.2 - Denial of service (DoS) technique
dos: 5.2.12.2 - Denial of service (DoS) technique
dos technique: 5.2.12.2 - Denial of service (DoS) technique
execution tactic: 5.2.2 - Execution tactic
execution activity: 5.2.2 - Execution tactic
code execution: 5.2.2 - Execution tactic
attack execution: 5.2.2 - Execution tactic
execution action: 5.2.2 - Execution tactic
persistence tactic: 5.2.3 - Persistence tactic
persistent presence: 5.2.3 - Persistence tactic
persistent access: 5.2.3 - Persistence tactic
long-term access: 5.2.3 - Persistence tactic
persistence method: 5.2.3 - Persistence tactic
privilege escalation: 5.2.4 - Privilege escalation tactic
escalation tactic: 5.2.4 - Privilege escalation tactic
privilege elevation: 5.2.4 - Privilege escalation tactic
access escalation: 5.2.4 - Privilege escalation tactic
escalation attack: 5.2.4 - Privilege escalation tactic
defense evasion: 5.2.5 - Defense evasion tactic
evasion tactic: 5.2.5 - Defense evasion tactic
security evasion: 5.2.5 - Defense evasion tactic
detection evasion: 5.2.5 - Defense evasion tactic
defense bypass: 5.2.5 - Defense evasion tactic
credential theft: 5.2.6 - Credential access tactic
credential access: 5.2.6 - Credential access tactic
password access: 5.2.6 - Credential access tactic
account access: 5.2.6 - Credential access tactic
credential harvesting: 5.2.6 - Credential access tactic
discovery tactic: 5.2.7 - Discovery tactic
network discovery: 5.2.7 - Discovery tactic
system discovery: 5.2.7 - Discovery tactic
environment discovery: 5.2.7 - Discovery tactic
discovery activity: 5.2.7 - Discovery tactic
lateral movement: 5.2.8 - Lateral movement tactic
movement tactic: 5.2.8 - Lateral movement tactic
network movement: 5.2.8 - Lateral movement tactic
lateral traversal: 5.2.8 - Lateral movement tactic
lateral access: 5.2.8 - Lateral movement tactic
information gathering: 5.2.9 - Collection tactic
collection tactic: 5.2.9 - Collection tactic
data collection: 5.2.9 - Collection tactic
data harvesting: 5.2.9 - Collection tactic
collection activity: 5.2.9 - Collection tactic
physical attack: 5.3 - Physical attack techniques against systems
system attack: 5.3 - Physical attack techniques against systems
hardware attack: 5.3 - Physical attack techniques against systems
physical breach: 5.3 - Physical attack techniques against systems
atm attack: 5.3.1 - Physical ATM attack techniques
physical atm attack: 5.3.1 - Physical ATM attack techniques
atm tampering: 5.3.1 - Physical ATM attack techniques
atm physical breach: 5.3.1 - Physical ATM attack techniques
cash machine attack: 5.3.1 - Physical ATM attack techniques
pos attack: 5.3.2 - Physical point-of-sale (PoS) system attack techniques
physical pos attack: 5.3.2 - Physical point-of-sale (PoS) system attack techniques
pos tampering: 5.3.2 - Physical point-of-sale (PoS) system attack techniques
pos physical breach: 5.3.2 - Physical point-of-sale (PoS) system attack techniques
payment terminal attack: 5.3.2 - Physical point-of-sale (PoS) system attack techniques
physical sabotage: 5.3.3 - Physical sabotage techniques (deprecated)
sabotage technique: 5.3.3 - Physical sabotage techniques (deprecated)
system sabotage: 5.3.3 - Physical sabotage techniques (deprecated)
physical disruption: 5.3.3 - Physical sabotage techniques (deprecated)
hardware sabotage: 5.3.3 - Physical sabotage techniques (deprecated)
insider threat: 5.4 - Insider threat tactics
insider attack: 5.4 - Insider threat tactics
internal threat: 5.4 - Insider threat tactics
employee threat: 5.4 - Insider threat tactics
insider sabotage: 5.4 - Insider threat tactics
data disclosure: 5.5 - Information compromise or disclosure tactics
information leak: 5.5 - Information compromise or disclosure tactics
compromise tactics: 5.5 - Information compromise or disclosure tactics
espionage: 5.5.1 - Espionage
corporate espionage: 5.5.1 - Espionage
industrial espionage: 5.5.1 - Espionage
spy activity: 5.5.1 - Espionage
espionage operation: 5.5.1 - Espionage
outsider trading: 5.5.2 - Outsider trading
insider trading: 5.5.2 - Outsider trading
illegal trading: 5.5.2 - Outsider trading
trading fraud: 5.5.2 - Outsider trading
stock manipulation: 5.5.2 - Outsider trading
data breach: 5.5.3 - Information or data breach
data theft: 5.5.3 - Information or data breach
information compromise: 5.5.3 - Information or data breach
information breach: 5.5.3 - Information or data breach
data leak: 5.5.3 - Information or data breach
ransom demand: 5.5.4 - Blackmail
blackmail: 5.5.4 - Blackmail
extortion: 5.5.4 - Blackmail
threat coercion: 5.5.4 - Blackmail
blackmail operation: 5.5.4 - Blackmail
supply chain attack: 5.5.5 - Supply chain attack tactic
supply chain compromise: 5.5.5 - Supply chain attack tactic
supply chain breach: 5.5.5 - Supply chain attack tactic
supplier attack: 5.5.5 - Supply chain attack tactic
vendor compromise: 5.5.5 - Supply chain attack tactic
hacktivism: 5.5.6 - Hacktivism
activist hacking: 5.5.6 - Hacktivism
political hacking: 5.5.6 - Hacktivism
cyber activism: 5.5.6 - Hacktivism
hacktivist activity: 5.5.6 - Hacktivism
industry threat: 6 - Threats Impacting Industry or Region
regional threat: 6 - Threats Impacting Industry or Region
sector threat: 6 - Threats Impacting Industry or Region
geographic threat: 6 - Threats Impacting Industry or Region
sector impact: 6.1 - All sectors and industries
all sectors: 6.1 - All sectors and industries
all industries: 6.1 - All sectors and industries
sector-wide threat: 6.1 - All sectors and industries
industry-wide threat: 6.1 - All sectors and industries
consumer sector: 6.1.1 - Consumer and industrial products sector
product industry: 6.1.1 - Consumer and industrial products sector
consumer business: 6.1.1.1 - Consumer business industry
consumer industry: 6.1.1.1 - Consumer business industry
business-to-consumer: 6.1.1.1 - Consumer business industry
transportation industry: 6.1.1.2 - Transportation industry
car rental: 6.1.1.2 - Transportation industry
taxi: 6.1.1.2 - Transportation industry
ridesharing: 6.1.1.2 - Transportation industry
transport sector: 6.1.1.2 - Transportation industry
freight: 6.1.1.2 - Transportation industry
transport services: 6.1.1.2 - Transportation industry
aviation industry: 6.1.1.2.1 - Aviation industry
airline: 6.1.1.2.1 - Aviation industry
air travel: 6.1.1.2.1 - Aviation industry
aircraft manufacturing: 6.1.1.2.1 - Aviation industry
aerospace: 6.1.1.2.1 - Aviation industry
airport: 6.1.1.2.1 - Aviation industry
aviation security: 6.1.1.2.1 - Aviation industry
flight industry: 6.1.1.2.1 - Aviation industry
consumer products: 6.1.1.3 - Consumer products industry
consumer market: 6.1.1.3 - Consumer products industry
retail products: 6.1.1.3 - Consumer products industry
ecommerce: 6.1.1.3 - Consumer products industry
e-commerce: 6.1.1.3 - Consumer products industry
consumer goods: 6.1.1.3 - Consumer products industry
product manufacturing: 6.1.1.3 - Consumer products industry
sports industry: 6.1.1.4 - Sports and leisure industry
leisure industry: 6.1.1.4 - Sports and leisure industry
sports sector: 6.1.1.4 - Sports and leisure industry
leisure sector: 6.1.1.4 - Sports and leisure industry
entertainment: 6.1.1.4 - Sports and leisure industry
gym: 6.1.1.4 - Sports and leisure industry
sports club: 6.1.1.4 - Sports and leisure industry
physical fitness: 6.1.1.4 - Sports and leisure industry
spa: 6.1.1.4 - Sports and leisure industry
hospitality industry: 6.1.1.5 - Hospitality industry
hotel industry: 6.1.1.5 - Hospitality industry
hotel: 6.1.1.5 - Hospitality industry
tourism: 6.1.1.5 - Hospitality industry
hospitality sector: 6.1.1.5 - Hospitality industry
accommodation: 6.1.1.5 - Hospitality industry
restaurant industry: 6.1.1.6 - Restaurants and food service industry
restaurants: 6.1.1.6 - Restaurants and food service industry
food service: 6.1.1.6 - Restaurants and food service industry
dining sector: 6.1.1.6 - Restaurants and food service industry
catering industry: 6.1.1.6 - Restaurants and food service industry
coffee shop: 6.1.1.6 - Restaurants and food service industry
bakery: 6.1.1.6 - Restaurants and food service industry
restaurant business: 6.1.1.6 - Restaurants and food service industry
food delivery: 6.1.1.6 - Restaurants and food service industry
meal kit: 6.1.1.6 - Restaurants and food service industry
retail business: 6.1.1.7 - Retail, wholesale and distribution industry
retail industry: 6.1.1.7 - Retail, wholesale and distribution industry
shopping mall: 6.1.1.7 - Retail, wholesale and distribution industry
grocery: 6.1.1.7 - Retail, wholesale and distribution industry
supermarket: 6.1.1.7 - Retail, wholesale and distribution industry
retail store: 6.1.1.7 - Retail, wholesale and distribution industry
clothing store: 6.1.1.7 - Retail, wholesale and distribution industry
department store: 6.1.1.7 - Retail, wholesale and distribution industry
convenience store: 6.1.1.7 - Retail, wholesale and distribution industry
convenience shop: 6.1.1.7 - Retail, wholesale and distribution industry
electronics store: 6.1.1.7 - Retail, wholesale and distribution industry
book store: 6.1.1.7 - Retail, wholesale and distribution industry
toy store: 6.1.1.7 - Retail, wholesale and distribution industry
home goods: 6.1.1.7 - Retail, wholesale and distribution industry
craft store: 6.1.1.7 - Retail, wholesale and distribution industry
outdoor equipment store: 6.1.1.7 - Retail, wholesale and distribution industry
hardware store: 6.1.1.7 - Retail, wholesale and distribution industry
wholesale industry: 6.1.1.7 - Retail, wholesale and distribution industry
distribution sector: 6.1.1.7 - Retail, wholesale and distribution industry
wholesale market: 6.1.1.7 - Retail, wholesale and distribution industry
fashion industry: 6.1.1.7.1 - Fashion industry
apparel sector: 6.1.1.7.1 - Fashion industry
clothing industry: 6.1.1.7.1 - Fashion industry
fashion market: 6.1.1.7.1 - Fashion industry
beauty salon: 6.1.1.7.1 - Fashion industry
hair salon: 6.1.1.7.1 - Fashion industry
nail salon: 6.1.1.7.1 - Fashion industry
textile industry: 6.1.1.7.1 - Fashion industry
nonprofit sector: 6.1.10 - Nonprofit sector
charity organizations: 6.1.10 - Nonprofit sector
nonprofit industry: 6.1.10 - Nonprofit sector
charitable sector: 6.1.10 - Nonprofit sector
church: 6.1.10 - Nonprofit sector
nonprofit organizations: 6.1.10 - Nonprofit sector
charitable organizations: 6.1.10.1 - Charitable organizations
charity: 6.1.10.1 - Charitable organizations
nonprofit charity: 6.1.10.1 - Charitable organizations
philanthropy: 6.1.10.1 - Charitable organizations
charity sector: 6.1.10.1 - Charitable organizations
civic leagues: 6.1.10.2 - Civic leagues and social welfare organizations
social welfare organizations: 6.1.10.2 - Civic leagues and social welfare organizations
civic organizations: 6.1.10.2 - Civic leagues and social welfare organizations
social welfare: 6.1.10.2 - Civic leagues and social welfare organizations
community groups: 6.1.10.2 - Civic leagues and social welfare organizations
ngos: 6.1.10.3 - Nongovernmental organizations (NGOs)
ngo: 6.1.10.3 - Nongovernmental organizations (NGOs)
nongovernmental organizations: 6.1.10.3 - Nongovernmental organizations (NGOs)
nonprofit ngos: 6.1.10.3 - Nongovernmental organizations (NGOs)
ngo sector: 6.1.10.3 - Nongovernmental organizations (NGOs)
ngo activities: 6.1.10.3.1 - Operational NGOs
operational ngos: 6.1.10.3.1 - Operational NGOs
active ngos: 6.1.10.3.1 - Operational NGOs
ngo operations: 6.1.10.3.1 - Operational NGOs
operational non-profits: 6.1.10.3.1 - Operational NGOs
advocacy ngos: 6.1.10.3.2 - Advocacy NGOs
campaigning ngos: 6.1.10.3.2 - Advocacy NGOs
ngo advocacy: 6.1.10.3.2 - Advocacy NGOs
ngo lobbying: 6.1.10.3.2 - Advocacy NGOs
advocacy non-profits: 6.1.10.3.2 - Advocacy NGOs
charitable foundations: 6.1.10.4 - Private charitable foundations
private foundations: 6.1.10.4 - Private charitable foundations
charity foundations: 6.1.10.4 - Private charitable foundations
philanthropic foundations: 6.1.10.4 - Private charitable foundations
private charity: 6.1.10.4 - Private charitable foundations
social advocacy: 6.1.10.5 - Social advocacy groups
advocacy groups: 6.1.10.5 - Social advocacy groups
social campaign: 6.1.10.5 - Social advocacy groups
community advocacy: 6.1.10.5 - Social advocacy groups
advocacy organizations: 6.1.10.5 - Social advocacy groups
r&d sector: 6.1.11 - Research and development sector
research sector: 6.1.11 - Research and development sector
development sector: 6.1.11 - Research and development sector
research and development: 6.1.11 - Research and development sector
r&d activities: 6.1.11 - Research and development sector
scientific research: 6.1.11.1 - Scientific research and development organizations
r&d organizations: 6.1.11.1 - Scientific research and development organizations
science r&d: 6.1.11.1 - Scientific research and development organizations
scientific development: 6.1.11.1 - Scientific research and development organizations
research institutions: 6.1.11.1 - Scientific research and development organizations
multipurpose research institute: 6.1.11.2 - Multipurpose research institutes
research organization: 6.1.11.2 - Multipurpose research institutes
academic research: 6.1.11.2 - Multipurpose research institutes
research lab: 6.1.11.2 - Multipurpose research institutes
research center: 6.1.11.2 - Multipurpose research institutes
multi-disciplinary research: 6.1.11.2 - Multipurpose research institutes
industrial automation: 6.1.12 - Industrial automation sector
automation sector: 6.1.12 - Industrial automation sector
automated industry: 6.1.12 - Industrial automation sector
industrial control: 6.1.12 - Industrial automation sector
automation systems: 6.1.12 - Industrial automation sector
scada: 6.1.12.1 - Supervisory control and data acquisition (SCADA) systems
scada systems: 6.1.12.1 - Supervisory control and data acquisition (SCADA) systems
industrial control systems: 6.1.12.1 - Supervisory control and data acquisition (SCADA) systems
supervisory control: 6.1.12.1 - Supervisory control and data acquisition (SCADA) systems
scada network: 6.1.12.1 - Supervisory control and data acquisition (SCADA) systems
cryptocurrency: 6.1.13 - Digital currency sector
digital currency: 6.1.13 - Digital currency sector
blockchain: 6.1.13 - Digital currency sector
crypto assets: 6.1.13 - Digital currency sector
crypto trading: 6.1.13 - Digital currency sector
digital coins: 6.1.13 - Digital currency sector
decentralized finance (defi): 6.1.13 - Digital currency sector
crypto market: 6.1.13 - Digital currency sector
crypto industry: 6.1.13.1 - Cryptocurrency industry
bitcoin: 6.1.13.1 - Cryptocurrency industry
ethereum: 6.1.13.1 - Cryptocurrency industry
altcoins: 6.1.13.1 - Cryptocurrency industry
crypto exchange: 6.1.13.1 - Cryptocurrency industry
crypto wallet: 6.1.13.1 - Cryptocurrency industry
energy sector: 6.1.2 - Energy, resources and agriculture sector
resources sector: 6.1.2 - Energy, resources and agriculture sector
agriculture sector: 6.1.2 - Energy, resources and agriculture sector
energy industry: 6.1.2 - Energy, resources and agriculture sector
resource industry: 6.1.2 - Energy, resources and agriculture sector
oil industry: 6.1.2.1 - Oil, gas and consumable fuels industry
gas industry: 6.1.2.1 - Oil, gas and consumable fuels industry
fuel industry: 6.1.2.1 - Oil, gas and consumable fuels industry
energy production: 6.1.2.1 - Oil, gas and consumable fuels industry
oil and gas: 6.1.2.1 - Oil, gas and consumable fuels industry
oil & gas: 6.1.2.1 - Oil, gas and consumable fuels industry
power industry: 6.1.2.2 - Power and utilities industry
utilities industry: 6.1.2.2 - Power and utilities industry
electricity sector: 6.1.2.2 - Power and utilities industry
utility services: 6.1.2.2 - Power and utilities industry
energy distribution: 6.1.2.2 - Power and utilities industry
logistics: 6.1.2.3 - Shipping and ports industry
shipping industry: 6.1.2.3 - Shipping and ports industry
ports industry: 6.1.2.3 - Shipping and ports industry
maritime sector: 6.1.2.3 - Shipping and ports industry
shipping operations: 6.1.2.3 - Shipping and ports industry
port of: 6.1.2.3 - Shipping and ports industry
water industry: 6.1.2.4 - Water industry
water sector: 6.1.2.4 - Water industry
water utilities: 6.1.2.4 - Water industry
water supply: 6.1.2.4 - Water industry
water management: 6.1.2.4 - Water industry
agriculture industry: 6.1.2.5 - Agriculture and food and beverage production industry
food production: 6.1.2.5 - Agriculture and food and beverage production industry
beverage production: 6.1.2.5 - Agriculture and food and beverage production industry
agricultural sector: 6.1.2.5 - Agriculture and food and beverage production industry
food industry: 6.1.2.5 - Agriculture and food and beverage production industry
mining industry: 6.1.2.6 - Mining industry
mining sector: 6.1.2.6 - Mining industry
resource extraction: 6.1.2.6 - Mining industry
mineral industry: 6.1.2.6 - Mining industry
mining operations: 6.1.2.6 - Mining industry
renewable energy: 6.1.2.7 - Renewable energy industry
solar power: 6.1.2.7 - Renewable energy industry
wind energy: 6.1.2.7 - Renewable energy industry
hydroelectric power: 6.1.2.7 - Renewable energy industry
biomass energy: 6.1.2.7 - Renewable energy industry
geothermal energy: 6.1.2.7 - Renewable energy industry
clean energy: 6.1.2.7 - Renewable energy industry
green energy: 6.1.2.7 - Renewable energy industry
finance industry: 6.1.3 - Financial services sector
financial institutions: 6.1.3 - Financial services sector
finance services: 6.1.3 - Financial services sector
brokerage: 6.1.3 - Financial services sector
stock exchange: 6.1.3 - Financial services sector
banking sector: 6.1.3.1 - Banking and securities industry
banking industry: 6.1.3.1 - Banking and securities industry
credit union: 6.1.3.1 - Banking and securities industry
securities industry: 6.1.3.1 - Banking and securities industry
financial securities: 6.1.3.1 - Banking and securities industry
investment banking: 6.1.3.1 - Banking and securities industry
insurance industry: 6.1.3.2 - Insurance industry
insurance sector: 6.1.3.2 - Insurance industry
insurance services: 6.1.3.2 - Insurance industry
financial insurance: 6.1.3.2 - Insurance industry
insurance market: 6.1.3.2 - Insurance industry
investment management: 6.1.3.3 - Investment management industry
investment industry: 6.1.3.3 - Investment management industry
asset management: 6.1.3.3 - Investment management industry
wealth management: 6.1.3.3 - Investment management industry
investment sector: 6.1.3.3 - Investment management industry
payment processing: 6.1.3.4 - Payment processing industry
payment industry: 6.1.3.4 - Payment processing industry
transaction processing: 6.1.3.4 - Payment processing industry
payment services: 6.1.3.4 - Payment processing industry
financial transactions: 6.1.3.4 - Payment processing industry
health care sector: 6.1.4 - Life sciences and health care sector
healthcare: 6.1.4 - Life sciences and health care sector
healthcare sector: 6.1.4 - Life sciences and health care sector
veterinary: 6.1.4 - Life sciences and health care sector
medical industry: 6.1.4 - Life sciences and health care sector
biotech industry: 6.1.4 - Life sciences and health care sector
health services: 6.1.4.1 - Health care providers and services industry
health care provider: 6.1.4.1 - Health care providers and services industry
healthcare provider: 6.1.4.1 - Health care providers and services industry
optometry: 6.1.4.1 - Health care providers and services industry
medical services: 6.1.4.1 - Health care providers and services industry
health industry: 6.1.4.1 - Health care providers and services industry
medical care: 6.1.4.1 - Health care providers and services industry
health care equipment: 6.1.4.2 - Health care equipment and technology
healthcare equipment: 6.1.4.2 - Health care equipment and technology
medical technology: 6.1.4.2 - Health care equipment and technology
health tech: 6.1.4.2 - Health care equipment and technology
medical devices: 6.1.4.2 - Health care equipment and technology
health care tools: 6.1.4.2 - Health care equipment and technology
healthcare tools: 6.1.4.2 - Health care equipment and technology
life sciences: 6.1.4.3 - Pharmaceuticals, biotechnology and life sciences industry
pharmaceutical: 6.1.4.3 - Pharmaceuticals, biotechnology and life sciences industry
pharmacy: 6.1.4.3 - Pharmaceuticals, biotechnology and life sciences industry
pharmacies: 6.1.4.3 - Pharmaceuticals, biotechnology and life sciences industry
biotechnology: 6.1.4.3 - Pharmaceuticals, biotechnology and life sciences industry
pharma industry: 6.1.4.3 - Pharmaceuticals, biotechnology and life sciences industry
biotech sector: 6.1.4.3 - Pharmaceuticals, biotechnology and life sciences industry
manufacturing sector: 6.1.5 - Manufacturing sector
manufacturing industry: 6.1.5 - Manufacturing sector
production industry: 6.1.5 - Manufacturing sector
industrial production: 6.1.5 - Manufacturing sector
manufacturing operations: 6.1.5 - Manufacturing sector
aerospace industry: 6.1.5.1 - Aerospace and defense industry
defense industry: 6.1.5.1 - Aerospace and defense industry
aerospace sector: 6.1.5.1 - Aerospace and defense industry
military manufacturing: 6.1.5.1 - Aerospace and defense industry
automotive industry: 6.1.5.2 - Automotive industry
car manufacturing: 6.1.5.2 - Automotive industry
vehicle production: 6.1.5.2 - Automotive industry
automotive sector: 6.1.5.2 - Automotive industry
car industry: 6.1.5.2 - Automotive industry
industrial products: 6.1.5.3 - Industrial products and services industry
industrial sector: 6.1.5.3 - Industrial products and services industry
industrial services: 6.1.5.3 - Industrial products and services industry
industrial goods: 6.1.5.3 - Industrial products and services industry
production services: 6.1.5.3 - Industrial products and services industry
chemicals industry: 6.1.5.4 - Chemicals and specialty materials industry
specialty materials: 6.1.5.4 - Chemicals and specialty materials industry
chemical sector: 6.1.5.4 - Chemicals and specialty materials industry
materials industry: 6.1.5.4 - Chemicals and specialty materials industry
chemical production: 6.1.5.4 - Chemicals and specialty materials industry
public sector: 6.1.6 - Public sector
tax authority: 6.1.6 - Public sector
post office: 6.1.6 - Public sector
government sector: 6.1.6 - Public sector
public services: 6.1.6 - Public sector
state sector: 6.1.6 - Public sector
public administration: 6.1.6 - Public sector
international government: 6.1.6.1 - International government
global government: 6.1.6.1 - International government
transnational administration: 6.1.6.1 - International government
international public sector: 6.1.6.1 - International government
national government: 6.1.6.2 - National government
federal government: 6.1.6.2 - National government
government agency: 6.1.6.2 - National government
federal agency: 6.1.6.2 - National government
country government: 6.1.6.2 - National government
national public sector: 6.1.6.2 - National government
government administration: 6.1.6.2 - National government
regional government: 6.1.6.3 - Regional government
local government: 6.1.6.3 - Regional government
state government: 6.1.6.3 - Regional government
regional administration: 6.1.6.3 - Regional government
local administration: 6.1.6.3 - Regional government
education sector: 6.1.6.4 - Education
university: 6.1.6.4 - Education
public school: 6.1.6.4 - Education
academic sector: 6.1.6.4 - Education
tutoring: 6.1.6.4 - Education
school industry: 6.1.6.4 - Education
education services: 6.1.6.4 - Education
academic institutions: 6.1.6.4 - Education
public safety: 6.1.6.5 - Public safety
safety sector: 6.1.6.5 - Public safety
safety services: 6.1.6.5 - Public safety
public security: 6.1.6.5 - Public safety
safety administration: 6.1.6.5 - Public safety
defense sector: 6.1.6.6 - Military and defense
military sector: 6.1.6.6 - Military and defense
armed forces: 6.1.6.6 - Military and defense
military industry: 6.1.6.6 - Military and defense
defense administration: 6.1.6.6 - Military and defense
real estate: 6.1.7 - Real estate sector
home builder: 6.1.7 - Real estate sector
property sector: 6.1.7 - Real estate sector
realty industry: 6.1.7 - Real estate sector
real estate market: 6.1.7 - Real estate sector
construction industry: 6.1.7.1 - Engineering and construction industry
engineering industry: 6.1.7.1 - Engineering and construction industry
building sector: 6.1.7.1 - Engineering and construction industry
construction services: 6.1.7.1 - Engineering and construction industry
engineering services: 6.1.7.1 - Engineering and construction industry
real estate fund: 6.1.7.2 - Real estate fund and investor industry
property fund: 6.1.7.2 - Real estate fund and investor industry
real estate investment: 6.1.7.2 - Real estate fund and investor industry
property investment: 6.1.7.2 - Real estate fund and investor industry
real estate investor: 6.1.7.2 - Real estate fund and investor industry
reit: 6.1.7.3 - Real estate investment trust (REIT) and property company industry
real estate investment trust: 6.1.7.3 - Real estate investment trust (REIT) and property company industry
property company: 6.1.7.3 - Real estate investment trust (REIT) and property company industry
real estate trust: 6.1.7.3 - Real estate investment trust (REIT) and property company industry
property investment trust: 6.1.7.3 - Real estate investment trust (REIT) and property company industry
property services: 6.1.7.4 - Real estate management, brokerage and service provider industry
real estate management: 6.1.7.4 - Real estate management, brokerage and service provider industry
property maagementn: 6.1.7.4 - Real estate management, brokerage and service provider industry
real estate brokerage: 6.1.7.4 - Real estate management, brokerage and service provider industry
real estate provider: 6.1.7.4 - Real estate management, brokerage and service provider industry
tenants: 6.1.7.5 - Tenants and occupiers industry
occupiers: 6.1.7.5 - Tenants and occupiers industry
tenant services: 6.1.7.5 - Tenants and occupiers industry
occupier services: 6.1.7.5 - Tenants and occupiers industry
property rental: 6.1.7.5 - Tenants and occupiers industry
technology sector: 6.1.8 - Technology, media and telecommunications sector
dating app: 6.1.8 - Technology, media and telecommunications sector
radio station: 6.1.8 - Technology, media and telecommunications sector
tv station: 6.1.8 - Technology, media and telecommunications sector
television station: 6.1.8 - Technology, media and telecommunications sector
broadcast network: 6.1.8 - Technology, media and telecommunications sector
telecommunications sector: 6.1.8 - Technology, media and telecommunications sector
tech industry: 6.1.8 - Technology, media and telecommunications sector
technology industry: 6.1.8.1 - Technology industry
tech sector: 6.1.8.1 - Technology industry
it industry: 6.1.8.1 - Technology industry
technology market: 6.1.8.1 - Technology industry
tech services: 6.1.8.1 - Technology industry
media sector: 6.1.8.2 - Media and entertainment industry
media industry: 6.1.8.2 - Media and entertainment industry
entertainment industry: 6.1.8.2 - Media and entertainment industry
theatre: 6.1.8.2 - Media and entertainment industry
arena: 6.1.8.2 - Media and entertainment industry
entertainment sector: 6.1.8.2 - Media and entertainment industry
amusement park: 6.1.8.2 - Media and entertainment industry
media services: 6.1.8.2 - Media and entertainment industry
gaming industry: 6.1.8.2.1 - Gaming industry
video games: 6.1.8.2.1 - Gaming industry
game development: 6.1.8.2.1 - Gaming industry
game developer: 6.1.8.2.1 - Gaming industry
game studio: 6.1.8.2.1 - Gaming industry
esports: 6.1.8.2.1 - Gaming industry
online gaming: 6.1.8.2.1 - Gaming industry
game publishers: 6.1.8.2.1 - Gaming industry
game consoles: 6.1.8.2.1 - Gaming industry
mobile gaming: 6.1.8.2.1 - Gaming industry
telecommunications industry: 6.1.8.3 - Telecommunications industry
telecom sector: 6.1.8.3 - Telecommunications industry
communication industry: 6.1.8.3 - Telecommunications industry
telecom services: 6.1.8.3 - Telecommunications industry
communication services: 6.1.8.3 - Telecommunications industry
iot industry: 6.1.8.4 - Internet of Things (IoT) industry
internet of things sector: 6.1.8.4 - Internet of Things (IoT) industry
connected devices: 6.1.8.4 - Internet of Things (IoT) industry
iot market: 6.1.8.4 - Internet of Things (IoT) industry
smart devices: 6.1.8.4 - Internet of Things (IoT) industry
cloud services: 6.1.8.5 - Cloud services industry
cloud industry: 6.1.8.5 - Cloud services industry
cloud sector: 6.1.8.5 - Cloud services industry
cloud computing: 6.1.8.5 - Cloud services industry
cloud market: 6.1.8.5 - Cloud services industry
professional services: 6.1.9 - Professional services and consulting sector
consulting sector: 6.1.9 - Professional services and consulting sector
consulting industry: 6.1.9 - Professional services and consulting sector
business services: 6.1.9 - Professional services and consulting sector
professional consulting: 6.1.9 - Professional services and consulting sector
it consulting: 6.1.9.1 - Information technology (IT) or technology consulting industry
technology consulting: 6.1.9.1 - Information technology (IT) or technology consulting industry
it services: 6.1.9.1 - Information technology (IT) or technology consulting industry
tech consulting: 6.1.9.1 - Information technology (IT) or technology consulting industry
technology services: 6.1.9.1 - Information technology (IT) or technology consulting industry
management consulting: 6.1.9.2 - Management and operations consulting industry
operations consulting: 6.1.9.2 - Management and operations consulting industry
business management: 6.1.9.2 - Management and operations consulting industry
management services: 6.1.9.2 - Management and operations consulting industry
operations services: 6.1.9.2 - Management and operations consulting industry
financial services: 6.1.9.3 - Financial and investment consulting industry
financial consulting: 6.1.9.3 - Financial and investment consulting industry
investment consulting: 6.1.9.3 - Financial and investment consulting industry
investment services: 6.1.9.3 - Financial and investment consulting industry
financial advisory: 6.1.9.3 - Financial and investment consulting industry
hr consulting: 6.1.9.4 - Human resources consulting industry
human resources: 6.1.9.4 - Human resources consulting industry
hr services: 6.1.9.4 - Human resources consulting industry
recruitment services: 6.1.9.4 - Human resources consulting industry
hr advisory: 6.1.9.4 - Human resources consulting industry
marketing consulting: 6.1.9.5 - Marketing and sales consulting industry
sales consulting: 6.1.9.5 - Marketing and sales consulting industry
marketing services: 6.1.9.5 - Marketing and sales consulting industry
sales services: 6.1.9.5 - Marketing and sales consulting industry
marketing advisory: 6.1.9.5 - Marketing and sales consulting industry
law services: 6.1.9.6 - Law services and consulting industry
legal consulting: 6.1.9.6 - Law services and consulting industry
legal services: 6.1.9.6 - Law services and consulting industry
law advisory: 6.1.9.6 - Law services and consulting industry
legal industry: 6.1.9.6 - Law services and consulting industry
notary: 6.1.9.6 - Law services and consulting industry
political consulting: 6.1.9.7 - Political consulting industry
political advisory: 6.1.9.7 - Political consulting industry
campaign consulting: 6.1.9.7 - Political consulting industry
political services: 6.1.9.7 - Political consulting industry
political advisory services: 6.1.9.7 - Political consulting industry
security consulting: 6.1.9.8 - Physical security consulting industry
physical security: 6.1.9.8 - Physical security consulting industry
security services: 6.1.9.8 - Physical security consulting industry
security advisory: 6.1.9.8 - Physical security consulting industry
physical protection: 6.1.9.8 - Physical security consulting industry
geographic regions: 6.2 - All geographic regions
global regions: 6.2 - All geographic regions
regional threats: 6.2 - All geographic regions
geographic threats: 6.2 - All geographic regions
regional impact: 6.2 - All geographic regions
africa: 6.2.1 - Africa
african countries: 6.2.1 - Africa
african region: 6.2.1 - Africa
africa threat: 6.2.1 - Africa
africa impact: 6.2.1 - Africa
algeria: 6.2.1.1 - Algeria
algerian threat: 6.2.1.1 - Algeria
algerian region: 6.2.1.1 - Algeria
algeria impact: 6.2.1.1 - Algeria
chad: 6.2.1.10 - Chad
chadian threat: 6.2.1.10 - Chad
chadian region: 6.2.1.10 - Chad
chad impact: 6.2.1.10 - Chad
comoros: 6.2.1.11 - Comoros
comorian threat: 6.2.1.11 - Comoros
comorian region: 6.2.1.11 - Comoros
comoros impact: 6.2.1.11 - Comoros
congo: 6.2.1.12 - Congo (Brazzaville)
brazzaville: 6.2.1.12 - Congo (Brazzaville)
congolese threat: 6.2.1.13 - Congo, Democratic Republic of the
congolese region: 6.2.1.13 - Congo, Democratic Republic of the
congo impact: 6.2.1.13 - Congo, Democratic Republic of the
drc: 6.2.1.13 - Congo, Democratic Republic of the
democratic republic of congo: 6.2.1.13 - Congo, Democratic Republic of the
ivory coast: 6.2.1.14 - Cote d'Ivoire (Ivory Coast)
cote d'ivoire: 6.2.1.14 - Cote d'Ivoire (Ivory Coast)
ivorian threat: 6.2.1.14 - Cote d'Ivoire (Ivory Coast)
ivorian region: 6.2.1.14 - Cote d'Ivoire (Ivory Coast)
ivory coast impact: 6.2.1.14 - Cote d'Ivoire (Ivory Coast)
djibouti: 6.2.1.15 - Djibouti
djiboutian threat: 6.2.1.15 - Djibouti
djiboutian region: 6.2.1.15 - Djibouti
djibouti impact: 6.2.1.15 - Djibouti
egypt: 6.2.1.16 - Egypt
egyptian threat: 6.2.1.16 - Egypt
egyptian region: 6.2.1.16 - Egypt
egypt impact: 6.2.1.16 - Egypt
equatorial guinea: 6.2.1.17 - Equatorial Guinea
equatoguinean threat: 6.2.1.17 - Equatorial Guinea
equatoguinean region: 6.2.1.17 - Equatorial Guinea
equatorial guinea impact: 6.2.1.17 - Equatorial Guinea
eritrea: 6.2.1.18 - Eritrea
eritrean threat: 6.2.1.18 - Eritrea
eritrean region: 6.2.1.18 - Eritrea
eritrea impact: 6.2.1.18 - Eritrea
eswatini: 6.2.1.19 - Eswatini (ex-Swaziland)
swaziland: 6.2.1.19 - Eswatini (ex-Swaziland)
swazi threat: 6.2.1.19 - Eswatini (ex-Swaziland)
swazi region: 6.2.1.19 - Eswatini (ex-Swaziland)
eswatini impact: 6.2.1.19 - Eswatini (ex-Swaziland)
angola: 6.2.1.2 - Angola
angolan threat: 6.2.1.2 - Angola
angolan region: 6.2.1.2 - Angola
angola impact: 6.2.1.2 - Angola
ethiopia: 6.2.1.20 - Ethiopia
ethiopian threat: 6.2.1.20 - Ethiopia
ethiopian region: 6.2.1.20 - Ethiopia
ethiopia impact: 6.2.1.20 - Ethiopia
gabon: 6.2.1.21 - Gabon
gabonese threat: 6.2.1.21 - Gabon
gabonese region: 6.2.1.21 - Gabon
gabon impact: 6.2.1.21 - Gabon
gambia: 6.2.1.22 - Gambia
gambian threat: 6.2.1.22 - Gambia
gambian region: 6.2.1.22 - Gambia
gambia impact: 6.2.1.22 - Gambia
ghana: 6.2.1.23 - Ghana
ghanaian threat: 6.2.1.23 - Ghana
ghanaian region: 6.2.1.23 - Ghana
ghana impact: 6.2.1.23 - Ghana
guinea: 6.2.1.24 - Guinea
guinean threat: 6.2.1.24 - Guinea
guinean region: 6.2.1.24 - Guinea
guinea impact: 6.2.1.24 - Guinea
guinea-bissau: 6.2.1.25 - Guinea-Bissau
bissau-guinean threat: 6.2.1.25 - Guinea-Bissau
bissau-guinean region: 6.2.1.25 - Guinea-Bissau
guinea-bissau impact: 6.2.1.25 - Guinea-Bissau
kenya: 6.2.1.26 - Kenya
kenyan threat: 6.2.1.26 - Kenya
kenyan region: 6.2.1.26 - Kenya
kenya impact: 6.2.1.26 - Kenya
lesotho: 6.2.1.27 - Lesotho
basotho threat: 6.2.1.27 - Lesotho
basotho region: 6.2.1.27 - Lesotho
lesotho impact: 6.2.1.27 - Lesotho
liberia: 6.2.1.28 - Liberia
liberian threat: 6.2.1.28 - Liberia
liberian region: 6.2.1.28 - Liberia
liberia impact: 6.2.1.28 - Liberia
libya: 6.2.1.29 - Libya
libyan threat: 6.2.1.29 - Libya
libyan region: 6.2.1.29 - Libya
libya impact: 6.2.1.29 - Libya
benin: 6.2.1.3 - Benin
beninese threat: 6.2.1.3 - Benin
beninese region: 6.2.1.3 - Benin
benin impact: 6.2.1.3 - Benin
madagascar: 6.2.1.30 - Madagascar
malagasy threat: 6.2.1.30 - Madagascar
malagasy region: 6.2.1.30 - Madagascar
madagascar impact: 6.2.1.30 - Madagascar
malawi: 6.2.1.31 - Malawi
malawian threat: 6.2.1.31 - Malawi
malawian region: 6.2.1.31 - Malawi
malawi impact: 6.2.1.31 - Malawi
mali: 6.2.1.32 - Mali
malian threat: 6.2.1.32 - Mali
malian region: 6.2.1.32 - Mali
mali impact: 6.2.1.32 - Mali
mauritania: 6.2.1.33 - Mauritania
mauritanian threat: 6.2.1.33 - Mauritania
mauritanian region: 6.2.1.33 - Mauritania
mauritania impact: 6.2.1.33 - Mauritania
mauritius: 6.2.1.34 - Mauritius
mauritian threat: 6.2.1.34 - Mauritius
mauritian region: 6.2.1.34 - Mauritius
mauritius impact: 6.2.1.34 - Mauritius
mayotte: 6.2.1.35 - Mayotte
mahoran threat: 6.2.1.35 - Mayotte
mahoran region: 6.2.1.35 - Mayotte
mayotte impact: 6.2.1.35 - Mayotte
morocco: 6.2.1.36 - Morocco
moroccan threat: 6.2.1.36 - Morocco
moroccan region: 6.2.1.36 - Morocco
morocco impact: 6.2.1.36 - Morocco
mozambique: 6.2.1.37 - Mozambique
mozambican threat: 6.2.1.37 - Mozambique
mozambican region: 6.2.1.37 - Mozambique
mozambique impact: 6.2.1.37 - Mozambique
namibia: 6.2.1.38 - Namibia
namibian threat: 6.2.1.38 - Namibia
namibian region: 6.2.1.38 - Namibia
namibia impact: 6.2.1.38 - Namibia
niger: 6.2.1.39 - Niger
nigerien threat: 6.2.1.39 - Niger
nigerien region: 6.2.1.39 - Niger
niger impact: 6.2.1.39 - Niger
botswana: 6.2.1.4 - Botswana
batswana threat: 6.2.1.4 - Botswana
batswana region: 6.2.1.4 - Botswana
botswana impact: 6.2.1.4 - Botswana
nigeria: 6.2.1.40 - Nigeria
nigerian threat: 6.2.1.40 - Nigeria
nigerian region: 6.2.1.40 - Nigeria
nigeria impact: 6.2.1.40 - Nigeria
reunion: 6.2.1.41 - Reunion
reunionese threat: 6.2.1.41 - Reunion
reunionese region: 6.2.1.41 - Reunion
reunion impact: 6.2.1.41 - Reunion
rwanda: 6.2.1.42 - Rwanda
rwandan threat: 6.2.1.42 - Rwanda
rwandan region: 6.2.1.42 - Rwanda
rwanda impact: 6.2.1.42 - Rwanda
saint helena: 6.2.1.43 - Saint Helena
saint helenian threat: 6.2.1.43 - Saint Helena
saint helenian region: 6.2.1.43 - Saint Helena
saint helena impact: 6.2.1.43 - Saint Helena
sao tome and principe: 6.2.1.44 - Sao Tome and Principe
santomean threat: 6.2.1.44 - Sao Tome and Principe
santomean region: 6.2.1.44 - Sao Tome and Principe
sao tome and principe impact: 6.2.1.44 - Sao Tome and Principe
senegal: 6.2.1.45 - Senegal
senegalese threat: 6.2.1.45 - Senegal
senegalese region: 6.2.1.45 - Senegal
senegal impact: 6.2.1.45 - Senegal
seychelles: 6.2.1.46 - Seychelles
seychellois threat: 6.2.1.46 - Seychelles
seychellois region: 6.2.1.46 - Seychelles
seychelles impact: 6.2.1.46 - Seychelles
sierra leone: 6.2.1.47 - Sierra Leone
sierra leonean threat: 6.2.1.47 - Sierra Leone
sierra leonean region: 6.2.1.47 - Sierra Leone
sierra leone impact: 6.2.1.47 - Sierra Leone
horn of africa: 6.2.1.48 - Somalia
somalia: 6.2.1.48 - Somalia
somalian threat: 6.2.1.48 - Somalia
somalian region: 6.2.1.48 - Somalia
somalia impact: 6.2.1.48 - Somalia
south africa: 6.2.1.49 - South Africa
south african threat: 6.2.1.49 - South Africa
south african region: 6.2.1.49 - South Africa
south africa impact: 6.2.1.49 - South Africa
burkina faso: 6.2.1.5 - Burkina Faso
burkinabe threat: 6.2.1.5 - Burkina Faso
burkinabe region: 6.2.1.5 - Burkina Faso
burkina faso impact: 6.2.1.5 - Burkina Faso
south sudan: 6.2.1.50 - South Sudan
south sudanese threat: 6.2.1.50 - South Sudan
south sudanese region: 6.2.1.50 - South Sudan
south sudan impact: 6.2.1.50 - South Sudan
sudan: 6.2.1.51 - Sudan
sudanese threat: 6.2.1.51 - Sudan
sudanese region: 6.2.1.51 - Sudan
sudan impact: 6.2.1.51 - Sudan
tanzania: 6.2.1.52 - Tanzania, United Republic of
tanzanian threat: 6.2.1.52 - Tanzania, United Republic of
tanzanian region: 6.2.1.52 - Tanzania, United Republic of
tanzania impact: 6.2.1.52 - Tanzania, United Republic of
togo: 6.2.1.53 - Togo
togolese threat: 6.2.1.53 - Togo
togolese region: 6.2.1.53 - Togo
togo impact: 6.2.1.53 - Togo
tunisia: 6.2.1.54 - Tunisia
tunisian threat: 6.2.1.54 - Tunisia
tunisian region: 6.2.1.54 - Tunisia
tunisia impact: 6.2.1.54 - Tunisia
uganda: 6.2.1.55 - Uganda
ugandan threat: 6.2.1.55 - Uganda
ugandan region: 6.2.1.55 - Uganda
uganda impact: 6.2.1.55 - Uganda
western sahara: 6.2.1.56 - Western Sahara
saharan threat: 6.2.1.56 - Western Sahara
saharan region: 6.2.1.56 - Western Sahara
western sahara impact: 6.2.1.56 - Western Sahara
zambia: 6.2.1.57 - Zambia
zambian threat: 6.2.1.57 - Zambia
zambian region: 6.2.1.57 - Zambia
zambia impact: 6.2.1.57 - Zambia
zimbabwe: 6.2.1.58 - Zimbabwe
zimbabwean threat: 6.2.1.58 - Zimbabwe
zimbabwean region: 6.2.1.58 - Zimbabwe
zimbabwe impact: 6.2.1.58 - Zimbabwe
burundi: 6.2.1.6 - Burundi
burundian threat: 6.2.1.6 - Burundi
burundian region: 6.2.1.6 - Burundi
burundi impact: 6.2.1.6 - Burundi
cameroon: 6.2.1.7 - Cameroon
cameroonian threat: 6.2.1.7 - Cameroon
cameroonian region: 6.2.1.7 - Cameroon
cameroon impact: 6.2.1.7 - Cameroon
cape verde: 6.2.1.8 - Cape Verde
cabo verde: 6.2.1.8 - Cape Verde
cape verdean threat: 6.2.1.8 - Cape Verde
cape verdean region: 6.2.1.8 - Cape Verde
cape verde impact: 6.2.1.8 - Cape Verde
central african republic: 6.2.1.9 - Central African Republic
central african threat: 6.2.1.9 - Central African Republic
central african region: 6.2.1.9 - Central African Republic
asia: 6.2.2 - Asia
asian countries: 6.2.2 - Asia
asian region: 6.2.2 - Asia
asia threat: 6.2.2 - Asia
asia impact: 6.2.2 - Asia
afghanistan: 6.2.2.1 - Afghanistan
afghan threat: 6.2.2.1 - Afghanistan
afghan region: 6.2.2.1 - Afghanistan
afghanistan impact: 6.2.2.1 - Afghanistan
hong kong: 6.2.2.10 - Hong Kong
hong kong threat: 6.2.2.10 - Hong Kong
hong kong region: 6.2.2.10 - Hong Kong
hong kong impact: 6.2.2.10 - Hong Kong
india: 6.2.2.11 - India
indian threat: 6.2.2.11 - India
indian region: 6.2.2.11 - India
india impact: 6.2.2.11 - India
indonesia: 6.2.2.12 - Indonesia
indonesian threat: 6.2.2.12 - Indonesia
indonesian region: 6.2.2.12 - Indonesia
indonesia impact: 6.2.2.12 - Indonesia
japan: 6.2.2.13 - Japan
japanese threat: 6.2.2.13 - Japan
japanese region: 6.2.2.13 - Japan
japan impact: 6.2.2.13 - Japan
kazakhstan: 6.2.2.14 - Kazakhstan
kazakh threat: 6.2.2.14 - Kazakhstan
kazakh region: 6.2.2.14 - Kazakhstan
kazakhstan impact: 6.2.2.14 - Kazakhstan
north korea: 6.2.2.15 - Korea, North
north korean threat: 6.2.2.15 - Korea, North
north korean region: 6.2.2.15 - Korea, North
north korea impact: 6.2.2.15 - Korea, North
south korea: 6.2.2.16 - Korea, South
south korean threat: 6.2.2.16 - Korea, South
south korean region: 6.2.2.16 - Korea, South
south korea impact: 6.2.2.16 - Korea, South
kyrgyzstan: 6.2.2.17 - Kyrgyzstan
kyrgyz threat: 6.2.2.17 - Kyrgyzstan
kyrgyz region: 6.2.2.17 - Kyrgyzstan
kyrgyzstan impact: 6.2.2.17 - Kyrgyzstan
laos: 6.2.2.18 - Laos
lao threat: 6.2.2.18 - Laos
lao region: 6.2.2.18 - Laos
laos impact: 6.2.2.18 - Laos
macao: 6.2.2.19 - Macao
macanese threat: 6.2.2.19 - Macao
macanese region: 6.2.2.19 - Macao
macao impact: 6.2.2.19 - Macao
armenia: 6.2.2.2 - Armenia
armenian threat: 6.2.2.2 - Armenia
armenian region: 6.2.2.2 - Armenia
armenia impact: 6.2.2.2 - Armenia
malaysia: 6.2.2.20 - Malaysia
malaysian threat: 6.2.2.20 - Malaysia
malaysian region: 6.2.2.20 - Malaysia
malaysia impact: 6.2.2.20 - Malaysia
maldives: 6.2.2.21 - Maldives
maldivian threat: 6.2.2.21 - Maldives
maldivian region: 6.2.2.21 - Maldives
maldives impact: 6.2.2.21 - Maldives
mongolia: 6.2.2.22 - Mongolia
mongolian threat: 6.2.2.22 - Mongolia
mongolian region: 6.2.2.22 - Mongolia
mongolia impact: 6.2.2.22 - Mongolia
myanmar: 6.2.2.23 - Myanmar (ex-Burma)
burma: 6.2.2.23 - Myanmar (ex-Burma)
burmese threat: 6.2.2.23 - Myanmar (ex-Burma)
burmese region: 6.2.2.23 - Myanmar (ex-Burma)
myanmar impact: 6.2.2.23 - Myanmar (ex-Burma)
nepal: 6.2.2.24 - Nepal
nepali threat: 6.2.2.24 - Nepal
nepali region: 6.2.2.24 - Nepal
nepal impact: 6.2.2.24 - Nepal
pakistan: 6.2.2.25 - Pakistan
pakistani threat: 6.2.2.25 - Pakistan
pakistani region: 6.2.2.25 - Pakistan
pakistan impact: 6.2.2.25 - Pakistan
philippines: 6.2.2.26 - Philippines
filipino threat: 6.2.2.26 - Philippines
filipino region: 6.2.2.26 - Philippines
philippines impact: 6.2.2.26 - Philippines
singapore: 6.2.2.27 - Singapore
singaporean threat: 6.2.2.27 - Singapore
singaporean region: 6.2.2.27 - Singapore
singapore impact: 6.2.2.27 - Singapore
sri lanka: 6.2.2.28 - Sri Lanka (ex-Ceylon)
ceylon: 6.2.2.28 - Sri Lanka (ex-Ceylon)
sri lankan threat: 6.2.2.28 - Sri Lanka (ex-Ceylon)
sri lankan region: 6.2.2.28 - Sri Lanka (ex-Ceylon)
sri lanka impact: 6.2.2.28 - Sri Lanka (ex-Ceylon)
taiwan: 6.2.2.29 - Taiwan
taiwanese threat: 6.2.2.29 - Taiwan
taiwanese region: 6.2.2.29 - Taiwan
taiwan impact: 6.2.2.29 - Taiwan
azerbaijan: 6.2.2.3 - Azerbaijan
azerbaijani threat: 6.2.2.3 - Azerbaijan
azerbaijani region: 6.2.2.3 - Azerbaijan
azerbaijan impact: 6.2.2.3 - Azerbaijan
tajikistan: 6.2.2.30 - Tajikistan
tajik threat: 6.2.2.30 - Tajikistan
tajik region: 6.2.2.30 - Tajikistan
tajikistan impact: 6.2.2.30 - Tajikistan
thailand: 6.2.2.31 - Thailand
thai threat: 6.2.2.31 - Thailand
thai region: 6.2.2.31 - Thailand
thailand impact: 6.2.2.31 - Thailand
timor leste: 6.2.2.32 - Timor Leste (West)
east timor: 6.2.2.32 - Timor Leste (West)
timorese threat: 6.2.2.32 - Timor Leste (West)
timorese region: 6.2.2.32 - Timor Leste (West)
timor leste impact: 6.2.2.32 - Timor Leste (West)
turkmenistan: 6.2.2.33 - Turkmenistan
turkmen threat: 6.2.2.33 - Turkmenistan
turkmen region: 6.2.2.33 - Turkmenistan
turkmenistan impact: 6.2.2.33 - Turkmenistan
central asia: 6.2.2.34 - Uzbekistan
uzbekistan: 6.2.2.34 - Uzbekistan
uzbek threat: 6.2.2.34 - Uzbekistan
uzbek region: 6.2.2.34 - Uzbekistan
uzbekistan impact: 6.2.2.34 - Uzbekistan
vietnam: 6.2.2.35 - Vietnam
vietnamese threat: 6.2.2.35 - Vietnam
vietnamese region: 6.2.2.35 - Vietnam
vietnam impact: 6.2.2.35 - Vietnam
bangladesh: 6.2.2.4 - Bangladesh
bangladeshi threat: 6.2.2.4 - Bangladesh
bangladeshi region: 6.2.2.4 - Bangladesh
bangladesh impact: 6.2.2.4 - Bangladesh
south asia: 6.2.2.5 - Bhutan
bhutan: 6.2.2.5 - Bhutan
bhutanese threat: 6.2.2.5 - Bhutan
bhutanese region: 6.2.2.5 - Bhutan
bhutan impact: 6.2.2.5 - Bhutan
brunei: 6.2.2.6 - Brunei Darussalam
bruneian threat: 6.2.2.6 - Brunei Darussalam
bruneian region: 6.2.2.6 - Brunei Darussalam
brunei impact: 6.2.2.6 - Brunei Darussalam
southeast asia: 6.2.2.7 - Cambodia
cambodia: 6.2.2.7 - Cambodia
cambodian threat: 6.2.2.7 - Cambodia
cambodian region: 6.2.2.7 - Cambodia
cambodia impact: 6.2.2.7 - Cambodia
east asia: 6.2.2.8 - China
china: 6.2.2.8 - China
chinese government: 6.2.2.8 - China
chinese region: 6.2.2.8 - China
china impact: 6.2.2.8 - China
caucasus: 6.2.2.9 - Georgia
georgia: 6.2.2.9 - Georgia
georgian threat: 6.2.2.9 - Georgia
georgian region: 6.2.2.9 - Georgia
georgia impact: 6.2.2.9 - Georgia
central american countries: 6.2.3 - Central America
central american region: 6.2.3 - Central America
central america threat: 6.2.3 - Central America
central america impact: 6.2.3 - Central America
belize: 6.2.3.1 - Belize
belizean threat: 6.2.3.1 - Belize
belizean region: 6.2.3.1 - Belize
belize impact: 6.2.3.1 - Belize
costa rica: 6.2.3.2 - Costa Rica
costa rican threat: 6.2.3.2 - Costa Rica
costa rican region: 6.2.3.2 - Costa Rica
costa rica impact: 6.2.3.2 - Costa Rica
el salvador: 6.2.3.3 - El Salvador
salvadoran threat: 6.2.3.3 - El Salvador
salvadoran region: 6.2.3.3 - El Salvador
el salvador impact: 6.2.3.3 - El Salvador
guatemala: 6.2.3.4 - Guatemala
guatemalan threat: 6.2.3.4 - Guatemala
guatemalan region: 6.2.3.4 - Guatemala
guatemala impact: 6.2.3.4 - Guatemala
honduras: 6.2.3.5 - Honduras
honduran threat: 6.2.3.5 - Honduras
honduran region: 6.2.3.5 - Honduras
honduras impact: 6.2.3.5 - Honduras
mexico: 6.2.3.6 - Mexico
mexican threat: 6.2.3.6 - Mexico
mexican region: 6.2.3.6 - Mexico
mexico impact: 6.2.3.6 - Mexico
nicaragua: 6.2.3.7 - Nicaragua
nicaraguan threat: 6.2.3.7 - Nicaragua
nicaraguan region: 6.2.3.7 - Nicaragua
nicaragua impact: 6.2.3.7 - Nicaragua
central america: 6.2.3.8 - Panama
panama: 6.2.3.8 - Panama
panamanian threat: 6.2.3.8 - Panama
panamanian region: 6.2.3.8 - Panama
panama impact: 6.2.3.8 - Panama
europe: 6.2.4 - Europe
european countries: 6.2.4 - Europe
european region: 6.2.4 - Europe
europe threat: 6.2.4 - Europe
europe impact: 6.2.4 - Europe
albania: 6.2.4.1 - Albania
albanian threat: 6.2.4.1 - Albania
albanian region: 6.2.4.1 - Albania
albania impact: 6.2.4.1 - Albania
czech republic: 6.2.4.10 - Czech Republic
czech threat: 6.2.4.10 - Czech Republic
czech region: 6.2.4.10 - Czech Republic
czech republic impact: 6.2.4.10 - Czech Republic
denmark: 6.2.4.11 - Denmark
danish threat: 6.2.4.11 - Denmark
danish region: 6.2.4.11 - Denmark
denmark impact: 6.2.4.11 - Denmark
estonia: 6.2.4.12 - Estonia
estonian threat: 6.2.4.12 - Estonia
estonian region: 6.2.4.12 - Estonia
estonia impact: 6.2.4.12 - Estonia
faroe islands: 6.2.4.13 - Faroe Islands
faroese threat: 6.2.4.13 - Faroe Islands
faroese region: 6.2.4.13 - Faroe Islands
faroe islands impact: 6.2.4.13 - Faroe Islands
finland: 6.2.4.14 - Finland
finnish threat: 6.2.4.14 - Finland
finnish region: 6.2.4.14 - Finland
finland impact: 6.2.4.14 - Finland
france: 6.2.4.15 - France
french threat: 6.2.4.15 - France
french region: 6.2.4.15 - France
france impact: 6.2.4.15 - France
germany: 6.2.4.16 - Germany
german threat: 6.2.4.16 - Germany
german region: 6.2.4.16 - Germany
germany impact: 6.2.4.16 - Germany
gibraltar: 6.2.4.17 - Gibraltar
gibraltarian threat: 6.2.4.17 - Gibraltar
gibraltarian region: 6.2.4.17 - Gibraltar
gibraltar impact: 6.2.4.17 - Gibraltar
greece: 6.2.4.18 - Greece
greek threat: 6.2.4.18 - Greece
greek region: 6.2.4.18 - Greece
greece impact: 6.2.4.18 - Greece
guernsey: 6.2.4.19 - Guernsey and Alderney
alderney: 6.2.4.19 - Guernsey and Alderney
guernsey threat: 6.2.4.19 - Guernsey and Alderney
alderney threat: 6.2.4.19 - Guernsey and Alderney
andorra: 6.2.4.2 - Andorra
andorran threat: 6.2.4.2 - Andorra
andorran region: 6.2.4.2 - Andorra
andorra impact: 6.2.4.2 - Andorra
hungary: 6.2.4.20 - Hungary
hungarian threat: 6.2.4.20 - Hungary
hungarian region: 6.2.4.20 - Hungary
hungary impact: 6.2.4.20 - Hungary
north atlantic: 6.2.4.21 - Iceland
iceland: 6.2.4.21 - Iceland
icelandic threat: 6.2.4.21 - Iceland
icelandic region: 6.2.4.21 - Iceland
iceland impact: 6.2.4.21 - Iceland
ireland: 6.2.4.22 - Ireland
irish threat: 6.2.4.22 - Ireland
irish region: 6.2.4.22 - Ireland
ireland impact: 6.2.4.22 - Ireland
italy: 6.2.4.23 - Italy
italian threat: 6.2.4.23 - Italy
italian region: 6.2.4.23 - Italy
italy impact: 6.2.4.23 - Italy
channel islands: 6.2.4.24 - Jersey
jersey: 6.2.4.24 - Jersey
jersey threat: 6.2.4.24 - Jersey
jersey region: 6.2.4.24 - Jersey
jersey impact: 6.2.4.24 - Jersey
kosovo: 6.2.4.25 - Kosovo
kosovar threat: 6.2.4.25 - Kosovo
kosovar region: 6.2.4.25 - Kosovo
kosovo impact: 6.2.4.25 - Kosovo
latvia: 6.2.4.26 - Latvia
latvian threat: 6.2.4.26 - Latvia
latvian region: 6.2.4.26 - Latvia
latvia impact: 6.2.4.26 - Latvia
liechtenstein: 6.2.4.27 - Liechtenstein
liechtensteiner threat: 6.2.4.27 - Liechtenstein
liechtensteiner region: 6.2.4.27 - Liechtenstein
liechtenstein impact: 6.2.4.27 - Liechtenstein
baltic states: 6.2.4.28 - Lithuania
lithuania: 6.2.4.28 - Lithuania
lithuanian threat: 6.2.4.28 - Lithuania
lithuanian region: 6.2.4.28 - Lithuania
lithuania impact: 6.2.4.28 - Lithuania
luxembourg: 6.2.4.29 - Luxembourg
luxembourgish threat: 6.2.4.29 - Luxembourg
luxembourgish region: 6.2.4.29 - Luxembourg
luxembourg impact: 6.2.4.29 - Luxembourg
austria: 6.2.4.3 - Austria
austrian threat: 6.2.4.3 - Austria
austrian region: 6.2.4.3 - Austria
austria impact: 6.2.4.3 - Austria
malta: 6.2.4.30 - Malta
maltese threat: 6.2.4.30 - Malta
maltese region: 6.2.4.30 - Malta
malta impact: 6.2.4.30 - Malta
isle of man: 6.2.4.31 - Man, Isle of
manx threat: 6.2.4.31 - Man, Isle of
manx region: 6.2.4.31 - Man, Isle of
isle of man impact: 6.2.4.31 - Man, Isle of
british isles: 6.2.4.31 - Man, Isle of
moldova: 6.2.4.32 - Moldova
moldovan threat: 6.2.4.32 - Moldova
moldovan region: 6.2.4.32 - Moldova
moldova impact: 6.2.4.32 - Moldova
monaco: 6.2.4.33 - Monaco
monegasque threat: 6.2.4.33 - Monaco
monegasque region: 6.2.4.33 - Monaco
monaco impact: 6.2.4.33 - Monaco
montenegro: 6.2.4.34 - Montenegro
montenegrin threat: 6.2.4.34 - Montenegro
montenegrin region: 6.2.4.34 - Montenegro
montenegro impact: 6.2.4.34 - Montenegro
netherlands: 6.2.4.35 - Netherlands
dutch threat: 6.2.4.35 - Netherlands
dutch region: 6.2.4.35 - Netherlands
netherlands impact: 6.2.4.35 - Netherlands
north macedonia: 6.2.4.36 - North Macedonia
macedonian threat: 6.2.4.36 - North Macedonia
macedonian region: 6.2.4.36 - North Macedonia
north macedonia impact: 6.2.4.36 - North Macedonia
norway: 6.2.4.37 - Norway
norwegian threat: 6.2.4.37 - Norway
norwegian region: 6.2.4.37 - Norway
norway impact: 6.2.4.37 - Norway
poland: 6.2.4.38 - Poland
polish threat: 6.2.4.38 - Poland
polish region: 6.2.4.38 - Poland
poland impact: 6.2.4.38 - Poland
portugal: 6.2.4.39 - Portugal
portuguese threat: 6.2.4.39 - Portugal
portuguese region: 6.2.4.39 - Portugal
portugal impact: 6.2.4.39 - Portugal
belarus: 6.2.4.4 - Belarus
belarusian threat: 6.2.4.4 - Belarus
belarusian region: 6.2.4.4 - Belarus
belarus impact: 6.2.4.4 - Belarus
romania: 6.2.4.40 - Romania
romanian threat: 6.2.4.40 - Romania
romanian region: 6.2.4.40 - Romania
romania impact: 6.2.4.40 - Romania
russia: 6.2.4.41 - Russia
russian threat: 6.2.4.41 - Russia
russian region: 6.2.4.41 - Russia
russia impact: 6.2.4.41 - Russia
san marino: 6.2.4.42 - San Marino
sammarinese threat: 6.2.4.42 - San Marino
sammarinese region: 6.2.4.42 - San Marino
san marino impact: 6.2.4.42 - San Marino
serbia: 6.2.4.43 - Serbia
serbian threat: 6.2.4.43 - Serbia
serbian region: 6.2.4.43 - Serbia
serbia impact: 6.2.4.43 - Serbia
slovakia: 6.2.4.44 - Slovakia
slovak threat: 6.2.4.44 - Slovakia
slovak region: 6.2.4.44 - Slovakia
slovakia impact: 6.2.4.44 - Slovakia
slovenia: 6.2.4.45 - Slovenia
slovenian threat: 6.2.4.45 - Slovenia
slovenian region: 6.2.4.45 - Slovenia
slovenia impact: 6.2.4.45 - Slovenia
spain: 6.2.4.46 - Spain
spanish threat: 6.2.4.46 - Spain
spanish region: 6.2.4.46 - Spain
spain impact: 6.2.4.46 - Spain
svalbard: 6.2.4.47 - Svalbard and Jan Mayen Islands
jan mayen islands: 6.2.4.47 - Svalbard and Jan Mayen Islands
svalbard threat: 6.2.4.47 - Svalbard and Jan Mayen Islands
jan mayen threat: 6.2.4.47 - Svalbard and Jan Mayen Islands
arctic region: 6.2.4.47 - Svalbard and Jan Mayen Islands
northern europe: 6.2.4.48 - Sweden
sweden: 6.2.4.48 - Sweden
swedish threat: 6.2.4.48 - Sweden
swedish region: 6.2.4.48 - Sweden
sweden impact: 6.2.4.48 - Sweden
central europe: 6.2.4.49 - Switzerland
switzerland: 6.2.4.49 - Switzerland
swiss threat: 6.2.4.49 - Switzerland
swiss region: 6.2.4.49 - Switzerland
switzerland impact: 6.2.4.49 - Switzerland
belgium: 6.2.4.5 - Belgium
belgian threat: 6.2.4.5 - Belgium
belgian region: 6.2.4.5 - Belgium
belgium impact: 6.2.4.5 - Belgium
turkey: 6.2.4.50 - Turkey
turkish threat: 6.2.4.50 - Turkey
turkish region: 6.2.4.50 - Turkey
turkey impact: 6.2.4.50 - Turkey
ukraine: 6.2.4.51 - Ukraine
ukrainian threat: 6.2.4.51 - Ukraine
ukrainian region: 6.2.4.51 - Ukraine
ukraine impact: 6.2.4.51 - Ukraine
western europe: 6.2.4.52 - United Kingdom
united kingdom: 6.2.4.52 - United Kingdom
british threat: 6.2.4.52 - United Kingdom
british region: 6.2.4.52 - United Kingdom
uk impact: 6.2.4.52 - United Kingdom
vatican city: 6.2.4.53 - Vatican City State (Holy See)
holy see: 6.2.4.53 - Vatican City State (Holy See)
vatican threat: 6.2.4.53 - Vatican City State (Holy See)
holy see threat: 6.2.4.53 - Vatican City State (Holy See)
vatican city impact: 6.2.4.53 - Vatican City State (Holy See)
bosnia: 6.2.4.6 - Bosnia
bosnian threat: 6.2.4.6 - Bosnia
bosnian region: 6.2.4.6 - Bosnia
bosnia impact: 6.2.4.6 - Bosnia
eastern europe: 6.2.4.7 - Bulgaria
bulgaria: 6.2.4.7 - Bulgaria
bulgarian threat: 6.2.4.7 - Bulgaria
bulgarian region: 6.2.4.7 - Bulgaria
bulgaria impact: 6.2.4.7 - Bulgaria
balkans: 6.2.4.8 - Croatia
croatia: 6.2.4.8 - Croatia
croatian threat: 6.2.4.8 - Croatia
croatian region: 6.2.4.8 - Croatia
croatia impact: 6.2.4.8 - Croatia
southern europe: 6.2.4.9 - Cyprus
cyprus: 6.2.4.9 - Cyprus
cypriot threat: 6.2.4.9 - Cyprus
cypriot region: 6.2.4.9 - Cyprus
cyprus impact: 6.2.4.9 - Cyprus
middle eastern countries: 6.2.5 - Middle East
middle eastern region: 6.2.5 - Middle East
middle east threat: 6.2.5 - Middle East
middle east impact: 6.2.5 - Middle East
bahrain: 6.2.5.1 - Bahrain
bahraini threat: 6.2.5.1 - Bahrain
bahraini region: 6.2.5.1 - Bahrain
bahrain impact: 6.2.5.1 - Bahrain
qatar: 6.2.5.10 - Qatar
qatari threat: 6.2.5.10 - Qatar
qatari region: 6.2.5.10 - Qatar
qatar impact: 6.2.5.10 - Qatar
saudi arabia: 6.2.5.11 - Saudi Arabia
saudi threat: 6.2.5.11 - Saudi Arabia
saudi region: 6.2.5.11 - Saudi Arabia
saudi arabia impact: 6.2.5.11 - Saudi Arabia
syria: 6.2.5.12 - Syria
syrian threat: 6.2.5.12 - Syria
syrian region: 6.2.5.12 - Syria
syria impact: 6.2.5.12 - Syria
united arab emirates: 6.2.5.13 - United Arab Emirates
uae: 6.2.5.13 - United Arab Emirates
emirati threat: 6.2.5.13 - United Arab Emirates
emirati region: 6.2.5.13 - United Arab Emirates
uae impact: 6.2.5.13 - United Arab Emirates
yemen: 6.2.5.14 - Yemen
yemeni threat: 6.2.5.14 - Yemen
yemeni region: 6.2.5.14 - Yemen
yemen impact: 6.2.5.14 - Yemen
iran: 6.2.5.2 - Iran
iranian threat: 6.2.5.2 - Iran
iranian region: 6.2.5.2 - Iran
iran impact: 6.2.5.2 - Iran
iraq: 6.2.5.3 - Iraq
iraqi threat: 6.2.5.3 - Iraq
iraqi region: 6.2.5.3 - Iraq
iraq impact: 6.2.5.3 - Iraq
israel: 6.2.5.4 - Israel
israeli threat: 6.2.5.4 - Israel
israeli region: 6.2.5.4 - Israel
israel impact: 6.2.5.4 - Israel
jordan: 6.2.5.5 - Jordan
jordanian threat: 6.2.5.5 - Jordan
jordanian region: 6.2.5.5 - Jordan
jordan impact: 6.2.5.5 - Jordan
kuwait: 6.2.5.6 - Kuwait
kuwaiti threat: 6.2.5.6 - Kuwait
kuwaiti region: 6.2.5.6 - Kuwait
kuwait impact: 6.2.5.6 - Kuwait
lebanon: 6.2.5.7 - Lebanon
lebanese threat: 6.2.5.7 - Lebanon
lebanese region: 6.2.5.7 - Lebanon
lebanon impact: 6.2.5.7 - Lebanon
middle east: 6.2.5.8 - Oman
oman: 6.2.5.8 - Oman
omani threat: 6.2.5.8 - Oman
omani region: 6.2.5.8 - Oman
oman impact: 6.2.5.8 - Oman
palestinian territories: 6.2.5.9 - Palestinian territories
palestinian threat: 6.2.5.9 - Palestinian territories
palestinian region: 6.2.5.9 - Palestinian territories
palestinian territories impact: 6.2.5.9 - Palestinian territories
north american countries: 6.2.6 - North America
north american region: 6.2.6 - North America
north america threat: 6.2.6 - North America
north america impact: 6.2.6 - North America
bermuda: 6.2.6.1 - Bermuda
bermudian threat: 6.2.6.1 - Bermuda
bermudian region: 6.2.6.1 - Bermuda
bermuda impact: 6.2.6.1 - Bermuda
canada: 6.2.6.2 - Canada
canadian threat: 6.2.6.2 - Canada
canadian region: 6.2.6.2 - Canada
canada impact: 6.2.6.2 - Canada
greenland: 6.2.6.3 - Greenland
greenlandic threat: 6.2.6.3 - Greenland
greenlandic region: 6.2.6.3 - Greenland
greenland impact: 6.2.6.3 - Greenland
saint pierre and miquelon: 6.2.6.4 - Saint Pierre and Miquelon
saint pierre and miquelon threat: 6.2.6.4 - Saint Pierre and Miquelon
saint pierre and miquelon region: 6.2.6.4 - Saint Pierre and Miquelon
saint pierre and miquelon impact: 6.2.6.4 - Saint Pierre and Miquelon
north america: 6.2.6.5 - United States
united states: 6.2.6.5 - United States
american threat: 6.2.6.5 - United States
american region: 6.2.6.5 - United States
united states impact: 6.2.6.5 - United States
oceania countries: 6.2.7 - Oceania
oceania region: 6.2.7 - Oceania
oceania threat: 6.2.7 - Oceania
oceania impact: 6.2.7 - Oceania
australia: 6.2.7.1 - Australia
australian threat: 6.2.7.1 - Australia
australian region: 6.2.7.1 - Australia
australia impact: 6.2.7.1 - Australia
palau: 6.2.7.10 - Palau
palauan threat: 6.2.7.10 - Palau
palauan region: 6.2.7.10 - Palau
palau impact: 6.2.7.10 - Palau
papua new guinea: 6.2.7.11 - Papua New Guinea
papua new guinean threat: 6.2.7.11 - Papua New Guinea
papua new guinean region: 6.2.7.11 - Papua New Guinea
papua new guinea impact: 6.2.7.11 - Papua New Guinea
samoa: 6.2.7.12 - Samoa
samoan threat: 6.2.7.12 - Samoa
samoan region: 6.2.7.12 - Samoa
samoa impact: 6.2.7.12 - Samoa
american samoa: 6.2.7.13 - Samoa, American
american samoan threat: 6.2.7.13 - Samoa, American
american samoan region: 6.2.7.13 - Samoa, American
american samoa impact: 6.2.7.13 - Samoa, American
solomon islands: 6.2.7.14 - Solomon Islands
solomon islander threat: 6.2.7.14 - Solomon Islands
solomon islander region: 6.2.7.14 - Solomon Islands
solomon islands impact: 6.2.7.14 - Solomon Islands
tonga: 6.2.7.15 - Tonga
tongan threat: 6.2.7.15 - Tonga
tongan region: 6.2.7.15 - Tonga
tonga impact: 6.2.7.15 - Tonga
tuvalu: 6.2.7.16 - Tuvalu
tuvaluan threat: 6.2.7.16 - Tuvalu
tuvaluan region: 6.2.7.16 - Tuvalu
tuvalu impact: 6.2.7.16 - Tuvalu
vanuatu: 6.2.7.17 - Vanuatu
vanuatuan threat: 6.2.7.17 - Vanuatu
vanuatuan region: 6.2.7.17 - Vanuatu
vanuatu impact: 6.2.7.17 - Vanuatu
fiji: 6.2.7.2 - Fiji
fijian threat: 6.2.7.2 - Fiji
fijian region: 6.2.7.2 - Fiji
fiji impact: 6.2.7.2 - Fiji
french polynesia: 6.2.7.3 - French Polynesia
polynesian threat: 6.2.7.3 - French Polynesia
polynesian region: 6.2.7.3 - French Polynesia
french polynesia impact: 6.2.7.3 - French Polynesia
guam: 6.2.7.4 - Guam
guamanian threat: 6.2.7.4 - Guam
guamanian region: 6.2.7.4 - Guam
guam impact: 6.2.7.4 - Guam
kiribati: 6.2.7.5 - Kiribati
i-kiribati threat: 6.2.7.5 - Kiribati
i-kiribati region: 6.2.7.5 - Kiribati
kiribati impact: 6.2.7.5 - Kiribati
marshall islands: 6.2.7.6 - Marshall Islands
marshallese threat: 6.2.7.6 - Marshall Islands
marshallese region: 6.2.7.6 - Marshall Islands
marshall islands impact: 6.2.7.6 - Marshall Islands
micronesia: 6.2.7.7 - Micronesia
micronesian threat: 6.2.7.7 - Micronesia
micronesian region: 6.2.7.7 - Micronesia
micronesia impact: 6.2.7.7 - Micronesia
new caledonia: 6.2.7.8 - New Caledonia
caledonian threat: 6.2.7.8 - New Caledonia
caledonian region: 6.2.7.8 - New Caledonia
new caledonia impact: 6.2.7.8 - New Caledonia
oceania: 6.2.7.9 - New Zealand
new zealand: 6.2.7.9 - New Zealand
new zealander threat: 6.2.7.9 - New Zealand
new zealander region: 6.2.7.9 - New Zealand
new zealand impact: 6.2.7.9 - New Zealand
south american countries: 6.2.8 - South America
south american region: 6.2.8 - South America
south america threat: 6.2.8 - South America
south america impact: 6.2.8 - South America
argentina: 6.2.8.1 - Argentina
argentine threat: 6.2.8.1 - Argentina
argentine region: 6.2.8.1 - Argentina
argentina impact: 6.2.8.1 - Argentina
paraguay: 6.2.8.10 - Paraguay
paraguayan threat: 6.2.8.10 - Paraguay
paraguayan region: 6.2.8.10 - Paraguay
paraguay impact: 6.2.8.10 - Paraguay
peru: 6.2.8.11 - Peru
peruvian threat: 6.2.8.11 - Peru
peruvian region: 6.2.8.11 - Peru
peru impact: 6.2.8.11 - Peru
suriname: 6.2.8.12 - Suriname
surinamese threat: 6.2.8.12 - Suriname
surinamese region: 6.2.8.12 - Suriname
suriname impact: 6.2.8.12 - Suriname
uruguay: 6.2.8.13 - Uruguay
uruguayan threat: 6.2.8.13 - Uruguay
uruguayan region: 6.2.8.13 - Uruguay
uruguay impact: 6.2.8.13 - Uruguay
venezuela: 6.2.8.14 - Venezuela
venezuelan threat: 6.2.8.14 - Venezuela
venezuelan region: 6.2.8.14 - Venezuela
venezuela impact: 6.2.8.14 - Venezuela
bolivia: 6.2.8.2 - Bolivia
bolivian threat: 6.2.8.2 - Bolivia
bolivian region: 6.2.8.2 - Bolivia
bolivia impact: 6.2.8.2 - Bolivia
brazil: 6.2.8.3 - Brazil
brazilian threat: 6.2.8.3 - Brazil
brazilian region: 6.2.8.3 - Brazil
brazil impact: 6.2.8.3 - Brazil
chile: 6.2.8.4 - Chile
chilean threat: 6.2.8.4 - Chile
chilean region: 6.2.8.4 - Chile
chile impact: 6.2.8.4 - Chile
colombia: 6.2.8.5 - Colombia
colombian threat: 6.2.8.5 - Colombia
colombian region: 6.2.8.5 - Colombia
colombia impact: 6.2.8.5 - Colombia
ecuador: 6.2.8.6 - Ecuador
ecuadorian threat: 6.2.8.6 - Ecuador
ecuadorian region: 6.2.8.6 - Ecuador
ecuador impact: 6.2.8.6 - Ecuador
falkland islands: 6.2.8.7 - Falkland Islands (Malvinas)
malvinas: 6.2.8.7 - Falkland Islands (Malvinas)
falklands threat: 6.2.8.7 - Falkland Islands (Malvinas)
malvinas threat: 6.2.8.7 - Falkland Islands (Malvinas)
falkland islands impact: 6.2.8.7 - Falkland Islands (Malvinas)
french guiana: 6.2.8.8 - French Guiana
guianese threat: 6.2.8.8 - French Guiana
guianese region: 6.2.8.8 - French Guiana
french guiana impact: 6.2.8.8 - French Guiana
south america: 6.2.8.9 - Guyana
guyana: 6.2.8.9 - Guyana
guyanese threat: 6.2.8.9 - Guyana
guyanese region: 6.2.8.9 - Guyana
guyana impact: 6.2.8.9 - Guyana
caribbean countries: 6.2.9 - The Caribbean
caribbean region: 6.2.9 - The Caribbean
caribbean threat: 6.2.9 - The Caribbean
caribbean impact: 6.2.9 - The Caribbean
anguilla: 6.2.9.1 - Anguilla
anguillian threat: 6.2.9.1 - Anguilla
anguillian region: 6.2.9.1 - Anguilla
anguilla impact: 6.2.9.1 - Anguilla
dominica: 6.2.9.10 - Dominica
dominica impact: 6.2.9.10 - Dominica
dominican threat: 6.2.9.11 - Dominican Republic
dominican region: 6.2.9.11 - Dominican Republic
dominican republic: 6.2.9.11 - Dominican Republic
dominican republic impact: 6.2.9.11 - Dominican Republic
grenada: 6.2.9.12 - Grenada
grenadian threat: 6.2.9.12 - Grenada
grenadian region: 6.2.9.12 - Grenada
grenada impact: 6.2.9.12 - Grenada
guadeloupe: 6.2.9.13 - Guadeloupe
guadeloupean threat: 6.2.9.13 - Guadeloupe
guadeloupean region: 6.2.9.13 - Guadeloupe
guadeloupe impact: 6.2.9.13 - Guadeloupe
haiti: 6.2.9.14 - Haiti
haitian threat: 6.2.9.14 - Haiti
haitian region: 6.2.9.14 - Haiti
haiti impact: 6.2.9.14 - Haiti
jamaica: 6.2.9.15 - Jamaica
jamaican threat: 6.2.9.15 - Jamaica
jamaican region: 6.2.9.15 - Jamaica
jamaica impact: 6.2.9.15 - Jamaica
martinique: 6.2.9.16 - Martinique
martinican threat: 6.2.9.16 - Martinique
martinican region: 6.2.9.16 - Martinique
martinique impact: 6.2.9.16 - Martinique
montserrat: 6.2.9.17 - Montserrat
montserratian threat: 6.2.9.17 - Montserrat
montserratian region: 6.2.9.17 - Montserrat
montserrat impact: 6.2.9.17 - Montserrat
puerto rico: 6.2.9.18 - Puerto Rico
puerto rican threat: 6.2.9.18 - Puerto Rico
puerto rican region: 6.2.9.18 - Puerto Rico
puerto rico impact: 6.2.9.18 - Puerto Rico
"saint barthélemy": "6.2.9.19 - Saint Barthélemy"
"saint barthélemy threat": "6.2.9.19 - Saint Barthélemy"
"saint barthélemy region": "6.2.9.19 - Saint Barthélemy"
"saint barthélemy impact": "6.2.9.19 - Saint Barthélemy"
antigua and barbuda: 6.2.9.2 - Antigua and Barbuda
antiguan threat: 6.2.9.2 - Antigua and Barbuda
barbudan threat: 6.2.9.2 - Antigua and Barbuda
antigua and barbuda region: 6.2.9.2 - Antigua and Barbuda
antigua and barbuda impact: 6.2.9.2 - Antigua and Barbuda
saint kitts and nevis: 6.2.9.20 - Saint Kitts and Nevis
saint kitts threat: 6.2.9.20 - Saint Kitts and Nevis
nevisian threat: 6.2.9.20 - Saint Kitts and Nevis
saint kitts and nevis impact: 6.2.9.20 - Saint Kitts and Nevis
saint lucia: 6.2.9.21 - Saint Lucia
saint lucian threat: 6.2.9.21 - Saint Lucia
saint lucian region: 6.2.9.21 - Saint Lucia
saint lucia impact: 6.2.9.21 - Saint Lucia
saint martin: 6.2.9.22 - Saint Martin
saint martin threat: 6.2.9.22 - Saint Martin
saint martin region: 6.2.9.22 - Saint Martin
saint martin impact: 6.2.9.22 - Saint Martin
saint vincent: 6.2.9.23 - Saint Vincent and the Grenadines
grenadines: 6.2.9.23 - Saint Vincent and the Grenadines
saint vincent threat: 6.2.9.23 - Saint Vincent and the Grenadines
grenadines threat: 6.2.9.23 - Saint Vincent and the Grenadines
saint vincent and the grenadines impact: 6.2.9.23 - Saint Vincent and the Grenadines
sint maarten: 6.2.9.24 - Sint Maarten
sint maarten threat: 6.2.9.24 - Sint Maarten
sint maarten region: 6.2.9.24 - Sint Maarten
sint maarten impact: 6.2.9.24 - Sint Maarten
trinidad and tobago: 6.2.9.25 - Trinidad and Tobago
trinidadian threat: 6.2.9.25 - Trinidad and Tobago
tobagonian threat: 6.2.9.25 - Trinidad and Tobago
trinidad and tobago impact: 6.2.9.25 - Trinidad and Tobago
turks and caicos: 6.2.9.26 - Turks and Caicos Islands
turks threat: 6.2.9.26 - Turks and Caicos Islands
caicos threat: 6.2.9.26 - Turks and Caicos Islands
turks and caicos impact: 6.2.9.26 - Turks and Caicos Islands
virgin islands: 6.2.9.27 - Virgin Islands (U.S.)
usvi: 6.2.9.27 - Virgin Islands (U.S.)
usvi threat: 6.2.9.27 - Virgin Islands (U.S.)
virgin islands impact: 6.2.9.27 - Virgin Islands (U.S.)
aruba: 6.2.9.3 - Aruba
aruban threat: 6.2.9.3 - Aruba
aruban region: 6.2.9.3 - Aruba
aruba impact: 6.2.9.3 - Aruba
bahamas: 6.2.9.4 - Bahamas
bahamian threat: 6.2.9.4 - Bahamas
bahamian region: 6.2.9.4 - Bahamas
bahamas impact: 6.2.9.4 - Bahamas
barbados: 6.2.9.5 - Barbados
barbadian threat: 6.2.9.5 - Barbados
barbadian region: 6.2.9.5 - Barbados
barbados impact: 6.2.9.5 - Barbados
bonaire: 6.2.9.6 - Bonaire, Sint Eustatius and Saba
sint eustatius: 6.2.9.6 - Bonaire, Sint Eustatius and Saba
saba: 6.2.9.6 - Bonaire, Sint Eustatius and Saba
bonaire threat: 6.2.9.6 - Bonaire, Sint Eustatius and Saba
sint eustatius threat: 6.2.9.6 - Bonaire, Sint Eustatius and Saba
saba threat: 6.2.9.6 - Bonaire, Sint Eustatius and Saba
virgin islands threat: 6.2.9.7 - British Virgin Islands
british virgin islands: 6.2.9.7 - British Virgin Islands
bvi: 6.2.9.7 - British Virgin Islands
bvi threat: 6.2.9.7 - British Virgin Islands
british virgin islands impact: 6.2.9.7 - British Virgin Islands
cuba: 6.2.9.8 - Cuba
cuban threat: 6.2.9.8 - Cuba
cuban region: 6.2.9.8 - Cuba
cuba impact: 6.2.9.8 - Cuba
caribbean: 6.2.9.9 - Curacao
curacao: 6.2.9.9 - Curacao
curacaoan threat: 6.2.9.9 - Curacao
curacaoan region: 6.2.9.9 - Curacao
curacao impact: 6.2.9.9 - CuracaoUse Case Example
- A Threat Analyst identifies a collection of reports from a provider that contains news about recent cyber attacks.
- The Threat Analyst adds the ThreatQ Intel Requirement Mapper Action to a workflow.
- The Threat Analyst configures the action with the desired parameters, and enables the workflow.
- The action automatically parses the reports and will create relationships to Intel Requirement objects when keywords are matched.
Outcome:
Using this action, teams will be able to quickly identify reports that are relevant to their organization. This will allow them to focus on the most critical threats and take action to mitigate threats and prevent future attacks.
Known Issues / Limitations
- Due to some platform limitation the keyword user field might not work as expected. Some keywords might not be matched.
- The Custom Intel Requirement Mapping user field supports up to 16k characters. Workflows with mapping larger than that should be split into multiple workflows to avoid mapping issues.
Change Log
- Version 1.0.0 rev-a
- Guide Update - updated custom object installation steps for ThreatQ v6 instances.
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| ThreatQ Intel Requirement Mapper Action Guide v1.0.0 | 5.12.1 or Greater |