Extract FQDNs Action
The web format of this guide reflects the most current release. Guides for older iterations are available in PDF format.
Integration Details
ThreatQuotient provides the following details for this integration:
| Current Integration Version | 1.0.0 |
| Compatible with ThreatQ Versions | >= 5.12.1 |
| ThreatQ TQO License Required | Yes |
| Support Tier | ThreatQ Supported |
Introduction
The Extract FQDNs action enables the automatic extraction of FQDNs (or IP Addresses) from URLs within your Threat Library.
The integration provides the following action:
- Extract FQDNs - extracts a URL's FQDN, or IP Address, add it your Threat Library, and relate it to the URL.
The action is compatible with URL type indicators.
The action returns the following enriched indicator types:
- FQDN
- IP Address
This action is intended for use with ThreatQ TDR Orchestrator (TQO). An active TQO license is required for this feature.
Prerequisites
- An active ThreatQ TDR Orchestrator (TQO) license.
- A data collection containing the following URL type indicators.
Installation
Perform the following steps to install the integration:
The same steps can be used to upgrade the integration to a new version.
- Log into https://marketplace.threatq.com/.
- Locate and download the action zip file.
- Navigate to the integrations management page on your ThreatQ instance.
- Click on the Add New Integration button.
- Upload the action zip file using one of the following methods:
- Drag and drop the zip file into the dialog box
- Select Click to Browse to locate the zip file on your local machine
ThreatQ will inform you if the action already exists on the platform and will require user confirmation before proceeding. ThreatQ will also inform you if the new version of the action contains changes to the user configuration. The new user configurations will overwrite the existing ones for the action and will require user confirmation before proceeding.
You will still need to configure the action.
Configuration
ThreatQuotient does not issue API keys for third-party vendors. Contact the specific vendor to obtain API keys and other integration-related credentials.
To configure the integration:
- Navigate to your integrations management page in ThreatQ.
- Select the Actions option from the Category dropdown (optional).
- Click on the action entry to open its details page.
- Enter the following parameters under the Configuration tab:
The configurations set on this page will be used as the default settings when inserting this action into a new workflow. Updating the configurations on this page will not update any instances of this action that have already been deployed to a workflow. In that scenario, you must update the action’s configurations within the workflow itself.
Parameter Description Do Not Extract IPs Enabling this option will result in the action skipping ingestion of IP Addresses extracted from a URL. This option is disabled by default. Strip www from FQDN Enabling this parameter will result in the www being stripped from the FQDN. This option is enabled by default. Source Handling Select how the action will handle the source of the extracted IoCs. Options include: - Use the original source (default) - this method is recommended.
- Use the name of the workflow. Example: Extract FQDNs.
- Use both the original source and the workflow name.
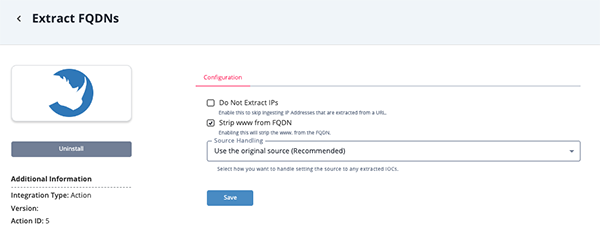
- Review any additional settings, make any changes if needed, and click on Save.
Actions
The following action is available:
| Action | Description | Object Type | Object Subtype |
|---|---|---|---|
| Extract FQDNs | Extracts FQDNs and IP Addresses from a URL in a given data collection. | Indicator | URL |
Extract FQDNs
The Extract FQDNs action will extract a URL's FQDN (or IP Address), add it to your Threat Library, and relate it to the URL.
There are no samples, endpoints, or data mapping tables for this action as it works with existing data in your ThreatQ Threat Library. No additional data is submitted or ingested to/from third-party providers.
Enriched Data
Object counts and action runtime are supplied as generalities only - objects returned by a provider can differ based on credential configurations and action runtime may vary based on system resources and load.
| Metric | Result |
|---|---|
| Run Time | 1 minute |
| Indicators | 184 |
Use Case Example
I have a feed that reports URLs to my Threat Library, but do not extract or report the underlying FQDNs. I want to send the FQDNs to my DNS resolver to be blocked, but I can't because they are reported as URLs. Using this action, I can extract those FQDNs so they can be disseminated to my downstream tools for blocking.
Change Log
- Version 1.0.0
- Initial release
PDF Guides
| Document | ThreatQ Version |
|---|---|
| Extract FQDNs Action Guide v1.0.0 | 5.12.1 or Greater |